In today’s interconnected digital landscape, the question is no longer *if* a security incident will occur, but *when* and *how* prepared your organization will be. Every business, from the nimble startup to the sprawling enterprise, faces a continuous barrage of cyber threats, evolving regulatory demands, and the inherent risks associated with data handling. Navigating this complex environment without a clear, defined strategy is akin to sailing without a compass – perilous and ultimately unsustainable. This is precisely where an Information Security Risk Assessment Policy Template becomes not just helpful, but absolutely indispensable.
An Information Security Risk Assessment Policy Template provides the foundational framework for systematically identifying, analyzing, and mitigating information security risks. It’s a critical tool for CISOs, IT managers, compliance officers, and anyone tasked with safeguarding sensitive data and ensuring business continuity. By offering a structured approach to risk management, this template empowers organizations to move beyond reactive fire-fighting and embrace a proactive, strategic posture against potential threats, ultimately protecting valuable assets and maintaining stakeholder trust.
Why an Information Security Risk Assessment Policy Template is Essential Today
The pace of digital transformation continues to accelerate, bringing with it unprecedented opportunities but also magnified risks. Data breaches, ransomware attacks, and insider threats are commonplace headlines, each carrying significant financial, reputational, and operational consequences. In this volatile environment, an Information Security Risk Assessment Policy Template is not a luxury; it’s a fundamental requirement for responsible corporate governance.
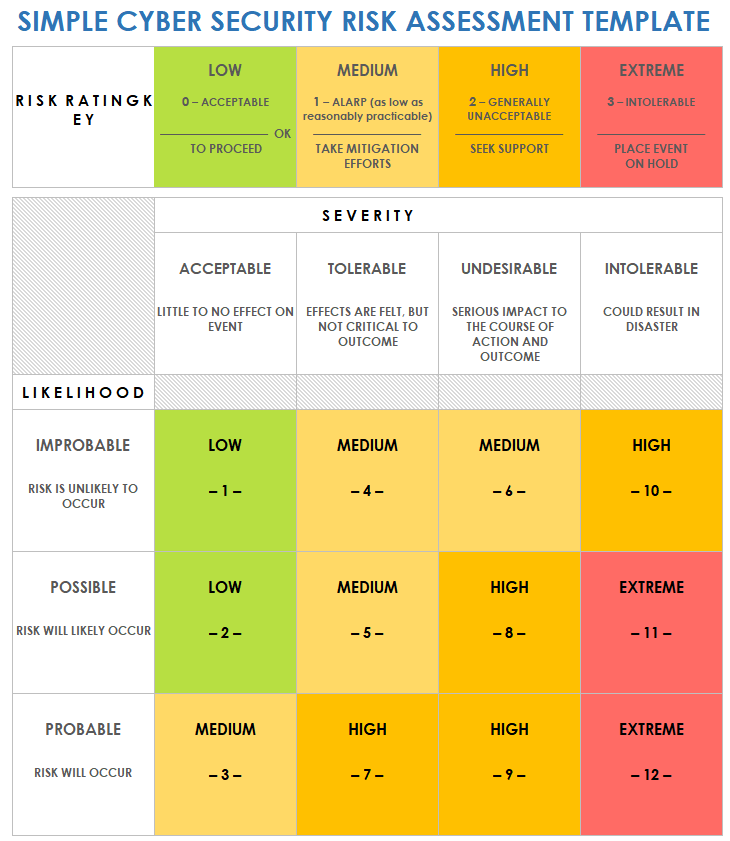
Regulatory bodies worldwide are imposing stricter compliance mandates, such as GDPR, CCPA, HIPAA, and various industry-specific regulations. Failing to demonstrate a robust approach to data security and risk management can lead to hefty fines, legal challenges, and irreversible damage to an organization’s brand. An Information Security Risk Assessment Policy Template provides the documented evidence of your commitment to these obligations, outlining the systematic processes undertaken to protect sensitive information. It serves as a cornerstone for internal controls and demonstrates due diligence to auditors and regulators.
