In today’s interconnected digital landscape, safeguarding sensitive information isn’t just a best practice—it’s an absolute imperative. From multinational corporations to budding startups, every organization faces an unrelenting barrage of cyber threats, regulatory pressures, and the ever-present risk of data breaches. Navigating this complex environment requires more than just advanced technology; it demands a robust, clearly defined set of rules and guidelines that govern how information is handled. This is precisely where an Information Security Policy Template Nist becomes an indispensable asset.
For any organization grappling with establishing or refining its cybersecurity posture, the idea of starting from scratch can be daunting. The good news is, you don’t have to. Leveraging a well-structured Information Security Policy Template Nist provides a foundational framework, drawing upon the authoritative guidance of the National Institute of Standards and Technology. This isn’t merely a document; it’s a strategic blueprint designed to protect your valuable data, ensure compliance with various regulatory requirements, and foster a culture of security throughout your entire enterprise. It’s particularly beneficial for IT managers, compliance officers, risk management professionals, and business owners looking to formalize their security efforts.
Why an Information Security Policy Template Nist is Essential
The modern business environment is a minefield of digital dangers. Ransomware attacks, phishing scams, insider threats, and sophisticated cyber espionage campaigns are daily realities. Without a clear and comprehensive information security policy, an organization is left vulnerable, reacting to incidents rather than proactively preventing them. This is why an Information Security Policy Template Nist is so critical. It provides a structured approach to identifying and mitigating risks, translating complex security requirements into actionable workplace rules.
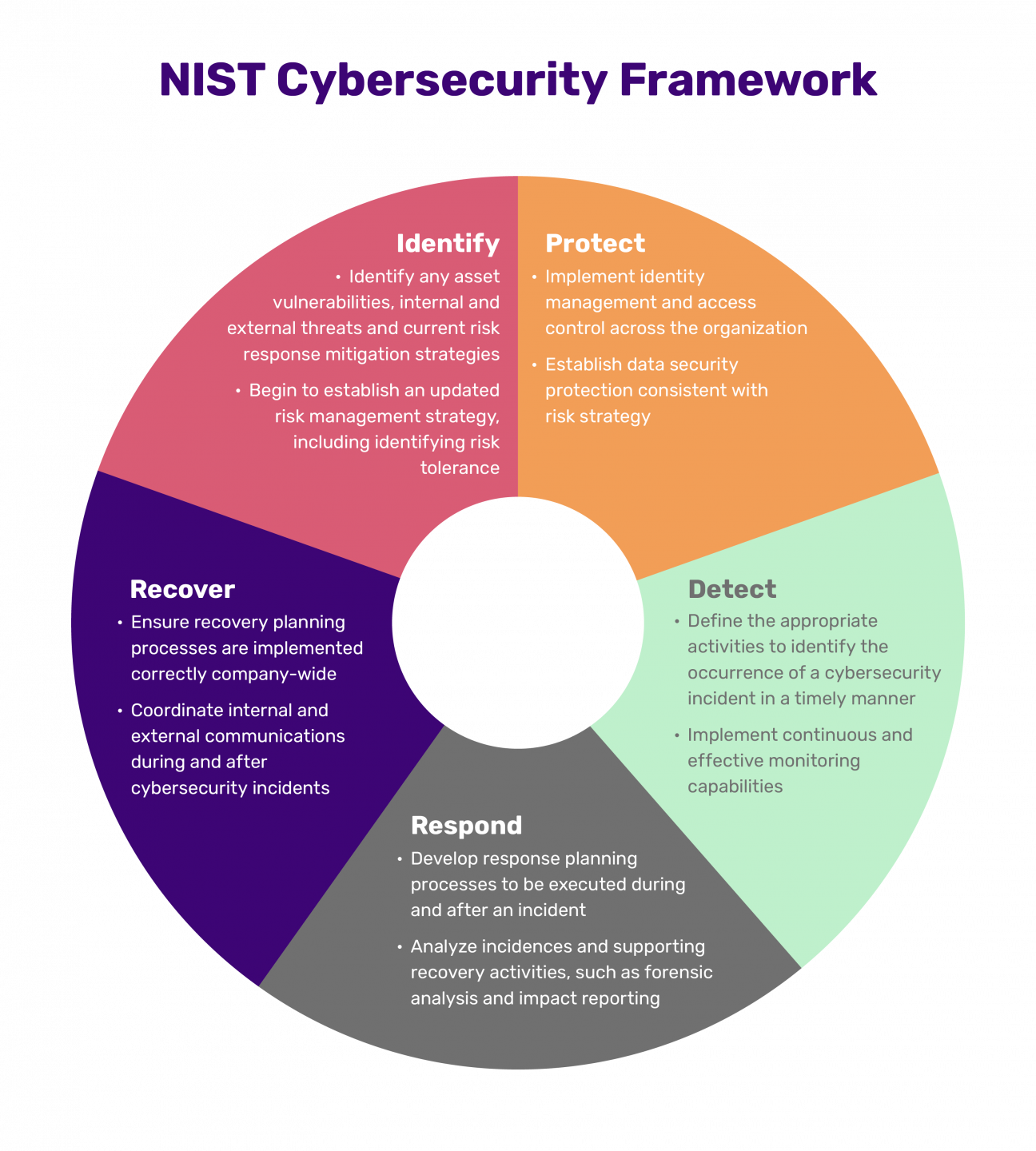
Beyond merely fending off attacks, regulatory compliance is a massive driver for adopting such a framework. Industries ranging from healthcare (HIPAA) to finance, and government contractors (CMMC), face stringent data protection obligations. The National Institute of Standards and Technology (NIST) frameworks, such as NIST SP 800-53 or the NIST Cybersecurity Framework, are widely recognized as authoritative benchmarks. By basing your policy on an Information Security Policy Template Nist, you naturally align your security practices with these recognized guidelines, significantly easing the burden of audits and demonstrating due diligence to regulatory bodies and contractual obligations.
Key Benefits of Using an Information Security Policy Template Nist
