In today’s interconnected digital landscape, where cyber threats lurk around every corner, the question for businesses isn’t if they’ll experience a security incident, but when. From sophisticated ransomware attacks to subtle data breaches, the potential for disruption and damage is immense. This reality makes a robust and clearly defined strategy for handling such events not just a best practice, but an absolute necessity. Enter the Security Incident Response Policy Template – an indispensable tool for any organization looking to fortify its defenses and ensure business continuity.
A well-crafted Security Incident Response Policy Template serves as the operational blueprint for an organization’s reaction to a security breach or cyberattack. It outlines the crucial steps, roles, and responsibilities needed to identify, contain, eradicate, recover from, and learn from an incident. This foundational document provides clarity and direction under pressure, benefiting everyone from IT security teams and compliance officers to executive leadership and legal counsel, ensuring a unified and effective response when seconds count.
Why a Security Incident Response Policy Template is Essential
The digital age has brought unprecedented opportunities, but also an escalating threat landscape. Cybercriminals are more organized, innovative, and persistent than ever, targeting organizations of all sizes. Without a predefined Security Incident Response Policy Template, companies often find themselves scrambling in the chaos of a security incident, leading to slower reaction times, uncoordinated efforts, and significantly greater damage.
This template is not just about reacting; it’s about minimizing the impact. A well-prepared organization can mitigate financial losses, protect its reputation, and maintain customer trust. Furthermore, regulatory bodies across various industries, such as HIPAA for healthcare, GDPR for data privacy in Europe (affecting US companies with European customers), and CCPA in California, increasingly mandate robust incident response capabilities. Having a comprehensive Security Incident Response Policy Template demonstrates due diligence and helps ensure compliance with these complex legal and regulatory requirements, avoiding hefty fines and legal repercussions. It transitions an organization from a reactive stance to a proactive, resilient one, embedding cyber resilience into its core operational framework.
Key Benefits of Utilizing a Security Incident Response Policy Template
Adopting and adapting a Security Incident Response Policy Template brings a multitude of strategic and operational advantages to an organization. Firstly, it establishes a standardized approach to incident management. This consistency ensures that every security event, regardless of its nature or severity, is handled through a predefined set of steps, reducing guesswork and potential errors during high-stress situations. This standardization also makes it easier to train personnel and assess performance.
Secondly, a clear policy significantly reduces downtime and accelerates recovery. By outlining specific procedures for detection, containment, eradication, and recovery, the template helps teams act swiftly and effectively, minimizing the operational disruption caused by an incident. This translates directly into cost savings by reducing lost productivity and potential revenue. Thirdly, it improves internal and external communication. The template specifies who needs to be informed, when, and how, ensuring stakeholders, customers, and even regulatory bodies receive timely and accurate information, which is critical for maintaining trust and fulfilling legal obligations. It also defines roles and responsibilities clearly, preventing confusion and ensuring accountability among response team members. Lastly, by documenting lessons learned from each incident, the Security Incident Response Policy Template fosters continuous improvement in an organization’s overall security posture, reinforcing data security best practices and strengthening workplace rules surrounding digital assets.
Customizing Your Security Incident Response Policy Template
While a Security Incident Response Policy Template provides an excellent starting point, it’s crucial to understand that it’s a foundation, not a one-size-fits-all solution. Each organization has unique operational requirements, a specific technological infrastructure, and varying compliance obligations. Therefore, effective customization is paramount to ensure the policy is relevant, practical, and truly effective for your specific environment.
The adaptation process should begin with a thorough assessment of your organization’s risk profile, considering factors such as industry sector, the volume and sensitivity of data handled, and the existing IT ecosystem. For instance, a healthcare provider will need to place a heavy emphasis on HIPAA compliance within their policy, whereas a financial institution will focus more on PCI DSS and other banking regulations. Small businesses might opt for a more streamlined approach, while larger enterprises will require more intricate structures and specialized teams. Involve key stakeholders from across departments, including IT, legal, HR, communications, and executive leadership, to ensure the policy aligns with business objectives, corporate governance, and existing workplace rules. This collaborative approach ensures that the customized Security Incident Response Policy Template is not only technically sound but also practically implementable across the organization, making it a living document that supports organizational resilience.
