In an increasingly digitized world, the safeguarding of sensitive information has become paramount, particularly within the healthcare sector. For any organization handling protected health information (PHI), maintaining robust security protocols isn’t just a best practice—it’s a legal mandate. This is where a comprehensive Hipaa Security Rule Policy Template steps in, acting as the bedrock for your entire data protection strategy. It provides a structured framework, guiding covered entities and business associates through the complexities of HIPAA compliance, ensuring patient data remains confidential, integral, and available only to authorized individuals.
Understanding and implementing the various technical, physical, and administrative safeguards outlined by the HIPAA Security Rule can be a daunting task. A well-crafted Hipaa Security Rule Policy Template simplifies this challenge, offering a clear roadmap for developing and enforcing the necessary workplace rules and procedures. It’s an indispensable tool for compliance officers, IT security managers, HR professionals, and indeed, anyone responsible for maintaining the security of healthcare data, helping to translate abstract regulatory language into actionable, understandable internal policies that protect both patients and the organization itself.
Why a Hipaa Security Rule Policy Template is Essential
The landscape of healthcare data security is fraught with challenges, from sophisticated cyberattacks to accidental data exposures. In this environment, a detailed Hipaa Security Rule Policy Template isn’t merely a bureaucratic formality; it’s a critical shield against significant risks. The Department of Health and Human Services (HHS) and its Office for Civil Rights (OCR) actively investigate breaches and enforce compliance, with penalties for non-compliance ranging from thousands to millions of dollars, not to mention reputational damage.
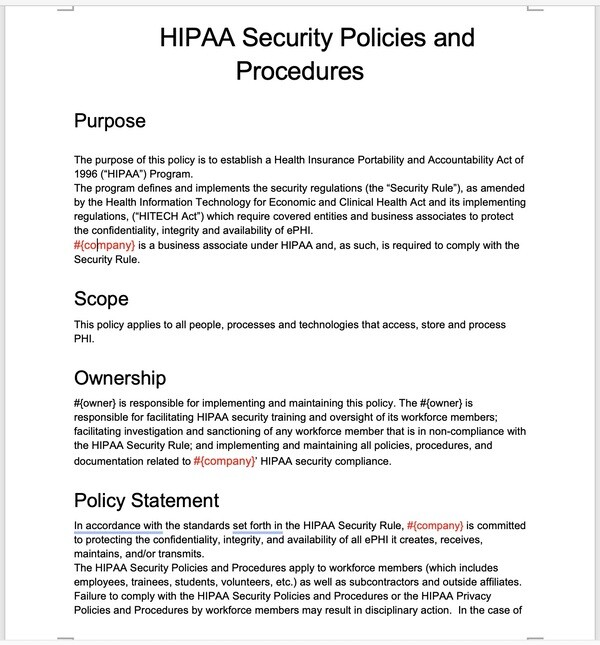
Implementing a robust policy based on a quality Hipaa Security Rule Policy Template is fundamental for demonstrating due diligence and a commitment to regulatory compliance. It ensures that your organization has documented security measures in place to protect PHI, addressing everything from access control to incident response. Without such a framework, organizations are left vulnerable to data breaches, audits, and the subsequent legal and financial ramifications, making proactive policy development an absolute necessity in today’s context.
Key Benefits of Using a Hipaa Security Rule Policy Template
Leveraging a professional Hipaa Security Rule Policy Template offers a multitude of advantages that extend beyond mere compliance. It provides a strategic advantage, streamlining operations and fostering a culture of security throughout your organization.
Firstly, it ensures streamlined compliance with the intricate requirements of the HIPAA Security Rule. Instead of building policies from scratch, which is time-consuming and prone to omissions, a template provides a pre-vetted structure that covers all necessary safeguards. This reduces the burden on internal teams and helps prevent costly errors.
Secondly, it significantly reduces legal and financial risk. Clear, documented policies demonstrate your organization’s commitment to protecting PHI, which can be crucial during an audit or in the event of a data breach. Having these organizational policies in place can mitigate fines and legal liabilities, showing that reasonable efforts were made to secure data.
Thirdly, it leads to an improved data security posture. By systematically addressing each facet of the Security Rule, from network security to physical facility access, the template helps you identify and close potential vulnerabilities. This comprehensive approach bolsters your defenses against a wide array of cyber threats and insider risks.
