In today’s interconnected digital landscape, safeguarding sensitive information isn’t just a best practice—it’s a critical imperative. Organizations across every sector face a relentless barrage of cyber threats, from sophisticated phishing attacks to debilitating ransomware. Navigating this complex environment without a clear, structured approach to information security is akin to sailing a ship without a compass. This is precisely where an Information Security Policy Template Iso 27001 becomes an indispensable tool, offering a comprehensive blueprint for protecting your most valuable assets.
Whether you’re a burgeoning startup or an established enterprise, understanding and implementing robust security measures is paramount for maintaining trust, ensuring business continuity, and complying with an ever-growing array of regulations. An Information Security Policy Template Iso 27001 provides a powerful starting point, helping organizations to systematically define their security objectives, manage risks, and foster a culture of vigilance. It’s a foundational element for anyone serious about achieving a high standard of data protection and operational resilience.
Why an Information Security Policy Template Iso 27001 is Essential Today
The modern business world operates under constant threat. Data breaches are not just costly in terms of financial penalties and operational downtime; they can irrevocably damage a company’s reputation and erode customer trust. Regulatory bodies worldwide, including those governing US-based organizations, are imposing stricter compliance requirements, making robust information security policies non-negotiable.
An Information Security Policy Template Iso 27001 offers a proactive defense against these challenges. It outlines the rules and procedures necessary to protect information assets, from intellectual property and financial data to employee and customer records. By adhering to the internationally recognized ISO 27001 standard, organizations demonstrate a serious commitment to managing information security risks effectively, a commitment that resonates with clients, partners, and regulators alike. This framework helps to ensure that all workplace rules and HR guidelines around data handling are clearly defined and consistently enforced.
Key Benefits of Using an Information Security Policy Template Iso 27001
Implementing an Information Security Policy Template Iso 27001 brings a multitude of tangible and intangible benefits to any organization. Firstly, it provides a structured pathway toward achieving ISO 27001 certification, a globally recognized award that signals adherence to the highest standards of information security management. This certification alone can open doors to new business opportunities, especially with partners who require their suppliers to demonstrate a strong security posture.
Beyond certification, the template helps in identifying, assessing, and mitigating information security risks more effectively. It encourages a systematic approach to risk management, leading to better resource allocation and a reduction in the likelihood and impact of security incidents. Furthermore, an Information Security Policy Template Iso 27001 fosters a security-aware culture throughout the organization, as employees become better informed about their roles and responsibilities in protecting sensitive data. This proactive stance can significantly reduce potential liabilities and the considerable costs associated with data breaches and non-compliance. It also strengthens internal controls and helps ensure that all legal terms and obligations related to data handling are met.
How an Information Security Policy Template Iso 27001 Can Be Customized
While the term "template" might suggest a one-size-fits-all solution, an Information Security Policy Template Iso 27001 is designed to be a robust starting point, not a rigid, finished product. Successful implementation hinges on the ability to customize and adapt it to your specific organizational context. No two businesses are exactly alike, and their information security needs will vary significantly based on industry, size, complexity, and the types of data they handle.
For instance, a healthcare provider will have different compliance requirements (like HIPAA in the US) than a financial institution (like GLBA), or a technology startup. The template needs to be tailored to reflect unique business processes, technological infrastructure, and specific legal and contractual obligations. This involves reviewing each section of the Information Security Policy Template Iso 27001 and modifying it to accurately describe your organization’s risk appetite, asset inventory, access controls, and incident response procedures. It’s about making the generalized framework reflect your company’s actual data security landscape and operational realities.
Important Elements to Include in an Information Security Policy Template Iso 27001
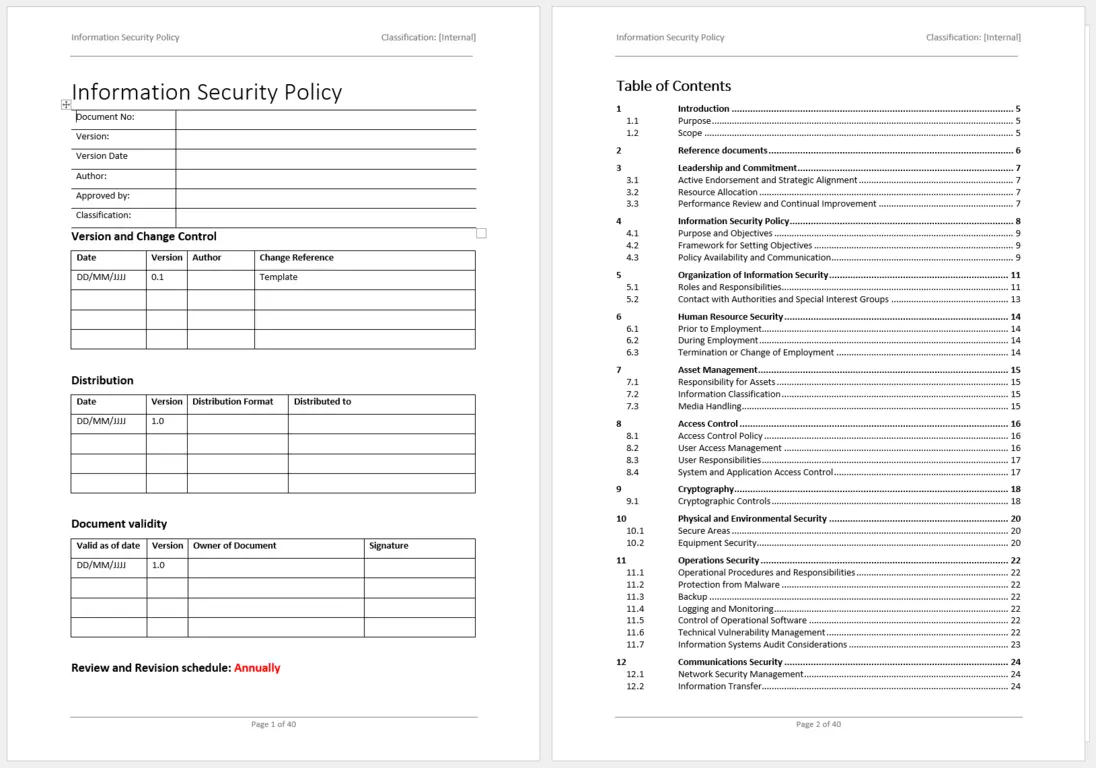
A comprehensive Information Security Policy Template Iso 27001 should cover a wide array of topics to ensure all facets of information security are addressed. These elements form the backbone of your Information Security Management System (ISMS) and provide clear guidance for employees and stakeholders.