Important Elements to Include in Your Security Incident Response Policy Template
A comprehensive Security Incident Response Policy Template is structured to guide an organization through every phase of an incident. While customization is key, certain core elements are universally essential for an effective policy. These components ensure clarity, accountability, and a systematic approach to incident management.
Here are the important elements that should be included:
- Policy Statement and Scope: Clearly articulate the policy’s purpose, objectives, and the systems, data, and personnel it covers. This sets the stage for the entire document, defining its parameters and the commitment to data security.
- Definitions: Provide clear, concise definitions for key terms such as "security incident," "data breach," "threat actor," "vulnerability," and "personally identifiable information (PII)." This ensures a common understanding across all stakeholders.
- Roles and Responsibilities: Delineate the specific duties and accountabilities of individuals and teams involved in incident response, including the incident response team (IRT) lead, technical specialists, legal counsel, HR, and public relations. This prevents confusion and ensures proper action.
- Incident Classification and Prioritization: Establish a system for classifying incidents based on their severity and impact (e.g., critical, high, medium, low). This guides the allocation of resources and determines the urgency of the response.
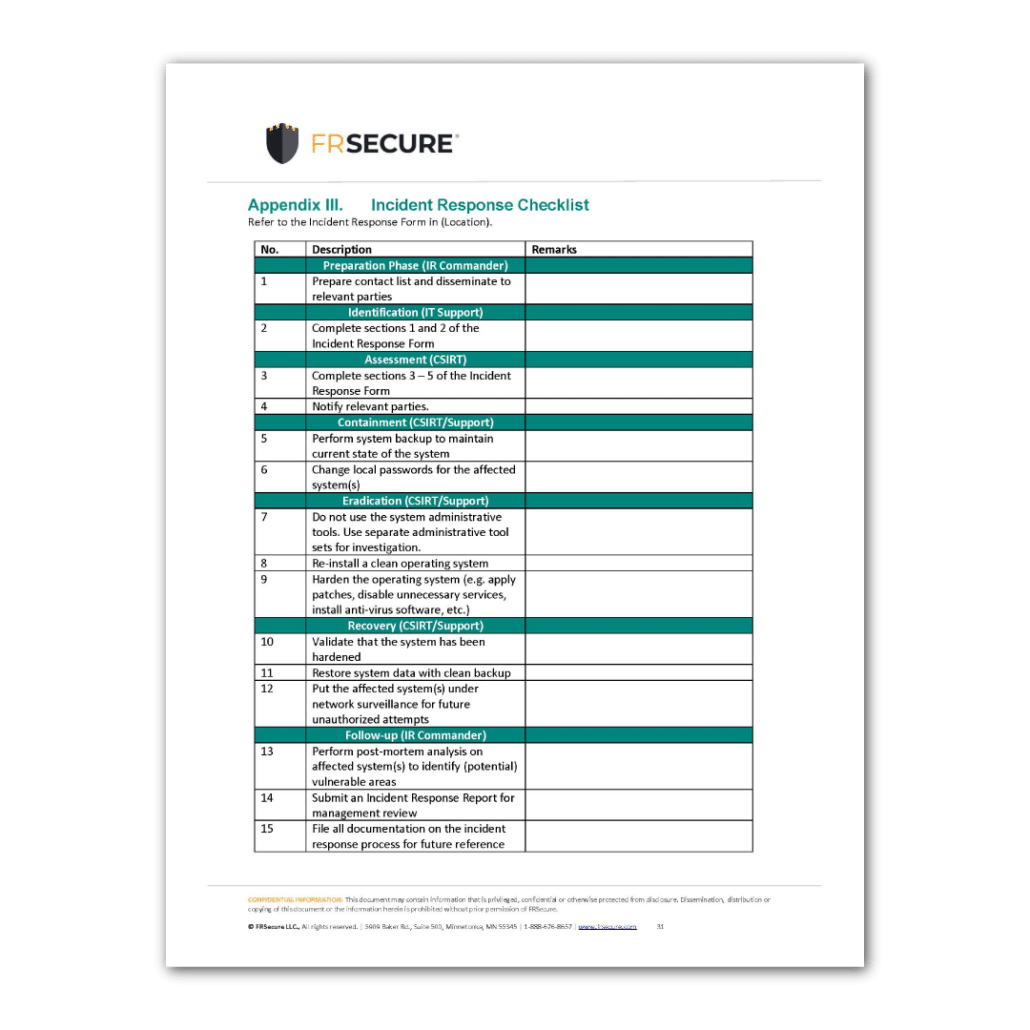
- Incident Response Lifecycle: Detail the phases of incident response, typically following a framework like NIST SP 800-61, which includes:
- Preparation: Activities before an incident, such as training, tool acquisition, and policy development.
