In an increasingly interconnected world, where digital transformation drives business operations and personal interactions, the threat landscape for information security is more complex and pervasive than ever before. Organizations of all sizes face a relentless barrage of cyber-attacks, ranging from sophisticated state-sponsored intrusions to opportunistic phishing scams and ransomware attacks. Navigating this treacherous environment successfully requires not just robust preventative measures, but also a clear, actionable plan for when the inevitable happens. This is precisely where an Information Security Incident Management Policy Template becomes an indispensable asset, providing the foundational framework to respond effectively, minimize damage, and maintain trust.
An Information Security Incident Management Policy Template isn’t merely a bureaucratic document; it’s a strategic blueprint for resilience. It empowers organizations to shift from reactive chaos to proactive control when a security incident strikes, ensuring a structured approach to identifying, containing, eradicating, recovering from, and learning from breaches. Whether you’re a small startup handling sensitive customer data or a large enterprise with complex regulatory obligations, having a well-defined Information Security Incident Management Policy Template is critical for protecting your digital assets, your reputation, and ultimately, your bottom line. It serves as a vital guide for everyone from IT security teams to executive leadership, clarifying roles, responsibilities, and the critical steps needed during a crisis.
Why an Information Security Incident Management Policy Template Is Essential in Today’s Context
In the current digital age, the question is no longer if an organization will experience a security incident, but when. The sheer volume and sophistication of cyber threats demand a proactive and well-documented response strategy. An Information Security Incident Management Policy Template provides the necessary structure to navigate these challenges effectively. It acts as a compass, guiding an organization through the turbulent waters of a cyber-attack, ensuring that every step taken is deliberate and aligned with best practices.
Beyond simply reacting to threats, a robust Information Security Incident Management Policy Template is crucial for compliance with a myriad of regulatory requirements. Standards like GDPR, CCPA, HIPAA, and various industry-specific regulations often mandate specific incident response capabilities and breach notification procedures. Without a predefined policy, organizations risk not only significant financial penalties but also severe reputational damage. This template helps establish clear workplace rules and protocols, ensuring that employees understand their obligations and the established procedures for reporting and managing security events. It solidifies an organization’s commitment to data protection and reinforces its legal obligations in safeguarding sensitive information.
Key Benefits of Using an Information Security Incident Management Policy Template
Adopting and implementing a comprehensive Information Security Incident Management Policy Template offers a multitude of benefits that extend far beyond simply addressing a crisis. It transforms potential chaos into a manageable process, yielding tangible advantages for the organization. One primary benefit is the establishment of a standardized, consistent response mechanism. This ensures that every incident, regardless of its scale or nature, is handled with the same level of diligence and according to predefined protocols, reducing the risk of human error and inconsistent actions.
Furthermore, a well-crafted Information Security Incident Management Policy Template significantly minimizes the financial and reputational impact of a security breach. By enabling swift detection and containment, it limits data loss, operational downtime, and the potential for regulatory fines. It also provides a clear communication strategy, which is vital for maintaining stakeholder trust and managing public perception during a crisis. The policy acts as a comprehensive agreement, outlining how various departments, from legal to public relations, will collaborate. This unified approach strengthens an organization’s overall data security posture, fostering a culture of preparedness and continuous improvement in risk management. It transforms a potential disaster into a valuable learning opportunity, enhancing future resilience.
How an Information Security Incident Management Policy Template Can Be Customized or Adapted to Different Needs
While a template provides a solid foundation, its true value comes from its adaptability. An Information Security Incident Management Policy Template is designed to be a flexible framework, not a rigid set of rules. Organizations of varying sizes, industries, and operational complexities will naturally have different needs and risk appetites, making customization an absolute necessity. A small business, for instance, might require a more streamlined version with fewer specialized roles, while a large financial institution would demand a highly detailed policy encompassing multiple layers of authorization and sophisticated forensic capabilities.
Customization involves tailoring the template to reflect an organization’s specific technology stack, legal obligations, and corporate structure. This means adjusting the scope to cover relevant assets, defining roles and responsibilities based on existing teams, and aligning communication protocols with internal and external stakeholder requirements. For example, an organization handling patient health information (PHI) would emphasize HIPAA compliance, whereas one dealing with credit card data would prioritize PCI DSS standards. The Information Security Incident Management Policy Template serves as an executive summary for your incident response strategy, allowing you to insert specific legal terms, define unique workplace rules, and establish reporting obligations that resonate with your particular operational environment. This ensures the policy is not just a document but a living, breathing component of your overall data protection strategy, reflecting the unique challenges and requirements of your business.
