In today’s hyper-connected world, where digital tools are the backbone of virtually every organization, the seamless integration of technology comes with a crucial responsibility: ensuring its proper and secure use. From small businesses to large corporations, educational institutions to non-profit organizations, computers and networks are indispensable. However, without clear guidelines, this powerful infrastructure can become a liability, leading to security breaches, productivity dips, and even legal complications. This is precisely where a well-crafted Computer Acceptable Use Policy Template becomes not just an asset, but a fundamental necessity.
A robust Computer Acceptable Use Policy Template serves as the cornerstone of digital governance, providing a clear framework for how employees, students, or members are expected to interact with an organization’s IT resources. It’s a proactive measure designed to protect valuable data, maintain system integrity, and foster a productive, secure digital environment for everyone. Whether you’re an HR professional looking to standardize workplace rules, an IT manager aiming to bolster cybersecurity, or a business owner striving for operational efficiency, understanding and implementing such a template is a strategic move that pays dividends in peace of mind and operational resilience.
Why a Computer Acceptable Use Policy Template is Essential
The digital landscape is constantly evolving, bringing with it both incredible opportunities and significant risks. In this environment, a Computer Acceptable Use Policy Template isn’t just good practice; it’s absolutely critical for safeguarding an organization’s most valuable assets. Cyber threats, from phishing scams to ransomware attacks, are increasingly sophisticated, making every user a potential entry point for malicious actors. Without clear guidelines, employees might inadvertently engage in practices that compromise data security, such as using unapproved software, accessing unsecured websites, or sharing sensitive information through unauthorized channels.
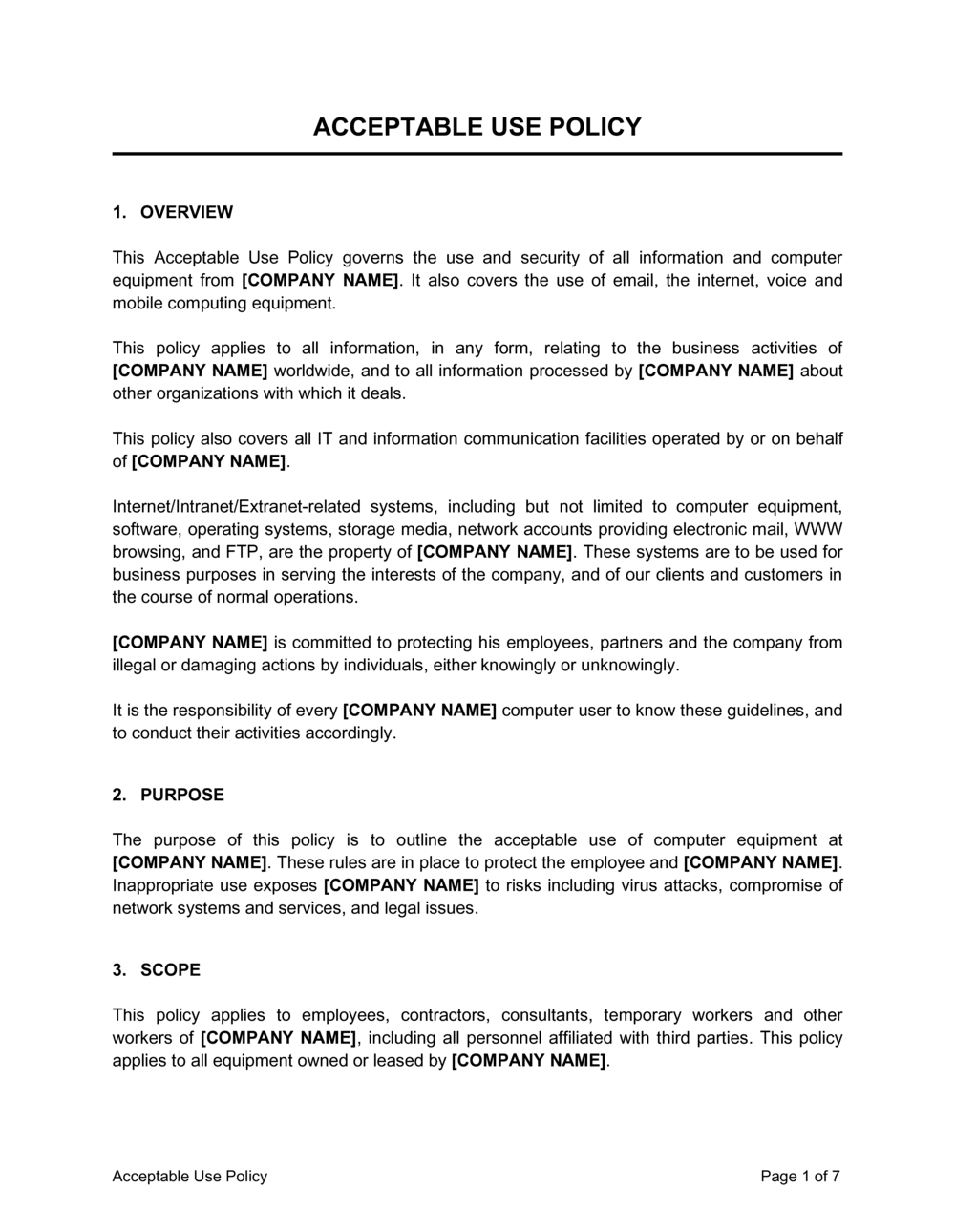
Furthermore, a comprehensive Computer Acceptable Use Policy Template addresses crucial aspects of legal compliance. Depending on the industry and the nature of the data handled, organizations may be subject to various regulations, such as HIPAA for healthcare, GDPR or CCPA for data privacy, and Sarbanes-Oxley for financial reporting. These regulations often mandate specific controls around data handling and system access. An effective policy helps ensure that all digital interactions align with these legal obligations, thereby mitigating the risk of costly fines, lawsuits, and reputational damage. It clearly outlines acceptable behavior, helping to set expectations and responsibilities for every individual who accesses the company’s IT infrastructure.
