In an era where digital threats constantly evolve and data breaches dominate headlines, the imperative for robust cybersecurity has never been clearer. Organizations across every sector are grappling with the challenge of safeguarding their assets, ensuring data privacy, and maintaining operational continuity against sophisticated adversaries. Yet, often overlooked in the rush to deploy new technologies is the foundational step of explicitly defining *what* security measures are actually needed, and *why*. This is where a structured approach to articulating security requirements becomes not just beneficial, but absolutely critical.
A well-crafted security requirements document serves as the bedrock for building secure systems and applications. It acts as a compass, guiding development teams, architects, and stakeholders through the complex landscape of cybersecurity by clearly outlining the protective measures, controls, and compliance standards that must be integrated. Without this precise blueprint, security efforts can become fragmented, reactive, and ultimately, ineffective, leaving organizations vulnerable to preventable risks. This article delves into the significance of such a document and how leveraging a robust Security Requirements Document Template can empower your organization to build security in from the ground up, rather than bolting it on as an afterthought.
The Criticality of Defining Security Upfront
The modern software development lifecycle is fraught with potential security pitfalls if not properly managed. Introducing security measures late in the development cycle, or attempting to retrofit them after a system is already built, invariably leads to increased costs, delays, and often, compromises in the quality and effectiveness of the security controls. This “shift left” philosophy – integrating security considerations at the earliest possible stages – is a fundamental principle for effective cybersecurity.
By systematically documenting security needs, an organization can proactively identify and mitigate risks before they manifest into costly vulnerabilities. This foresight allows for better resource allocation, clearer communication among teams, and a more resilient end product. Furthermore, the regulatory landscape, with mandates like GDPR, HIPAA, and CCPA, demands demonstrable due diligence in protecting sensitive information, making a formal articulation of security measures a legal and ethical necessity.
Benefits of a Structured Security Specification
Adopting a formal framework for your cybersecurity requirements documentation brings a multitude of advantages that extend beyond mere compliance. It transforms security from an abstract concept into a set of actionable, measurable objectives. A well-organized security specification document ensures that security is an inherent quality of your systems, not an optional feature.
These benefits ripple across an organization, improving efficiency, reducing risk, and fostering a culture of security. From developers to executives, everyone gains a clearer understanding of their role in protecting the organization’s digital assets.
- **Improved Communication and Alignment:** Provides a common language and understanding across development, operations, security, and business teams, ensuring everyone is on the same page regarding security expectations. It eliminates ambiguity and reduces misinterpretations.
- **Reduced Risk and Cost:** Identifying and addressing security vulnerabilities during the design and development phases is significantly less expensive than remediating them after deployment. Early integration prevents costly rework and potential breach expenses.
- **Enhanced Compliance and Audit Readiness:** A clear record of security requirements and their implementation greatly simplifies demonstrating adherence to industry standards, regulatory mandates, and internal policies during audits.
- **Consistent Security Posture:** Ensures a standardized approach to security across different projects and systems, leading to a more uniform and robust organizational security posture. This consistency simplifies management and reduces complexity.
- **Faster Development Cycles (Paradoxically):** While seemingly adding an upfront step, clearly defined security requirements prevent late-stage security-related blockers and rework, ultimately streamlining the development process.
- **Better Vendor Management:** Provides a clear basis for communicating security expectations to third-party vendors and assessing their compliance with your organization’s security standards.
Key Components of a Robust Security Requirements Document
A comprehensive security requirements framework is more than just a checklist; it’s a living document that captures the full spectrum of security considerations for a given system or application. While specific content will vary based on project scope and industry, certain core elements are universally essential. These components ensure that all facets of security, from technical controls to operational procedures, are thoroughly addressed.
When developing a strong security specification, consider including these vital sections:
- **Executive Summary:** A concise overview of the document’s purpose, scope, and key security objectives. It should quickly inform high-level stakeholders about the document’s essence.
- **Project Overview and Scope:** Details about the system or application being secured, its primary functions, boundaries, and any interfaces with other systems. This sets the context for all subsequent requirements.
- **Threat Model Summary:** An outline of identified threats, vulnerabilities, and potential attack vectors relevant to the system. This section often includes a summary of the risks, their likelihood, and potential impact.
- **Security Goals and Objectives:** High-level strategic aims for the system’s security, often aligned with business objectives. These are typically broad statements of intent (e.g., “ensure data confidentiality,” “maintain system availability”).
-
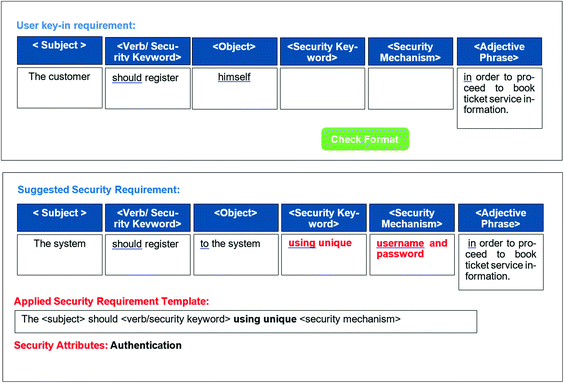
**Functional Security Requirements:** Specific, testable requirements that describe *what* the system must do to enforce security. Examples include:
- **Authentication:** How users and systems verify their identity (e.g., “The system shall support multi-factor authentication for all administrative access.”).
