In today’s interconnected digital landscape, the question is no longer if your organization will face a cyber threat, but when. Data breaches, ransomware attacks, and insider threats are constant realities, making robust information security a fundamental pillar of business continuity and trust. For any enterprise, regardless of size or industry, a haphazard approach to security is a recipe for disaster, risking financial ruin, reputational damage, and legal penalties.
This pressing need for a structured and proactive defense is precisely why developing a comprehensive security program is paramount. It’s not merely about deploying firewalls and antivirus software; it’s about establishing a strategic, organization-wide framework that addresses people, processes, and technology. This is where an effective Information Security Program Plan Template becomes not just useful, but indispensable, offering a guiding hand to build a resilient and adaptable security posture.
Why a Robust Security Program is Non-Negotiable
In an era dominated by digital transformation, every piece of data, every transaction, and every customer interaction relies on secure information systems. A well-defined security program provides the bedrock for these operations, safeguarding sensitive data, intellectual property, and critical infrastructure. It moves an organization from reactive crisis management to proactive risk mitigation, building confidence among stakeholders and clients alike.
Beyond mere defense, a solid security program also ensures compliance with an ever-growing labyrinth of regulations. Laws like GDPR, CCPA, HIPAA, and industry-specific standards demand stringent data protection practices. A thoughtfully crafted organizational security plan helps you navigate these requirements, minimizing the risk of costly fines and legal entanglements. It’s about more than just staying out of trouble; it’s about fostering an environment where trust and reliability can thrive.
Understanding the Core Components of Your Security Blueprint
A truly effective information security program encompasses a wide array of elements, working in concert to protect your digital assets. It’s far more than a checklist; it’s a living document that reflects your organization’s unique risk profile, business objectives, and regulatory obligations. While each enterprise security program will have its specific nuances, certain foundational components are universally critical.
Developing a comprehensive security blueprint requires a holistic perspective, integrating security into the fabric of your business operations rather than treating it as an isolated IT function. It involves identifying what needs protection, understanding potential threats, and implementing appropriate controls. The goal is to build a layered defense that can withstand various attack vectors and adapt to new challenges.
Key Pillars of an Effective Security Framework
A well-structured security strategy document typically addresses several interconnected domains. These pillars form the framework upon which your entire defense mechanism is built, ensuring all critical aspects of security are systematically managed.
- **Governance and Risk Management:** This involves defining the overall direction for information security, establishing clear roles and responsibilities, and implementing a robust risk assessment and management process. It includes developing security policies, standards, and procedures.
- **Asset Management:** Identifying and cataloging all information assets (data, systems, applications, hardware) is crucial for understanding what needs protection and assigning appropriate security controls. This also covers asset classification and ownership.
- **Human Resources Security:** Recognizing that people are often the weakest link, this pillar focuses on security awareness training, background checks for employees, clear roles and responsibilities, and processes for onboarding and offboarding personnel.
- **Physical and Environmental Security:** Protecting physical access to information assets, data centers, and network equipment is just as important as digital security. This includes access controls, environmental controls, and safeguarding critical infrastructure.
- **Operations Security:** This covers the day-to-day management of IT systems, including patch management, vulnerability management, logging and monitoring, backup and recovery procedures, and network security.
- **Access Control:** Implementing strict measures to ensure that only authorized individuals have access to specific information and systems, utilizing principles like least privilege and segregation of duties.
- **Cryptography:** Employing encryption and other cryptographic controls to protect the confidentiality and integrity of data, both in transit and at rest.
- **Communication Security:** Protecting information flowing over networks, including email security, VPNs, and secure remote access protocols.
- **Vendor and Third-Party Security:** Managing the security risks introduced by external service providers and partners who may have access to your systems or data.
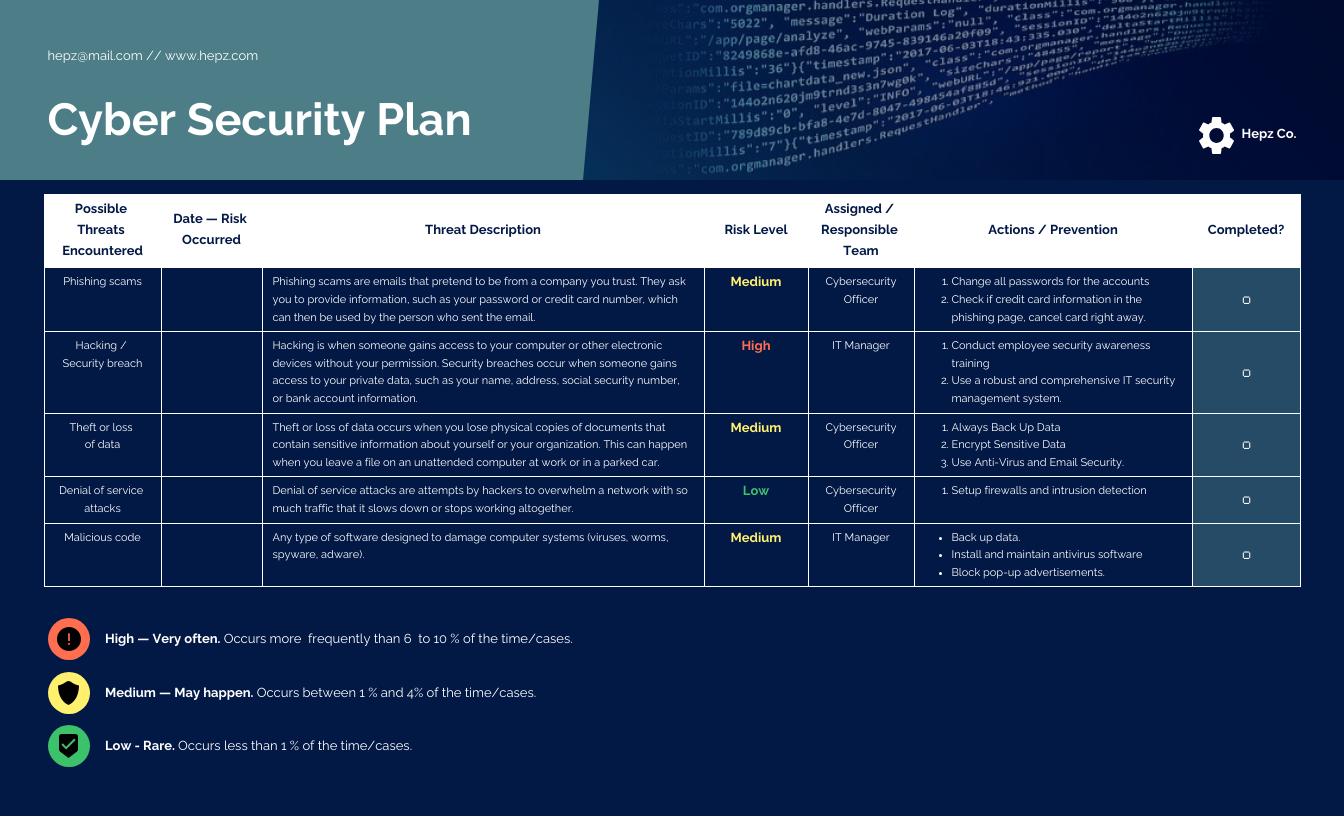
- **Incident Management:** Establishing a clear plan for detecting, responding to, and recovering from security incidents, minimizing their impact and facilitating a swift return to normal operations. This includes an **incident response protocol**.