Beyond security and compliance, a Computer Acceptable Use Policy Template plays a vital role in maintaining productivity and a positive work environment. It sets clear workplace rules regarding the use of company resources for personal activities, defining boundaries to prevent excessive non-work-related internet use or unauthorized software installations that can consume bandwidth and introduce vulnerabilities. By establishing clear expectations for ethical conduct and professional behavior online, it helps reduce potential conflicts and ensures that IT resources are primarily used to advance organizational goals. Ultimately, it’s about creating a predictable and secure digital ecosystem where everyone understands their part in maintaining system integrity.
Key Benefits of Utilizing a Computer Acceptable Use Policy Template
Adopting a well-defined Computer Acceptable Use Policy Template offers a multitude of benefits that extend across various facets of an organization. One of the primary advantages is enhanced data security. By outlining prohibited activities, such as downloading unauthorized software or accessing malicious websites, the policy acts as a first line of defense against cyber threats. It educates users on best practices for password management, handling sensitive data, and identifying suspicious communications, thereby significantly reducing the likelihood of a data breach or system compromise.
Another significant benefit is improved legal protection and compliance. A robust Computer Acceptable Use Policy Template serves as a contractual understanding between the organization and its users, clearly detailing obligations and acceptable behavior. In the event of a security incident, a violation of company policy, or even a lawsuit, having a signed acknowledgment of these terms can be invaluable. It demonstrates due diligence in establishing standards for information security and employee conduct, aligning with various regulatory requirements and helping to shield the organization from potential legal repercussions. This commitment to corporate governance showcases a responsible approach to digital operations.
Moreover, a Computer Acceptable Use Policy Template fosters a more productive and efficient work environment. By setting clear boundaries around personal use of company resources, it helps minimize distractions and ensures that bandwidth and computing power are dedicated to business operations. It also promotes digital hygiene and responsible use, preventing issues like malware infections that can lead to costly downtime. Employees understand what is expected of them, leading to fewer ambiguities and a more consistent approach to using company IT assets. This clarity in workplace rules reduces the need for constant supervision and allows IT and HR departments to focus on strategic initiatives rather than reactive problem-solving.
Customizing Your Computer Acceptable Use Policy Template for Specific Needs
While a Computer Acceptable Use Policy Template provides an excellent starting point, its true power lies in its adaptability. No two organizations are exactly alike, and what works for a tech startup might not be suitable for a healthcare provider or a school district. Customization is key to ensuring the policy is relevant, enforceable, and truly effective for your specific environment. Consider the nature of your industry, the size of your workforce, and the specific technologies you utilize when adapting the template.
For instance, a financial institution will need to place a heavy emphasis on data encryption, transaction security, and strict compliance with financial regulations, integrating these details directly into their Computer Acceptable Use Policy Template. An educational institution, on the other hand, might focus more on student privacy, responsible internet use for learning, and restrictions on content access, especially for minors. Similarly, a company with a high percentage of remote workers might need to add specific clauses about home network security, VPN usage, and secure file sharing protocols, distinguishing them from policies for on-site employees.
The process of customization should involve input from various stakeholders, including IT, HR, legal counsel, and even representatives from different departments. This collaborative approach ensures that the policy addresses real-world scenarios and covers all potential vulnerabilities. It also helps in identifying specific software or hardware unique to your operations that need explicit mention or particular guidelines. Regular review and updates are also crucial to keep your Computer Acceptable Use Policy Template aligned with evolving technology, new legal requirements, and changes in your organizational structure or operational practices. This ensures your organizational standards remain current and effective in managing digital risks.