Adopting an Information Security Policy Template Nist offers a multitude of tangible benefits that extend far beyond simply having a document on file. Firstly, it establishes a standardized approach to information security across the entire organization. This consistency ensures that all employees, from the CEO to new hires, understand their roles and responsibilities in protecting data, minimizing confusion and potential security gaps. It’s about creating a unified front against cyber threats.
Secondly, it significantly enhances risk management. By clearly outlining policies for data access, handling, storage, and disposal, the template helps identify potential vulnerabilities and implement controls before incidents occur. This proactive stance reduces the likelihood of costly data breaches and their associated reputational damage. Furthermore, an Information Security Policy Template Nist acts as a critical communication tool. It articulates the organization’s commitment to security, setting clear expectations for employee conduct and vendor management. This clarity fosters a security-aware culture, where employees are empowered to act as the first line of defense, understanding the legal terms and obligations related to data protection.
Customizing Your Information Security Policy Template Nist
While an Information Security Policy Template Nist provides an excellent starting point, it’s crucial to understand that it’s not a one-size-fits-all solution. Every organization has unique operational models, industry-specific risks, and compliance requirements. Therefore, customization is not just recommended; it’s essential for the policy to be truly effective and relevant. The beauty of a template lies in its adaptability.
To begin the customization process, conduct a thorough risk assessment specific to your organization. What data do you handle? Where is it stored? Who has access? What are your unique regulatory pressures (e.g., GDPR for European data, CCPA for California residents, or CMMC for DoD contractors)? These questions will guide your modifications. For a small business, a streamlined version focusing on essential controls might suffice, whereas a large enterprise will require more granular details on various security domains, incorporating specific workplace rules and HR policies. Remember, the goal is to tailor the Information Security Policy Template Nist to reflect your actual operations and threat landscape, making it a living document that truly serves your organization’s needs rather than a rigid, generic contract.
Important Elements to Include in Your Information Security Policy Template Nist
A comprehensive Information Security Policy Template Nist should cover a broad spectrum of security domains to ensure all critical aspects of information protection are addressed. These elements form the backbone of your organization’s security posture and must be clearly defined.
