In today’s hyper-connected digital landscape, software applications are the lifeblood of businesses, driving innovation and facilitating critical operations. Yet, with every new line of code and every deployed feature, a new potential attack surface emerges. The relentless tide of cyber threats means that security can no longer be an afterthought, tacked on at the end of the development cycle.
Proactive security starts at the very beginning – in the planning and design phases. This is where defining clear, comprehensive security expectations becomes paramount, ensuring that every application is built with resilience and protection baked in from the ground up. A well-structured Application Security Requirements Template provides this foundational guidance, making it a strategic imperative for safeguarding your digital assets and maintaining user trust.
Why Robust Application Security Requirements Matter
Building secure applications requires more than just skilled developers and penetration testing; it demands a foundational understanding of what “secure” truly means for your specific context. Without clearly articulated security specifications, development teams often operate in a grey area, leading to vulnerabilities, rework, and increased costs down the line. A well-defined set of security criteria acts as a blueprint, guiding every stage of the Software Development Life Cycle (SDLC).
Implementing a comprehensive guide for application security requirements brings numerous benefits. It minimizes security debt by addressing issues early, improves compliance with regulatory standards like GDPR or HIPAA, and significantly reduces the risk of costly data breaches. Ultimately, it fosters a culture of security throughout the organization, making everyone accountable for the protection of digital assets.
Key Components of a Comprehensive Security Requirements Guide
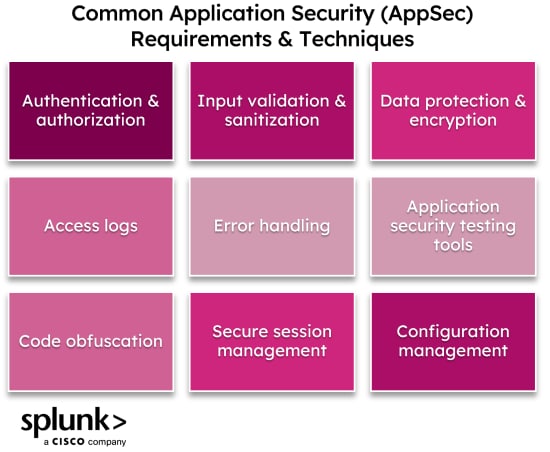
A robust document outlining security criteria for software applications isn’t just a simple checklist; it’s a living guide that covers a multitude of domains. It translates high-level security policies into actionable engineering tasks, ensuring that developers, QA testers, and product managers all understand their role in building resilient software. Here are some fundamental areas typically covered:
- **Authentication:** Specifies how users verify their identity, including multi-factor authentication (MFA) requirements, password policies, and integration with enterprise identity providers.
- **Authorization:** Defines user roles, permissions, and access controls, detailing what actions authenticated users can perform and what resources they can access based on their privileges.
- **Data Protection:** Covers requirements for data at rest and in transit, including encryption standards, data sanitization, privacy controls (e.g., pseudonymization), and secure data storage practices.
- **Input Validation:** Outlines rules for validating all user and system inputs to prevent common injection attacks like SQL injection, XSS, and command injection.
- **Error Handling & Logging:** Details secure error handling practices to avoid information leakage, and requirements for comprehensive, tamper-proof logging of security-relevant events for auditing and incident response.
- **Session Management:** Addresses how user sessions are established, maintained, and securely terminated, including session timeout policies and protection against session hijacking.
- **API Security:** Specifies security measures for APIs, encompassing authentication, authorization, rate limiting, and protection against common API vulnerabilities.
- **Cryptography:** Defines approved cryptographic algorithms, key management practices, and proper implementation of cryptographic functions for various data protection needs.
- **Configuration Management:** Sets standards for secure configuration of application components, servers, and databases, minimizing default credentials and unnecessary services.
- **Supply Chain Security:** Addresses requirements for third-party components, libraries, and services, including vulnerability scanning, license management, and secure integration practices.
- **Resilience & Availability:** Specifies requirements to ensure the application remains available and responsive under various conditions, including denial-of-service attack mitigation and disaster recovery considerations.
Leveraging an Application Security Requirements Template in Your SDLC
Integrating an Application Security Requirements Template effectively into your development workflow transforms it from a static document into a dynamic tool for secure software delivery. Its utility spans across multiple phases of the Software Development Life Cycle, acting as a consistent reference point for all stakeholders.
During the **design phase**, architects use the security specification document to inform their architectural decisions, ensuring that security controls are designed into the system from the outset. This early consideration prevents costly redesigns later. For **development teams**, the detailed criteria serve as clear guidelines for coding practices, helping them build features securely and consistently across modules.
