In today’s interconnected digital world, the question isn’t if an organization will face a security threat, but when and how severe. From sophisticated ransomware attacks to subtle phishing schemes, the threat landscape is constantly evolving, demanding a proactive and structured approach to safeguarding valuable information assets. Navigating this complexity requires more than just technical solutions; it calls for a clear, comprehensive strategy that every employee can understand and adhere to.
This is precisely where a well-crafted Information Security Risk Management Policy Template becomes indispensable. It serves as the foundational blueprint, outlining an organization’s commitment to identifying, assessing, mitigating, and monitoring information security risks in a systematic manner. For IT managers, compliance officers, security professionals, and even C-suite executives, this template provides the framework to build a robust security posture, ensuring business continuity and protecting reputation.
Why an Information Security Risk Management Policy Template is Essential Today
The digital age, while offering unprecedented opportunities, also ushers in an era of heightened cyber threats. Businesses of all sizes are under constant siege from malicious actors aiming to exploit vulnerabilities, leading to costly data breaches, operational disruptions, and severe reputational damage. In this volatile environment, having a robust Information Security Risk Management Policy Template isn’t merely good practice; it’s a critical imperative for survival and sustained success.
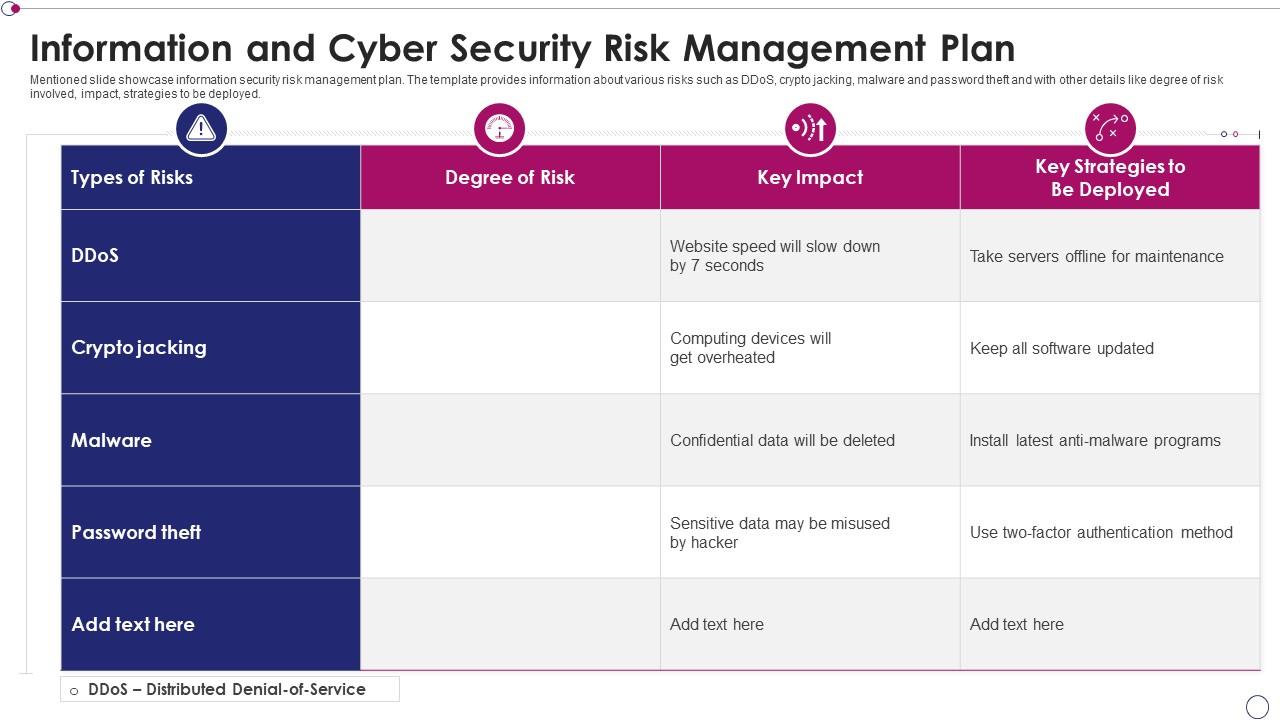
Firstly, the sheer volume and sophistication of cyber threats necessitate a formalized approach. Without a clear policy, organizations often find themselves reacting to incidents rather than proactively preventing them, leading to a fragmented and inefficient security posture. This Information Security Risk Management Policy Template provides the roadmap to anticipate potential attacks, understand their potential impact, and deploy effective security controls before disaster strikes. It underscores the importance of a structured risk assessment process.
Secondly, regulatory compliance has become a non-negotiable aspect of doing business. Regulations like GDPR, CCPA, HIPAA, SOX, and frameworks such as NIST and ISO 27001 impose stringent requirements on how organizations manage and protect sensitive data. A well-implemented Information Security Risk Management Policy Template helps organizations demonstrate due diligence and adherence to these complex legal and industry obligations, mitigating the risk of hefty fines and legal repercussions. It’s a key component for achieving and maintaining compliance.
