In today’s interconnected business landscape, the reliance on third-party vendors is not just a convenience—it’s a fundamental operational reality. From cloud computing providers storing sensitive data to logistical partners managing supply chains, external entities play a pivotal role in the daily functioning of virtually every organization. This expansive network, while offering agility and specialized expertise, simultaneously introduces a myriad of risks that, if left unmanaged, can lead to severe financial, reputational, and operational consequences.
Navigating this complex web of partnerships requires more than just good intentions or ad-hoc practices; it demands a structured, proactive, and comprehensive approach. This is precisely where a robust Vendor Risk Management Policy Template becomes indispensable. It serves as the bedrock for establishing clear guidelines, responsibilities, and processes to identify, assess, mitigate, and monitor the risks associated with engaging third-party vendors. Organizations of all sizes, across every industry, from nascent startups to established enterprises, will find immense value in leveraging such a template to fortify their defenses and ensure business continuity.
Why a Vendor Risk Management Policy Template is Essential in Today’s Context
The digital age has ushered in an era of unprecedented data breaches, supply chain disruptions, and increasingly stringent regulatory demands. The headlines are replete with stories of companies facing massive fines, reputational damage, and loss of customer trust due to vulnerabilities introduced by their vendors. These incidents underscore the critical need for a formalized approach to third-party risk. A well-crafted Vendor Risk Management Policy Template provides that much-needed framework.
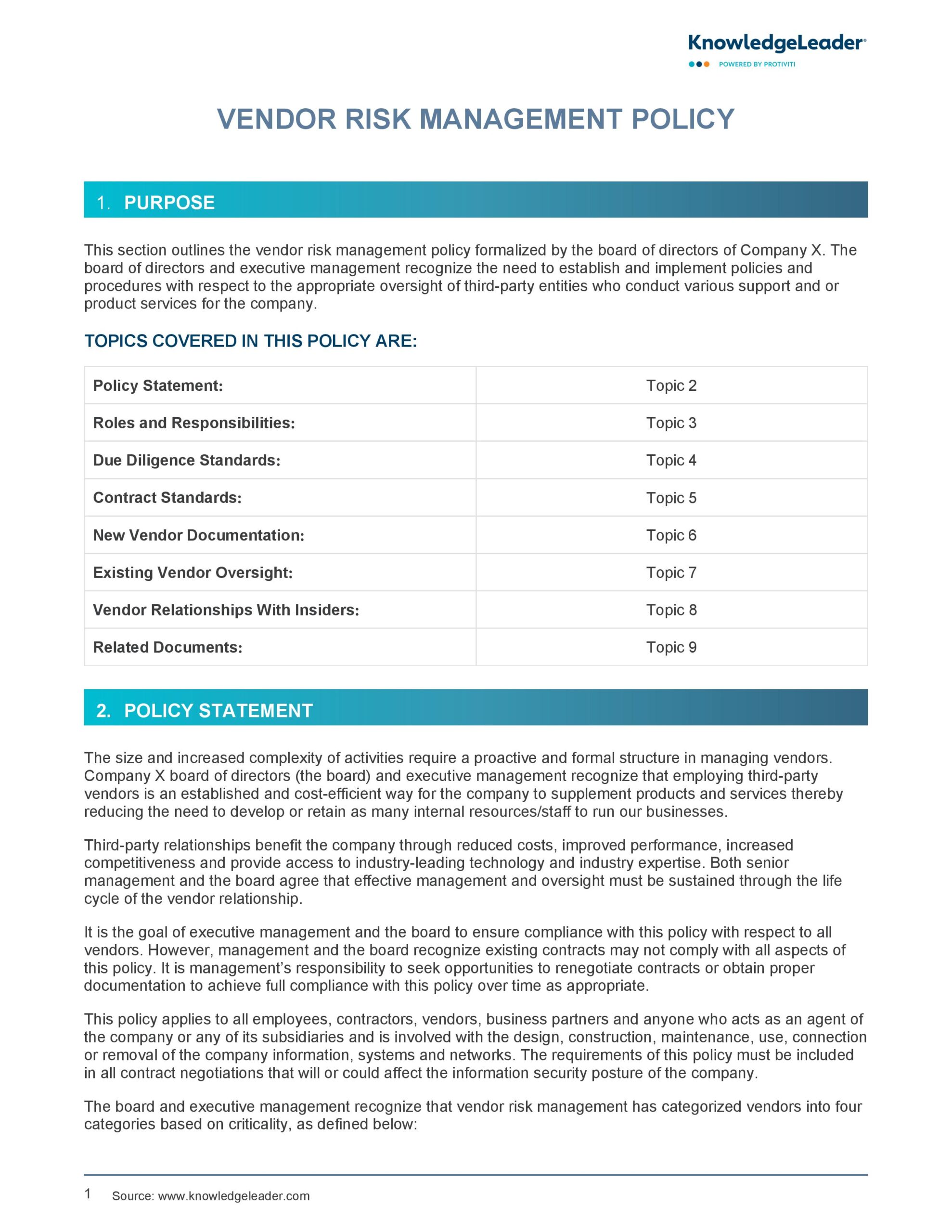
Without a clear policy, organizations often find themselves in a reactive mode, scrambling to address issues only after they’ve escalated. This leads to inefficient resource allocation, inconsistent risk assessments, and significant gaps in control. The regulatory landscape is also continuously evolving, with laws like GDPR, CCPA, HIPAA, and various industry-specific compliance requirements placing a direct onus on organizations for their vendors’ actions. A Vendor Risk Management Policy Template helps ensure that your organization remains compliant and can demonstrate due diligence when scrutinized by auditors or regulators.
