In an era defined by constant digital transformation, the safeguarding of sensitive information has transcended from a technical concern to a fundamental business imperative. Organizations of all sizes, from nascent startups to multinational corporations and government agencies, face an ever-evolving landscape of cyber threats, regulatory demands, and the critical need to maintain public trust. This complex environment makes a clear, comprehensive, and adaptable information security strategy not just a best practice, but an absolute necessity for survival and growth.
This is precisely where a Nist Information Security Policy Template enters the picture, offering a beacon of guidance in what can often feel like an overwhelming storm of cybersecurity challenges. It provides a structured, authoritative foundation upon which any organization can build its robust security posture, ensuring that policies are not only well-defined but also aligned with internationally recognized standards. For anyone tasked with establishing or refining their organization’s data protection strategies, understanding and leveraging such a template can be a game-changer, transforming abstract security concepts into actionable, enforceable workplace rules and procedures.
Why Nist Information Security Policy Template is Essential
The digital age, while offering unprecedented opportunities, also presents a minefield of risks. Data breaches are no longer headline anomalies but daily occurrences, threatening financial stability, reputation, and customer loyalty. In this precarious environment, the Nist Information Security Policy Template stands out as an indispensable tool, rooted in the National Institute of Standards and Technology (NIST) frameworks, which are widely recognized for their rigor and adaptability. Its importance stems from several critical factors relevant to today’s organizations.
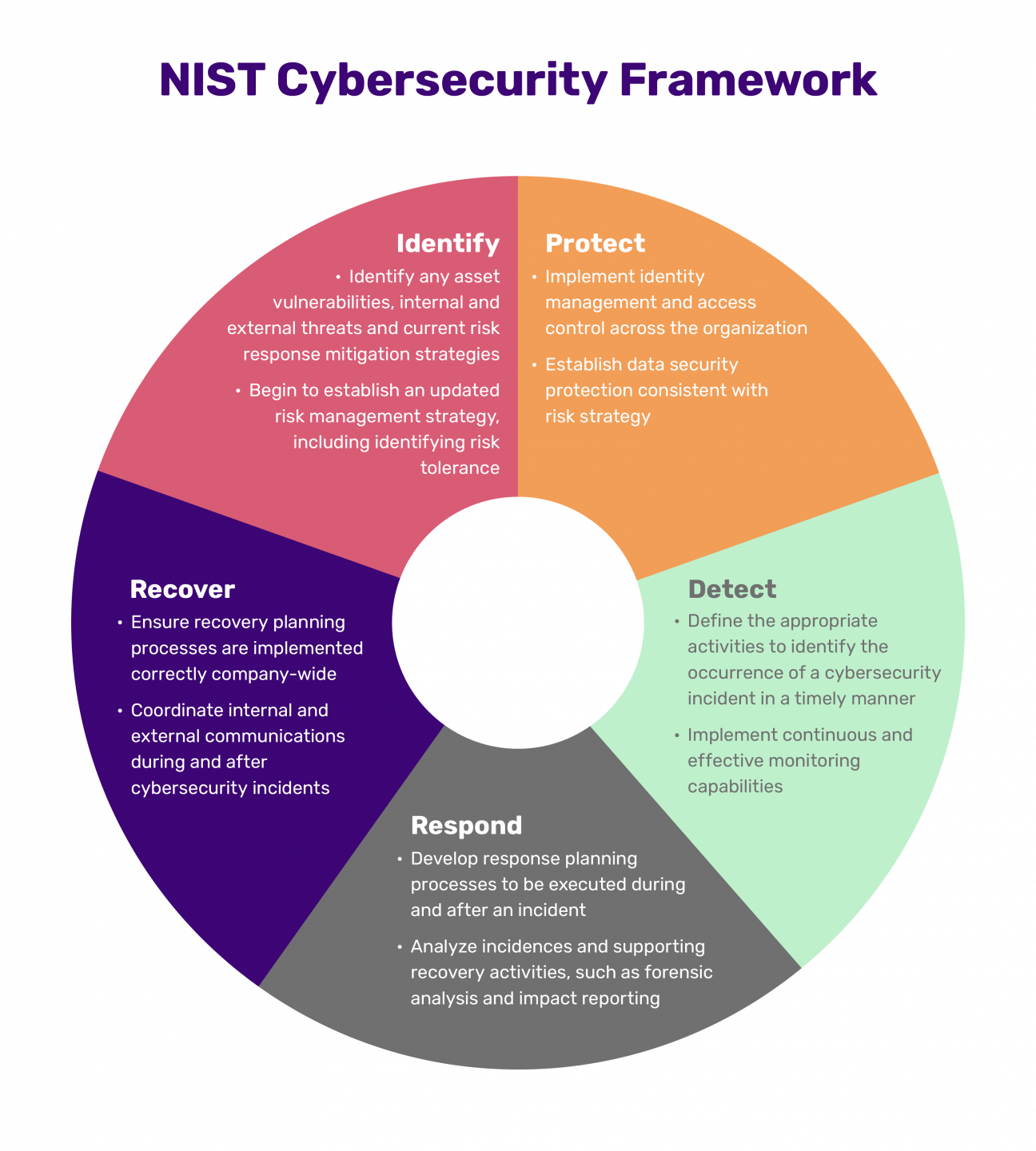
Firstly, regulatory compliance has become a non-negotiable aspect of doing business. Whether it’s HIPAA for healthcare, GDPR for data privacy in Europe, CCPA in California, or the emerging CMMC standard for defense contractors, organizations face stringent legal terms and obligations regarding how they protect data. A Nist Information Security Policy Template provides a powerful head start in meeting these diverse requirements, offering a pre-aligned structure that addresses common compliance domains, making the journey toward audit readiness significantly smoother.
