In today’s fast-paced digital landscape, businesses of all sizes wrestle with the dual challenge of empowering their workforce with technology while simultaneously safeguarding sensitive data and maintaining operational integrity. Employees frequently utilize a diverse array of devices, applications, and cloud services to perform their daily tasks, often operating outside the direct purview of traditional IT oversight. This dynamic environment, known as End User Computing (EUC), presents both incredible opportunities for productivity and significant risks if not managed effectively.
Navigating these complexities requires a robust framework, and that’s precisely where an End User Computing Policy Template becomes an indispensable asset. It provides a structured approach to defining acceptable use, security protocols, and compliance requirements for all digital tools and platforms used by employees. From startups to sprawling enterprises, any organization leveraging technology for business operations stands to gain immensely from clear, well-articulated guidelines, ensuring everyone understands their responsibilities in maintaining a secure and efficient computing environment.
Why an End User Computing Policy Template is Essential Today
The modern workplace is characterized by a rapid evolution of technology and work styles. With the pervasive adoption of remote work, cloud services, and Bring Your Own Device (BYOD) programs, the perimeter of traditional IT security has effectively dissolved. An End User Computing Policy Template is no longer a luxury; it’s a foundational element of sound IT governance and risk management. Without it, organizations face a heightened risk of data breaches, compliance failures, and operational disruptions.
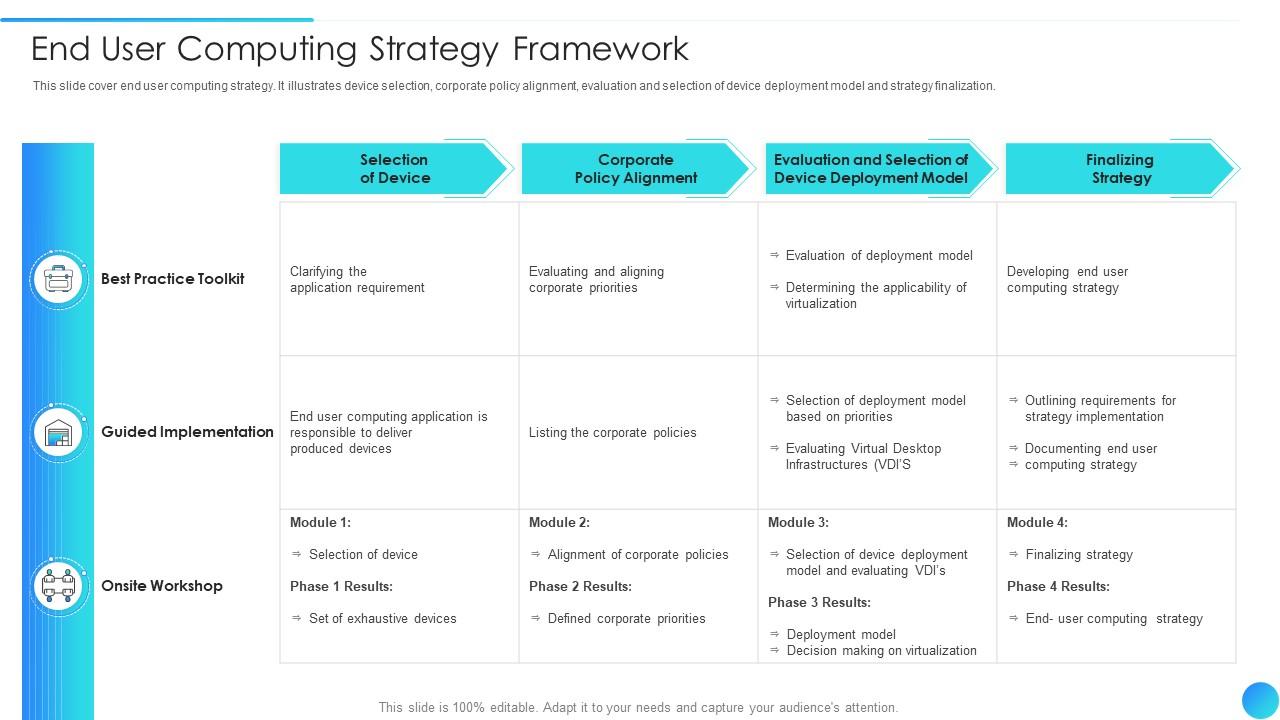
This policy establishes clear expectations, helping to mitigate the "shadow IT" phenomenon where employees use unauthorized applications or services, often unknowingly exposing the company to vulnerabilities. It codifies the rules for everything from software installations and data storage practices to acceptable use of internet resources and mobile device management. By providing a comprehensive set of workplace rules, an End User Computing Policy Template ensures consistency and reduces ambiguity across the organization, fostering a more secure and disciplined computing culture.
