In today’s digital age, where financial data flows with unprecedented speed and volume, the imperative for robust information security has never been greater. For financial institutions across the United States, navigating the complex landscape of data protection isn’t merely good practice; it’s a stringent legal requirement mandated by the Gramm-Leach-Bliley Act (GLBA). Ensuring the confidentiality, integrity, and availability of sensitive customer information is not just about avoiding penalties; it’s about building and maintaining the trust that is the bedrock of any successful financial relationship.
Developing a comprehensive information security program from scratch can feel like a daunting task, consuming significant time and resources. This is where a well-crafted Glba Information Security Program Template becomes an invaluable asset. It provides a structured, pre-defined framework, allowing organizations to efficiently build, implement, and maintain a compliance posture that meets regulatory expectations without reinventing the wheel. It’s an essential tool for any financial entity seeking to streamline its security efforts and demonstrate due diligence in protecting customer data.
Understanding GLBA Compliance: The Foundation
The Gramm-Leach-Bliley Act, enacted in 1999, fundamentally changed the way financial institutions operate, especially concerning privacy and data security. A cornerstone of GLBA is its Safeguards Rule, which requires financial institutions to implement an information security program to protect the confidentiality and security of customer nonpublic personal information. This isn’t a suggestion; it’s a legal obligation enforced by various federal agencies, including the Federal Trade Commission (FTC) and banking regulators. Non-compliance can lead to severe fines, reputational damage, and a significant erosion of customer trust, making a proactive approach to security indispensable.
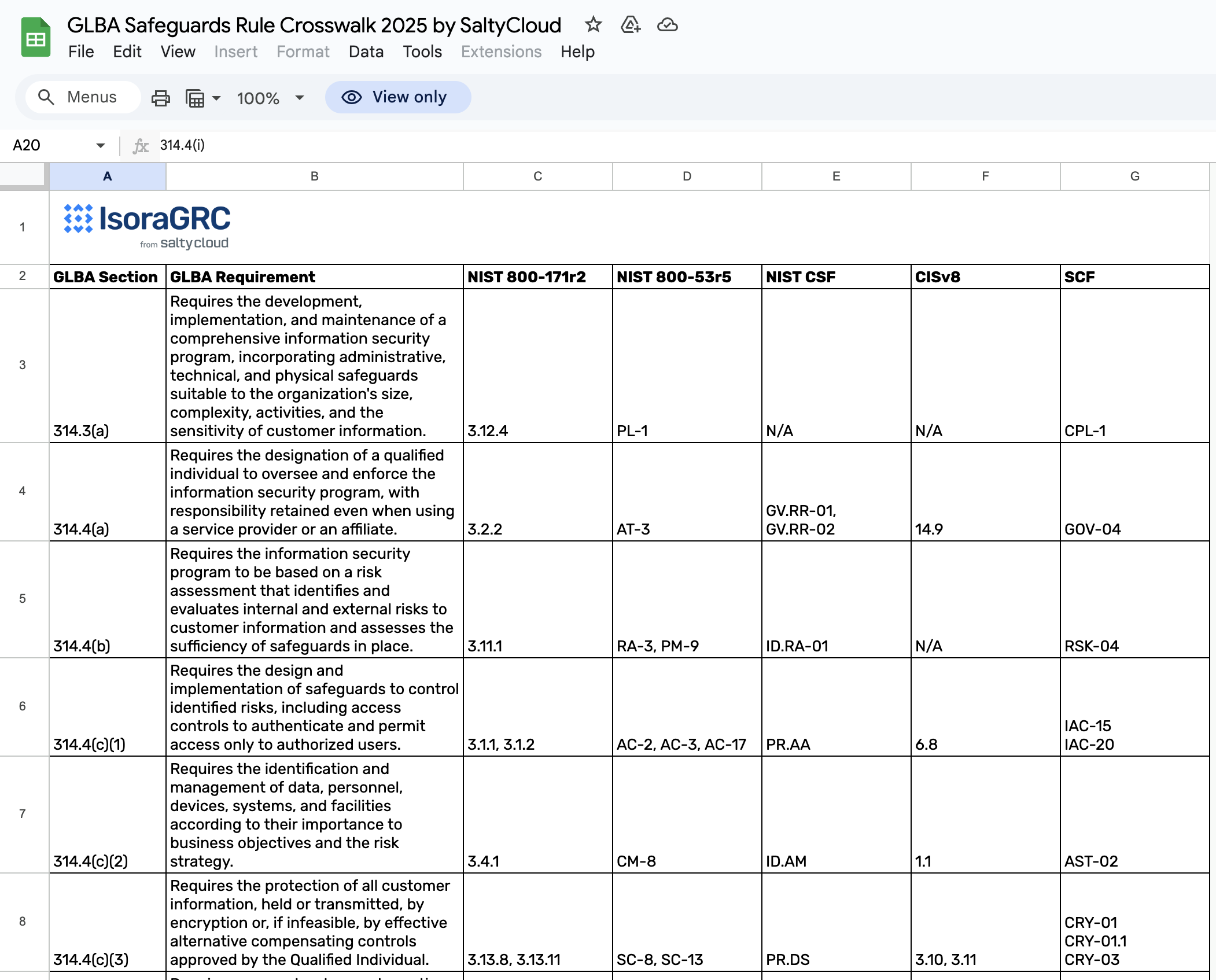
At its core, a GLBA-compliant security program demands a systematic process for assessing and addressing risks to customer information. It requires financial institutions to identify foreseeable internal and external threats, assess the sufficiency of current safeguards, and design and implement controls to mitigate those risks. This continuous cycle of evaluation and improvement ensures that an organization’s defenses evolve with the threat landscape, providing ongoing protection for sensitive data.
The Power of a GLBA Security Program Template