In the **testing phase**, QA and security testers rely on these security feature lists to create robust test cases, including functional security tests, vulnerability assessments, and penetration tests. This ensures that the implemented controls meet the specified requirements. Finally, during **deployment and operations**, the document provides essential information for secure configuration, monitoring, and incident response planning, facilitating the ongoing secure posture of the application.
Tailoring Your Security Requirements Guide for Optimal Impact
While a general framework is an excellent starting point, no two applications are exactly alike, and therefore, no single security requirements document will fit every scenario perfectly. Customization is key to ensuring that your security specifications are relevant, actionable, and proportionate to the risks faced by your specific application.
Begin by assessing the **risk profile** of your application. Is it handling highly sensitive personal data? Is it a public-facing e-commerce platform? Does it manage critical infrastructure? The answers to these questions will dictate the depth and rigor of your application’s security requirements. High-risk applications will naturally demand a more stringent and extensive set of controls compared to internal, low-impact tools.
Consider the **technology stack** and **deployment environment**. Requirements for a microservices architecture deployed in the cloud will differ significantly from a monolithic on-premise application. Integrate industry-specific compliance needs, such as PCI DSS for payment applications or HIPAA for healthcare data. Engaging with legal and compliance teams early in this process is crucial to ensure all necessary regulatory obligations are met and documented within the secure application development checklist.
Best Practices for Implementing Your Application Security Requirements
Simply having a document isn’t enough; its successful implementation requires a strategic approach. Effective integration into your organizational processes ensures that the security criteria translate into tangible security improvements rather than just remaining theoretical.
- **Start Early, Iterate Often:** Introduce the security specification document at the very beginning of the project lifecycle and refine it iteratively as the application evolves and new threats emerge. Security is not a one-time task.
- **Foster Collaboration:** Involve all relevant stakeholders – developers, architects, QA, product owners, operations, and security teams – in defining and reviewing the digital product security needs. This broad involvement ensures buy-in and practical applicability.
- **Automate Where Possible:** Integrate security requirements into your CI/CD pipeline. Use static application security testing (SAST), dynamic application security testing (DAST), and software composition analysis (SCA) tools to automatically check for compliance with secure coding requirements.
- **Provide Training and Support:** Ensure teams have the necessary knowledge and resources to meet the defined secure software guidelines. Offer regular training on secure coding practices and the specific expectations outlined in the enterprise application security needs document.
- **Regularly Review and Update:** The threat landscape, technology stack, and business needs are constantly changing. Schedule periodic reviews of your software assurance framework to keep it current and effective.
Frequently Asked Questions
What is an application security requirements template?
An application security requirements template is a structured document that outlines the necessary security controls, features, and practices that must be incorporated into a software application throughout its development lifecycle. It serves as a guide for developers, testers, and product managers to ensure the application meets defined security standards and mitigates potential risks.
Who benefits most from using a security requirements template?
Primarily, development teams (developers, architects, QA), security teams, product managers, and project managers benefit. It provides clear guidance for building secure software, simplifies security testing, streamlines compliance efforts, and helps manage security debt more effectively across the organization.
How does a security requirements template differ from a security policy?
A security policy is a high-level statement of an organization’s overall security posture, objectives, and rules. A security requirements template, conversely, translates those high-level policies into specific, actionable, and testable technical requirements for individual applications. It bridges the gap between organizational policy and practical implementation.
Can I use a security requirements template for all types of applications?
Yes, while the core principles remain the same, a security requirements template is designed to be customizable. You should tailor it to the specific context, technology, risk profile, and compliance needs of each application, whether it’s a web application, mobile app, desktop application, or API service.
How often should these security criteria documents be updated?
Security criteria documents should be reviewed and updated regularly, ideally annually or whenever there are significant changes to the application’s architecture, technology stack, regulatory environment, or the prevailing threat landscape. Continuous monitoring and feedback from security assessments also inform necessary revisions.
Embracing a proactive approach to application security, formalized through a well-crafted Application Security Requirements Template, is no longer a luxury but a fundamental necessity for any organization operating in the digital realm. It empowers teams to build with confidence, knowing that security considerations are embedded from inception, rather than bolted on as an afterthought.
By systematically defining and integrating security requirements, businesses can significantly reduce their attack surface, protect sensitive data, and uphold the trust placed in them by their users and customers. This strategic investment in secure application development ultimately translates into reduced operational risks, enhanced brand reputation, and a stronger foundation for sustained digital growth and innovation. Don’t just build applications; build secure applications.