Here are the important elements that should be included:
- Policy Scope and Purpose: Clearly define what the policy applies to (systems, data, personnel) and its overall objective (e.g., protect confidentiality, integrity, availability).
- Roles and Responsibilities: Delineate who is responsible for what, from executive leadership to individual employees, including security officers, data owners, and system administrators.
- Information Classification: Establish categories for data (e.g., public, internal, confidential, restricted) and define handling requirements for each.
- Access Control: Detail policies for user access management, least privilege principles, strong authentication requirements (MFA), and regular access reviews.
- Password Policy: Specify minimum password length, complexity, change frequency, and storage guidelines.
- Incident Response: Outline procedures for detecting, reporting, analyzing, and responding to security incidents, including communication plans and recovery steps.
- Security Awareness and Training: Mandate regular training for all employees on security best practices, phishing awareness, and their obligations under the policy.
- Data Encryption: Specify requirements for encrypting data at rest and in transit, especially for sensitive or regulated information.
- Physical Security: Address controls for protecting physical access to facilities, data centers, and equipment where sensitive information is processed or stored.
- Endpoint Security: Policies for securing workstations, laptops, mobile devices, including antivirus, anti-malware, and patch management.
- Network Security: Guidelines for firewalls, intrusion detection/prevention systems, secure network configurations, and segmentation.
- Vulnerability Management: Policies for regular vulnerability scanning, penetration testing, and timely remediation of identified weaknesses.
- Change Management: Procedures for managing and documenting changes to systems, applications, and network infrastructure to minimize security risks.
- Vendor and Third-Party Risk Management: Policies for assessing and managing security risks posed by external service providers and partners.
- Business Continuity and Disaster Recovery: Requirements for backup and recovery plans to ensure operational resilience in the face of disruptions.
- Acceptable Use Policy: Defines appropriate use of company assets, email, internet, and social media for business purposes.
- Monitoring and Auditing: Requirements for logging, monitoring, and auditing security events to detect unauthorized activity and ensure compliance.
- Policy Review and Update: A schedule for periodic review and revision of the policy to keep it current with evolving threats and technologies.
Tips on Design, Usability, and Implementation
A policy, however perfectly crafted, is only effective if it’s understood and followed. This means paying attention to its design, usability, and implementation strategy. When working with an Information Security Policy Template Nist, think about your audience. While the content must be comprehensive, its presentation should prioritize clarity and ease of comprehension for everyone from technical staff to general employees.
For usability, break down complex concepts into digestible sections. Use clear, concise language, avoiding excessive jargon wherever possible. Employ headings, subheadings, bullet points, and tables to enhance readability, much like an executive summary. Consider creating different versions or summaries for various audiences; for example, a high-level overview for general staff and a detailed technical document for IT personnel. Digitally, make the policy easily searchable and accessible through an intranet or document management system. If a printed version is necessary for certain scenarios or initial distribution, ensure it’s professionally formatted, perhaps even using a clear, branded template similar to an award or certificate for completion of training, to underscore its importance. Implementation involves more than just publishing the document; it requires ongoing security awareness training, regular communication, and consistent enforcement of the workplace rules. Embed security into your organizational culture by continuously reinforcing the policy’s principles, making it a fundamental part of daily operations and employee onboarding.
Leveraging an Information Security Policy Template Nist is not merely about ticking a compliance box; it’s about building a resilient, secure foundation for your organization’s future. In an era where data is often an organization’s most valuable asset, protecting it with a well-defined and rigorously implemented information security policy is paramount. It serves as a clear statement of your commitment to security, both internally to your employees and externally to your clients and partners.
By starting with a robust Information Security Policy Template Nist and diligently customizing it to your specific needs, you equip your organization with a powerful tool for risk mitigation, regulatory adherence, and operational stability. It’s an investment that pays dividends by safeguarding your reputation, financial health, and customer trust. Embrace this pragmatic solution to fortify your digital defenses and navigate the complex cybersecurity landscape with confidence.


