In today’s fast-paced digital landscape, software applications are the lifeblood of almost every business. From mission-critical enterprise systems to customer-facing mobile apps, their continuous performance and availability are paramount. Yet, without a robust strategy for monitoring, even the most meticulously developed applications can suffer from silent failures, degraded performance, and ultimately, user dissatisfaction or significant financial loss. The challenge often isn’t just having monitoring tools, but knowing what to monitor and why.
This is where a structured approach becomes invaluable. Far too often, monitoring is an afterthought, implemented reactively when issues arise. However, proactive planning, guided by a clear understanding of an application’s specific operational needs, can transform monitoring from a troubleshooting chore into a strategic asset. A well-defined Application Monitoring Requirements Template provides that critical framework, ensuring all stakeholders are aligned on what truly matters for the application’s health and the business’s success.
The Unseen Pillars of Software Reliability
Every modern application, regardless of its complexity or domain, relies on a delicate balance of underlying systems. Databases, network infrastructure, cloud services, and custom code all intertwine to deliver functionality. When one of these components falters, the entire application can be impacted. Effective application health monitoring isn’t merely about catching errors; it’s about gaining deep insights into the behavior, performance, and availability of these intricate systems.
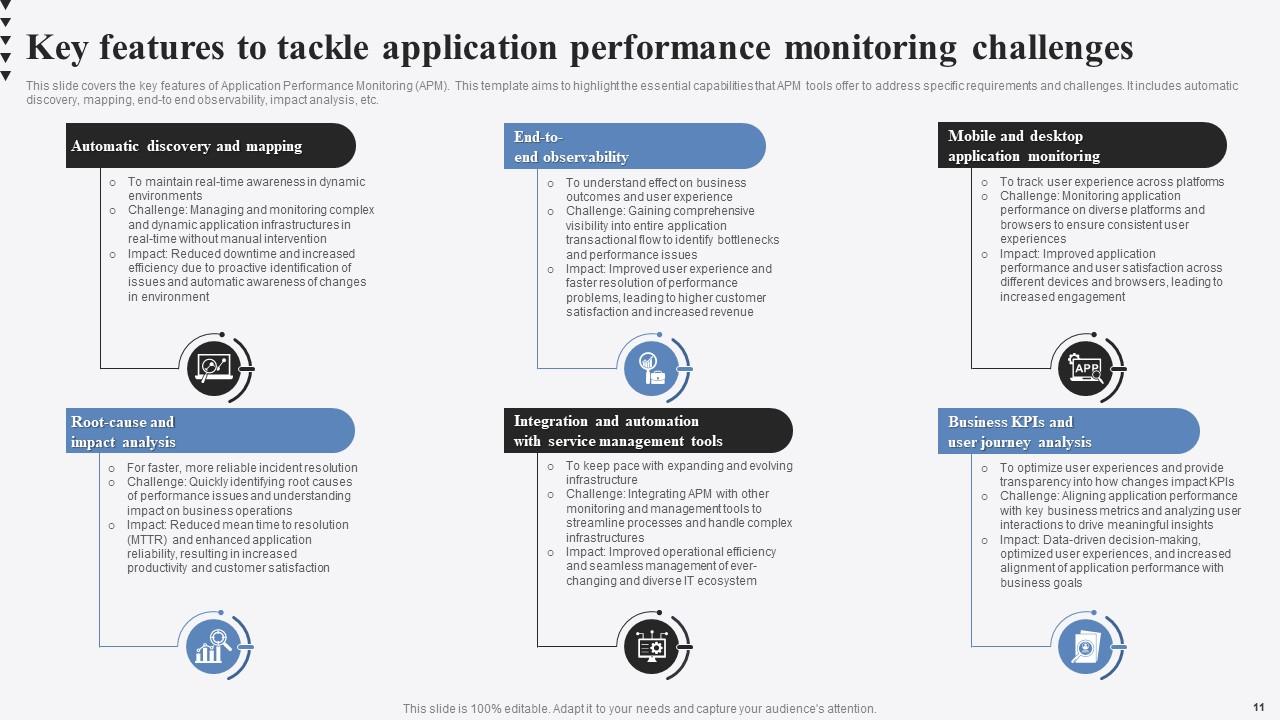
Establishing clear monitoring requirements from the outset is a foundational step in building reliable software. It bridges the gap between development, operations, and business expectations. Without a shared understanding of what constitutes "healthy" application performance, teams often work in silos, leading to incomplete monitoring solutions or an overwhelming deluge of irrelevant data. This not only wastes resources but also masks critical issues, leaving systems vulnerable to unexpected downtime.