Furthermore, a well-defined Information Security Risk Assessment Policy Template fosters a culture of security awareness throughout the organization. By clearly articulating roles, responsibilities, and methodologies, it ensures that everyone understands their part in the overall risk management strategy. This proactive approach not only helps prevent incidents but also improves an organization’s resilience, enabling quicker and more effective responses should a security event occur. It transforms security from a mere technical concern into a strategic business imperative.
Key Benefits of Using an Information Security Risk Assessment Policy Template
Adopting a standardized Information Security Risk Assessment Policy Template offers a multitude of tangible benefits that extend across an organization’s operational, financial, and strategic dimensions. One of the most significant advantages is the establishment of consistency and clarity in the risk assessment process. Instead of ad-hoc, disparate efforts, the template ensures a uniform methodology, making risk identification and analysis more reliable and comparable over time.
This consistency directly translates into improved resource allocation. With a clear understanding of the highest priority risks, organizations can direct their limited budgets and personnel towards the most critical areas, maximizing the impact of their security investments. An Information Security Risk Assessment Policy Template helps in prioritizing vulnerabilities and threats, ensuring that remediation efforts are focused where they matter most for data security. It allows for a more strategic approach to security spending, rather than reactive, often inefficient, outlays.
Another crucial benefit is enhanced compliance posture. By mapping directly to common security frameworks (like NIST, ISO 27001, or CIS Controls), an Information Security Risk Assessment Policy Template ensures that an organization meets its regulatory and contractual obligations. This not only minimizes legal and financial risks but also builds trust with customers, partners, and other stakeholders who rely on the organization to safeguard their data. It simplifies audit preparation and provides a clear audit trail for all risk management activities.
Finally, an Information Security Risk Assessment Policy Template facilitates better decision-making at all levels. By providing a clear, documented understanding of the organization’s risk landscape, it empowers leadership to make informed choices regarding business initiatives, technology adoption, and strategic investments. It allows for effective communication of risk, turning abstract security concerns into actionable insights that drive business strategy and safeguard future growth.
Customizing Your Information Security Risk Assessment Policy Template for Diverse Needs
While a robust Information Security Risk Assessment Policy Template provides an excellent starting point, its true value is unlocked through thoughtful customization. No two organizations are exactly alike; differences in size, industry, regulatory environment, and technological footprint necessitate adaptation. The beauty of a well-designed template is its inherent flexibility, allowing it to be tailored to meet unique organizational requirements without reinventing the wheel.
For instance, a small business might require a more streamlined Information Security Risk Assessment Policy Template, focusing on foundational controls and common risks, while a large financial institution would need to incorporate highly specific regulatory mandates, complex threat modeling, and detailed contractual obligations. Industry-specific considerations, such as HIPAA for healthcare or PCI DSS for payment processors, must be meticulously integrated into the policy’s scope and methodology. The template should be scalable, enabling it to evolve as the organization grows and its risk profile changes.
Customization also extends to the specific types of information assets being protected. An organization handling vast amounts of personally identifiable information (PII) will emphasize data privacy and compliance elements more heavily than one primarily focused on intellectual property protection. The Information Security Risk Assessment Policy Template should be adaptable enough to incorporate various risk assessment methodologies (e.g., qualitative vs. quantitative), aligning with the organization’s existing risk management framework and preferred analytical approaches.
The key is to view the Information Security Risk Assessment Policy Template not as a rigid set of workplace rules, but as a living document. It should be reviewed and updated regularly to reflect changes in the threat landscape, business operations, and regulatory requirements. This continuous adaptation ensures the policy remains relevant, effective, and a true asset in maintaining a strong data security posture.
Important Elements to Include in Your Information Security Risk Assessment Policy Template
A comprehensive Information Security Risk Assessment Policy Template is structured to provide a clear, actionable guide for managing information security risks. While specifics may vary, several core elements are crucial for any effective template:
- Policy Statement: A high-level declaration of the organization’s commitment to information security risk management, outlining its objectives and strategic importance.