Furthermore, regulatory requirements are becoming increasingly stringent. Data privacy laws like GDPR, CCPA, and industry-specific regulations such as HIPAA and SOX demand meticulous attention to how data is accessed, processed, and stored. An End User Computing Policy Template serves as a critical component of demonstrating compliance, outlining the legal obligations and organizational guidelines that employees must adhere to. It acts as a proactive defense, safeguarding the company from potential legal ramifications, hefty fines, and reputational damage stemming from non-compliance or security incidents.
Key Benefits of Using an End User Computing Policy Template
Implementing a well-crafted End User Computing Policy Template brings a multitude of strategic and operational benefits to an organization. Foremost among these is enhanced data security. By clearly outlining acceptable security protocols, password requirements, and data handling procedures, it significantly reduces the likelihood of human error-induced data breaches. This proactive stance protects sensitive corporate information, intellectual property, and customer data from unauthorized access or loss.
Beyond security, an End User Computing Policy Template streamlines IT operations. When employees understand the proper channels for software requests, hardware support, and incident reporting, IT departments can allocate their resources more efficiently. It minimizes time spent on troubleshooting issues arising from unauthorized software or misconfigured devices, allowing IT professionals to focus on strategic initiatives rather than reactive problem-solving. This contributes to better overall IT infrastructure management and more predictable system access.
Another significant advantage is improved compliance and audit readiness. A robust policy provides clear documentation of an organization’s approach to managing end-user technology, making it easier to demonstrate adherence to various regulatory requirements and internal controls during audits. This proactive documentation can save considerable time and effort during compliance checks, proving that the organization has a structured framework in place for maintaining data integrity and user accountability. Ultimately, an End User Computing Policy Template fosters a culture of responsibility and awareness among employees, leading to greater organizational efficiency and reduced long-term risk.
Customizing Your End User Computing Policy Template
While an End User Computing Policy Template provides an excellent starting point, its true value lies in its adaptability to your organization’s unique needs, culture, and operational landscape. No two businesses are exactly alike, and a one-size-fits-all approach to IT governance often falls short. The template should be seen as a flexible framework, ready to be molded to fit specific industry regulations, company size, employee roles, and the technological stack in use.
For instance, a healthcare provider will need to place a heavy emphasis on HIPAA compliance and data privacy, dictating stricter controls on patient information access and mobile device usage. Conversely, a creative agency might prioritize guidelines for software licensing and intellectual property protection, allowing for more flexibility in application choice while ensuring legal adherence. The goal is to create organizational guidelines that are both comprehensive and practical, avoiding policies that are either too restrictive or too vague.
Customization involves more than just filling in blanks; it requires careful consideration of specific use cases, such as remote work scenarios, BYOD policies, or the use of specific SaaS applications. Engaging key stakeholders from IT, legal, HR, and various business units during the customization process is crucial. Their input ensures that the End User Computing Policy Template addresses real-world challenges and gains broader acceptance from the workforce, making it an effective and respected set of workplace rules rather than an ignored mandate.
Important Elements for Your End User Computing Policy Template
A truly effective End User Computing Policy Template must be comprehensive, covering all critical aspects of how employees interact with technology within the organization. While the exact scope may vary, certain fundamental elements are non-negotiable for establishing robust IT governance and risk management.
- Policy Statement and Purpose: Clearly define the policy’s objectives, scope, and who it applies to (all employees, contractors, etc.). This section sets the stage and explains why the policy exists.
- Acceptable Use Policy (AUP): Detail what constitutes appropriate and inappropriate use of company-owned and personal devices, networks, and software. This includes internet browsing, social media use, and communication channels.
