In today’s interconnected digital landscape, the question isn’t if an organization will face a cyber threat, but when. From sophisticated ransomware attacks to subtle phishing scams, the range and complexity of digital dangers are constantly evolving, posing significant risks to data integrity, operational continuity, and an organization’s hard-earned reputation. Without a structured approach to identifying, assessing, and mitigating these threats, businesses are essentially navigating a minefield blindfolded, leaving their most valuable digital assets exposed.
This is where a robust Cybersecurity Risk Management Policy Template becomes not just a helpful document, but an indispensable strategic asset. It provides a foundational framework, a clear roadmap for organizations to proactively address potential vulnerabilities and establish a resilient cybersecurity posture. Whether you’re a burgeoning startup, a mid-sized enterprise, or a large corporation, this template offers a scalable solution, helping IT managers, compliance officers, and executive leadership to articulate, enforce, and maintain comprehensive information security measures.
Why a Cybersecurity Risk Management Policy Template is Essential
The imperative for a well-defined Cybersecurity Risk Management Policy Template has never been greater. The current threat landscape is characterized by its volatility and pervasiveness; cyberattacks are increasing in frequency, sophistication, and potential for damage. Organizations face not only direct financial losses from breaches but also severe reputational harm, operational disruptions, and potential legal liabilities.
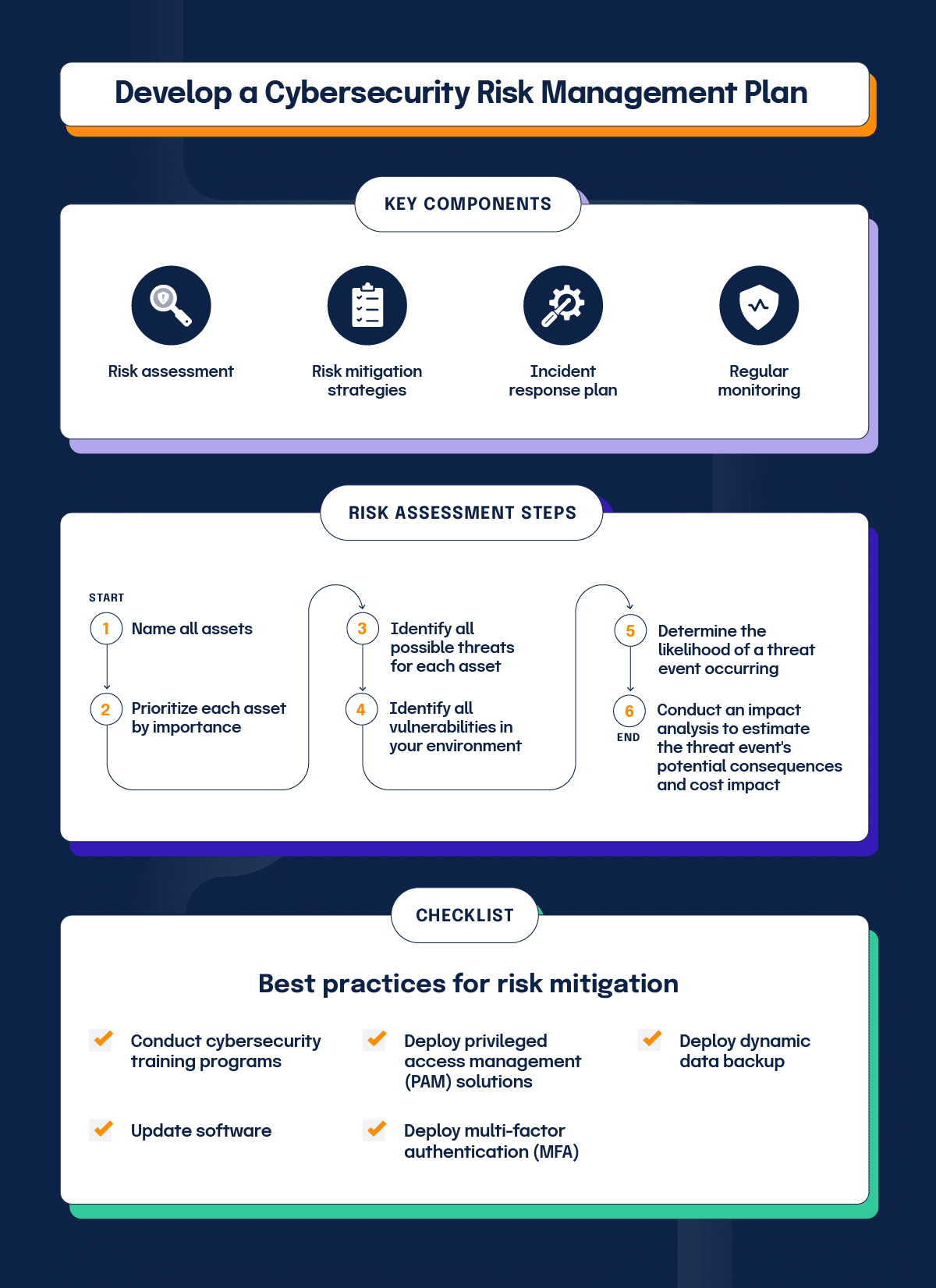
Beyond the immediate threats, regulatory compliance is a formidable challenge for businesses of all sizes. Frameworks such as HIPAA, GDPR, CCPA, and NIST SP 800-53 impose strict requirements for data protection and risk management. A comprehensive Cybersecurity Risk Management Policy Template helps ensure that an organization’s security practices align with these intricate legal obligations, minimizing the risk of hefty fines and sanctions. It demonstrates due diligence to regulators, customers, and partners, establishing a clear commitment to safeguarding sensitive information.
