In an increasingly complex and interconnected digital world, the question isn’t if an organization will face a cyber incident, but when. From sophisticated phishing attacks to debilitating ransomware, the threat landscape is a constant, evolving challenge for businesses of all sizes. Navigating these turbulent waters requires more than just reactive measures; it demands a proactive, structured approach to incident management. This is precisely where an Incident Response Policy Template Nist becomes an indispensable asset, serving as the strategic blueprint that guides an organization through the chaos of a security breach.
For IT professionals, security analysts, compliance officers, and even executive leadership, understanding and implementing a robust incident response framework is paramount. It’s the difference between a minor disruption and a catastrophic data breach that erodes customer trust and incurs significant financial and reputational damage. An Incident Response Policy Template Nist provides a foundational, yet adaptable, structure based on globally recognized security standards, enabling organizations to prepare for, detect, contain, and recover from security incidents with efficiency and clarity.
Why Incident Response Policy Template Nist is Essential Today
The digital age has ushered in unprecedented opportunities, but also an alarming array of cyber threats. Organizations are now targets for state-sponsored attackers, organized cybercrime syndicates, and even disgruntled insiders. Data breaches are reported almost daily, with the average cost of an incident soaring, encompassing everything from investigation and recovery to legal fees and regulatory fines. In this volatile environment, relying on ad-hoc responses or wishful thinking is simply not an option.
An Incident Response Policy Template Nist is essential because it provides a structured, methodical approach to managing these inevitable occurrences. It moves an organization beyond panic mode, establishing clear procedures and responsibilities long before an incident strikes. This proactive stance is not just about damage control; it’s about building resilience, ensuring business continuity, and protecting critical assets. Furthermore, for many industries, having a well-defined incident response plan isn’t merely best practice; it’s a legal obligation and a core component of demonstrating due diligence for various compliance frameworks, including HIPAA, GDPR, CCPA, and PCI DSS. A robust policy reduces legal exposure and reinforces trust with customers, partners, and regulators.
Key Benefits of Using Incident Response Policy Template Nist
Adopting an Incident Response Policy Template Nist offers a multitude of strategic advantages, transforming incident management from a reactive scramble into a well-oiled process. Firstly, it provides a standardized framework based on the National Institute of Standards and Technology (NIST) guidelines, a globally recognized authority in cybersecurity. This ensures that your organization’s approach aligns with industry best practices, enhancing the credibility and effectiveness of your security posture.
Secondly, the template significantly reduces the time and effort required to develop a comprehensive policy from scratch. Instead of reinventing the wheel, security teams can leverage a pre-designed structure, focusing their expertise on customization rather than foundational drafting. This efficiency translates into quicker implementation and a more rapid uplift in organizational readiness. Thirdly, a clear Incident Response Policy Template Nist defines roles, responsibilities, and communication channels, eliminating confusion during high-stress situations. Everyone from the IT help desk to the executive crisis management team knows their part, facilitating a coordinated and swift response. This clarity not only minimizes the impact of an incident but also accelerates the recovery process, reducing downtime and protecting revenue streams. Finally, the structured nature of the policy aids in meeting various compliance requirements and simplifies audit processes, demonstrating a commitment to data security and effective risk management.
Customizing Incident Response Policy Template Nist
While an Incident Response Policy Template Nist provides an excellent starting point, it’s crucial to understand that no single policy fits every organization perfectly. The true value lies in adapting the template to your specific operational context, industry, and risk profile. Customization is not just an option; it’s a necessity for ensuring the policy is practical, effective, and truly serves your organization’s unique needs.
Consider, for example, the industry you operate in. A healthcare provider will need to place a heavy emphasis on HIPAA compliance and protected health information (PHI), whereas a financial institution will focus more on PCI DSS and financial data security. The scale and complexity of your organization also play a significant role. A small startup might have a more streamlined incident response team, while a large enterprise will require more granular roles and multi-departmental coordination. Integrating the Incident Response Policy Template Nist with existing security frameworks, technologies, and business continuity plans is also vital. This includes mapping the policy’s steps to your current IT infrastructure, specific security tools, and data classification schemas. By tailoring the incident definitions, response procedures, and reporting requirements to reflect your actual systems and organizational structure, you transform a generic document into a living, actionable plan that strengthens your overall cybersecurity framework and reinforces workplace rules regarding data handling.