- Data Security and Privacy: Outline guidelines for handling, storing, transmitting, and disposing of sensitive data. This should cover data classification, encryption requirements, and compliance with data privacy regulations (e.g., GDPR, CCPA).
- Account and Password Management: Establish rules for creating strong passwords, changing them regularly, not sharing credentials, and securing user accounts.
- Software and Application Usage: Address software licensing, unauthorized installations, freeware/shareware, and the use of cloud-based applications. It should define the process for requesting new software.
- Hardware and Device Management: Cover company-issued equipment, BYOD policies (if applicable), proper care of devices, reporting loss or theft, and mobile device management (MDM) requirements.
- Network Security: Define acceptable use of company networks, Wi-Fi, VPNs, and prohibitions against attempting to bypass security controls or unauthorized network access.
- Incident Reporting and Response: Outline the procedure for reporting security incidents, suspected breaches, or policy violations, and the steps for incident response.
- Physical Security: Briefly address the physical security of devices and data, especially for remote workers or when working in public spaces.
- Data Backup and Recovery: Provide guidelines on how and when data should be backed up, especially for critical business data, to ensure business continuity.
- Monitoring and Audit: Inform users that their activities on company systems may be monitored for security and compliance purposes, and outline audit trails.
- Training and Acknowledgment: Specify that employees are required to read, understand, and acknowledge the policy, often including mandatory security awareness training.
- Enforcement and Disciplinary Actions: Clearly state the consequences of policy violations, which can range from retraining to disciplinary action, up to and including termination or legal action.
- Policy Review and Updates: Include a clause about how frequently the policy will be reviewed and updated to reflect changes in technology, regulations, and business needs.
Tips for Design, Usability, and Implementation
Crafting an effective End User Computing Policy Template goes beyond just the content; its design, usability, and thoughtful implementation are equally crucial for its success. A policy that is difficult to understand, hard to access, or poorly communicated is likely to be ignored, regardless of how well-intentioned its rules are.
First, focus on clarity and conciseness. Use plain language, avoiding overly technical jargon where possible. Break down complex topics into digestible sections with clear headings and bullet points, much like this article. A table of contents can significantly improve navigation, especially for longer documents. For digital implementation, consider creating a searchable PDF or a web-based document that is easily accessible on your internal intranet or knowledge base. This improves system access for all employees.
For usability, consider the "user experience" of the policy itself. Make it visually appealing with consistent branding and formatting. Instead of a dense wall of text, use white space effectively. Alongside the comprehensive End User Computing Policy Template, consider creating a concise "quick reference guide" or an executive summary that highlights the most critical acceptable use guidelines and security protocols. These shorter versions can be excellent tools for initial onboarding or periodic reminders.
Implementation is where the policy truly comes to life. Don’t just publish it and expect compliance. Implement a mandatory training program for all employees, explaining the policy’s rationale, key provisions, and their responsibilities. Use engaging formats like interactive modules or short video explainers. Require employees to digitally acknowledge that they have read and understood the policy, keeping a record for audit purposes. Regularly communicate updates and reminders through internal newsletters, town halls, or team meetings. Furthermore, ensure the policy is integrated into your new employee onboarding process, setting expectations from day one. Consistent enforcement is also key; the policy loses credibility if violations are not addressed consistently and fairly.
Conclusion
In an age where digital tools are central to nearly every business function, a well-defined End User Computing Policy Template is not merely a formality; it’s a strategic imperative. It stands as a testament to an organization’s commitment to data security, operational efficiency, and regulatory compliance, providing a clear framework for responsible technology use. By equipping employees with transparent workplace rules, companies can harness the power of end-user innovation without succumbing to the associated risks.
Embracing and customizing an End User Computing Policy Template empowers your organization to proactively manage its digital environment, minimize vulnerabilities, and foster a culture of shared responsibility for IT governance. It’s an investment in your company’s resilience, ensuring that as technology continues to evolve, your foundational guidelines remain robust, relevant, and ready to protect your most valuable assets. Consider leveraging such a practical solution to secure your digital future and empower your workforce effectively.