In today’s complex digital landscape, managing who has access to what – and why – is not just a technical challenge; it’s a strategic imperative. Organizations grapple with a constantly evolving threat landscape, stringent compliance mandates, and the sheer volume of users, applications, and data. Without a clear, systematic approach to defining access needs, projects can drift, security gaps can emerge, and audit failures become a real risk.
This is where a robust framework for documenting and tracking your Identity and Access Management (IAM) needs becomes invaluable. It’s about moving beyond informal conversations and disparate documents to a centralized, comprehensive system that ensures every aspect of your access control strategy is meticulously planned and aligned with business objectives. Whether you’re implementing a new IAM system, optimizing an existing one, or preparing for an audit, understanding your requirements is the first critical step.
The Critical Role of Robust Identity and Access Management
Identity and Access Management forms the backbone of an organization’s security posture. It encompasses the processes and technologies that manage digital identities and control user access to resources. From onboarding new employees to revoking access for departing ones, and from ensuring least privilege access to meeting regulatory mandates like GDPR or HIPAA, IAM touches nearly every aspect of business operations. Inadequate IAM can lead to data breaches, compliance penalties, operational inefficiencies, and significant reputational damage.
Effective IAM ensures that the right people have the right access to the right resources at the right time and for the right reasons. This involves not only managing user identities but also defining and enforcing access policies, monitoring access activity, and reporting on compliance. Achieving this level of precision and control requires a clear understanding of stakeholder needs and technical specifications, which is precisely where a structured requirements approach proves its worth.
What is an IAM Requirements Matrix?
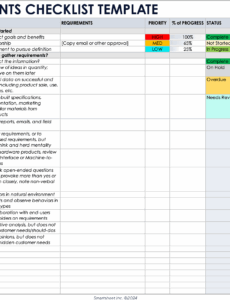
An IAM requirements matrix is a structured document that meticulously details all the necessary capabilities, functionalities, and constraints for an Identity and Access Management solution or project. It serves as a single source of truth, aligning business objectives with technical specifications. This tool provides a clear, traceable, and verifiable list of what an IAM system must achieve to meet organizational goals and satisfy various stakeholders.
The Iam Requirements Matrix Template serves as a foundational tool, offering a standardized framework to capture diverse requirements from various departments, including IT, security, HR, and legal. It transforms abstract needs into concrete, actionable items, facilitating communication between technical teams and business units. By centralizing these requirements, the matrix helps prevent scope creep, ensures critical needs aren’t overlooked, and provides a benchmark for evaluating solution effectiveness.
Why a Structured Approach Matters
Adopting a structured approach to defining your IAM needs brings numerous benefits. Firstly, it enhances clarity and reduces ambiguity. By systematically documenting each requirement, assumptions are minimized, and all stakeholders gain a shared understanding of project goals and deliverables. This clarity is crucial for successful implementation and adoption of any complex IAM solution.
Secondly, a requirements matrix significantly improves traceability. Each requirement can be linked to specific business objectives, design elements, test cases, and deployment stages. This traceability is invaluable for project management, quality assurance, and demonstrating compliance during audits. It ensures that every feature or functionality directly addresses an identified need, preventing unnecessary development.
Finally, this structured method empowers better decision-making and risk management. With a comprehensive overview of all requirements, project managers and solution architects can prioritize effectively, allocate resources optimally, and identify potential conflicts or gaps early in the project lifecycle. This proactive approach saves time and money, minimizes rework, and ultimately leads to a more robust and successful IAM deployment.
Key Elements of an Effective IAM Requirements Template
A well-crafted Iam Requirements Matrix Template should encompass a range of categories to provide a holistic view of your needs. These elements ensure that both functional and non-functional requirements are captured comprehensively, covering everything from user provisioning to audit logging. It’s essential to customize these categories to fit your specific organizational context and project scope.
While specific fields may vary, a comprehensive IAM solution requirements document typically includes:
- **Requirement ID:** A unique identifier for traceability.
- **Requirement Description:** A clear, concise statement of the requirement.
- **Requirement Type:** Categorization (e.g., functional, non-functional, security, compliance, performance).
- **Priority:** Indication of importance (e.g., **Must Have**, Should Have, Could Have, Won’t Have).
- **Source:** Who or what originated the requirement (e.g., business unit, regulation, technical team).
- **Stakeholder:** The primary person or group affected by or responsible for the requirement.
- **Status:** Current state of the requirement (e.g., **Draft**, Approved, In Progress, Completed).
- **Acceptance Criteria:** Measurable conditions that must be met for the requirement to be considered fulfilled.
- **Related Use Cases:** Links to specific scenarios where the requirement is applicable.
- **Compliance/Regulatory Reference:** Any specific regulations or policies the requirement addresses.
- **Non-Functional Aspects:** Such as **performance**, scalability, availability, usability, and maintainability.
Building Your IAM Requirements Matrix: A Step-by-Step Guide
Using an Iam Requirements Matrix Template effectively begins with a systematic approach to gathering and documenting your needs. This process is iterative and collaborative, requiring input from various departments and roles within your organization. The goal is to build a living document that guides your IAM project from inception to deployment and beyond.
