In today’s hyper-connected world, technology is the lifeblood of nearly every organization, from bustling startups to established enterprises and educational institutions. It empowers productivity, facilitates communication, and unlocks unprecedented opportunities. However, this indispensable tool also comes with inherent risks, ranging from data security breaches and intellectual property theft to misuse of company resources and potential legal liabilities. Without clear guidelines, the digital landscape can quickly become a minefield, impacting employee efficiency, organizational reputation, and bottom-line stability.
This is where a robust Technology Acceptable Use Policy (AUP) steps in as a critical line of defense. It’s more than just a set of rules; it’s a foundational agreement that defines the boundaries and expectations for how employees, contractors, and other authorized users interact with your organization’s digital assets. For anyone tasked with establishing clear workplace rules, managing IT resources, or ensuring compliance – be it an HR professional, an IT director, or a business owner – a well-crafted Technology Acceptable Use Policy Template offers an invaluable head start, providing a structured framework to protect your digital ecosystem.
Why a Technology Acceptable Use Policy Template is Essential
The rapid evolution of technology, coupled with the increasing complexity of cybersecurity threats, makes a comprehensive AUP not just good practice, but an absolute necessity. Organizations face an ever-present threat landscape, from sophisticated phishing attacks to insider threats, and a lack of clear guidelines can exacerbate these vulnerabilities. A Technology Acceptable Use Policy Template helps address these challenges head-on.
Firstly, it serves as a cornerstone for compliance. Many industries are subject to stringent regulatory requirements regarding data privacy and security. Without clearly defined workplace rules around technology use, organizations risk non-compliance with laws like HIPAA for healthcare data, or various state-level privacy statutes, potentially leading to hefty fines and reputational damage. An AUP outlines employee obligations, helping ensure adherence to these critical legal terms.
Secondly, it’s a powerful tool for risk mitigation. By setting clear expectations for how technology should and should not be used, you significantly reduce the likelihood of accidental data breaches, malware infections, and the unauthorized disclosure of sensitive information. This proactive approach to data security can save countless hours and resources that would otherwise be spent on incident response and recovery.
Finally, an AUP fosters a culture of responsibility and professionalism within the workplace. It clarifies what constitutes acceptable behavior, from internet browsing to email etiquette, helping to maintain productivity and prevent distractions. Employees understand their roles and responsibilities concerning company assets, contributing to a more secure and efficient operational environment.
Key Benefits of Using a Technology Acceptable Use Policy Template
Leveraging a pre-designed Technology Acceptable Use Policy Template provides a multitude of advantages that streamline the policy creation process and enhance organizational security and efficiency. It transforms a potentially daunting task into a manageable and strategic initiative.
One of the primary benefits is clarity and consistency. A template ensures that your policies are clearly articulated and uniformly applied across the organization. This removes ambiguity, allowing employees to understand their obligations regarding company technology and minimizing the chances of misinterpretation. Everyone operates under the same set of workplace rules, fostering fairness and reducing internal disputes.
Furthermore, a well-structured Technology Acceptable Use Policy Template significantly saves time and resources. Instead of building a policy from scratch, which can be a complex and time-consuming endeavor, you start with a robust framework. This allows your HR and IT teams to focus on customizing specific sections rather than developing the entire document, leading to greater efficiency and faster implementation.
The template also acts as a benchmark for security enhancement. It typically includes best practices for data security, password management, and device handling, drawing on common industry standards. By adopting such a template, you inherently raise your organization’s security posture, reducing vulnerabilities introduced by human error or lack of awareness.
Finally, a comprehensive AUP contributes to legal protection. In instances of policy violation, having clearly documented obligations and consequences provides a legal basis for disciplinary action. It demonstrates that the organization has taken reasonable steps to communicate its expectations and protect its assets, potentially reducing legal exposure in disputes.
Customizing Your Technology Acceptable Use Policy Template
While a Technology Acceptable Use Policy Template offers an excellent starting point, it’s crucial to recognize that no single policy fits every organization perfectly. Customization is not just recommended; it’s essential to ensure the policy genuinely reflects your specific needs, industry, and operational realities. Treating the template as a living document, rather than a rigid contract, is key to its long-term effectiveness.
The customization process should begin with a thorough assessment of your organization’s unique digital landscape. Consider the types of technology your employees use daily – are they company-issued laptops, personal mobile devices (BYOD), cloud-based software, or a mix of everything? Each scenario presents different challenges and requires tailored guidelines within your acceptable use policy. For instance, a policy for an organization heavy on intellectual property might have stricter rules about data transfer and external storage than a non-profit primarily using public-facing communication tools.