- **Authorization:** How the system controls access to resources based on identity (e.g., “Users shall only be able to view data relevant to their assigned department.”).
- **Auditing and Logging:** What security-relevant events must be recorded (e.g., “All failed login attempts shall be logged with a timestamp, username, and source IP address.”).
- **Data Confidentiality:** How sensitive data is protected from unauthorized disclosure (e.g., “Sensitive customer data shall be encrypted both in transit and at rest.”).
-
**Non-Functional Security Requirements:** Requirements detailing *how* the system must behave to maintain security, often related to system attributes. Examples include:
- **Resilience:** The system’s ability to withstand and recover from attacks (e.g., “The system shall remain operational during a denial-of-service attack up to X requests per second.”).
- **Performance:** How security controls impact system speed (e.g., “Authentication processes shall complete within 500 milliseconds for 95% of users.”).
- **Scalability:** How security scales with system growth.
- **Availability:** Ensuring the system is accessible when needed.
- **Compliance and Regulatory Requirements:** Specific laws, regulations, industry standards (e.g., PCI DSS, ISO 27001), and internal policies that the system must adhere to. This section often lists relevant controls or mandates.
- **Security Architecture and Design Principles:** High-level architectural decisions and guiding principles that underpin the system’s security design (e.g., “Principle of Least Privilege,” “Defense in Depth”).
- **Testing and Verification Requirements:** How the implemented security controls will be validated and tested, including penetration testing, vulnerability assessments, and security code reviews.
- **Incident Response and Recovery Requirements:** Outlines procedures for detecting, responding to, and recovering from security incidents, ensuring business continuity.
Crafting Effective Security Requirements: Best Practices
Merely listing security considerations isn’t enough; the way these requirements are formulated significantly impacts their effectiveness. Vague, untestable, or overly broad statements can lead to misinterpretations and weak implementations. The goal is to create clear, unambiguous, and actionable security criteria.
Begin the process early, ideally during the initial concept and design phases of a project. Engaging a diverse group of stakeholders, including business owners, developers, architects, and security specialists, ensures a holistic perspective and buy-in. Foster a collaborative environment where security is seen as a shared responsibility, not solely owned by a single department.
Furthermore, ensure that each requirement is specific, measurable, achievable, relevant, and time-bound (SMART). For instance, instead of "the system should be secure," aim for "all user passwords shall be at least 12 characters long, include a mix of upper/lowercase letters, numbers, and special characters, and be hashed using PBKDF2 with a minimum of 100,000 iterations." Regularly review and refine these security needs as the project evolves and new threats emerge.
Customizing Your Security Requirements Document
While a general Security Requirements Document Template provides an excellent starting point, effective implementation requires customization. No two projects or organizations are identical, and a ‘one-size-fits-all’ approach rarely suffices for comprehensive security. Adapting your cybersecurity requirements framework to the specific context is paramount for relevance and effectiveness.
Consider the unique attributes of your project. Is it a small internal tool or a large-scale public-facing application handling sensitive financial data? The criticality of the system, the type of data it processes, and its potential impact on business operations should heavily influence the depth and breadth of your security specifications. Industry-specific regulations (e.g., HIPAA for healthcare, PCI DSS for credit card processing) must be integrated directly into your document, ensuring all legal and compliance obligations are met. The underlying technology stack, whether cloud-native, on-premise, or a hybrid environment, will also dictate specific technical controls and architectural requirements. A tailored approach ensures that your documented security measures are both appropriate and optimally effective for your unique environment.
Frequently Asked Questions
What is a security requirements document?
A security requirements document is a formal specification that outlines the necessary security controls, measures, and standards a system or application must implement to protect its assets, data, and users from threats. It serves as a blueprint for building security into the design and development process.
Who typically uses a security specification document?
This document is primarily used by security architects, software developers, quality assurance testers, project managers, and compliance officers. It guides design, development, testing, and auditing activities, ensuring all stakeholders understand and contribute to the system’s security posture.
How often should security requirements be updated?
Security requirements should be a living part of the project lifecycle. They should be reviewed and updated whenever there are significant changes to the system’s functionality, architecture, or environment, or when new threats, vulnerabilities, or compliance regulations emerge. At a minimum, a formal review should occur at key project milestones or annually.
Is a security requirements document different from a threat model?
Yes, they are distinct but complementary. A threat model identifies potential threats and vulnerabilities to a system, assessing their risk. A security requirements document then specifies the controls and measures needed to mitigate those identified risks. The threat model often informs and drives the creation of specific security requirements.
Can a small project benefit from a formal security specification?
Absolutely. Even small projects benefit significantly from a structured approach to defining security. While the document might be less extensive, formalizing security requirements ensures that critical protections aren’t overlooked. It instills good security practices from the start, saving time and resources in the long run.
Embracing a systematic approach to documenting your security needs is no longer optional; it’s a strategic imperative. By leveraging a comprehensive Security Requirements Document Template, organizations can transform abstract security concerns into tangible, actionable requirements that guide development and safeguard valuable assets. This proactive stance ensures that security is woven into the very fabric of your systems, making them resilient by design.
The journey to building truly secure systems begins with clarity and intentionality. A well-defined security requirements document provides that clarity, acting as the single source of truth for all security-related decisions throughout a project’s lifecycle. Invest the time and effort upfront to articulate your security vision, and you’ll reap the rewards of enhanced protection, reduced risk, and greater confidence in your digital infrastructure. Start building security in, today.