Important Elements That Should Be Included in an Information Security Incident Management Policy Template
A robust Information Security Incident Management Policy Template is composed of several critical elements that collectively form a comprehensive plan for handling security incidents. Each section plays a vital role in ensuring a coordinated, effective, and compliant response.
- **Purpose and Scope:** Clearly define why the policy exists and what types of incidents, systems, data, and personnel it covers. This sets the boundaries and expectations for the entire document, outlining the fundamental workplace rules for incident handling.
- **Roles and Responsibilities:** Delineate specific duties and authorities for individuals and teams involved in incident management, including the incident response team, management, legal counsel, and communication specialists. This clarifies reporting obligations and decision-making structures.
- **Incident Definition and Classification:** Establish clear criteria for what constitutes a security incident (e.g., unauthorized access, data loss, malware infection) and how incidents are categorized based on severity and impact. This ensures consistent assessment and prioritization.
- **Detection and Reporting:** Detail the mechanisms for identifying potential incidents and the procedures for employees, customers, or automated systems to report them. Include contact information and required initial information.
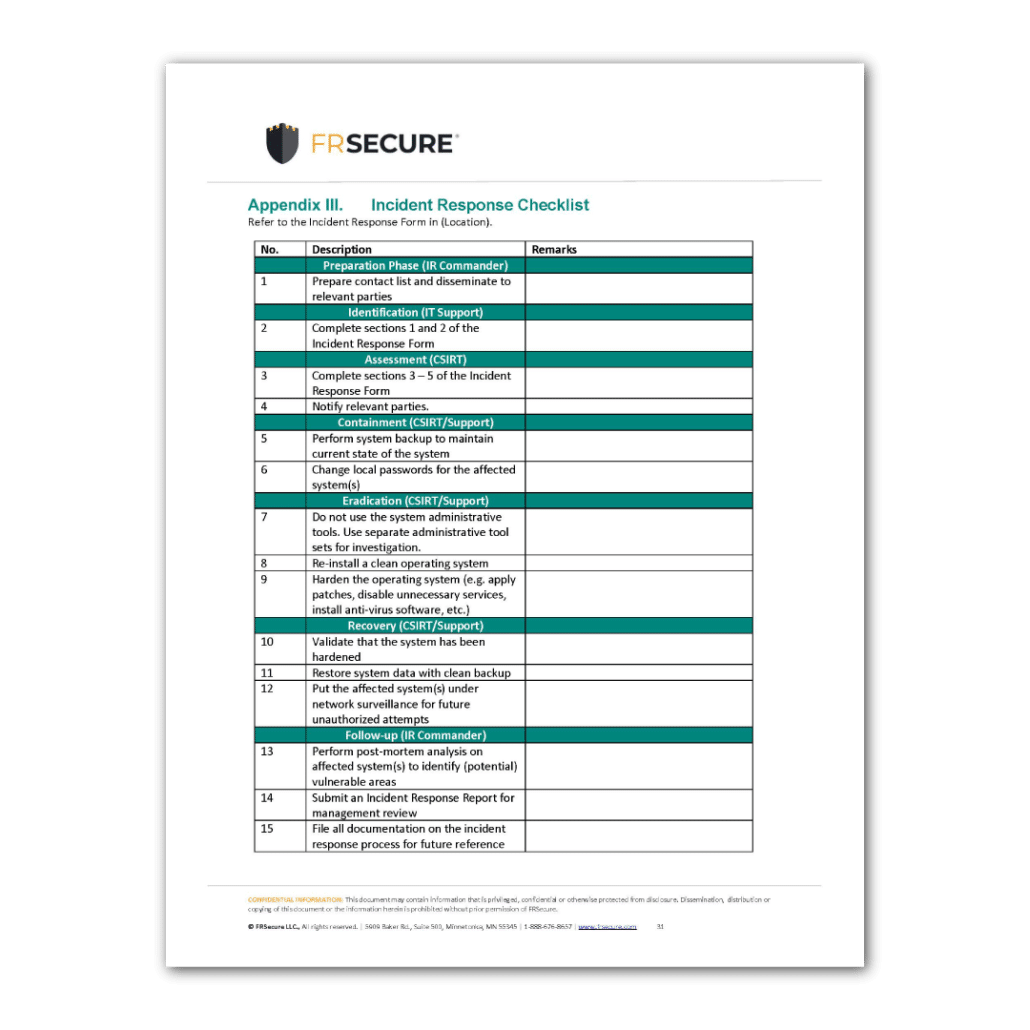
- **Incident Response Phases:** Outline the step-by-step process for handling an incident, typically including:
- **Preparation:** Proactive measures like training, tool acquisition, and policy review.