Finally, an effective policy fosters trust. Customers, partners, and investors increasingly scrutinize an organization’s commitment to data security. A transparent and well-communicated policy signals a professional, responsible approach to protecting information assets, thereby enhancing stakeholder confidence and strengthening market position. It reinforces organizational resilience against evolving cyber threats, transforming potential weaknesses into strategic strengths.
Key Benefits of Using an Information Security Risk Management Policy Template
Leveraging a pre-built Information Security Risk Management Policy Template offers a multitude of advantages that go beyond merely ticking a compliance box. It streamlines the complex process of establishing a comprehensive security framework, delivering tangible benefits across various facets of an organization.
One of the primary benefits is efficiency and consistency. Starting from scratch to create a detailed information security policy can be an arduous, time-consuming task. A robust template provides a pre-structured framework, saving countless hours of research and drafting. Furthermore, it ensures a consistent approach to risk management across all departments and information assets, eliminating ad-hoc security measures and promoting a unified security culture. This consistency is vital for policy enforcement and clear communication of workplace rules regarding data handling.
Secondly, it acts as a powerful compliance catalyst. For organizations grappling with multiple regulatory requirements and industry standards, an Information Security Risk Management Policy Template can be a game-changer. It is designed to incorporate best practices aligned with leading frameworks, making it significantly easier to adapt for specific needs such as HIPAA for healthcare, PCI DSS for payment processing, or CMMC for defense contractors. This greatly simplifies the journey towards achieving and maintaining certification or regulatory adherence, reducing audit complexities.
Moreover, a solid Information Security Risk Management Policy Template significantly improves decision-making. By clearly defining risk appetite, assessment methodologies, and mitigation strategies, it empowers leadership and security teams to make informed decisions regarding security investments, resource allocation, and risk acceptance. This structured approach helps prioritize security controls and allocate budgets effectively, ensuring that resources are directed towards the most critical vulnerabilities and threats. It provides a clear governance structure for managing information security.
Finally, the template contributes to an enhanced security posture and increased stakeholder confidence. By systematizing the identification of vulnerabilities, assessment of threats, and implementation of preventative measures, it inherently strengthens the organization’s defenses against cyberattacks and data breaches. This demonstrable commitment to robust data security policies assures customers, partners, and employees that their sensitive information is being handled responsibly, bolstering reputation and fostering long-term trust.
Customizing Your Information Security Risk Management Policy Template
While a standardized Information Security Risk Management Policy Template provides an invaluable starting point, it’s crucial to understand that no single document can perfectly fit every organization’s unique context. Effective information security isn’t a one-size-fits-all solution; it requires careful adaptation to reflect the specific realities of your business. The power of a template lies in its flexibility as a foundation.
Customization should begin with a thorough understanding of your organization’s specific industry, size, and operational landscape. A small startup with limited data processing may require a less complex policy than a multinational financial institution dealing with vast amounts of sensitive customer data. Consider the particular regulatory obligations that apply to your sector, whether it’s the stringent privacy requirements of healthcare, the financial controls of banking, or specific government contract mandates.
Next, assess your organization’s risk appetite and existing technology stack. What level of risk is your leadership willing to accept? Are you heavily reliant on cloud services, on-premise infrastructure, or a hybrid model? These factors will directly influence the types of security controls, incident response plans, and data protection measures that need to be emphasized within your Information Security Risk Management Policy Template. Tailoring the language and technical specifications to your actual environment ensures relevance and enforceability.
To adapt the template effectively, you might need to:
- Refine the scope: Clearly define which assets, systems, and personnel are covered, aligning with your business operations.
- Integrate specific controls: Add or modify security controls that are unique to your applications, databases, or network architecture.
- Define unique risk thresholds: Adjust the criteria for identifying and evaluating risk levels based on your organizational tolerance.
- Incorporate existing policies: Ensure seamless integration with other HR policies, IT policies, and compliance documents, avoiding contradictions.
- Personalize roles and responsibilities: Clearly assign duties based on your organizational chart and existing team structures.
Remember, the Information Security Risk Management Policy Template is a dynamic tool. It’s a living document that should evolve with your organization, technological advancements, and the ever-changing threat landscape. Treat it as a robust framework that you build upon, rather than a rigid, unalterable text.
Important Elements for Your Information Security Risk Management Policy Template
A truly effective Information Security Risk Management Policy Template is comprehensive, covering all critical aspects of managing information security risks. While the specifics will vary with customization, several core elements should always be present to ensure a robust and actionable policy.
- Policy Statement and Purpose: A clear, concise declaration of the organization’s commitment to information security, outlining the policy’s objectives and its importance in protecting information assets.
- Scope: Defines what the policy covers, including information assets (data, systems, hardware, software), processes, locations, and personnel (employees, contractors, third parties).
- Roles and Responsibilities: Clearly delineates who is accountable for what, from the CISO and IT department to asset owners, departmental heads, and every individual employee. This includes responsibilities for risk identification, mitigation, and adherence.