Embarking on the journey of creating an information security program can be overwhelming, given the specificity and depth required by GLBA. A pre-designed GLBA security program template offers a significant advantage, providing a solid starting point that incorporates best practices and regulatory requirements. It transforms what could be a months-long project into a structured, manageable process, accelerating your path to compliance and strengthening your overall security posture.
Beyond mere efficiency, utilizing a robust template helps ensure consistency and thoroughness. It acts as a comprehensive checklist, reminding organizations of all the critical components that must be addressed, from risk assessments to incident response plans. This systematic approach minimizes the risk of oversight and provides a clear, defensible framework should regulators ever inquire about your data protection efforts. It’s about more than just checking boxes; it’s about establishing a resilient defense against cyber threats.
Core Elements of a Robust Information Security Program
A comprehensive GLBA-compliant information security program isn’t a single document; it’s a living framework composed of several interconnected elements. A high-quality regulatory compliance template will guide you through establishing each of these critical components, ensuring a holistic approach to safeguarding customer data.
Risk Assessments
At the heart of any effective data protection program is a thorough and ongoing risk assessment. This involves identifying potential threats to the security, confidentiality, and integrity of customer information, both internal and external. It also requires an evaluation of the vulnerabilities within your systems and processes that these threats could exploit. A template provides structured prompts to ensure you cover all bases, from physical security to network vulnerabilities and employee practices.
Information Security Policies and Procedures
Policies are the rules, and procedures are the steps to follow those rules. These documents define your organization’s stance on security, outlining acceptable use of IT resources, data handling protocols, access control mechanisms, and more. A well-structured security policy template offers pre-written sections that you can customize, covering areas like password policies, data encryption standards, and acceptable use guidelines for employees and third-party vendors.
Employee Training
People are often the weakest link in any security chain, making ongoing security awareness training absolutely crucial. Your program must include regular education for all employees on their roles and responsibilities in protecting customer information. A template will include provisions for outlining training content, frequency, and tracking mechanisms to ensure everyone understands their part in maintaining a secure environment.