Your industry also plays a significant role. Businesses in regulated sectors, such as finance or healthcare, will need to integrate specific compliance requirements into their AUP. This might involve detailed sections on data encryption, access controls, and incident reporting procedures that go beyond a general template. Engaging legal counsel during this phase is highly advisable to ensure all specific legal terms and obligations are adequately addressed.
Finally, consider your organizational culture. While an AUP needs to be firm, it should also be reflective of your company’s values. Some organizations might embrace a more flexible approach to personal internet use during breaks, while others require a stricter focus on work-related activities. Balancing security needs with employee morale and trust is a delicate but important aspect of customization, ensuring that the final document is both effective and accepted.
Important Elements to Include in Your Technology Acceptable Use Policy Template
A robust and effective Technology Acceptable Use Policy Template should cover a comprehensive range of topics to provide clear guidance and protect organizational assets. Here are the key elements that should be meticulously drafted and included:
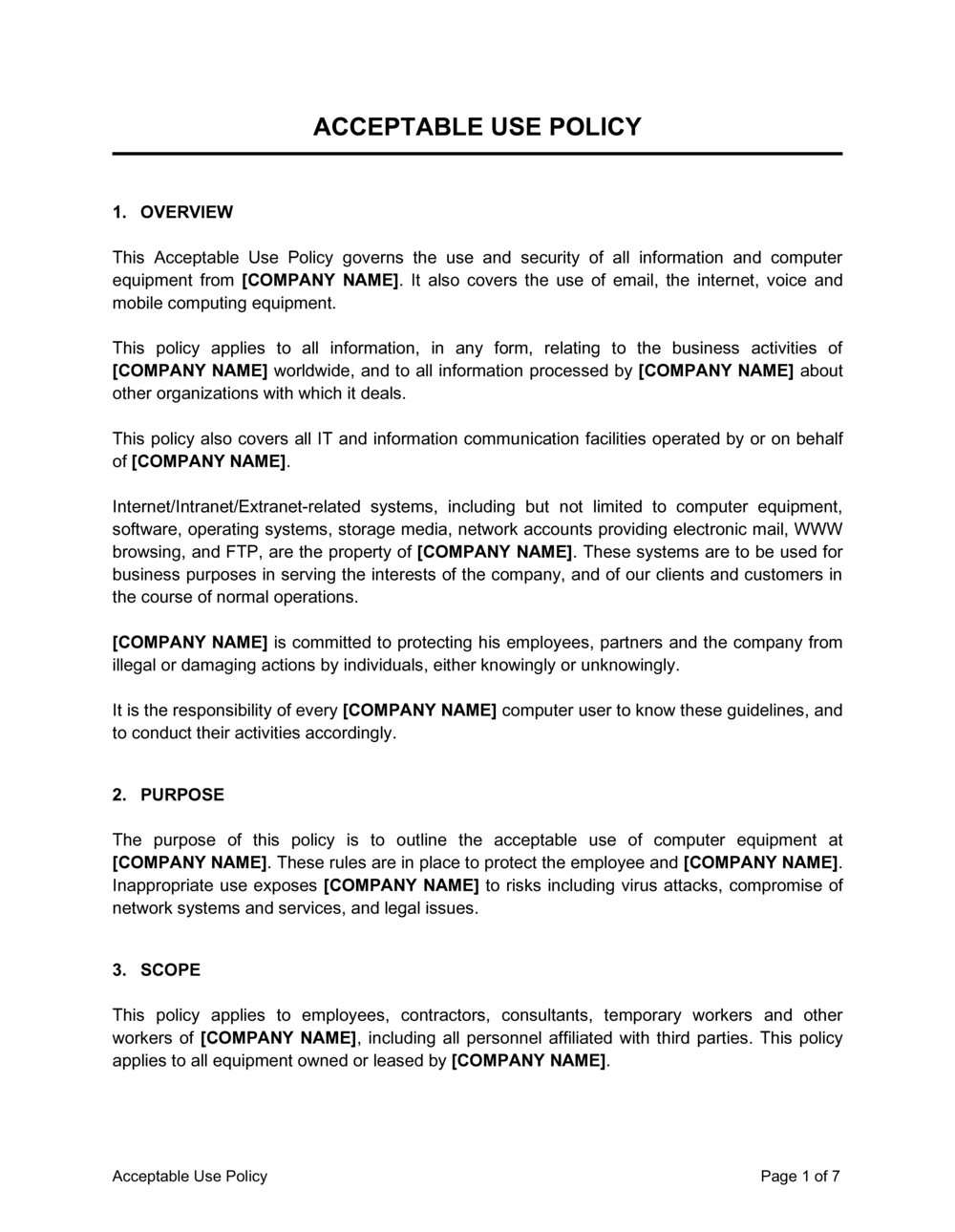
- Purpose and Scope: Clearly state why the policy exists (e.g., to protect assets, ensure productivity, comply with laws) and who it applies to (all employees, contractors, interns, volunteers, etc.), outlining which devices and systems are covered.