Important Elements to Include in Incident Response Policy Template Nist
A comprehensive Incident Response Policy Template Nist should be structured to cover the entire lifecycle of an incident, from preparation to post-incident analysis. Drawing heavily from NIST Special Publication 800-61, "Computer Security Incident Handling Guide," the policy typically includes the following critical elements:
- Policy Statement and Scope: Clearly defines the purpose, objectives, and applicability of the policy across the organization, outlining what types of incidents it covers and to whom it applies.
- Roles and Responsibilities: Delineates the structure of the Incident Response Team (IRT), including team lead, analysts, legal counsel, communications, and other stakeholders, detailing their specific duties and authorities during an incident.
- Incident Definition and Classification: Establishes clear criteria for what constitutes a security incident, how incidents are categorized (e.g., severity, type), and the initial reporting mechanisms. This ensures consistency in incident management.
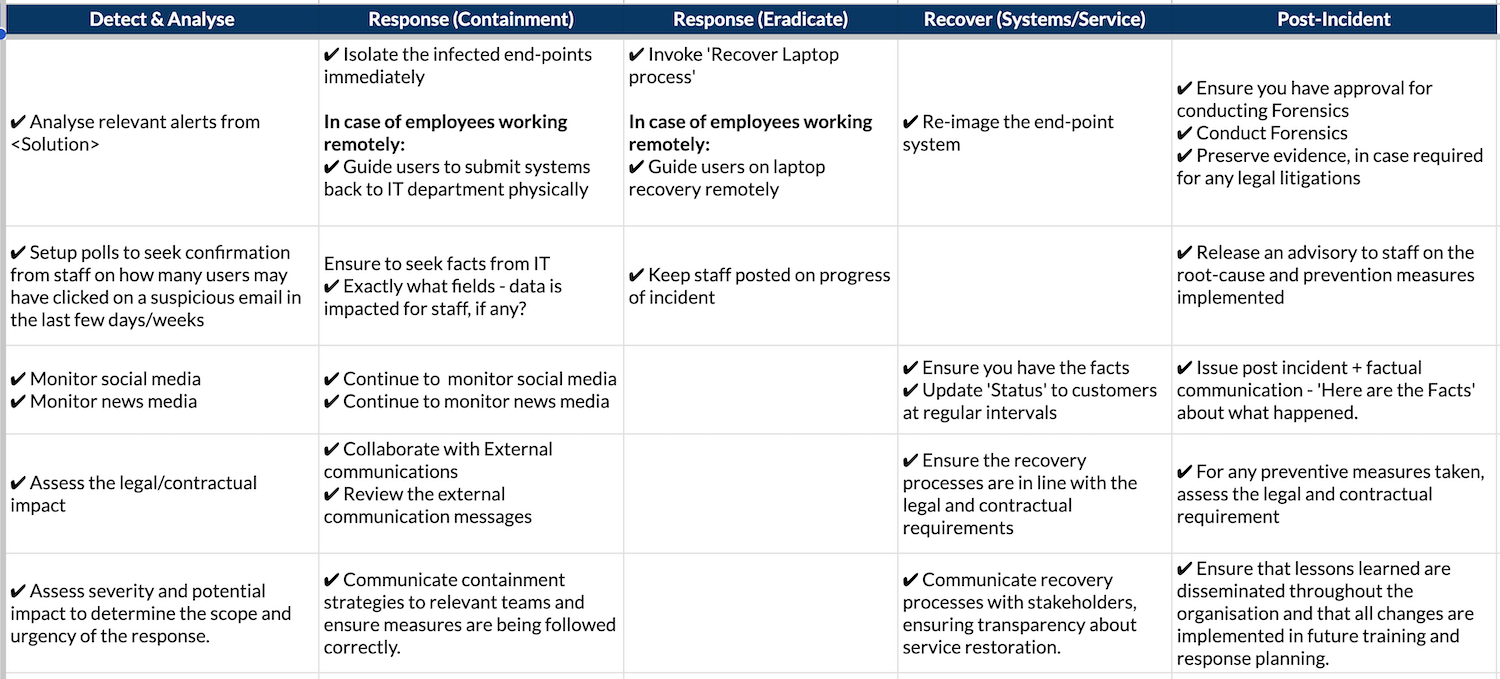
- Phases of Incident Response: Outlines the core stages of incident handling, typically following the NIST 800-61 model:
- Preparation: Activities taken before an incident occurs, such as training, tool acquisition, and policy development.