- **Identification:** Confirming an incident has occurred and gathering initial information.
- **Containment:** Limiting the scope and impact of the incident.
- **Eradication:** Removing the root cause of the incident.
- **Recovery:** Restoring affected systems and data to normal operation.
- **Post-Incident Activity/Lessons Learned:** Analyzing the incident, identifying improvements, and updating policies and procedures.
- **Communication Plan:** Define who needs to be informed, when, and through what channels, both internally (employees, leadership) and externally (customers, regulators, law enforcement, media). This addresses legal terms and public relations strategy.
- **Forensic Analysis and Evidence Handling:** Establish procedures for collecting, preserving, and analyzing digital evidence in a legally sound manner, crucial for investigations and potential legal action.
- **Policy Review and Maintenance:** Specify how often the Information Security Incident Management Policy Template will be reviewed and updated to reflect changes in threats, technology, and organizational structure. This ensures continuous relevance and compliance.
- **Training and Awareness:** Describe the training programs required for employees to understand their roles in incident management and general data security awareness. This reinforces an organization’s commitment to compliance.
- **Regulatory Compliance and Legal Obligations:** Explicitly reference relevant laws, regulations, and contractual agreements that impact incident response, such as breach notification laws or data protection standards.
Tips on Design, Usability, and Implementation
Creating an effective Information Security Incident Management Policy Template goes beyond just the content; its design, usability, and implementation strategy are equally crucial for its success. A policy that is difficult to navigate or understand will be ineffective, regardless of how thoroughly it’s written.
Firstly, focus on clarity and conciseness. Use plain language, avoid excessive jargon, and break down complex concepts into manageable sections. Utilize clear headings, subheadings, bullet points, and numbered lists to improve readability. A well-designed Information Security Incident Management Policy Template should allow a user to quickly find the information they need during a high-stress situation. Consider developing an executive summary for quick reference by senior leadership, alongside a more detailed document for technical teams.
For usability, consider both print and digital formats. While a physical binder might be useful for certain emergency scenarios, a digitally accessible version (e.g., on an internal knowledge base or intranet) is essential. Ensure the digital version is searchable, properly hyperlinked, and compatible with various devices. Integrating flowcharts and decision trees can also be incredibly helpful, visually guiding users through the incident response process.
Implementation is where the rubber meets the road. Simply having an Information Security Incident Management Policy Template isn’t enough; it must be actively used and practiced. This involves comprehensive training for all relevant personnel, from the incident response team to general employees who might be the first to spot an anomaly. Conduct regular drills and tabletop exercises to test the policy’s effectiveness, identify gaps, and ensure everyone understands their roles and responsibilities. Treat the policy as a living document; schedule periodic reviews and updates based on new threats, technological changes, and lessons learned from actual incidents or exercises. This iterative process ensures that your Information Security Incident Management Policy Template remains a relevant, practical, and potent tool in your data security arsenal.
In an era where cyber threats loom larger than ever, waiting for an incident to occur before scrambling for a response plan is a gamble no organization can afford to take. A meticulously crafted and regularly updated Information Security Incident Management Policy Template stands as a beacon of preparedness, offering a clear path through the fog of a security breach. It’s more than just a set of instructions; it’s a testament to an organization’s commitment to protecting its assets, its customers, and its future.
Embracing an Information Security Incident Management Policy Template is an investment in resilience, ensuring that when the inevitable cyber-attack occurs, your organization is not just reacting, but responding with precision and purpose. By proactively defining your incident response strategy, establishing clear workplace rules, and fostering a culture of preparedness, you empower your team to mitigate damage, restore operations swiftly, and safeguard your most valuable digital assets. Make the commitment today to fortify your defenses and ensure your organization can navigate the challenges of the digital landscape with confidence and control.