Why a Structured Approach to Monitoring Matters
Implementing application performance monitoring (APM) tools without a clear strategy is like buying a high-end sports car without knowing how to drive. You have powerful capabilities, but no direction. A well-crafted Application Monitoring Requirements Template guides the definition of what data points are crucial, what thresholds signal an impending problem, and how alerts should be routed. It moves teams from a reactive "fix-it-when-it-breaks" mentality to a proactive "prevent-it-from-breaking" one.
Beyond preventing outages, a structured approach helps optimize resource utilization and user experience. By systematically documenting and evaluating monitoring needs, organizations can ensure they’re collecting relevant metrics, logs, and traces without incurring unnecessary costs or data overload. This focused data collection enables faster root cause analysis, more accurate performance tuning, and ultimately, a more stable and efficient application environment. It fosters collaboration, ensuring that developers build with observability in mind and operations teams are equipped to maintain robust systems.
Key Components of an Effective Monitoring Requirements Document
A comprehensive set of monitoring requirements should cover various aspects of an application’s lifecycle and operational needs. It’s not just about CPU usage; it delves into the user experience, business impact, and security posture. Developing a robust monitoring requirements document involves collaboration between development, operations, product management, and even business stakeholders.
Here are the essential categories that your application monitoring strategy should address:
- Application Performance Metrics: These are core to understanding how quickly and efficiently your application responds.
- Response Times: Define acceptable latency for key transactions and API calls.
- Throughput: Specify expected request rates (requests per second, transactions per minute).
- Error Rates: Set thresholds for HTTP errors (5xx, 4xx), application exceptions, and database errors.
- Resource Utilization: Monitor CPU, memory, disk I/O, and network usage for application servers and databases.
- Availability and Uptime: Crucial for understanding if the application is accessible and functional.
- Uptime Targets: Define target uptime percentages (e.g., 99.99%).
- Synthetic Transactions: Outline critical user journeys to simulate and monitor from external locations.
- Health Checks: Specify endpoints for load balancers and orchestrators to check application status.
- Business Metrics: Translate technical performance into business impact.
- Conversion Rates: Monitor success rates for critical business processes (e.g., sign-ups, purchases).
- User Activity: Track active users, session duration, and feature adoption.
- Transaction Volume: Monitor the number of successful and failed business transactions.
- Log Management and Analysis: Essential for detailed troubleshooting and auditing.
- Logging Levels: Standardize WARN, ERROR, INFO, DEBUG logging across services.
- Log Aggregation: Define requirements for centralizing logs for easy search and analysis.
- Key Log Patterns: Identify specific error messages or events that require immediate alerting.
- Security Monitoring: Identify and respond to potential threats.
- Authentication Failures: Monitor suspicious login attempts or account lockouts.
- Vulnerability Scans: Track results and remediation of security scans.
- Network Anomalies: Monitor unusual traffic patterns or unauthorized access attempts.
- Alerting and Notification: How and when stakeholders are informed of issues.
- Severity Levels: Define P1 (critical), P2 (major), P3 (minor) and associated actions.
- Escalation Paths: Outline who gets notified, when, and through which channels (email, SMS, pager).
- Alert Context: Specify what information an alert should contain for quick diagnosis.
- Dashboarding and Reporting: Visualizing data for insights and communication.
- Audience-Specific Views: Define dashboards for operations, development, and business teams.
- Key Performance Indicators (KPIs): Specify critical metrics to be prominently displayed.
- Historical Reporting: Requirements for trend analysis and capacity planning.
Crafting Your Application Monitoring Requirements Template
Building a practical and effective Application Monitoring Requirements Template isn’t a one-time task; it’s an iterative process that evolves with your application. Start by identifying the application’s core functionality and its most critical user journeys. Then, engage all relevant teams to map out potential failure points and their business impact.
- Define Scope and Stakeholders: Clearly delineate which application(s) or services are covered. Identify key stakeholders from product, development, operations, and security who will contribute to and use this document.
- Identify Critical Business Functions: Work with product owners to pinpoint the 2-3 most vital workflows (e.g., "add item to cart," "submit payment," "create user account"). These require the most stringent monitoring.
- Map Technical Components: List all infrastructure and software components that support these critical functions (databases, microservices, third-party APIs, message queues).
- Brainstorm Failure Scenarios: For each critical function and technical component, consider what could go wrong. How would it manifest? What would be the impact?