Vendor Management
Financial institutions frequently rely on third-party service providers who may have access to customer data. GLBA requires you to exercise due diligence in ensuring these vendors also maintain appropriate safeguards. Your information security program for financial institutions must include robust vendor assessment and management policies, covering contractual agreements, security reviews, and ongoing monitoring of third-party risk.
Incident Response Plan
Even with the best safeguards, security incidents can occur. A detailed incident response plan is essential to minimize damage, address the breach, and comply with notification requirements. This plan outlines the steps to take when an incident is detected, from containment and eradication to recovery and post-incident analysis. A template helps ensure all critical roles, procedures, and communication channels are pre-defined, ready for immediate activation.
Testing and Monitoring
An effective program isn’t static; it requires continuous monitoring and regular testing to ensure its effectiveness. This includes penetration testing, vulnerability assessments, and regular audits of security controls. The template provides sections to document your testing schedule, methodologies, and the process for addressing identified weaknesses, ensuring your financial data security plan remains robust against evolving threats.
Implementing Your GLBA Compliance Framework
Adopting a **Glba Information Security Program Template** is a strategic move, but its true value is unlocked through careful implementation and ongoing management. Here’s a practical roadmap to effectively integrate a new or updated information security framework into your operations.
Assemble Your Team
Designate a cross-functional team responsible for overseeing the information security program. This team should include representatives from IT, legal, operations, and senior management to ensure all perspectives are considered and buy-in is secured across the organization. Clear roles and responsibilities are paramount for successful execution.
Conduct a Comprehensive Risk Assessment
Before tailoring the template, perform an updated, thorough risk assessment specific to your institution. Identify all systems, processes, and data repositories that handle customer nonpublic personal information. Document potential threats, vulnerabilities, and the likelihood and impact of various security incidents. This assessment will directly inform which sections of the template require the most customization.
Tailor the Template to Your Organization
While a template provides a fantastic foundation, it’s not a one-size-fits-all solution. Customize the document to reflect your institution’s unique operational environment, technology stack, and specific risk profile. Review each policy and procedure, adjusting language, adding specific controls relevant to your systems, and incorporating any existing security measures you already have in place. The goal is to create a security policy template that is genuinely yours.
Implement and Train
Once customized, formally adopt the information security program. Crucially, communicate its contents to all employees. Conduct mandatory training sessions that explain the policies, procedures, and each employee’s role in protecting customer data. Reinforce the importance of security awareness and provide clear channels for reporting suspicious activities or potential security incidents.
Regular Review and Update
The digital threat landscape is constantly changing, meaning your GLBA compliance framework cannot remain static. Establish a schedule for regular reviews and updates of your security program – at least annually, or whenever there are significant changes to your business operations, technology, or the regulatory environment. This continuous process ensures your data protection measures remain relevant and effective.
Beyond the Checklist: Cultivating a Security Culture
While a **Glba Information Security Program Template** provides the essential framework, achieving true compliance and robust data protection goes beyond merely filling out a document. It requires fostering a pervasive culture of security throughout the entire organization. Every employee, from the CEO to the newest hire, must understand their role in protecting sensitive customer information. This means consistent communication, regular training refreshers, and leadership that models secure behavior.
Embedding security into daily operations transforms compliance from a burden into a core operational strength. When security becomes second nature, risks are naturally mitigated, and the institution is better positioned to adapt to emerging threats. This commitment to an ongoing security ethos is what truly differentiates a compliant organization from one that simply adheres to the letter of the law, building lasting trust with customers and stakeholders alike.
In the complex and ever-evolving world of financial services, the protection of customer data is not just a regulatory hurdle but a fundamental business imperative. Utilizing a comprehensive GLBA information security program template offers a strategic advantage, providing a clear, structured path to meeting your obligations while significantly enhancing your security posture. It’s an investment in your institution’s future, ensuring compliance, mitigating risk, and, most importantly, safeguarding the trust your customers place in you. Don’t merely react to compliance demands; proactively build a resilient security framework that stands the test of time.