- Risk Identification Process: Details the methodology for identifying potential threats and vulnerabilities to information assets, including asset classification, threat modeling, and vulnerability assessments.
- Risk Assessment Methodology: Explains how identified risks will be analyzed and evaluated, typically including criteria for determining likelihood, impact, and an overall risk rating (e.g., using a risk matrix).
- Risk Treatment/Mitigation Strategies: Outlines the acceptable approaches to managing identified risks, such as implementing security controls (technical, administrative, physical), risk acceptance, risk transfer (e.g., insurance), or risk avoidance.
- Risk Monitoring and Review: Specifies the procedures for ongoing monitoring of risks, control effectiveness, and the frequency of policy reviews and updates to adapt to new threats and business changes. This also ties into incident response and management.
- Reporting and Communication: Describes how risk information, assessment results, and policy changes will be communicated to relevant stakeholders, including management, employees, and potentially regulatory bodies.
- Compliance and Legal Considerations: References specific laws, regulations, and industry standards (e.g., HIPAA, GDPR, ISO 27001) that the policy aims to satisfy, emphasizing the organization’s commitment to these obligations.
- Definitions and References: A glossary of key terms and references to other related policies, standards, or guidelines to ensure clarity and consistency.
- Policy Enforcement and Disciplinary Actions: Clearly states the consequences for non-compliance with the policy, reinforcing its importance and ensuring accountability.
- Review and Update Schedule: Mandates a regular review cycle for the policy, ensuring it remains current, relevant, and effective in light of evolving threats and organizational changes.
By including these crucial components, your Information Security Risk Management Policy Template transforms into a powerful, actionable document that guides your organization’s security efforts and fosters a culture of diligent risk management.
Tips for Design, Usability, and Implementation
Creating a comprehensive Information Security Risk Management Policy Template is only half the battle; ensuring its usability, accessibility, and effective implementation is equally vital. A well-designed policy is one that isn’t just stored away in a digital folder but actively used and understood by all stakeholders.
Clarity and Simplicity: When designing your policy, prioritize plain language over technical jargon. While some technical terms are unavoidable, ensure they are clearly defined in a glossary. Short, concise paragraphs and bullet points, as seen here, enhance readability. The goal is for everyone, from an entry-level employee to a senior executive, to comprehend their responsibilities and the policy’s intent without needing specialized training. Avoid overly complex sentences that obscure the message.
Accessibility and Discoverability: An excellent Information Security Risk Management Policy Template is useless if no one can find it. Implement it digitally, perhaps on your company intranet or a dedicated compliance portal, making it easily searchable. Consider both desktop and mobile access. For certain critical aspects, a condensed "quick reference guide" or a printable summary might be beneficial for physical notices or during onboarding, especially for frontline staff who might not always have digital access. Version control is also crucial here; always ensure employees are referencing the latest approved version.
Training and Awareness: Policies are only as effective as the understanding and adherence they command. Implement mandatory, regular training sessions for all employees, explaining the core tenets of the Information Security Risk Management Policy Template. Use engaging methods like interactive modules, real-world examples, and quizzes to reinforce learning. Continuous awareness campaigns, such as regular security newsletters or brief reminders, can help keep security top of mind and ensure the policy’s principles become second nature.
Integration and Alignment: Your Information Security Risk Management Policy Template shouldn’t exist in a vacuum. Ensure it integrates seamlessly with other organizational policies, such as acceptable use policies, data privacy statements, HR guidelines, and incident response plans. Cross-referencing these documents can create a cohesive framework that avoids contradictions and provides a holistic approach to governance and workplace rules. This holistic view strengthens the overall security posture.
Regular Review and Updates: The digital threat landscape is dynamic. Your policy must be too. Schedule regular reviews – at least annually, or whenever there are significant organizational changes, technology shifts, or new regulatory requirements. Appoint a dedicated team or individual responsible for monitoring compliance, assessing the policy’s effectiveness, and initiating updates. This iterative process ensures your Information Security Risk Management Policy Template remains relevant, robust, and capable of addressing emerging cyber threats.
Emphasizing these design and implementation tips will transform your Information Security Risk Management Policy Template from a mere document into an active, protective force within your organization, fostering a strong culture of data security.
Crafting a comprehensive Information Security Risk Management Policy Template might seem like a daunting task, but the effort invested is an invaluable step towards securing your organization’s future. In an era where data is paramount and cyber threats are relentless, a clear, well-articulated policy acts as your first line of defense, guiding every decision and action related to information security. It’s not just about meeting regulatory requirements; it’s about building resilience, protecting reputation, and ensuring business continuity in the face of adversity.
By leveraging a structured Information Security Risk Management Policy Template, you empower your team with clarity, consistency, and a shared understanding of their roles in safeguarding sensitive information. This proactive approach transforms potential vulnerabilities into strengths, turning the abstract concept of "cybersecurity" into actionable, everyday practices. Consider this template not as an expense, but as a strategic investment in your organization’s long-term stability, trustworthiness, and success.