Beyond compliance, the sheer volume and complexity of modern vendor relationships necessitate a standardized approach. From onboarding new vendors to managing ongoing performance and eventual offboarding, each stage carries inherent risks. A comprehensive Vendor Risk Management Policy Template ensures that these risks are systematically addressed, promoting operational resilience and safeguarding your core business interests against external threats.
Key Benefits of Using a Vendor Risk Management Policy Template
Adopting a Vendor Risk Management Policy Template offers a multitude of tangible and intangible benefits that extend across an organization’s operations. It transforms a potentially chaotic and inconsistent process into a streamlined, predictable, and defensible system.
Firstly, it significantly enhances compliance assurance. By embedding regulatory requirements and industry best practices directly into your processes, a well-defined Vendor Risk Management Policy Template helps ensure that all vendor engagements meet necessary legal and contractual obligations. This proactive stance can dramatically reduce the likelihood of regulatory fines and legal challenges.
Secondly, it leads to improved decision-making. With clear guidelines for risk assessment and due diligence, decision-makers have better information to evaluate potential vendor partners. This means making informed choices that align with the company’s risk appetite and strategic objectives, avoiding costly mistakes from the outset.
Thirdly, operational efficiency is greatly enhanced. A standardized Vendor Risk Management Policy Template streamlines the vendor lifecycle, from initial selection and contracting to performance monitoring and termination. This reduces redundant efforts, clarifies responsibilities, and minimizes delays, allowing teams to focus on core business activities rather than reinventing risk processes for each vendor.
Furthermore, leveraging a robust Vendor Risk Management Policy Template fosters stronger vendor relationships. When expectations, obligations, and performance metrics are clearly defined and communicated from the start, it builds a foundation of transparency and trust. This clarity often leads to more productive partnerships and better service delivery, as vendors understand what is expected of them and how their performance will be measured.
Finally, and perhaps most critically, it significantly bolsters data security and overall risk posture. By mandating rigorous security assessments, data privacy agreements, and incident response planning within the policy, an organization can proactively identify and mitigate vulnerabilities that could expose sensitive information or disrupt critical operations. This protective layer is invaluable in the face of persistent cyber threats.
How a Vendor Risk Management Policy Template Can Be Customized or Adapted to Different Needs
While a Vendor Risk Management Policy Template provides an excellent starting point, its true value lies in its adaptability. No two organizations are exactly alike, and neither are their vendor ecosystems or risk appetites. Therefore, the template must be flexible enough to be tailored to specific organizational contexts, industry nuances, and evolving business requirements.
For instance, a small startup might need a more streamlined Vendor Risk Management Policy Template compared to a large financial institution. The startup might prioritize essential data security and compliance basics, while the financial institution will require extensive sections on regulatory compliance (e.g., SOX, GLBA), business continuity, and highly detailed service level agreements (SLAs). The complexity of third-party contracts and obligations will vary greatly.
Industry-specific adaptations are also crucial. A healthcare provider’s Vendor Risk Management Policy Template will place a heavy emphasis on HIPAA compliance, patient data privacy, and strict access controls for any vendor handling protected health information (PHI). Conversely, a manufacturing company’s template might focus more on supply chain resilience, ethical sourcing, quality control, and environmental impact assessments.
Furthermore, the types of vendors an organization engages with will influence customization. A Vendor Risk Management Policy Template designed for IT service providers might delve deep into cloud security, software vulnerabilities, and data encryption. One for a marketing agency, however, might focus more on brand reputation, intellectual property rights, and adherence to advertising standards. Organizations can adapt sections to address specific risk categories like operational risk, financial risk, reputational risk, and strategic risk, aligning the policy with their enterprise risk management framework. The key is to see the Vendor Risk Management Policy Template not as a rigid dictate, but as a living document that can be scaled and refined over time to meet specific and changing organizational needs.
Important Elements or Fields That Should Be Included in a Vendor Risk Management Policy Template
A comprehensive Vendor Risk Management Policy Template should cover all stages of the vendor lifecycle and address various aspects of risk. While the specifics can be customized, certain core elements are non-negotiable for an effective policy.
