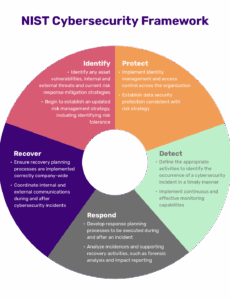
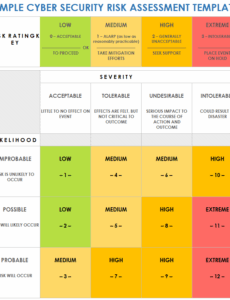
In an era defined by constant digital innovation, the flip side of progress often manifests as an escalating landscape of cyber threats. From sophisticated phishing attacks to widespread ransomware campaigns, […]
Category: Policy Template
Information Security Policy Template Uk
In an age where data breaches are daily headlines and cyber threats evolve at an alarming pace, the importance of a robust information security framework cannot be overstated. Organizations, regardless […]
Information Security Policy Template Nist
In today’s interconnected digital landscape, safeguarding sensitive information isn’t just a best practice—it’s an absolute imperative. From multinational corporations to budding startups, every organization faces an unrelenting barrage of cyber […]
Information Risk Management Policy Template
In an increasingly digital world, where data is often a company’s most valuable asset, the notion of risk management has evolved from a niche concern to a top-tier business imperative. […]
Information Security Risk Assessment Policy Template
In today’s interconnected digital landscape, the question is no longer *if* a security incident will occur, but *when* and *how* prepared your organization will be. Every business, from the nimble […]
Hybrid Working Policy Template Uk
In the modern professional landscape, the traditional office model has undergone a seismic shift. The pandemic accelerated a move towards flexible working arrangements, and now, hybrid working has emerged as […]
Human Rights Policy Template South Africa
In an increasingly interconnected world, where corporate actions are scrutinized on a global stage, the concept of human rights extends far beyond national borders. For organizations operating internationally or engaging […]
Human Resource Management Policy Template
In the dynamic landscape of modern business, managing human capital effectively is not just an operational necessity; it’s a strategic imperative. Organizations, regardless of size or industry, face a myriad […]
Hybrid Work Model Policy Template
The modern workplace has undergone a seismic shift, forever altering our perceptions of productivity, collaboration, and employee well-being. What was once a niche concept has now become a mainstream expectation: […]
Hiv Policy Template South Africa
The global fight against HIV/AIDS has seen remarkable progress, yet the enduring legacy of the epidemic continues to demand sophisticated and compassionate policy responses. For organizations, particularly those operating in […]