- Establish Metrics, Logs, and Traces: For each identified failure scenario, determine what data points would indicate the problem. Is it a specific error message in a log, a spike in latency, or a drop in a business metric?
- Set Thresholds and Baselines: Define what constitutes "normal" behavior and what cross a line into an "alert-worthy" event. Establish dynamic baselines where possible.
- Detail Alerting and Escalation: Design a clear communication plan for different alert severities, specifying who is responsible for responding and within what timeframe.
- Plan for Visualization: Decide how the collected data will be presented to various audiences – executive dashboards, operational health monitors, developer troubleshooting views.
- Review and Iterate: Regularly review your application monitoring requirements with your teams. As applications evolve, so too should their monitoring needs. This document should be a living guide, not a static artifact.
Benefits Beyond Uptime
The advantages of a well-defined set of monitoring requirements extend far beyond merely keeping applications running. It fundamentally transforms an organization’s approach to software delivery and operational excellence. By focusing on critical application monitoring, teams gain the ability to proactively identify and resolve issues before they impact users, significantly reducing the mean time to resolution (MTTR). This translates directly into improved customer satisfaction and a stronger brand reputation.
Furthermore, comprehensive operational visibility fosters a culture of data-driven decision-making. Performance trends, resource consumption patterns, and user behavior analytics provide invaluable insights for future development, infrastructure scaling, and product enhancements. It allows teams to move beyond anecdotal evidence, making informed choices about where to invest resources for maximum impact. This strategic foresight is a competitive differentiator in today’s digital economy.
Real-World Application and Best Practices
Putting your monitoring requirements into practice involves integrating them seamlessly into your development and operations workflows. It starts with developers writing code with observability in mind, ensuring appropriate logging, metrics, and tracing are instrumented from the start. For operations teams, it means configuring monitoring tools to collect the specified data, set up alerts based on defined thresholds, and build dashboards that provide actionable insights.
Consider using this structured approach as a checklist during your planning and review stages.
- Integrate into SDLC: Make defining software health monitoring part of your software development lifecycle, not an afterthought. Discuss monitoring during design and sprint planning.
- Automate Where Possible: Leverage infrastructure-as-code and configuration management tools to automate the deployment of monitoring agents and configurations.
- Test Your Alerts: Periodically simulate failure conditions to ensure alerts trigger correctly and escalation paths function as expected. There’s nothing worse than finding out your monitoring system failed to alert you when an actual outage occurs.
- Right-Size Your Tools: Choose monitoring solutions that align with your defined requirements, budget, and team’s technical expertise. Avoid over-engineering with complex tools if simpler ones suffice.
- Continuous Improvement: Regularly review incident reports and post-mortems to identify gaps in your monitoring requirements or system. Use these insights to refine your template and improve your overall monitoring posture.
Frequently Asked Questions
What is the primary goal of defining application monitoring requirements?
The primary goal is to establish a clear, shared understanding of what constitutes healthy application performance, availability, and security, ensuring that all critical aspects are monitored effectively to proactively identify and resolve issues before they impact users or business operations.
Who should be involved in creating a monitoring requirements document?
Key stakeholders from various departments should be involved, including product managers (for business context), software developers (for application internals), operations/SRE teams (for infrastructure and tooling), security teams (for threat detection), and potentially business analysts.
How often should application monitoring requirements be reviewed and updated?
Monitoring requirements should be treated as a living document. They should be reviewed at least quarterly, or more frequently if there are significant application updates, architectural changes, new feature deployments, or after major incidents. Regular reviews ensure they remain relevant and effective.
Is this template only for large enterprises or can small businesses use it too?
A structured approach to defining operational metrics is beneficial for organizations of all sizes. While large enterprises might have more complex needs, small businesses can adapt the core principles to ensure their critical applications are reliably monitored, scaled down to fit their specific resources and application landscape.
The journey to building resilient and high-performing applications is continuous, and effective monitoring is its compass. By investing time and effort into creating a thorough Application Monitoring Requirements Template, organizations can shift from merely reacting to problems to proactively managing their application health. This structured approach fosters clearer communication, reduces operational overhead, and ultimately drives better business outcomes through enhanced reliability and efficiency.
Embrace the power of a well-defined strategy for observing your software. It’s not just about collecting data; it’s about gaining intelligence that empowers your teams to build, deploy, and operate applications with confidence. Start documenting your application’s vital signs today and pave the way for a more stable, performant, and successful digital future.