In the rapidly evolving digital landscape, where cyber threats loom large and regulatory demands grow ever more stringent, maintaining a stable and secure IT infrastructure is paramount. Organizations grapple daily with the complexities of managing countless systems, applications, and configurations, where a single misstep can lead to catastrophic data breaches, operational downtime, or compliance penalties. This intricate challenge is precisely why robust configuration management is not merely a technical task, but a strategic imperative.
To navigate this complexity effectively, organizations need a clear, actionable framework. Enter the Configuration Management Policy Template Nist – a powerful tool that offers a structured approach to defining, documenting, and enforcing how system configurations are managed across an enterprise. By leveraging the esteemed guidance of the National Institute of Standards and Technology (NIST), this template provides a gold standard for establishing consistent, secure, and resilient IT environments. It’s an indispensable resource for IT managers, cybersecurity professionals, compliance officers, and anyone responsible for maintaining the integrity and security of digital assets.
Why a Configuration Management Policy Template Nist is Essential Today
The modern IT ecosystem is a dynamic, interconnected web of servers, networks, applications, and cloud services. Without a well-defined Configuration Management Policy Template Nist, this environment can quickly descend into chaos, leading to inconsistencies, vulnerabilities, and an inability to meet critical operational and security objectives. The stakes are simply too high to leave configuration management to chance.
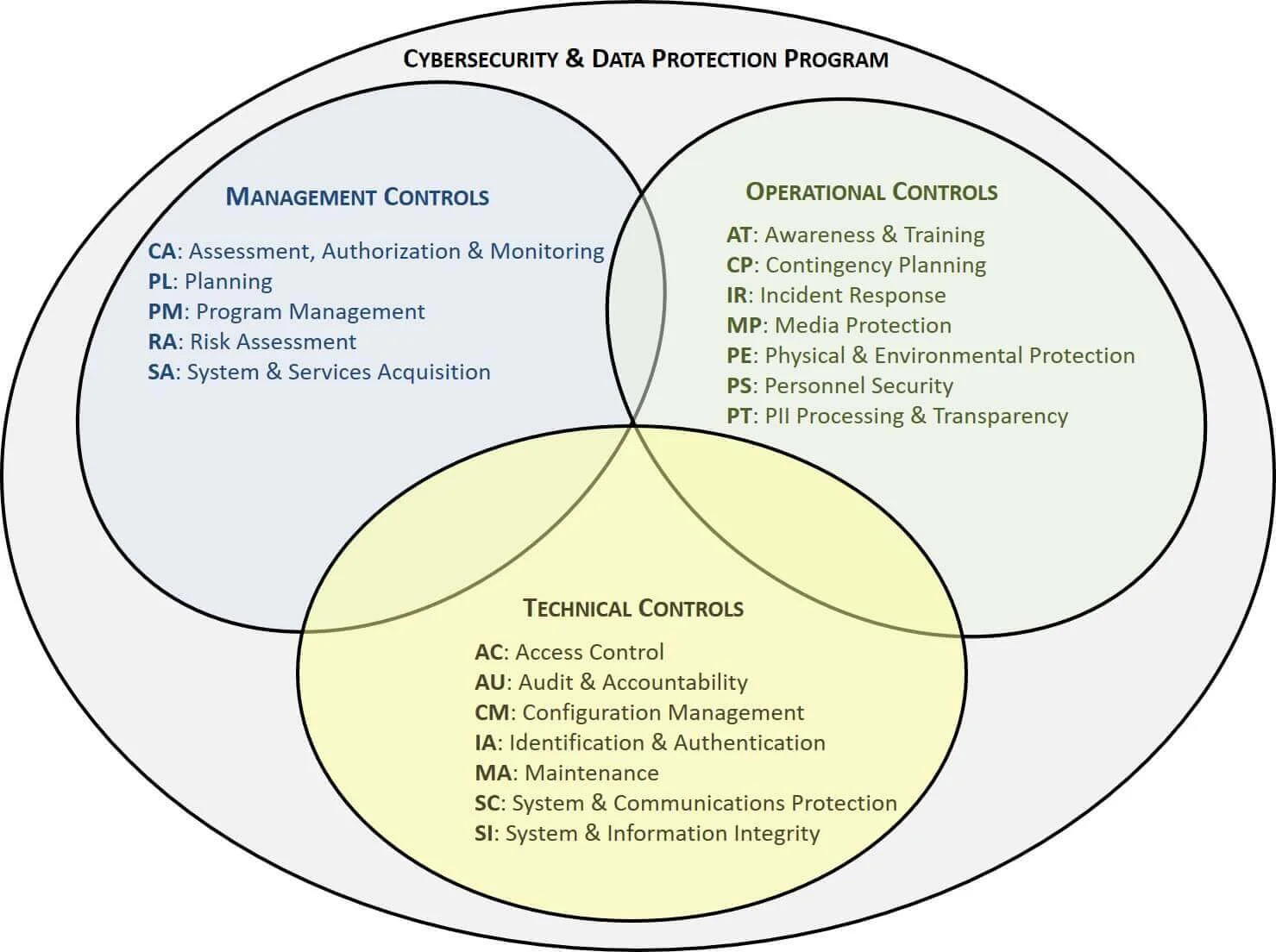
One of the most compelling reasons for its essentiality lies in cybersecurity. Misconfigurations are consistently cited as a leading cause of data breaches and security incidents. A clear Configuration Management Policy Template Nist, rooted in NIST’s security controls, ensures that systems are hardened from the outset, reducing the attack surface and proactively mitigating risks. It establishes a baseline of security that all systems must adhere to, making it significantly harder for malicious actors to exploit weaknesses.