Key Benefits of Using a Cybersecurity Risk Management Policy Template
Adopting a standardized Cybersecurity Risk Management Policy Template offers a multitude of strategic and operational advantages that extend far beyond simply having a document on file. It transforms an organization’s approach to security from reactive damage control to proactive threat prevention and management. This foundational tool is critical for building a resilient and secure operational environment.
One primary benefit is the establishment of a consistent and repeatable risk assessment methodology. By providing clear steps for identifying, analyzing, and evaluating potential cyber risks, the template ensures that no critical vulnerabilities are overlooked. It fosters a culture of security awareness and accountability across the organization, making cybersecurity everyone’s responsibility, not just the IT department’s.
Furthermore, a well-implemented Cybersecurity Risk Management Policy Template significantly strengthens an organization’s compliance posture. It acts as a single source of truth for all security-related rules and guidelines, making it easier to demonstrate adherence to various industry standards and government regulations. This streamlines audit processes and reduces the administrative burden associated with proving compliance.
In the event of an incident, the policy template ensures a predefined and efficient incident response plan is in place. Clear procedures for detection, containment, eradication, recovery, and post-incident analysis minimize the impact of breaches and accelerate recovery times. This structured approach saves valuable time and resources during critical moments, helping to preserve business continuity and reduce potential financial losses from operational downtime.
How a Cybersecurity Risk Management Policy Template Can Be Customized
While a Cybersecurity Risk Management Policy Template provides a robust starting point, its true value comes from its adaptability. No two organizations are exactly alike, and a one-size-fits-all approach to cybersecurity can often leave critical gaps. Tailoring the template to an organization’s unique operational context is paramount for its effectiveness.
Customization involves considering the specific industry in which your organization operates. For instance, a healthcare provider will need to place a heavy emphasis on HIPAA compliance and protected health information (PHI), while a financial institution will focus on PCI DSS and safeguarding financial transactions. The template should be adapted to reflect these sector-specific regulatory frameworks and data handling requirements.
The size and complexity of your organization also play a significant role in adapting the Cybersecurity Risk Management Policy Template. A small business with limited IT resources might consolidate certain roles or simplify procedures, whereas a large enterprise will require detailed hierarchies, comprehensive vendor management clauses, and extensive reporting mechanisms. Scalability is key, allowing the policy to grow and evolve with the organization.
Furthermore, existing IT infrastructure, the types of data processed, and the specific threat landscape faced by the organization must inform the customization process. Whether your operations are cloud-based, on-premise, or hybrid, the policy needs to clearly define controls and responsibilities relevant to your technology stack. The template should be viewed as a living document, subject to regular review and updates to reflect changes in technology, threats, and organizational priorities.
Important Elements to Include in Your Cybersecurity Risk Management Policy Template
A truly comprehensive Cybersecurity Risk Management Policy Template must delineate a clear framework that covers all critical aspects of an organization’s information security program. Each element plays a vital role in creating a robust and defensible posture against cyber threats. Skipping or minimizing any of these components can create significant vulnerabilities.
Here are the essential elements that should be included:
- Policy Statement and Objectives: This section clearly articulates the organization’s overarching commitment to cybersecurity, defining the policy’s purpose, scope, and the strategic objectives it aims to achieve. It sets the tone for the entire document.
- Scope: Defines what the policy covers, including all information systems, data, networks, and personnel within the organization’s control, whether owned, leased, or managed. It clarifies boundaries and applicability.