Secondly, the sheer volume and sophistication of cyber threats demand a proactive, well-documented defense. Relying on ad-hoc security measures or hoping for the best is no longer viable. This template helps organizations articulate a clear set of security controls, outlining how they will protect their assets, manage risk, and respond to incidents. It shifts the focus from reactive damage control to a strategic, preventive approach, enhancing the overall data security posture and demonstrating a commitment to responsible information governance.
Finally, trust is the currency of the digital economy. Customers, partners, and stakeholders expect organizations to safeguard their personal and proprietary information diligently. Adopting a framework like the Nist Information Security Policy Template signals a serious commitment to robust security practices, building confidence and fostering stronger relationships. It’s not just about avoiding penalties; it’s about safeguarding the very foundation of your business operations and brand reputation.
Key Benefits of Using Nist Information Security Policy Template
Leveraging a Nist Information Security Policy Template offers a multitude of tangible benefits that extend far beyond simply having a document on file. It fundamentally transforms an organization’s approach to information security, embedding best practices into its operational DNA.
One of the most significant advantages is standardization and consistency. Instead of piecing together disparate policies or relying on individual interpretations, the template provides a coherent, unified framework. This ensures that all employees, departments, and even third-party vendors adhere to a consistent set of security standards and workplace rules, significantly reducing the likelihood of vulnerabilities arising from inconsistent practices.
Efficiency and resource optimization are also paramount. Developing a comprehensive set of information security policies from scratch is a monumental undertaking, demanding significant time, expertise, and financial investment. A Nist Information Security Policy Template acts as a highly effective starting point, providing pre-vetted content and structure that can be adapted, rather than created anew. This dramatically reduces the effort required, allowing organizations to allocate resources more strategically.
Furthermore, these templates are invaluable for risk reduction. By clearly defining acceptable use policies, access controls, incident response procedures, and data handling protocols, they minimize human error and system vulnerabilities. Employees are given clear obligations and guidelines, reducing the chances of accidental data exposure or malicious activity. This proactive approach helps identify and mitigate potential threats before they escalate into costly breaches.
For organizations navigating complex regulatory landscapes, the Nist Information Security Policy Template is a powerful aid in achieving and maintaining compliance. Its alignment with NIST frameworks means that many of the core elements required by various laws and industry standards are already present. This streamlines audit processes, provides clear evidence of due diligence, and helps avoid costly fines and legal repercussions associated with non-compliance. It essentially provides a roadmap for meeting contractual and legal terms.
Finally, effective security policies foster improved communication and accountability. By clearly outlining roles, responsibilities, and expected behaviors regarding information security, the template clarifies who is responsible for what. This transparency improves collaboration between IT, HR, legal, and operational teams, ensuring that everyone understands their part in maintaining a secure environment and reinforcing the importance of data security across the organization.
Customizing Nist Information Security Policy Template for Different Needs
While the Nist Information Security Policy Template provides an excellent, robust foundation, it’s crucial to understand that it serves as a starting point, not a one-size-fits-all solution. No two organizations are exactly alike; their risk profiles, operational contexts, industry regulations, and technological infrastructures vary widely. Therefore, effective implementation hinges on judicious customization and adaptation.
The process of tailoring the Nist Information Security Policy Template begins with a thorough understanding of your organization’s unique environment. Consider your industry: a healthcare provider will have different concerns (e.g., HIPAA, patient confidentiality) than a financial institution (e.g., PCI DSS, financial transaction security) or a manufacturing company (e.g., intellectual property, operational technology security). The type and sensitivity of data processed, stored, or transmitted are primary drivers for policy specificity. For instance, an organization handling highly classified government information will require more stringent controls than one dealing primarily with public-facing marketing data.
Organizational size and complexity also play a significant role. A small business with a handful of employees might consolidate certain policies or simplify procedures, while a large enterprise with global operations will need more detailed, multi-layered policies addressing diverse geographic regulations and distributed teams. The existing IT infrastructure, including cloud usage, remote work policies, and legacy systems, must also be factored in, ensuring that the policies are practical and enforceable within your current technical landscape.
Furthermore, a critical step involves aligning the template with your organization’s specific risk appetite and business objectives. What level of risk is acceptable? What are your most critical assets that absolutely must be protected? These questions help prioritize security controls and allocate resources effectively. Customization should also involve integrating the policies with existing HR policies and workplace rules, making sure they complement rather than contradict established internal guidelines, such as acceptable use agreements for employee conduct or data retention policies.