Furthermore, compliance with various regulatory frameworks – such as HIPAA, PCI DSS, SOC 2, GDPR, and the Department of Defense’s CMMC – often mandates rigorous configuration management practices. Auditors frequently scrutinize an organization’s ability to demonstrate control over its IT configurations. A well-articulated Configuration Management Policy Template Nist provides the necessary documentation and procedural clarity to prove adherence to these requirements, streamlining audit processes and avoiding costly fines or reputational damage. It ensures that an organization can confidently show its commitment to IT governance and data security.
Key Benefits of Using a Configuration Management Policy Template Nist
Adopting a comprehensive Configuration Management Policy Template Nist offers a multitude of tangible benefits that extend beyond mere compliance, touching upon operational efficiency, risk reduction, and strategic alignment. These advantages contribute significantly to an organization’s overall resilience and ability to thrive in a competitive landscape.
Firstly, it fosters standardization and consistency. By defining a uniform approach to configuration management, the policy ensures that all systems, whether on-premise or in the cloud, adhere to the same established baselines. This consistency drastically reduces configuration drift, minimizes human error, and simplifies troubleshooting, leading to a more predictable and stable IT environment.
Secondly, it leads to enhanced security posture. A NIST-aligned Configuration Management Policy Template Nist inherently incorporates best practices for security hardening. This means stronger passwords, disabled unnecessary services, up-to-date patches, and secure default configurations, all of which work in concert to significantly reduce vulnerabilities and protect against cyber threats. It’s a proactive defense mechanism against the constantly evolving threat landscape.
Thirdly, organizations experience improved audit readiness and compliance. With clearly documented processes and established configuration baselines, demonstrating adherence to regulatory requirements becomes far easier. The policy acts as a central reference point for auditors, proving that an organization has a systematic approach to managing its IT configurations and is committed to meeting its legal and contractual obligations for data security.
Finally, it drives operational efficiency and reduces downtime. By standardizing configurations and establishing clear change management procedures, the likelihood of configuration-related outages decreases. When incidents do occur, having documented "known good" configurations enables faster diagnosis and recovery, minimizing disruption to business operations and associated costs. This focus on stable configurations contributes to greater reliability and productivity across the enterprise.
Customizing and Adapting Your Configuration Management Policy Template Nist
While a Configuration Management Policy Template Nist provides an excellent foundation, it’s crucial to remember that NIST frameworks are designed to be adaptable, not prescriptive. A "one-size-fits-all" approach rarely works in the diverse world of IT. Therefore, tailoring the template to fit your organization’s unique context, risk appetite, and operational realities is not just recommended, but essential for its effectiveness.
Consider your organization’s size, industry, and the specific regulatory landscape it operates within. A small startup might have different needs than a large financial institution, even if both strive for strong data security. The template should be adapted to reflect the scale of your operations, the sensitivity of the data you handle, and the specific compliance requirements you face (e.g., healthcare organizations will emphasize HIPAA controls, while government contractors will focus on CMMC).
Furthermore, evaluate your existing IT infrastructure and technology stack. Are you predominantly cloud-based, hybrid, or entirely on-premises? Do you use specific configuration management tools like Ansible, Puppet, or Chef? The policy needs to integrate seamlessly with your current tools and processes, outlining how they will be used to enforce the defined configurations. Customization might involve adding specific annexes for different departments, outlining variations for legacy systems, or specifying unique requirements for critical business applications.
The key is to use the Configuration Management Policy Template Nist as a robust starting point, identifying the core NIST controls that apply, and then expanding or contracting them as necessary. This ensures that the policy is not just a document sitting on a shelf, but a living, breathing guide that genuinely supports your organization’s security posture and operational objectives, making it truly your own.
Important Elements for Your Configuration Management Policy Template Nist
A truly effective Configuration Management Policy Template Nist must encompass a range of critical elements to ensure comprehensive coverage and clarity. These components define the scope, responsibilities, and procedures necessary to manage configurations systematically and securely.
Here are the important elements that should be included:
- Policy Statement: A clear, concise statement outlining the organization’s commitment to configuration management, its objectives (e.g., security, compliance, operational stability), and its alignment with NIST guidelines.