- **Policy Statement and Purpose:** Clearly articulate the policy’s objective, its scope (what vendors/relationships it covers), and the organization’s commitment to effective vendor risk management.
- **Roles and Responsibilities:** Define who is accountable for what, including the board, senior management, risk management teams, legal, procurement, IT, and individual business units. Clarify ownership for risk assessments, due diligence, and ongoing monitoring.
- **Vendor Categorization and Tiering:** Establish a methodology for classifying vendors based on the criticality of their service and the level of risk they introduce (e.g., critical, high, moderate, low). This informs the depth of due diligence and ongoing oversight.
- **Risk Assessment Methodology:** Detail the process for identifying, assessing, and analyzing vendor risks. This should include criteria for evaluating data security, financial stability, operational resilience, compliance with laws and regulations, and reputation.
- **Due Diligence Procedures:** Outline the steps involved in vetting prospective vendors, including background checks, financial reviews, security questionnaires, on-site audits, and review of certifications (e.g., ISO 27001, SOC 2). Emphasize the importance of thoroughly reviewing their obligations and legal terms.
- **Contractual Requirements:** Specify essential clauses that must be included in vendor agreements, such as data privacy protections, service level agreements (SLAs), right-to-audit clauses, insurance requirements, incident reporting protocols, and clear termination clauses. These form the basis of the contractual relationship.
- **Ongoing Monitoring and Performance Management:** Describe how vendor performance and risk posture will be continuously monitored. This includes periodic risk assessments, performance reviews, security posture evaluations, and ensuring compliance with contract terms and regulatory requirements.
- **Incident Response and Business Continuity:** Establish protocols for how vendor-related incidents (e.g., data breaches, service outages) will be reported, managed, and resolved. Include requirements for vendors’ business continuity and disaster recovery plans.
- **Vendor Offboarding and Exit Strategy:** Detail procedures for the orderly termination of vendor relationships, including data retrieval/destruction, access revocation, return of assets, and ensuring continuity of services.
- **Training and Awareness:** Require periodic training for employees involved in vendor management to ensure they understand the policy and their responsibilities.
- **Policy Review and Updates:** Specify how often the Vendor Risk Management Policy Template itself will be reviewed and updated to reflect changes in the regulatory landscape, organizational risk appetite, or business operations.
- **Documentation and Record Keeping:** Emphasize the importance of maintaining comprehensive records of all vendor risk management activities, including assessments, contracts, and monitoring reports.
Tips on Design, Usability, or Implementation
Creating a comprehensive Vendor Risk Management Policy Template is one thing; ensuring it’s actually used and effective is another. Thoughtful design, usability, and a strategic implementation approach are paramount.
For usability, prioritize clarity and conciseness. Avoid overly technical jargon where plain language will suffice. Use headings, subheadings, bullet points, and numbered lists to break up dense text, making the document easy to scan and digest. A table of contents with hyperlinks (for digital versions) can greatly enhance navigation. Ensure that definitions of key terms are readily available, perhaps in an appendix or glossary.
When it comes to design, whether for print or digital, consistency is key. Use your organization’s branding guidelines (logos, colors, fonts) to make the document professional and recognizable. For a print version, consider a clean layout with ample white space. For a digital Vendor Risk Management Policy Template, ensure it’s accessible across different devices and platforms. PDF is a common format, but consider an interactive web-based version if your organization has the resources, allowing for easier updates and searchability.
Implementation strategies should focus on integration and communication. Don’t just publish the Vendor Risk Management Policy Template and expect magic. Integrate the policy requirements into existing procurement, legal, and IT processes. Develop clear workflows and assign specific ownership for each step. Provide mandatory training sessions for all relevant stakeholders, explaining the "why" behind the policy, not just the "what." This fosters understanding and buy-in. Regularly communicate updates and provide refresher training as needed. Also, consider developing supplementary guides or checklists that condense complex sections of the Vendor Risk Management Policy Template into actionable steps for day-to-day use.
A well-designed and implemented Vendor Risk Management Policy Template isn’t just a document; it’s a living tool that empowers your teams to manage third-party risks effectively, protect your organization, and ensure operational resilience.
In an era where interconnectedness defines the modern business world, the proactive management of vendor risks is no longer optional; it’s a strategic imperative. A robust Vendor Risk Management Policy Template serves as the essential blueprint for building a resilient, secure, and compliant organization. It’s the foundational document that guides every decision, from initial vendor selection to ongoing performance review and eventual offboarding, ensuring that every third-party engagement aligns with your organization’s values and risk tolerance.
By adopting, customizing, and diligently implementing such a policy, organizations can transform potential vulnerabilities into controlled, manageable elements of their operational landscape. It’s an investment in your organization’s future, safeguarding its reputation, financial health, and customer trust. Consider leveraging a comprehensive Vendor Risk Management Policy Template not merely as a compliance checklist, but as a dynamic tool to foster stronger, more secure, and ultimately more successful external partnerships.


