In today’s interconnected digital landscape, organizations face an unprecedented barrage of cyber threats. From sophisticated phishing campaigns to debilitating ransomware attacks and persistent data breaches, the risks to sensitive information and critical systems are ever-present and continually evolving. Navigating this complex environment requires more than just reactive measures; it demands a proactive, structured approach to identify, assess, and mitigate potential vulnerabilities before they can be exploited.
This is where a robust information security risk management program becomes indispensable, serving as the strategic backbone for protecting your digital assets. While the thought of building such a program from scratch might seem daunting, establishing a comprehensive framework for digital security doesn’t have to be an overwhelming endeavor. An effective Information Security Risk Management Program Template offers a powerful starting point, providing the foundational structure and guiding principles necessary to build a resilient and compliant security posture.
Understanding the Imperative: Why Risk Management Matters Now More Than Ever
The modern business world is driven by data, making information security not merely an IT concern but a fundamental business imperative. Regulatory bodies across industries, from HIPAA in healthcare to GDPR in Europe (impacting US companies dealing with EU data) and CCPA in California, mandate stringent data protection and privacy standards. Non-compliance can lead to hefty fines, legal repercussions, and severe reputational damage.
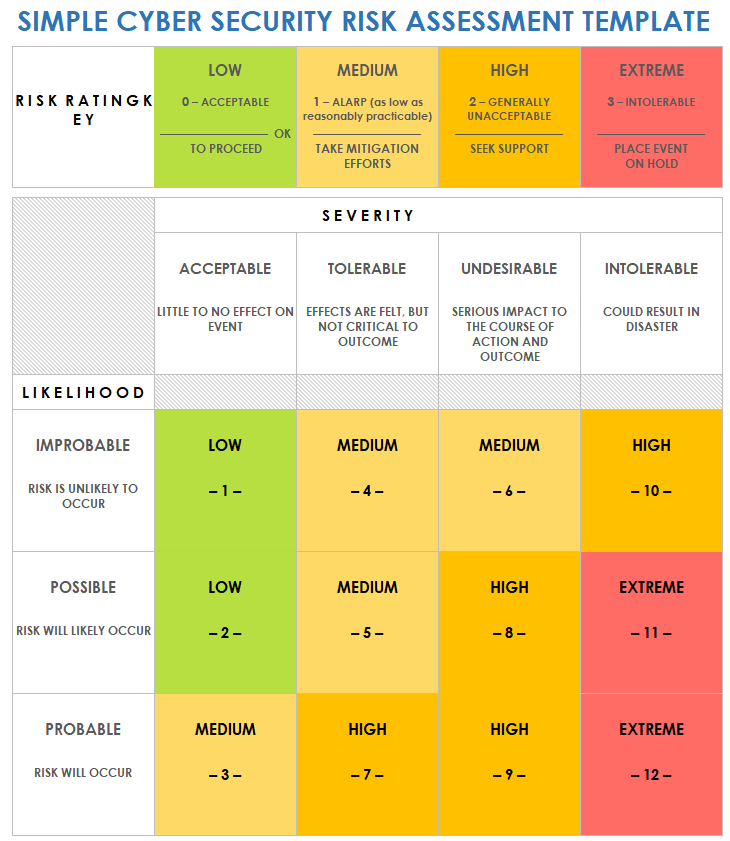
Beyond compliance, the financial and operational costs of a security incident can be catastrophic. Downtime, recovery efforts, customer churn, and the erosion of trust can impact an organization for years. A well-defined security risk management program helps organizations systematically understand their risk exposure, prioritize investments in security controls, and make informed decisions that align with their overall business objectives and risk appetite. It’s about strategic resilience in the face of persistent digital adversity.
What Goes Into a Robust Information Security Risk Management Program?
A comprehensive security risk management program is a living document and a continuous process, not a one-time project. It encompasses a series of ongoing activities designed to protect an organization’s information assets. At its core, it involves systematically identifying potential threats and vulnerabilities, assessing the likelihood and impact of these risks, developing and implementing strategies to mitigate them, and continuously monitoring their effectiveness.
This iterative cycle ensures that as the threat landscape changes, or as the organization’s technological infrastructure evolves, the security posture remains adaptive and strong. It’s about establishing clear policies, procedures, and responsibilities that govern how information security risks are managed across the entire enterprise. Ultimately, it provides a clear roadmap for safeguarding sensitive data, intellectual property, and critical business operations.
Leveraging an Effective Risk Management Template: Your Blueprint for Success
Starting the journey of building a security risk management program can feel like charting unexplored territory. This is precisely where a high-quality information security risk management program template proves invaluable. It provides a pre-structured framework, guiding you through the essential components and considerations without reinventing the wheel. Such a template is more than just a document; it’s a strategic accelerator, helping you establish a consistent, repeatable process for managing digital security risks.
Using a well-designed template helps ensure that no critical steps are missed, facilitates easier communication across teams, and provides a clear audit trail for compliance purposes. It offers a standardized approach, fostering organizational alignment and efficiency in tackling complex security challenges. Moreover, it empowers even organizations with limited dedicated security resources to build out a credible and effective program.
Customizing Your Template for Unique Organizational Needs
While a risk management template provides an excellent foundation, it’s crucial to remember that it’s a starting point, not a rigid instruction manual. Every organization has a unique operational environment, a specific set of information assets, varying risk appetites, and different regulatory obligations. Therefore, tailoring your security program blueprint is an absolute necessity.
Customization involves adapting the template’s generic elements to reflect your organization’s specific context. This includes detailing your unique asset inventory, identifying threats and vulnerabilities pertinent to your industry, defining risk assessment criteria that resonate with your business impact, and selecting mitigation controls that are feasible and effective for your operational reality. A truly effective security risk management framework is one that is perfectly attuned to your specific organizational DNA.
