In today’s hyper-connected business world, the line between professional and personal use of technology can often blur. Employees rely on computers, the internet, and a vast array of digital tools to perform their daily tasks, access company resources, and communicate with colleagues and clients. While this digital dependency fuels efficiency and innovation, it also introduces a complex landscape of potential risks, from data breaches and productivity drains to legal liabilities and compliance challenges.
This is precisely where an Employee Computer Use Policy Template becomes an indispensable asset for any organization. It’s not just a dry, legalistic document; rather, it’s a foundational blueprint for establishing clear expectations, safeguarding critical assets, and fostering a secure, productive digital environment for everyone. Whether you’re a burgeoning startup, a growing small business, or an established enterprise, understanding and implementing such a policy is no longer optional—it’s a strategic necessity that protects your business, your data, and your people.
Why an Employee Computer Use Policy Template is Essential
The modern workplace is increasingly digital, mobile, and remote, making a well-defined Employee Computer Use Policy Template more critical than ever. Without clear guidelines, businesses expose themselves to a myriad of risks that can have severe financial, reputational, and legal consequences. This template serves as a proactive measure, laying out the ground rules for acceptable conduct and technological engagement.
One primary reason for its importance is compliance. Various regulations, from data privacy laws like HIPAA or GDPR (though written for US readers, global data touches US businesses) to industry-specific standards, mandate how organizations handle sensitive information. A robust policy helps ensure your team adheres to these legal obligations, reducing the likelihood of costly fines or legal action. It acts as a clear set of workplace rules, giving employees unambiguous instructions on how to handle company assets and data.
Beyond compliance, an Employee Computer Use Policy Template is crucial for data security. Cyber threats are constant, and human error is often the weakest link. By outlining protocols for password strength, data storage, acceptable software installations, and recognizing phishing attempts, the policy significantly strengthens your organization’s defense against cyberattacks, malware, and unauthorized data access. It mitigates the risk of intellectual property theft and ensures the confidentiality of proprietary information.
Furthermore, it plays a vital role in maintaining productivity and preventing misuse of resources. While some personal use might be tolerated, excessive recreational browsing, social media activity, or streaming can severely impact bandwidth and employee focus. The policy sets boundaries, allowing employees to understand what is considered appropriate and inappropriate use of company time and equipment, thereby safeguarding efficiency. It also provides a framework for addressing potential issues, ensuring consistent application of consequences.
Key Benefits of Using an Employee Computer Use Policy Template
Adopting an Employee Computer Use Policy Template offers a multitude of tangible benefits that extend across various facets of your business operations. It’s a proactive step that pays dividends in terms of security, efficiency, and employee relations. These advantages underscore why such a template should be a cornerstone of your HR and IT strategies.
Firstly, it provides unambiguous clarity and consistent expectations. Employees know exactly what is expected of them regarding computer and internet use, eliminating guesswork and potential misunderstandings. This clarity fosters a more professional environment and ensures that all team members are on the same page regarding acceptable conduct, obligations, and the responsible use of company resources.
Secondly, an Employee Computer Use Policy Template offers significant legal protection and risk mitigation. In the event of an employee misusing company systems, causing a data breach, or engaging in inappropriate online behavior, a signed policy can serve as crucial evidence that the employee was informed of the rules and potential consequences. This legal backing is invaluable in defending against lawsuits, unemployment claims, or regulatory inquiries, proving that the company took reasonable steps to prevent such incidents. It’s a critical component of any strong HR framework and legal terms for employment.
Thirdly, it directly enhances data security and confidentiality. By clearly outlining procedures for handling sensitive information, creating strong passwords, and avoiding suspicious downloads, the policy acts as a continuous reminder for employees to prioritize security. This collective adherence to best practices dramatically reduces the risk of data breaches, malware infections, and the unauthorized disclosure of confidential business information. It solidifies your data protection strategy.
Finally, the template contributes to improved productivity and resource management. By establishing guidelines on acceptable internet and software use, it helps minimize distractions and ensures that company computing resources are primarily utilized for business-related tasks. This leads to a more focused workforce and optimized use of valuable network bandwidth and computing power, ultimately driving greater operational efficiency.
Customizing Your Employee Computer Use Policy Template
While an Employee Computer Use Policy Template provides an excellent starting point, its true value lies in its adaptability. No two businesses are exactly alike; they differ in size, industry, corporate culture, and the specific technologies they employ. Therefore, customizing the template to reflect your organization’s unique needs and circumstances is paramount for its effectiveness and successful implementation.
Consider the nature of your industry. A technology firm dealing with proprietary software development will have different security requirements and acceptable use parameters than a retail chain or a healthcare provider. For instance, a medical office will need to incorporate specific HIPAA compliance measures directly into its policy regarding patient data access and handling, going beyond generic data security clauses. Your workplace rules must align with industry standards and legal terms.