- Detection and Analysis: Methods for identifying and understanding the scope and nature of an incident.
- Containment: Strategies to limit the damage and prevent further spread of the incident.
- Eradication: Steps to remove the root cause of the incident from affected systems.
- Recovery: Procedures to restore systems and data to normal operations.
- Post-Incident Activity: Lessons learned, policy updates, and forensic analysis.
- Communication Plan: Outline internal and external communication protocols. This includes who to notify internally (management, legal, HR), when and how to notify affected parties (customers, regulators), and coordination with public relations for media statements.
- Reporting Requirements: Specify what information must be documented for each incident, including timelines, actions taken, and the impact. This is crucial for compliance, post-incident analysis, and potential legal proceedings.
- Training and Awareness: Describe ongoing training programs for employees on security awareness and their role in incident reporting, reinforcing workplace rules related to information security.
- Policy Review and Update: Mandate regular reviews and updates of the Security Incident Response Policy Template to ensure it remains current with evolving threats, technologies, and regulatory requirements. This ensures the policy remains an effective, living document.
- Legal and Regulatory Compliance: Clearly state the legal obligations and regulatory requirements the policy aims to meet (e.g., HIPAA, GDPR, CCPA, PCI DSS), ensuring the organization adheres to all relevant governance frameworks and compliance standards.
Tips for Design, Usability, and Implementation of Your Security Incident Response Policy
Developing a robust Security Incident Response Policy Template is only half the battle; its effectiveness hinges on its design, usability, and successful implementation. A policy, no matter how comprehensive, is useless if it’s difficult to understand or inaccessible when needed most.
For design, focus on clarity and conciseness. Use plain language, avoiding overly technical jargon where possible, or provide a glossary of terms. Employ a logical structure with clear headings (like those used here) and subheadings to guide the reader. Bullet points and numbered lists, as demonstrated in the previous section, are excellent for breaking down complex information into digestible parts. Incorporate flowcharts or diagrams for processes like incident classification or communication workflows, as these visual aids can convey information much faster than text alone.
Regarding usability, ensure the policy is easily accessible to all relevant personnel. Digital versions, ideally stored in a secure, centralized location like a company intranet or document management system, are crucial for quick searching and dissemination. Consider providing both a comprehensive main document and condensed "cheat sheets" or quick reference guides for front-line staff who need immediate instructions. The policy should be searchable, allowing users to quickly find specific procedures or contact information during a crisis.
Implementation involves more than just publishing the document. It requires active engagement and integration into organizational culture. Conduct regular training sessions for all employees, emphasizing their role in detecting and reporting incidents. For the incident response team, conduct frequent drills and simulations to test the policy’s effectiveness under realistic conditions. Integrate the policy with existing IT service management (ITSM) tools and processes to streamline incident logging, tracking, and resolution. Finally, designate a clear owner for the policy who is responsible for its regular review, updates, and overall enforcement, ensuring it remains current and effective against evolving cyber threats and changing organizational needs.
In a world where cyberattacks are an increasingly common occurrence, a well-defined and rigorously implemented Security Incident Response Policy Template is no longer a luxury, but a fundamental component of good business practice. It serves as your organization’s digital fire escape plan, ensuring that when an incident inevitably strikes, you are not caught unprepared. By systematically approaching incident management, you protect not just your data and systems, but also your reputation, financial stability, and the trust of your customers and stakeholders.
Embracing a comprehensive Security Incident Response Policy Template signifies a proactive commitment to data security and operational resilience. It’s an investment that pays dividends by minimizing the impact of potential threats, ensuring regulatory compliance, and fostering a culture of preparedness. Start today by reviewing your current security posture and considering how a tailored incident response framework can fortify your defenses and safeguard your future in the ever-evolving digital landscape.