Fourthly, a well-defined template enhances employee awareness and training. It serves as the authoritative source for workplace rules regarding PHI handling, making it easier to educate staff on their obligations. Consistent security awareness training, built upon these policies, transforms employees into an active line of defense.
Finally, it provides a solid foundation for audit readiness. When the OCR comes knocking, having a fully developed and implemented set of policies derived from a Hipaa Security Rule Policy Template dramatically simplifies the audit process. It presents clear evidence of your organization’s compliance efforts, saving time and stress during regulatory reviews. This ultimately contributes to greater trust from patients and partners, reinforcing your organization’s integrity.
Customizing Your Hipaa Security Rule Policy Template
While a Hipaa Security Rule Policy Template provides a strong foundational structure, it’s crucial to understand that it’s not a one-size-fits-all solution. Each covered entity and business associate operates with unique characteristics—different sizes, organizational structures, technological infrastructures, and specific workflows for handling protected health information. Therefore, adapting the template to your specific environment is not just recommended, but essential for effective and compliant data security.
Customization involves tailoring the general policies to reflect your organization’s specific risk assessment findings. For instance, a small dental practice will have different physical safeguard requirements than a large hospital system, just as a cloud service provider acting as a business associate will have distinct technical safeguard configurations. You’ll need to incorporate details about your specific IT systems, physical locations, personnel roles, and incident response procedures. This might include naming specific software, hardware, or responsible individuals.
Furthermore, a dynamic approach to policy management is vital. Your Hipaa Security Rule Policy Template should be a living document, subject to periodic review and updates. As technology evolves, new threats emerge, or your organizational operations change, your policies must adapt accordingly. Establishing a regular review cycle ensures that your customized policies remain relevant, effective, and fully compliant with the latest regulatory interpretations and best practices in data security.
Important Elements to Include in Your Hipaa Security Rule Policy Template
A robust Hipaa Security Rule Policy Template must systematically address all the requirements laid out in the HIPAA Security Rule. This involves comprehensive coverage of administrative, physical, and technical safeguards, along with organizational requirements and thorough documentation.
Here are the critical elements and fields that should be incorporated:
- Security Management Process:
- Risk Analysis: Policies for identifying and assessing potential risks and vulnerabilities to PHI.
- Risk Management: Procedures for implementing security measures to reduce risks to a reasonable and appropriate level.
- Sanction Policy: Guidelines for applying sanctions against workforce members who violate security policies.
- Information System Activity Review: Processes for regularly reviewing audit logs and other security activity.
- Assigned Security Responsibility: Designation of a Security Official responsible for the development and implementation of security policies and procedures.
- Workforce Security:
- Authorization and/or Supervision: Policies for granting and modifying access to PHI.
- Workforce Clearance Procedures: Background checks or other processes for new hires with PHI access.
- Termination Procedures: Protocols for promptly revoking access upon employee termination.
- Information Access Management:
- Access Establishment and Modification: Procedures for setting up and changing user access rights.
- Accountability: Mechanisms to track user access to PHI.
- Security Awareness and Training:
- Security Reminders: Regular updates and reminders for the workforce.
- Protection from Malicious Software: Policies and procedures for guarding against, detecting, and reporting malicious software.
- Log-in Monitoring: Procedures for monitoring successful and unsuccessful log-in attempts.
- Password Management: Requirements for strong, unique passwords and regular changes.
- Security Incident Procedures:
- Response and Reporting: Policies for identifying, reporting, and responding to security incidents (e.g., data breaches).
- Contingency Plan:
- Data Backup Plan: Procedures for creating and maintaining retrievable exact copies of PHI.
- Disaster Recovery Plan: Strategy for restoring lost data and normal operations after an emergency.
- Emergency Mode Operation Plan: Procedures for continuing critical business processes during an emergency.
- Testing and Revision Procedures: Policies for periodic testing and revision of contingency plans.
- Facility Access Controls:
- Contingency Operations: Procedures for granting access in emergency situations.
- Facility Security Plan: Measures to safeguard the facility and equipment from unauthorized physical access, tampering, and theft.
- Access Control and Validation Procedures: Mechanisms for controlling and validating physical access to facilities containing PHI.
- Maintenance Records: Documentation of repairs and modifications to physical security components.
- Workstation Use: Policies and procedures governing the use of workstations that access PHI.