Company size and structure also play a significant role. A small startup with limited IT resources might opt for a simpler, more concise policy, while a large enterprise with multiple departments and global operations will require a more comprehensive document addressing various user roles, remote access policies, and potentially region-specific regulations. The template should be scalable, allowing you to add or remove sections as your business grows or evolves.
Furthermore, think about your specific technologies and tools. Do your employees primarily use company-issued laptops, or do you have a Bring Your Own Device (BYOD) policy? Are certain cloud-based applications central to your operations? Your policy should address these specifics, outlining acceptable use for each platform, data storage guidelines, and security protocols relevant to your technological ecosystem. For example, if your company heavily relies on a specific SaaS solution, your policy might include specific provisions about its authorized use.
Finally, your company culture should subtly influence the tone and emphasis of your customized policy. While maintaining a professional and authoritative stance, you can tailor the language to resonate with your workforce, making it feel less like a restrictive contract and more like a guiding document designed for mutual benefit. The goal is to create a robust framework that supports your business objectives while being understood and respected by your employees.
Important Elements to Include in Your Employee Computer Use Policy Template
A truly effective Employee Computer Use Policy Template must be comprehensive, covering all critical aspects of digital conduct and resource management. When customizing your template, ensure these essential elements are thoroughly addressed to create a clear, enforceable, and protective document. These are the fundamental workplace rules that form the backbone of your digital governance strategy.
-
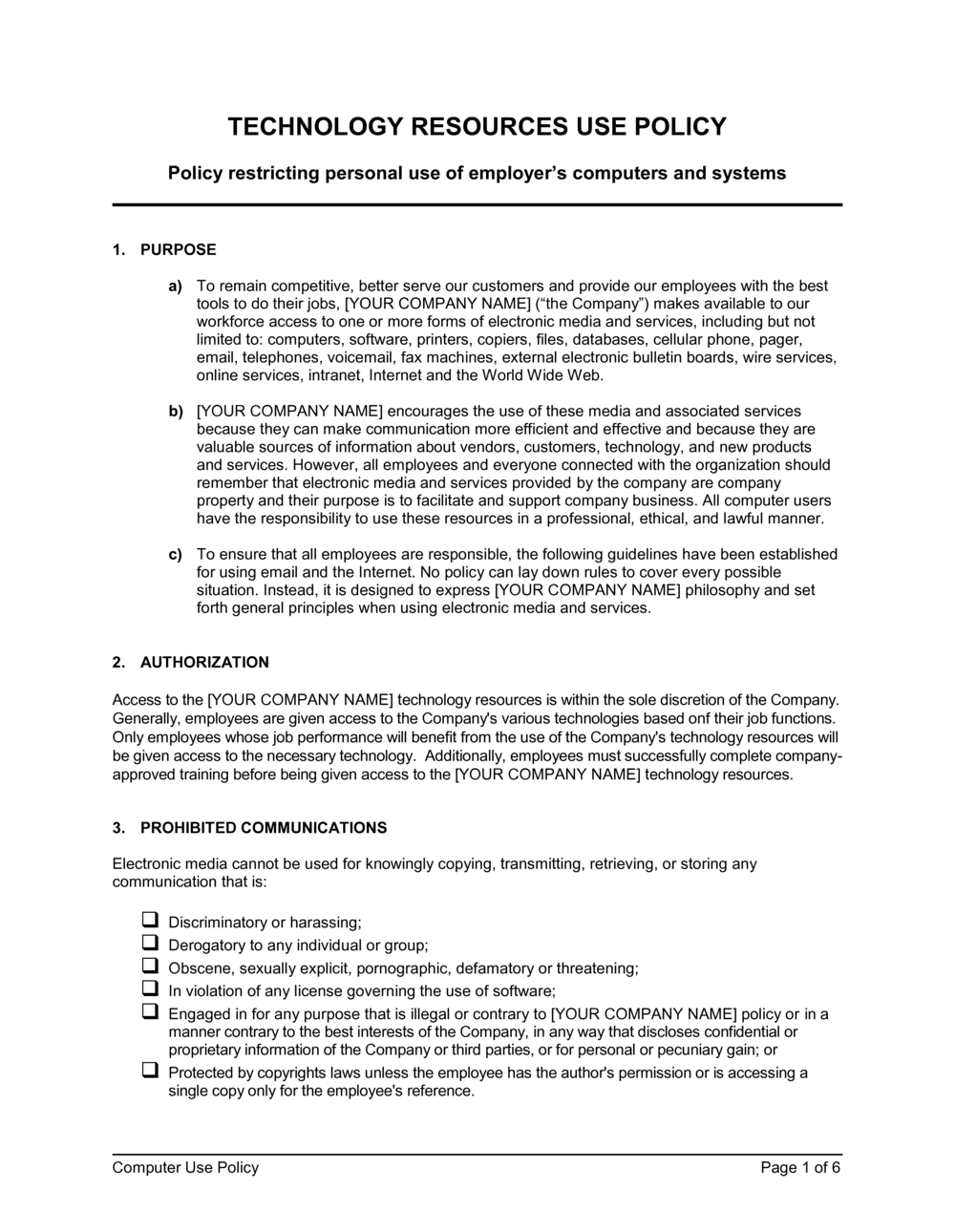
Purpose and Scope: Clearly state the policy’s objective (e.g., protect company assets, ensure productivity, mitigate risk) and whom it applies to (all employees, contractors, interns, etc., using company or personal devices for business).