Engaging key stakeholders, including legal counsel, IT leadership, HR, and relevant department heads, throughout the customization process is vital. Their input ensures that the adapted Nist Information Security Policy Template is not only technically sound and legally compliant but also operationally feasible and effectively communicated across the entire organization.
Important Elements to Include in Nist Information Security Policy Template
A truly comprehensive Nist Information Security Policy Template, once customized, should clearly articulate an organization’s stance and procedures on a wide range of security domains. While the specific list of elements might vary based on the organization’s unique profile, the following represent core components that should almost universally be included:
- Policy Scope and Purpose: Clearly define what the policy covers (e.g., all information assets, systems, employees, contractors) and its overarching goals (e.g., protecting confidentiality, integrity, availability of information).
- Roles and Responsibilities: Delineate who is accountable for what. This includes roles for management, IT staff, HR, employees, and any designated Information Security Officer. Clear obligations ensure no gaps in oversight.
- Information Classification and Handling: Establish categories for data (e.g., public, internal, confidential, restricted) and define how each category must be stored, processed, transmitted, and disposed of to maintain data security.
- Access Control: Detail policies for granting, reviewing, and revoking access to systems, networks, applications, and physical facilities. This includes rules for user authentication, password management, and least privilege principles.
- Incident Response and Management: Outline procedures for identifying, reporting, containing, eradicating, recovering from, and learning from security incidents. This section is critical for minimizing the impact of breaches.
- Security Awareness and Training: Specify requirements for ongoing security training for all employees and contractors, covering topics like phishing awareness, social engineering, and general workplace rules for data handling.
- Risk Assessment and Management: Describe the process for identifying, analyzing, evaluating, and treating information security risks. This includes defining risk tolerance and mitigation strategies.
- Business Continuity and Disaster Recovery: Address how the organization will maintain critical operations and restore systems and data in the event of a significant disruption or disaster.
- Vendor and Third-Party Security: Establish policies for evaluating, managing, and monitoring the security posture of third-party vendors and service providers who have access to organizational data or systems. These policies often involve contracts and legal terms.
- Acceptable Use Policy: Clearly define the acceptable and unacceptable uses of organizational IT resources, including networks, hardware, software, and internet access, by employees and contractors.
- Physical Security: Detail controls for protecting physical access to facilities, data centers, and equipment where sensitive information is processed or stored.
- Audit and Compliance: Explain the organization’s commitment to regular audits, reviews, and assessments to ensure compliance with internal policies, external regulations, and contractual agreements. This ensures the policies are effective and enforced.
Tips on Design, Usability, and Implementation
Having a robust Nist Information Security Policy Template is only half the battle; its true value is realized through effective design, usability, and thoughtful implementation. A technically perfect policy that nobody reads or understands is effectively useless.
For Design and Usability:
Prioritize clarity and conciseness. Policies should be written in plain language, avoiding overly technical jargon wherever possible. If technical terms are necessary, provide clear definitions. Use a logical structure with headings, subheadings, and bullet points to break up text and make it easy to scan and comprehend. A professional, clean layout enhances readability, whether the policy is viewed digitally or printed. Consider using a consistent branding identity, perhaps incorporating your company logo and color scheme, to make the document feel integrated with your organization’s internal communications. For digital versions, ensure the document is easily searchable and accessible via an internal portal or intranet, making it simple for employees to quickly find relevant information, like specific workplace rules or data security guidelines. Version control is also paramount; clearly indicate the policy version number and effective date.
For Implementation:
The journey from policy creation to effective implementation involves strategic communication and continuous engagement. Start with a comprehensive communication plan: simply publishing the policy isn’t enough. Organizations must actively educate employees about the Nist Information Security Policy Template, its importance, and their individual responsibilities. This often involves mandatory security awareness training programs, interactive workshops, and regular reminders.
Furthermore, integrate the policies into existing HR and IT processes. For instance, the acceptable use policy should be part of the new employee onboarding process, and data classification guidelines should be built into IT system design and development. Establish clear enforcement mechanisms and communicate the consequences of non-compliance. This isn’t about fostering a culture of fear, but rather one of accountability and shared responsibility. Finally, remember that information security is not a static state. The Nist Information Security Policy Template, once implemented, must be regularly reviewed, updated, and adapted to reflect changes in technology, threats, regulations, and organizational structure. Schedule periodic reviews (e.g., annually or biennially) and update cycles to ensure the policies remain relevant and effective.
In today’s interconnected world, an organization’s resilience and reputation are increasingly tied to the strength of its cybersecurity posture. The Nist Information Security Policy Template offers a proven, structured pathway to achieve this strength, moving beyond generic guidelines to provide a customized, actionable framework. By meticulously detailing policies for everything from data classification to incident response, it empowers organizations to proactively manage risks and comply with complex regulatory landscapes.
Embracing and meticulously adapting a Nist Information Security Policy Template is more than just a procedural task; it’s a strategic investment in the future of your enterprise. It cultivates a culture of security awareness, minimizes vulnerabilities, and builds critical trust with customers and partners. For any organization committed to safeguarding its digital assets and ensuring operational continuity, considering this template as a foundational piece of their security architecture is not just a practical solution, but an absolute necessity for enduring success.