Here’s a practical step-by-step guide to help you construct your identity and access management requirements:
- **Define Scope and Objectives:** Clearly outline what your IAM project aims to achieve. What business problems are you trying to solve? What systems and users will be in scope?
- **Identify Stakeholders:** Determine all key individuals and groups who will be impacted by or have input on the IAM solution. This includes business users, IT administrators, security officers, HR, legal, and executive sponsors.
- **Gather Requirements:** Employ various techniques such as interviews, workshops, surveys, and analysis of existing documentation to collect needs. Focus on both current state challenges and desired future state capabilities.
- **Categorize and Document:** Use your chosen **IAM requirements matrix** template to categorize and record each requirement. Ensure descriptions are clear, unambiguous, and testable.
- **Prioritize Requirements:** Work with stakeholders to assign a priority level to each requirement. This helps in managing scope, sequencing development, and making informed trade-offs.
- **Define Acceptance Criteria:** For each requirement, establish clear, measurable criteria that will be used to verify its successful implementation. This is crucial for testing and sign-off.
- **Review and Validate:** Share the matrix with all stakeholders for review and validation. Obtain formal sign-off to ensure alignment and prevent late-stage changes.
- **Manage Changes:** Establish a formal change management process for the matrix. Requirements are rarely static, and a controlled process ensures all changes are evaluated and approved.
Common Use Cases and Best Practices
The application of an IAM requirements framework extends across various phases of an identity and access management project. It’s not just for initial setup; it’s a tool for ongoing management and improvement. Common use cases include initial system implementation, system upgrades or migrations, compliance audits, and strategic planning for future security enhancements.
When implementing a new IAM system, the matrix provides a comprehensive blueprint, ensuring all necessary functionalities from user provisioning to single sign-on are considered. For upgrades, it helps assess whether new features are required and how they integrate with existing capabilities. During compliance audits, the document can quickly demonstrate that access management needs are well-defined and met. A best practice is to treat the requirements matrix as a living document, regularly reviewing and updating it to reflect evolving business needs and threat landscapes. Integrate it with your project management tools for seamless traceability.
Overcoming Challenges in Requirements Gathering
Gathering comprehensive and accurate requirements for IAM projects can be fraught with challenges. One common hurdle is the **diversity of stakeholders**, each with their own perspectives and priorities. IT administrators might focus on technical feasibility, while business users prioritize usability, and security teams emphasize stringent controls. Reconciling these varied viewpoints requires strong facilitation skills and a commitment to collaborative decision-making.
Another significant challenge is dealing with unclear or ambiguous requirements. Stakeholders may express needs in broad terms, making it difficult for technical teams to design and implement specific solutions. Overcoming this requires asking probing questions, providing examples, and using techniques like user stories or use cases to flesh out details. Finally, managing scope creep – the tendency for new requirements to emerge throughout the project – is critical. A robust change management process, as outlined in the step-by-step guide, is essential to control this and keep the project on track. Regular communication and validation workshops can also help mitigate these issues, ensuring that the identity governance requirements template remains relevant and actionable.
Frequently Asked Questions
What is the primary benefit of using an IAM requirements matrix?
The primary benefit is achieving clarity, alignment, and traceability across all aspects of an IAM project. It ensures all stakeholders have a shared understanding of what needs to be built, why it’s important, and how success will be measured, significantly reducing project risks and improving outcomes.
How often should an IAM requirements matrix be updated?
An IAM requirements matrix should be treated as a living document. It should be reviewed and updated whenever there are significant changes to business processes, regulatory requirements, technology infrastructure, or project scope. Ideally, a formal review process should be scheduled periodically (e.g., quarterly or annually) even outside of major changes.
Can a single template be used for all types of IAM projects?
While a core IAM requirements matrix template can be adapted for various projects, it’s often beneficial to customize it based on the specific project’s scope and complexity. For instance, a template for a new identity governance implementation might require more detailed sections on workflow and policy management than one for a simple single sign-on integration.
Who should be involved in creating and maintaining the requirements matrix?
Key stakeholders from various departments should be involved, including business users, IT security teams, network administrators, application owners, HR representatives, legal and compliance officers, and executive sponsors. A dedicated business analyst or project manager typically facilitates the creation and ongoing maintenance of the matrix.
Crafting a comprehensive IAM solution is an intricate journey, but with the right tools, it becomes a manageable and highly successful endeavor. A well-structured requirements document serves as your compass, guiding every decision and ensuring that your identity and access management initiatives are robust, secure, and perfectly aligned with your organizational goals. It transforms potential chaos into controlled progress, turning abstract needs into tangible, impactful solutions.
By embracing a meticulous approach to requirements gathering and documentation, organizations can build IAM systems that not only meet today’s demanding security and compliance standards but are also agile enough to adapt to future challenges. Leverage the power of a structured requirements framework to secure your digital future and empower your business with confidence.