-
Acceptable Use: Define what constitutes appropriate use of company computers, networks, software, and internet access. This might include using resources for job-related tasks, adhering to ethical standards, and maintaining professionalism.
-
Prohibited Use: Explicitly list activities that are strictly forbidden, such as accessing illegal content, harassment, unauthorized software installation, engaging in extensive personal use, gambling, or political campaigning on company time/equipment. This section outlines key obligations.
-
Privacy Expectations: Clarify that employees should have no expectation of privacy when using company equipment or networks. State that the company reserves the right to monitor usage for legitimate business purposes (e.g., security, productivity, legal compliance).
-
Security Measures: Outline requirements for password strength and confidentiality, use of antivirus software, avoiding suspicious links, reporting security incidents, and proper data storage and backup procedures. This is crucial for data security.
-
Data Ownership and Confidentiality: State that all data created or stored on company systems is the property of the company. Emphasize the importance of protecting confidential and proprietary information and the consequences of its unauthorized disclosure.
-
Software and Hardware Installation: Specify rules regarding installing personal software or hardware on company devices, typically prohibiting it without explicit IT department approval to prevent malware and compatibility issues.
-
Internet and Email Use: Detail guidelines for professional internet browsing and email communication, including restrictions on mass mailings, chain letters, and any content that could be considered offensive, harassing, or illegal. It sets clear legal terms for digital communication.
-
Social Media Use: If applicable, provide guidelines for professional conduct on social media, especially when discussing the company or its clients, distinguishing between personal and professional profiles, and prohibiting disparaging remarks.
-
Mobile Devices and BYOD Policy: Address the use of company-issued mobile devices and, if permitted, the rules for Bring Your Own Device (BYOD), including security requirements, data wiping policies, and acceptable usage outside the office.
-
Monitoring and Enforcement: Clearly state that the company monitors computer and network activity and reserves the right to review files and communications. Outline the disciplinary actions for policy violations, ranging from warnings to termination.
-
Employee Acknowledgment: Include a section requiring employees to read, understand, and sign the policy, confirming their agreement to abide by its terms. This signature is vital for legal enforceability, acting as a form of contract or agreement.
Tips for Design, Usability, and Implementation
Having a robust Employee Computer Use Policy Template is one thing; ensuring it’s actually read, understood, and adhered to is another. Effective design, usability, and a well-thought-out implementation strategy are crucial for turning your policy from a static document into a living guide that protects your organization.
First and foremost, focus on clarity and conciseness in your design. Avoid overly technical jargon or complex legalistic phrasing where simpler terms suffice. Use clear headings, short paragraphs, and bullet points to break up text and improve readability. A policy that is easy to understand is more likely to be followed. Think of it as an executive summary for your digital operations – it needs to be direct and to the point.
For usability, consider both print and digital formats. While a physical copy signed by the employee is essential for legal purposes (acting as a tangible agreement or contract), having the policy readily available digitally is equally important. Store it on your company intranet, shared drive, or HR portal where employees can easily access it for reference at any time. Make it searchable so employees can quickly find specific guidelines, turning it into a practical, everyday resource.
Implementation requires a multi-faceted approach. Don’t just hand out the policy and expect immediate compliance. Integrate the Employee Computer Use Policy Template into your onboarding process for new hires. During orientation, explain the policy’s importance, highlight key sections, and answer any questions. This initial education is critical for setting expectations from day one.
Beyond onboarding, regular communication and reminders are vital. Conduct periodic training sessions or send out internal communications to refresh employees’ understanding, especially when updates are made to the policy or new technologies are introduced. Encourage an open-door policy where employees feel comfortable asking questions about appropriate computer use. Finally, ensure your IT and HR departments are aligned on enforcement, applying the policy consistently and fairly across the board. This unified front reinforces the policy’s seriousness and validity as a core set of workplace rules.
Implementing an effective Employee Computer Use Policy Template is not merely a formality; it’s a strategic investment in your organization’s future. It serves as a clear declaration of your expectations, safeguarding your valuable data, promoting a culture of responsible digital citizenship, and protecting your business from the myriad risks inherent in our interconnected world. By providing clear guidelines, you empower your employees to make informed decisions, transforming potential vulnerabilities into strengths.
Embrace the proactive power of a well-crafted Employee Computer Use Policy Template. It offers peace of mind by establishing a robust framework that supports productivity, ensures compliance, and fortifies your cybersecurity posture. Don’t leave your digital environment to chance; equip your team with the clear direction they need to thrive securely and efficiently.