- **Business Continuity and Disaster Recovery:** Planning for how your organization will continue critical operations and recover data and systems in the event of a major disruption.
- **Compliance Management:** Ensuring adherence to relevant legal, regulatory, and contractual obligations, and conducting regular audits to verify compliance.
Key Steps to Developing Your Information Security Program
Crafting a comprehensive security program involves a systematic approach, moving from initial assessment to ongoing improvement. It’s an iterative process that demands commitment and continuous evaluation. Utilizing an adaptable Information Security Program Plan Template allows organizations to streamline this often complex process, providing a structured starting point rather than building from scratch.
First, begin with a thorough risk assessment. Identify your critical assets, potential threats, and existing vulnerabilities. Understand the likelihood of various risks materializing and their potential impact on your business. This assessment will inform your priorities and guide the allocation of resources. Your risk management framework should be dynamic, regularly reviewed to reflect changes in the threat landscape and business operations.
Next, define your security objectives. What exactly are you trying to protect, and why? These objectives should align with your business goals and regulatory requirements. From there, you can start developing detailed security policy development, standards, and procedures for each of the core components outlined earlier. These documents will serve as the guiding principles for all security-related activities within your organization.
Implementation is the operational phase where policies are put into practice. This involves configuring systems, training staff, deploying new technologies, and establishing monitoring processes. Regular security audits and vulnerability assessments are crucial to identify gaps and measure the effectiveness of your controls. The final, and arguably most critical, step is continuous monitoring and improvement. The threat landscape is constantly evolving, so your security posture must evolve with it.
Benefits of a Structured Security Framework
Implementing a well-defined security governance framework yields a multitude of benefits that extend far beyond simply preventing breaches. It enhances an organization’s overall resilience, fosters a culture of security, and provides a competitive advantage in the marketplace. For instance, a clear data protection strategy builds trust with customers, who are increasingly concerned about the privacy and security of their personal information.
Such a framework facilitates better decision-making by providing a clear understanding of risks and priorities. It optimizes resource allocation, ensuring that investments in security are targeted and effective. Moreover, an established information security program promotes efficiency by standardizing processes and reducing redundancies, leading to smoother operations and faster incident response times. It also significantly improves an organization’s ability to achieve and maintain compliance management, demonstrating due diligence to auditors and regulators.
Maintaining and Evolving Your Security Posture
An effective cybersecurity program framework is not a static document; it’s a living, breathing entity that requires constant attention and adaptation. The digital world is in perpetual motion, with new threats emerging daily and technologies evolving at an incredible pace. Therefore, your security plan must be regularly reviewed, tested, and updated to remain relevant and effective.
Ongoing security awareness training for all employees is critical. Human error remains a leading cause of security incidents, and continuous education ensures that your team acts as an informed first line of defense. Regular vulnerability scanning, penetration testing, and tabletop exercises for incident response are essential to identify weaknesses and refine your protocols before a real attack occurs. Establishing a feedback loop from these activities back into your enterprise security program ensures continuous improvement.
In essence, a robust security program is a journey, not a destination. It demands vigilance, adaptability, and a commitment to continuous enhancement. By embracing this philosophy, your organization can build a truly resilient security posture that protects your most valuable assets and ensures long-term success in the digital age.
Developing a comprehensive security program might seem like a daunting task, but the effort is an investment that pays dividends in protection, trust, and business continuity. It provides the structured approach necessary to navigate the complexities of modern cyber threats and regulatory demands. By systematically addressing your security needs, you not only safeguard your organization but also build a foundation for sustainable growth and innovation.
Embrace the strategic importance of this endeavor. Leverage the insights and structure provided by best practices to design and implement a security framework that is both robust and agile. Your proactive commitment to information security will undoubtedly become a cornerstone of your organization’s resilience and a testament to its forward-thinking approach in a challenging digital world.