- Scope: Define what systems, applications, data, infrastructure components (e.g., network devices, servers, workstations), and personnel are covered by the policy. Specify any exclusions.
- Roles and Responsibilities: Clearly delineate who is responsible for what aspects of configuration management. This includes system owners, configuration managers, security officers, change approvers, implementers, and auditors.
- Baseline Configuration Management: Establish processes for defining, documenting, approving, and maintaining secure and functional baseline configurations for all covered systems and applications. This includes security baselines and hardening guides.
- Configuration Item Identification (CI): Detail how configuration items will be identified, tracked, and uniquely named. This might involve an asset management system or configuration management database (CMDB).
- Change Management Process: Outline the procedures for requesting, reviewing, approving, testing, implementing, and documenting all changes to approved configurations. Emphasize the need for proper authorization and rollback plans.
- Configuration Control: Specify mechanisms for preventing unauthorized changes and ensuring that only approved modifications are applied to systems. This often involves version control for software and configuration files.
- Configuration Monitoring and Auditing: Describe how configurations will be regularly monitored for drift from baselines, unauthorized changes, and compliance with policy. Include procedures for periodic security audits and vulnerability assessments.
- Configuration Reporting: Define requirements for generating reports on configuration status, changes, and compliance. This supports audit readiness and decision-making.
- Training and Awareness: Address the need for educating personnel on configuration management policies, procedures, and their individual responsibilities.
- Tooling and Automation: Identify the configuration management tools (e.g., SCCM, InTune, Ansible, Puppet, Chef, SaltStack) and automation platforms used to enforce, monitor, and manage configurations.
- Policy Review and Update Cycle: Establish a schedule and process for reviewing and updating the Configuration Management Policy Template Nist to ensure its continued relevance and effectiveness in response to evolving threats, technologies, and regulatory requirements.
- Compliance Requirements: Explicitly link the policy to specific regulatory, legal, and contractual obligations (e.g., HIPAA, CMMC, ISO 27001) that it helps the organization meet.
Tips on Design, Usability, and Implementation
Crafting a robust Configuration Management Policy Template Nist is only half the battle; ensuring its practical application and effectiveness across the organization is the ultimate goal. Thoughtful design, usability, and a strategic implementation approach can make all the difference.
When designing your policy, prioritize clarity and conciseness. Avoid overly technical jargon where plain language will suffice, and structure the document logically with clear headings and short paragraphs (2-4 sentences max). This enhances readability and ensures that all stakeholders, from technical staff to executive leadership, can understand their roles and the policy’s intent. For digital dissemination, ensure the document is easily searchable and accessible, perhaps as a PDF on an internal portal or integrated into an organizational wiki. Version control is also paramount for tracking changes over time.
For usability, consider how the policy will be referenced in day-to-day operations. It shouldn’t be a document that sits forgotten. Link it to relevant standard operating procedures (SOPs), technical guides, and your change management system. Provide practical examples where possible to illustrate complex concepts. Integrate it with your incident response plan and disaster recovery strategies, highlighting how stable configurations contribute to faster restoration efforts. The policy should feel like a living guide, not a static compliance artifact.
Implementation requires a multi-faceted approach. Start with executive buy-in; leadership endorsement is crucial for driving adoption and allocating necessary resources. Roll out the policy with comprehensive training and awareness programs for all relevant personnel. Emphasize not just what the policy states, but why it matters – linking it to security, compliance, and operational stability. Leverage automation tools to enforce configurations wherever possible, reducing manual effort and human error. Begin with a pilot program or focus on high-priority systems, iteratively expanding the policy’s reach as you gain experience and refine processes. Regularly review and update the Configuration Management Policy Template Nist to reflect changes in technology, threats, and organizational structure, ensuring it remains a relevant and effective control mechanism.
In an era defined by constant digital transformation and escalating cyber threats, the strategic importance of well-executed configuration management cannot be overstated. It stands as a foundational pillar for cybersecurity, operational resilience, and unwavering compliance. By adopting and diligently applying a Configuration Management Policy Template Nist, organizations gain a clear, structured roadmap to achieve these critical objectives, transforming potential chaos into controlled, secure stability.
This template, grounded in the proven expertise of NIST, offers more than just guidelines; it provides a framework for building a culture of meticulousness and security within your IT operations. It empowers teams to standardize configurations, minimize vulnerabilities, and respond effectively to change, ensuring that every system operates from a known, trusted state. Embracing this disciplined approach is not merely about meeting minimum requirements, but about cultivating an environment where innovation can thrive securely.
Therefore, for any organization committed to safeguarding its digital assets, maintaining operational integrity, and navigating the complex landscape of regulatory compliance, a robust Configuration Management Policy Template Nist is not just an option—it is an indispensable strategic investment. Consider integrating this practical solution into your IT governance framework today, setting the stage for a more secure, efficient, and resilient future.


