In an era where digital perimeters are constantly under siege from external forces, a more subtle and often more damaging threat lurks within: the insider. Whether driven by malicious intent, negligence, or accidental error, insiders possess a unique vantage point and privileged access that can bypass even the most sophisticated external defenses. The consequences of such breaches range from devastating financial losses and intellectual property theft to severe reputational damage and regulatory fines.
Protecting an organization from these internal vulnerabilities requires more than just reactive measures; it demands a proactive, comprehensive strategy. This is precisely where a well-structured plan for mitigating insider risks becomes indispensable. Leveraging an Insider Threat Program Plan Template can provide the essential framework, guiding organizations through the complex process of identifying, preventing, detecting, and responding to threats originating from within their own ranks, ensuring a cohesive and effective security posture.
Why Insider Threats Demand Proactive Planning
The landscape of cybersecurity is ever-evolving, yet one constant remains: human fallibility. Insider threats encompass a broad spectrum, from the disgruntled employee intentionally exfiltrating sensitive data to the busy executive inadvertently clicking a phishing link, or even the contractor with elevated access making a critical configuration error. The sheer diversity of these scenarios underscores the need for a multi-faceted approach to security.
Recent studies consistently highlight the severe impact of insider incidents, often incurring higher costs per incident compared to external attacks due to the loss of trust, deeper system access, and prolonged detection times. Beyond financial repercussions, operational disruptions, intellectual property erosion, and compliance failures can cripple an organization. A robust insider threat program moves beyond merely reacting to incidents; it focuses on establishing controls and processes to deter, detect, and mitigate these risks before they escalate, safeguarding critical assets and maintaining operational integrity.
The Core Purpose of an Insider Threat Program Blueprint
An effective insider threat program blueprint serves as an organization’s strategic guide, detailing its approach to managing internal risks. It’s not just a document; it’s a living framework that integrates people, processes, and technology to create a resilient defense against insider threats. This blueprint ensures consistency in how potential risks are identified, assessed, and addressed across all departments and levels of an organization.
Its primary purpose is to establish clear roles, responsibilities, and procedures, fostering a collaborative environment where security is a shared responsibility, not just an IT function. By providing a structured roadmap, a well-defined program plan helps secure executive buy-in, facilitates cross-departmental cooperation (involving HR, Legal, IT, and Security), and articulates the organization’s commitment to protecting its most valuable assets from internal compromise. It transforms abstract security concepts into actionable strategies, paving the way for a more secure and resilient enterprise.
Key Elements of a Robust Program Blueprint
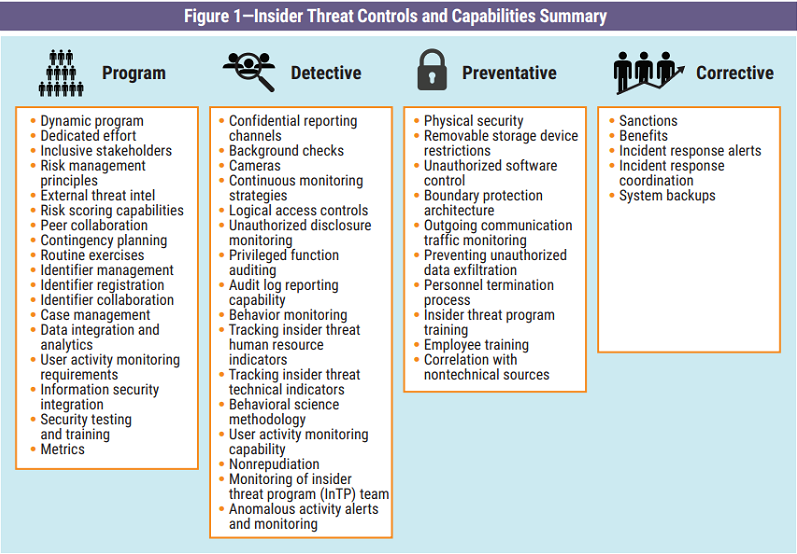
Developing a comprehensive strategy for combating insider risks requires careful consideration of numerous interconnected components. A solid program plan for insider threats should delineate how an organization will systematically build and manage its defenses. While specific elements may vary by industry and organizational size, certain foundational pillars are universal.
Here are the essential components that should be addressed in any organizational insider threat blueprint:
- **Program Vision and Objectives:** Clearly articulate the program’s mission, scope, and what it aims to achieve, aligning it with the overall business objectives and risk tolerance.
- **Governance and Leadership:** Define the organizational structure, roles, and responsibilities for managing the program, including executive sponsorship and oversight. Establish a cross-functional team with representation from HR, Legal, IT, and Security.
- **Risk Assessment and Identification:** Outline methodologies for identifying potential insider risks, categorizing critical assets, and understanding user access patterns. This includes vulnerability assessments and threat modeling specific to internal actors.
- **Behavioral Indicators and Monitoring:** Detail the types of behavioral indicators (e.g., unusual data access, policy violations, signs of disgruntlement) the program will monitor, along with the ethical and legal boundaries for such surveillance.
- **Policy and Procedures:** Establish clear policies on acceptable use, data handling, access controls, and a comprehensive incident response plan tailored for insider incidents.
- **Training and Awareness:** Develop continuous training programs for all employees, emphasizing security best practices, the importance of reporting suspicious activity, and the consequences of policy violations. Leadership and specialized roles also require targeted training.