- Detection and Analysis: Methods for identifying, confirming, and analyzing security incidents to determine their scope, cause, and impact.
- Containment: Strategies and actions to limit the damage and prevent further spread of the incident (e.g., isolation, shutdown).
- Eradication: Steps taken to remove the cause of the incident from affected systems (e.g., patching, malware removal).
- Recovery: Actions to restore affected systems and services to operational status, including validation and monitoring.
- Post-Incident Activity (Lessons Learned): Documentation, review, and analysis of the incident to identify areas for improvement in the policy, procedures, and overall security posture.
- Communication Plan: Specifies who needs to be informed, when, and how, encompassing internal stakeholders (management, employees) and external parties (customers, regulators, law enforcement, media).
- Reporting Requirements: Details the documentation process for incidents, including initial reports, status updates, and final incident reports, which are crucial for compliance and legal obligations.
- Legal and Regulatory Compliance: Addresses specific legal or regulatory requirements that must be met during and after an incident, such as data breach notification laws (e.g., GDPR, CCPA).
- Training and Awareness: Outlines the need for regular training programs for the IRT and general security awareness training for all employees, reinforcing security best practices.
- Policy Review and Update Schedule: Defines a regular cadence for reviewing and updating the Incident Response Policy Template Nist to ensure it remains relevant and effective in the face of evolving threats and organizational changes.
- Glossary of Terms: Provides definitions for key terms used within the policy, ensuring common understanding across all readers and stakeholders.
Design, Usability, and Implementation Tips
An Incident Response Policy Template Nist, however comprehensive, is only as good as its usability and accessibility. When designing and implementing your customized policy, prioritize clarity, practicality, and ease of access for all relevant personnel.
Firstly, keep the language clear, concise, and unambiguous. Avoid overly technical jargon where plain language will suffice, ensuring that even non-technical stakeholders can understand their roles and the overall process. For digital accessibility, consider making the policy available on your internal intranet, a dedicated SharePoint site, or a shared drive, ensuring it’s searchable and easily updated. Use clear headings, bullet points, and flowcharts to break up dense text and make complex processes digestible. For print availability, especially for critical personnel or emergency situations where digital access might be compromised, consider having physical copies available in designated emergency binders.
Implement strong version control for your Incident Response Policy Template Nist. Any updates or revisions should be clearly dated and documented, with previous versions archived, to maintain an accurate history and ensure everyone is working from the most current document. Regular training and awareness programs are also non-negotiable. It’s not enough to just have a policy; your team needs to understand it, practice it, and be able to execute it under pressure. Conduct tabletop exercises and full-scale simulations regularly to test the policy’s effectiveness and identify areas for improvement. Finally, integrate the Incident Response Policy Template Nist with other related policies, such as your data security policy, acceptable use policy, and business continuity plans, to create a cohesive and robust security framework that addresses all facets of your organizational obligations and resilience needs.
In a world where cyber threats are a constant, an organization’s ability to effectively respond to incidents is a true measure of its maturity and resilience. An Incident Response Policy Template Nist is not merely a bureaucratic document; it’s a strategic investment in safeguarding your assets, maintaining operational continuity, and preserving your reputation. It provides the structured guidance needed to navigate the inevitable challenges of the digital landscape, turning potential chaos into a manageable process.
By leveraging the robust framework offered by an Incident Response Policy Template Nist and meticulously customizing it to your specific context, you empower your team with the clarity and direction needed during critical moments. Embrace this proactive approach to cybersecurity, and equip your organization with the tools to not just survive, but thrive, in the face of ever-evolving cyber risks. It’s a practical solution that ensures your business is prepared, protected, and poised for a rapid recovery, reinforcing your commitment to strong data security and incident management.