- Workstation Security: Physical safeguards for workstations to restrict unauthorized access to PHI.
- Device and Media Controls:
- Disposal: Procedures for secure disposal of electronic media and hardware containing PHI.
- Media Re-use: Procedures for clearing PHI from electronic media before re-use.
- Accountability: Records of the movement of hardware and electronic media.
- Data Backup and Storage: Policies for creating retrievable copies of PHI and storing them securely.
- Access Control (Technical Safeguard):
- Unique User Identification: Requirement for individual and unique user IDs.
- Emergency Access Procedure: Procedures for obtaining necessary PHI during an emergency.
- Automatic Logoff: Implementation of automatic log-off for electronic sessions.
- Encryption and Decryption: Procedures for encrypting and decrypting PHI when appropriate.
- Audit Controls: Hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use PHI.
- Integrity: Mechanisms to ensure that PHI has not been altered or destroyed in an unauthorized manner.
- Person or Entity Authentication: Procedures to verify that a person or entity seeking access to PHI is the one claimed.
- Transmission Security:
- Integrity Controls: Mechanisms to ensure that electronically transmitted PHI is not improperly modified without detection.
- Encryption: Use of encryption where appropriate for PHI transmitted over electronic networks.
- Business Associate Agreements: Policies for creating and managing contractual obligations with business associates to ensure they also protect PHI.
- Policies and Procedures: A clear framework for developing, documenting, and maintaining all required HIPAA Security Rule policies and procedures.
- Documentation: Requirements for documenting all security measures, compliance activities, and policy reviews.
Tips for Designing, Usability, and Implementation
Designing and implementing a Hipaa Security Rule Policy Template effectively requires careful consideration beyond just content. The way it’s presented and integrated into your organization can significantly impact its usability and overall effectiveness.
For design and usability, strive for clarity and simplicity. Use plain language, avoiding overly technical jargon where possible, to ensure that all employees, regardless of their role or technical expertise, can understand their obligations. Employ clear headings, bullet points, and short paragraphs to enhance readability. A logical flow, perhaps mirroring the structure of the HIPAA Security Rule itself, will help users navigate the document efficiently. Consider creating an accessible digital format that allows for easy searching and cross-referencing, whether it’s on an intranet or a dedicated document management system.
When it comes to implementation, the key is integration and continuous engagement. Don’t let your Hipaa Security Rule Policy Template sit in a digital folder gathering dust. Instead, make it a cornerstone of your ongoing compliance efforts. This involves:
- Comprehensive Training: Develop mandatory training programs for all workforce members, directly referencing and explaining the policies outlined in the template. Regular refresher training is also essential.
- Accessibility: Ensure the policy document is easily accessible to all employees at all times, whether through a centralized digital repository, an HR portal, or printed copies in common areas if relevant for your setting.
- Version Control: Implement strict version control to track changes and ensure everyone is always referencing the most current iteration of your organizational policies.
- Senior Leadership Buy-in: Secure the commitment of management and leadership. Their visible support reinforces the importance of these security measures and encourages compliance throughout the organization.
- Regular Review and Updates: Schedule annual or biennial reviews of your policies, or more frequently if there are significant changes in technology, regulations, or your organizational structure. This ensures the policies remain current and effective.
- Integration with Other Policies: Align the Hipaa Security Rule Policy Template with other existing HR, IT, and workplace rules to create a cohesive and consistent set of company-wide policies.
By focusing on these aspects, your Hipaa Security Rule Policy Template transforms from a static document into a dynamic tool that actively contributes to a secure and compliant healthcare environment.
Ultimately, navigating the complexities of healthcare data security demands a proactive and structured approach. A meticulously developed and properly implemented Hipaa Security Rule Policy Template is not just a tool for meeting regulatory obligations; it’s an investment in your organization’s integrity, reputation, and long-term success. It empowers you to establish clear expectations, reduce vulnerabilities, and respond effectively to potential threats, ensuring that protected health information remains secure from end to end.
Embracing such a comprehensive policy framework, tailored to your unique operational context, sets a high standard for data protection. It fosters a culture of security awareness among your workforce and demonstrates an unwavering commitment to patient privacy. Consider integrating a robust Hipaa Security Rule Policy Template into your compliance strategy today—it’s an indispensable step towards building a resilient and trustworthy healthcare enterprise in the digital age.