- **Technology and Tools:** Identify the security solutions that will support the program, such as User and Entity Behavior Analytics (**UEBA**), Data Loss Prevention (**DLP**), Security Information and Event Management (**SIEM**), and robust access management systems.
- **Legal and Privacy Considerations:** Address all relevant legal and regulatory compliance requirements (e.g., GDPR, CCPA, HIPAA, CMMC, NIST), ensuring employee privacy rights are protected while maintaining security effectiveness.
- **Incident Response and Remediation:** Establish detailed protocols for detecting, investigating, containing, and recovering from insider threat incidents, including forensic analysis and disciplinary actions.
- **Metrics and Program Evaluation:** Define key performance indicators (**KPIs**) and metrics to measure the program’s effectiveness, facilitate continuous improvement, and demonstrate value to stakeholders.
Building Your Insider Threat Program Plan: A Phased Approach
Developing and implementing a comprehensive internal threat mitigation strategy is an iterative process, best approached in distinct, manageable phases. Rushing implementation without proper foundational work can lead to inefficiencies, employee distrust, and a less effective program. A phased approach ensures thoroughness, adaptability, and sustained success.
The initial phase should focus on foundation and buy-in. This involves securing executive sponsorship, assembling a multi-disciplinary team, and conducting an initial risk assessment to understand the organization’s specific vulnerabilities and critical assets. Establishing clear communication channels and setting realistic expectations are crucial at this stage to build trust and foster collaboration.
Next comes the design and development phase. This is where policies, procedures, and technical requirements are meticulously crafted based on the initial risk assessment. Here, the team defines the scope of monitoring, selects appropriate technologies, and develops comprehensive training materials. This phase also includes defining incident response protocols and legal frameworks, ensuring all aspects align with organizational values and regulatory mandates.
The implementation phase involves rolling out the program in a controlled manner, often starting with a pilot program or specific departments before a full organizational deployment. This includes configuring security tools, delivering targeted training, and establishing reporting mechanisms. Careful monitoring and adjustment during this phase are vital to address unforeseen challenges and optimize performance.
Finally, the operations and continuous improvement phase ensures the program remains effective and relevant over time. This involves ongoing monitoring, regular review of policies and procedures, periodic risk re-assessments, and continuous training updates. Feedback loops and performance metrics are critical for identifying areas for enhancement, adapting to new threat vectors, and ensuring the insider risk management strategy remains robust against evolving challenges.
Customizing for Your Organization’s Unique Landscape
While a general framework for mitigating insider risks provides an excellent starting point, effective deployment hinges on tailoring the approach to your organization’s specific context. There’s no one-size-fits-all solution, as each enterprise has a unique culture, operational model, regulatory environment, and risk profile. Ignoring these nuances can lead to a program that is either overly burdensome or woefully inadequate.
Consider your industry’s specific regulatory requirements and common threat vectors. A financial institution, for example, faces different insider threats and compliance obligations than a manufacturing firm or a healthcare provider. The size and structure of your organization also play a significant role; a small startup will require a different scale of program than a multinational corporation. Your existing security infrastructure, technological capabilities, and even the established organizational culture—whether open and collaborative or hierarchical and restrictive—must inform the design of your enterprise insider threat framework. Balancing security with employee productivity and trust is paramount, ensuring that the program enhances rather than hinders the workplace environment.
Best Practices for Sustained Program Success
A security program documentation focused on insider threats is not a one-time project; it’s an ongoing commitment that requires continuous attention and adaptation. To ensure its long-term success, organizations must integrate several best practices into their operational rhythm. These practices extend beyond technical controls, encompassing cultural, educational, and procedural elements that foster a truly resilient security posture.
Firstly, cultivate a culture of trust and transparency. Position the program as a means of protection for the organization and its employees, rather than a punitive "gotcha" system. Open communication about the program’s objectives and safeguards for privacy can significantly reduce employee anxiety and increase cooperation. Secondly, ensure cross-functional collaboration is at the program’s heart. Regular engagement between security, HR, legal, IT, and business unit leaders guarantees a holistic understanding of risks and ensures policies are practical and legally sound. Thirdly, prioritize continuous learning and adaptation. The threat landscape is dynamic; therefore, the program must evolve with new technologies, emerging threats, and organizational changes. Regular training and awareness campaigns are crucial to keep employees informed and vigilant. Finally, focus on deterrence and prevention as much as detection. Early intervention, psychological countermeasures, and robust access controls can significantly reduce the likelihood of malicious acts, while strong security education can prevent accidental errors.
Building an effective program for addressing insider threats is a significant undertaking, yet an absolutely critical one in today’s interconnected world. It requires a thoughtful, strategic approach that acknowledges the unique challenges posed by internal actors. By leveraging a comprehensive plan, organizations can move beyond reactive measures, establishing a proactive defense that protects their most valuable assets from both malicious intent and inadvertent actions.
The journey to a resilient security posture is continuous, demanding ongoing commitment, adaptation, and a collaborative spirit across all levels of the organization. By investing in a well-defined insider risk management strategy, businesses can not only mitigate significant threats but also foster a more secure, trustworthy, and productive environment for everyone. Start strengthening your internal defenses today, because the integrity of your organization truly begins within.