Essential Elements to Include in Your Computer Acceptable Use Policy Template
A comprehensive Computer Acceptable Use Policy Template should cover a wide range of topics to provide clear guidance and protection. While the specifics will vary based on customization, several core elements are universally important:
- Purpose and Scope: Clearly state the policy’s objective – typically to protect company assets, ensure productivity, and maintain a secure computing environment. Define who the policy applies to (all employees, contractors, interns, etc.) and what resources it covers (all company-owned devices, networks, software, email, internet access, and potentially personal devices used for work).
- User Responsibilities: Outline the expected conduct of users, including protecting passwords, reporting security incidents, safeguarding company data, and respecting intellectual property. This section emphasizes the individual’s role in maintaining system integrity.
- Prohibited Activities: Detail specific actions that are strictly forbidden. This often includes unauthorized software installation, accessing illegal content, harassment, spamming, copyright infringement, sharing confidential information, using company resources for personal gain, or attempting to bypass security measures.
- Data Security and Privacy: Address how sensitive and confidential information should be handled, stored, and transmitted. This includes guidelines on encryption, data backups, cloud service usage, and adherence to data privacy laws. It also clarifies that users should have no expectation of privacy when using company systems.
- Software and Hardware Use: Specify rules regarding the installation, licensing, and use of software. Outline acceptable use of company-provided hardware, including laptops, mobile devices, and peripherals, and policies for personal devices (BYOD – Bring Your Own Device), if permitted.
- Internet and Email Usage: Define acceptable use of company internet access and email systems, including restrictions on recreational browsing, social media use, and sending unsolicited or offensive content. It should also cover phishing awareness and suspicious email protocols.
- Monitoring and Enforcement: Clearly state that the organization reserves the right to monitor all network traffic, system usage, and communications on its IT infrastructure. Outline the consequences of policy violations, which can range from warnings to disciplinary action, up to and including termination of employment and legal action.
- Acknowledgement of Understanding: Include a section requiring users to read, understand, and formally acknowledge their agreement to abide by the terms of the policy, often through a digital signature or signed document. This is critical for legal terms and establishing user agreement.
- Policy Review and Updates: Acknowledge that the policy is a living document and will be reviewed and updated periodically to reflect changes in technology, legal requirements, and organizational needs.
Design, Usability, and Implementation Tips for Your Computer Acceptable Use Policy Template
Creating a comprehensive Computer Acceptable Use Policy Template is only half the battle; ensuring it’s effectively communicated, understood, and adhered to is equally crucial. The design and usability of the document play a significant role in its adoption. Start by making the language clear, concise, and easy to understand. Avoid overly technical jargon or complex legalistic phrasing that might deter users from reading it thoroughly. Use headings, bullet points, and short paragraphs to break up the text, enhancing readability, whether it’s printed or accessed digitally.
For implementation, consider how the policy will be introduced and integrated into your organization’s operational standards. It shouldn’t just be a document tucked away in an HR folder. During onboarding, new employees, contractors, or students should be thoroughly briefed on the Computer Acceptable Use Policy Template as part of their initial orientation. This initial training is an excellent opportunity to explain the “why” behind the rules, emphasizing their importance for both individual and organizational security. Require a formal acknowledgment of understanding, perhaps through a digital sign-off system integrated with your HR or IT platforms, ensuring there’s a verifiable record of agreement to these legal terms.
Furthermore, make the Computer Acceptable Use Policy Template easily accessible at all times, whether through your internal intranet, an HR portal, or a shared drive. Consider creating a simplified, visual summary or an FAQ document to complement the full policy, making it even more approachable. Regular reminders and refresher training sessions are also beneficial, especially when significant updates are made or new threats emerge. This ongoing reinforcement helps embed the principles of acceptable use into the organizational culture, ensuring that compliance with these workplace rules remains a top priority and that everyone is contributing to strong information security.
In an era where digital tools are indispensable, a well-defined and diligently implemented Computer Acceptable Use Policy Template is far more than just bureaucratic paperwork. It’s a strategic investment in the security, productivity, and legal well-being of any organization. By clearly articulating expectations, protecting valuable data, and fostering a culture of responsible digital citizenship, it lays the groundwork for a resilient and efficient operational environment.
Embracing the principles outlined in a robust Computer Acceptable Use Policy Template helps mitigate risks, ensures compliance with evolving regulations, and empowers users to be proactive guardians of the organization’s digital assets. It’s a practical, actionable solution that brings clarity to complex digital interactions, allowing your team to leverage technology’s full potential safely and effectively. Consider this template not as a static document, but as a dynamic cornerstone of your overall information security strategy, continually evolving to meet the challenges of the modern digital world.