- Policy Statement and Scope: Clearly defines the organization’s commitment to information security, its objectives, and the boundaries of the ISMS. This sets the overarching tone and purpose for all subsequent policies.
- Roles and Responsibilities: Outlines who is accountable for specific security tasks and decisions, from top management to individual employees. This includes data ownership and custodianship.
- Risk Assessment and Treatment: Details the methodology for identifying, analyzing, and evaluating information security risks, along with the processes for selecting and implementing appropriate controls.
- Asset Management: Specifies how information assets (physical, digital, and intangible) are identified, classified, and protected based on their value and sensitivity.
- Access Control: Establishes rules for granting, reviewing, and revoking user access to information systems and data, ensuring the principle of least privilege.
- Cryptography: Defines the organization’s approach to using cryptographic controls to protect the confidentiality, integrity, and authenticity of information.
- Physical and Environmental Security: Addresses measures to protect information processing facilities and physical assets from unauthorized access, damage, and interference.
- Operations Security: Covers procedures for managing operational systems, including backup, logging, monitoring, and patch management to prevent failures and unauthorized access.
- Communications Security: Details measures for securing networks, electronic communications, and information transfers both internally and externally.
- Supplier Relationships: Outlines requirements for managing information security risks associated with third-party suppliers, vendors, and partners, including contractual obligations.
- Information Security Incident Management: Establishes a structured process for responding to, reporting, and learning from information security incidents and data breaches.
- Information Security Aspects of Business Continuity Management: Ensures that information security is integrated into business continuity and disaster recovery planning to maintain operational resilience.
- Compliance: Articulates the organization’s adherence to relevant legal, statutory, regulatory, and contractual obligations, including privacy laws and industry-specific mandates.
- Review and Improvement: Sets out a framework for regular reviews of the ISMS performance, audits, and continuous improvement processes to adapt to evolving threats and business needs.
Tips on Design, Usability, and Implementation
A well-crafted Information Security Policy Template Iso 27001 is only effective if it’s usable and understood by everyone it applies to. When designing and implementing your customized policy, consider these tips for maximum impact. First, prioritize clarity and conciseness. Avoid overly technical jargon; aim for language that is accessible to all employees, regardless of their technical background. Short paragraphs (typically 2-4 sentences) and bullet points enhance readability significantly, whether the policy is viewed in print or digital format.
Next, ensure a logical structure with clear headings and subheadings. This makes it easy for users to navigate and find specific information quickly. For digital versions, consider interactive elements, search functions, and hyperlinking to related documents or resources, such as workplace rules or HR policies. Version control is also crucial; clearly mark the current version, date of last review, and approval status to avoid confusion. Finally, effective implementation goes beyond simply publishing the document. It requires ongoing communication, training, and awareness programs to ensure that all employees understand their role in upholding the organization’s information security posture. Regular training sessions and awareness campaigns are key to embedding these policies into the daily operations and overall company culture, turning abstract agreements into concrete actions.
Implementing an Information Security Policy Template Iso 27001 is a journey, not a destination. It represents a continuous commitment to protecting your organization’s valuable information assets in an ever-evolving threat landscape. By adopting this structured approach, you’re not merely ticking a compliance box; you’re building a resilient, trustworthy, and secure operational environment that safeguards your future.
Leveraging an Information Security Policy Template Iso 27001 provides the foundational framework necessary to navigate the complexities of modern cyber risks with confidence. It empowers you to not only meet regulatory demands but also to instill confidence in your customers and stakeholders, proving your dedication to data integrity and privacy. Embrace this powerful tool to strengthen your defenses and ensure your organization remains secure and compliant in the digital age.