- Roles and Responsibilities: Clearly assigns accountability for various aspects of cybersecurity. This includes identifying the CISO, IT security teams, departmental heads, and all employees, detailing their specific duties in upholding the policy.
- Risk Assessment Methodology: Outlines the systematic process for identifying, analyzing, and evaluating information security risks. This includes criteria for likelihood and impact, risk scoring, and prioritization.
- Risk Treatment and Mitigation Strategies: Details the organization’s approach to addressing identified risks, including strategies for avoidance, transference, reduction (e.g., implementing specific security controls), or acceptance. This section links directly to the output of risk assessments.
- Incident Response Plan: Provides a structured, step-by-step procedure for detecting, reporting, assessing, containing, eradicating, recovering from, and learning from cybersecurity incidents. This is crucial for minimizing damage and ensuring business continuity.
- Business Continuity and Disaster Recovery: Describes the plans and procedures for maintaining essential business functions during and after a significant disruption, including data backup, restoration, and alternative operational sites.
- Third-Party Risk Management: Addresses the risks associated with vendors, suppliers, and other third parties who have access to the organization’s data or systems. It includes due diligence requirements, contract clauses, and ongoing monitoring.
- Data Classification and Handling: Establishes guidelines for categorizing data based on its sensitivity (e.g., public, internal, confidential, restricted) and specifies appropriate handling procedures for each classification, including storage, transmission, and disposal.
- Access Control Policy: Defines rules for granting, reviewing, and revoking user access to systems and data based on the principle of least privilege, including authentication methods and password requirements.
- Security Awareness Training: Mandates regular cybersecurity training for all employees, covering topics such as phishing, social engineering, password hygiene, and policy adherence, fostering an informed workforce.
- Vulnerability Management: Outlines the process for regularly identifying, assessing, and remediating security vulnerabilities in systems, applications, and networks through patching, configuration management, and penetration testing.
- Compliance and Legal Requirements: Identifies specific regulatory and statutory obligations (e.g., HIPAA, GDPR, CCPA, NIST, ISO 27001) that the organization must adhere to, ensuring the policy aligns with these mandates.
- Policy Review and Updates: Specifies the frequency and process for reviewing and updating the Cybersecurity Risk Management Policy Template to ensure its continued relevance and effectiveness against evolving threats and organizational changes.
Tips for Design, Usability, and Implementation
A Cybersecurity Risk Management Policy Template is only as effective as its readability and accessibility. Even the most perfectly crafted policy can fail if it’s too cumbersome to navigate or difficult to understand. Therefore, thoughtful design and strategic implementation are crucial for ensuring the policy truly becomes an organizational cornerstone, rather than just another document gathering dust.
When it comes to design, prioritize clarity and conciseness. Use clear, unambiguous language, avoiding overly technical jargon where possible, or providing glossaries for essential terms. Employ consistent formatting, including headings, subheadings, and bullet points, to break up large blocks of text and improve scannability. Consider using tables or flowcharts for complex processes, such as the incident response steps, to make them visually digestible and actionable.
For usability, ensure the Cybersecurity Risk Management Policy Template is easily accessible to all relevant personnel. In a digital format, this means hosting it on a well-known internal portal, shared drive, or document management system that everyone can access readily. Implement version control to track changes and ensure employees are always referring to the most current iteration of the policy. Make sure digital documents are searchable, allowing users to quickly find specific sections or keywords.
Regarding implementation, don’t just distribute the document; actively integrate it into your organizational culture. This includes mandatory initial training sessions for all employees, ongoing awareness campaigns, and regular refreshers. For roles with specific security responsibilities, consider more in-depth training that covers their obligations detailed in the Cybersecurity Risk Management Policy Template. Even if a print version is provided for archival or specific operational needs, emphasize that the digital version is the active, most up-to-date document. Regularly audit compliance with the policy to identify gaps and reinforce its importance.
The digital threat landscape will continue to evolve, presenting new challenges and demanding constant vigilance from every organization. A well-articulated, easily understood, and regularly updated Cybersecurity Risk Management Policy Template is not merely a formality; it is a foundational pillar of an effective cybersecurity strategy. It empowers employees, guides decision-makers, and provides a clear framework for navigating the complexities of digital defense.
By proactively adopting and customizing a comprehensive Cybersecurity Risk Management Policy Template, your organization can move beyond reactive measures to establish a robust and resilient security posture. It’s an investment in your future, protecting your data, reputation, and operational continuity in an increasingly digital world. Don’t wait for an incident to define your security; let a solid policy guide your proactive protection efforts today.