- Definitions: Provide clear definitions for key terms used throughout the policy, such as "Company Devices," "Sensitive Data," "Authorized User," and "Acceptable Use," to eliminate ambiguity.
- General Principles: Establish overarching principles of responsible and ethical technology use, emphasizing professionalism, respect for others, and adherence to all legal terms and workplace rules.
- Acceptable Use of Technology: Detail what activities are permitted, such as using company equipment for legitimate business purposes, accessing approved software, and professional communication channels.
- Unacceptable Use of Technology: Clearly list prohibited activities, including illegal acts, harassment, accessing inappropriate content, unauthorized software installation, excessive personal use, intellectual property theft, and circumventing security measures. This section is critical for data security.
- Privacy and Monitoring: Inform users about their limited expectation of privacy when using company resources and explicitly state the organization’s right to monitor activity on its networks and devices, consistent with relevant laws.
- Data Security and Handling: Outline responsibilities for protecting sensitive information, including guidelines for password strength, data encryption, secure storage, and the reporting of security incidents or data breaches.
- Device Usage (Company-Owned vs. BYOD): Provide specific rules for company-issued devices and, if applicable, a separate section for Bring Your Own Device (BYOD) policies, addressing security, data backup, and remote wipe capabilities.
- Software and Licensing: Enforce the use of only licensed and approved software, prohibiting the installation of unauthorized applications, and ensuring compliance with licensing agreements.
- Internet, Email, and Social Media Usage: Set guidelines for internet browsing, professional email communication, and the appropriate use of social media platforms during work hours or when representing the company.
- Consequences of Violation: Clearly articulate the disciplinary actions that may be taken for policy violations, ranging from warnings to termination of employment and, in severe cases, legal action.
- Policy Acknowledgment: Require all users to read, understand, and formally acknowledge their agreement to abide by the policy, often through a signed document or digital consent. This forms a critical part of the employment agreement.
- Policy Review and Updates: Specify a schedule for regular review and updates to the policy, ensuring it remains current with technological advancements, legal changes, and organizational needs.
Tips for Design, Usability, and Implementation
Creating a comprehensive Technology Acceptable Use Policy Template is only half the battle; ensuring it is easily understood, accessible, and effectively implemented is equally important. Design and usability play a crucial role in its adoption and adherence.
Clarity and Simplicity: Write in plain language, avoiding overly technical jargon or complex legal terms where possible. The goal is for every employee, regardless of their technical expertise, to understand their obligations. Use concise sentences and active voice. A policy that’s difficult to decipher will often be ignored.
Accessibility and Readability: Ensure the policy is easy to find and access. Host it on your company’s intranet, in your HR portal, and provide a printed copy during onboarding if preferred. Use clear headings (<h3> can be useful here), bullet points, and ample white space to break up text and improve readability. Consider providing the policy in digital formats that are searchable and easily navigable.
Comprehensive Communication and Training: Don’t just publish the policy and expect everyone to read it. Actively communicate its importance, especially during onboarding and annual reviews. Conduct training sessions that highlight key aspects, explain the rationale behind certain rules (e.g., why data security matters), and provide opportunities for questions. Use real-world examples to illustrate acceptable and unacceptable use.
Digital Acknowledgment: Implement a system for employees to digitally sign or acknowledge their review and understanding of the Technology Acceptable Use Policy Template. This creates a verifiable record of their agreement to the workplace rules and strengthens the policy’s enforceability. Many HR software platforms offer features for managing and tracking these essential agreements.
Regular Review and Updates: Technology, threats, and legal landscapes are constantly evolving. Schedule regular reviews (e.g., annually or bi-annually) of your AUP to ensure it remains relevant and effective. Update the policy as new technologies are introduced, new compliance requirements emerge, or as lessons are learned from internal incidents. Communicate any changes clearly and require re-acknowledgment.
Adopting a robust Technology Acceptable Use Policy isn’t merely a bureaucratic exercise; it’s a strategic investment in your organization’s security, productivity, and resilience. By clearly defining the parameters for digital engagement, you empower your workforce to leverage technology effectively while safeguarding your valuable assets from an array of potential threats. It builds a foundation of trust and responsibility, where everyone understands their role in maintaining a secure and professional digital environment.
So, as you navigate the complexities of modern business operations, consider the profound impact a well-implemented Technology Acceptable Use Policy Template can have. It provides the essential framework for clear communication, robust data security, and unwavering compliance, transforming potential liabilities into managed risks. Don’t leave your organization vulnerable; take the proactive step to customize and deploy a comprehensive acceptable use policy that protects your future and empowers your team.