- Scope: Clearly defines what the policy covers, including types of information assets, systems, processes, business units, and geographical locations subject to risk assessment. It should also specify any exclusions.
- Roles and Responsibilities: Delineates who is accountable for what in the risk assessment process. This includes the Information Security Officer, risk owners, asset owners, IT department, HR, and senior management for approval.
- Risk Assessment Methodology: Details the specific approach for identifying, analyzing, and evaluating risks. This includes criteria for defining assets, threats, vulnerabilities, likelihood, and impact. It may specify a qualitative, quantitative, or hybrid approach.
- Risk Register Management: Describes how identified risks will be documented, including risk ID, description, associated assets, likelihood, impact, current controls, residual risk, and risk treatment plans.
- Risk Treatment and Acceptance: Outlines strategies for responding to identified risks (e.g., mitigate, transfer, avoid, accept) and the process for formal risk acceptance by management. This often includes developing specific incident response plans.
- Monitoring and Review Schedule: Specifies how often risk assessments will be conducted, when the policy itself will be reviewed and updated, and how changes in the risk landscape or business operations will trigger reassessments.
- Training and Awareness: A section on the importance of training employees on their obligations related to data security and risk awareness, ensuring the policy’s principles are understood and followed.
- Definitions: A glossary of key terms used within the policy to ensure consistent understanding across the organization.
- Compliance and Regulatory Alignment: Explicitly references relevant laws, regulations, and industry standards that the policy helps to address, reinforcing the organization’s commitment to legal terms and obligations.
- Policy Approval and Version Control: Details the approval authority for the policy and mandates a system for tracking versions and revision history, crucial for audit trails and governance.
Tips for Design, Usability, and Implementation of Your Policy Template
A policy, however perfectly worded, is ineffective if it’s not usable and easily understood by its intended audience. When designing and implementing your Information Security Risk Assessment Policy Template, focus on clarity, accessibility, and integration into daily operations.
First, prioritize clear and concise language. Avoid overly technical jargon where plain English suffices, especially for sections that apply to non-IT personnel. Use headings, subheadings, and bullet points to break up dense text, making the document easy to skim and reference. For digital versions, ensure it’s searchable and ideally hyperlinked to related documents or resources, like specific security standards or incident response procedures. This enhances overall data security guidance.
Consider both print and digital usability. While most modern policies are primarily digital, ensure the Information Security Risk Assessment Policy Template is easily printable in a professional, readable format. For digital access, host it on an accessible internal platform, such as an intranet or a document management system, ensuring version control is robust. Implementing strong version control is paramount to prevent confusion and ensure everyone is referencing the most current set of workplace rules.
Implementation goes beyond simply publishing the document. It requires a strategic communication plan. Conduct awareness campaigns and provide targeted training sessions for key stakeholders, particularly those with defined roles and responsibilities within the policy. Integrate the policy into existing HR onboarding processes for new employees and annual compliance training for existing staff. Regularly reinforce the policy’s importance through internal communications, highlighting its role in safeguarding company assets and meeting compliance obligations. This ongoing engagement transforms the Information Security Risk Assessment Policy Template from a static document into an active component of your organization’s security posture.
In a world where digital threats are constantly evolving, a robust Information Security Risk Assessment Policy Template is more than just a document; it’s a strategic asset. It provides the structured approach necessary to navigate the complex landscape of cyber risks, transforming potential chaos into manageable, actionable insights. By embracing such a template, organizations can systematically identify vulnerabilities, proactively mitigate threats, and build a resilient defense against the ever-present dangers to their data security.
Ultimately, the goal is not merely to avoid breaches but to foster a culture of informed risk management that underpins all business operations. An Information Security Risk Assessment Policy Template empowers organizations to make intelligent, data-driven decisions about security investments, ensuring compliance, protecting reputation, and sustaining long-term growth. Don’t leave your organization’s security to chance; embrace this practical solution to fortify your digital future.