Key Components of a Comprehensive Risk Management Framework
A robust security risk management framework must cover all angles, from initial planning to ongoing maintenance. Here are the essential elements that should be integrated into any effective program, ideally structured within your chosen program outline:
- Scope and Objectives: Clearly define what the risk management program covers (e.g., all information systems, specific departments, critical data types). Establish measurable goals, such as reducing the number of critical vulnerabilities or achieving specific compliance milestones.
- Roles and Responsibilities: Assign clear ownership for various aspects of the program, including executive sponsorship, risk owners, and implementation teams. This ensures accountability and promotes engagement.
- Risk Identification: Establish a systematic process for identifying potential threats (e.g., malware, insider threats, natural disasters) and vulnerabilities (e.g., unpatched software, weak configurations, human error) that could impact information assets.
- Risk Assessment Methodology: Define consistent criteria for evaluating identified risks. This typically involves assessing the likelihood of a threat exploiting a vulnerability and the potential impact if it occurs. Quantify or qualify risks to enable prioritization.
- Risk Treatment/Mitigation Strategies: Develop plans to address identified risks. Options include: avoidance (eliminate the activity), transfer (e.g., insurance), acceptance (live with the risk if low impact), or mitigation (implementing controls to reduce likelihood or impact).
- Risk Monitoring and Review: Implement continuous monitoring of identified risks and the effectiveness of implemented controls. Establish a schedule for regular reviews of the entire security risk management framework to adapt to changes.
- Reporting and Communication: Define how risk information will be communicated to relevant stakeholders, from technical teams to executive leadership and the board. Clear, concise reporting is crucial for informed decision-making.
- Policy and Procedure Integration: Ensure the risk management program is aligned with and supports existing organizational security policies, standards, and operational procedures.
- Compliance Mapping: Document how the program addresses specific regulatory, legal, and contractual requirements (e.g., NIST, ISO 27001, PCI DSS, SOX).
Implementing Your Program: A Phased Approach
Putting your security risk management program into action requires a structured, phased approach to ensure thoroughness and minimize disruption. While the exact steps may vary, a common progression includes:
- Phase 1: Foundation and Planning – Begin by securing executive buy-in and defining the scope and objectives of your risk management plan. Assemble your core team, identify key stakeholders, and establish the governance structure for the program. This phase also involves selecting or customizing your information security risk management program template to fit your organizational needs.
- Phase 2: Asset Identification and Risk Assessment – Conduct a thorough inventory of all information assets, including hardware, software, data, and critical business processes. For each asset, identify potential threats and existing vulnerabilities. Perform a comprehensive risk analysis using your defined methodology to determine the likelihood and impact of each risk, leading to a prioritized list of exposures.
- Phase 3: Risk Treatment and Mitigation – Based on the risk assessment, develop detailed risk treatment plans for the most significant risks. This involves selecting appropriate security controls (technical, administrative, physical) to reduce the likelihood or impact of an incident. Implement these controls, ensuring they are properly configured and integrated into your operational environment.
- Phase 4: Monitoring, Review, and Improvement – Establish key performance indicators (KPIs) and metrics to continuously monitor the effectiveness of your security controls and the overall risk posture. Conduct regular reviews of your security risk management program, typically annually or whenever significant organizational or environmental changes occur. This iterative process ensures continuous improvement and adaptation to new threats.
Common Pitfalls to Avoid and Best Practices to Embrace
Even with a solid security template, certain missteps can hinder a program’s effectiveness. Being aware of these pitfalls and adopting best practices can significantly enhance your success.
- Lack of Executive Buy-in: Without strong leadership support, securing necessary resources and driving cultural change for information security risk management becomes an uphill battle. Secure executive sponsorship early and keep them informed.
- Treating it as a Checkbox Exercise: Viewing risk management as a one-time compliance activity rather than an ongoing strategic process will lead to a stagnant and ineffective program. Emphasize continuous improvement and adaptation.
- Ignoring Business Context: A security program that doesn’t align with business goals and operational realities will face resistance. Integrate security considerations into business processes and decision-making.
- Over-complication: Don’t let the pursuit of perfection paralyze progress. Start with a manageable scope, iterate, and gradually expand your security risk management framework as your capabilities mature.
- Neglecting Communication: Poor communication about risks, controls, and responsibilities can create silos and hinder effective collaboration. Foster transparency and regular dialogue across all levels of the organization.
- Inadequate Tooling: Relying solely on manual processes for risk assessment and monitoring can be inefficient and error-prone. Leverage appropriate security tools and technologies to automate and streamline tasks where possible.
A well-defined and meticulously implemented information security risk management program is not just a shield against cyber threats; it’s a strategic asset that fosters resilience, builds trust, and ensures business continuity. By systematically identifying, assessing, and mitigating digital risks, organizations can operate with greater confidence, protect their valuable assets, and meet their regulatory obligations. It transitions security from a reactive cost center to a proactive enabler of business success.
While the journey to a fully mature security risk management framework is ongoing, commencing with a strong foundation is the most critical step. Utilizing a comprehensive template and tailoring it to your unique organizational landscape empowers you to establish a robust security program blueprint efficiently. This strategic approach paves the way for a more secure, compliant, and ultimately, more successful future in the digital age.
Investing the time and effort into building and maintaining a structured program for managing digital security risks is an investment in your organization’s longevity and reputation. It provides the clarity and direction needed to navigate the turbulent waters of the cyber world, transforming potential threats into manageable challenges.