In an era defined by ubiquitous digital connectivity, the security of information has transitioned from a niche IT concern to a paramount business imperative. Every organization, regardless of its size or sector, is a custodian of valuable data – from sensitive customer details and intellectual property to critical operational records. The constant threat of cyberattacks, data breaches, and regulatory non-compliance looms large, making a robust information security framework not just a best practice, but an absolute necessity for survival and growth.
This is where the ISO 27001 standard emerges as a beacon, providing a globally recognized framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). However, embarking on the journey to ISO 27001 certification or simply fortifying your security posture can feel like a daunting task, especially when it comes to crafting comprehensive and compliant policies from scratch. This is precisely why an Iso 27001 Information Security Policy Template Pdf becomes an invaluable asset, offering a streamlined, pre-structured foundation that benefits anyone from startups seeking foundational security to large enterprises refining their existing ISMS documentation.
Why an Iso 27001 Information Security Policy Template Pdf is Essential in Today’s Context
The contemporary business landscape is a minefield of information security risks. From sophisticated phishing campaigns and ransomware attacks to insider threats and accidental data leaks, the avenues for compromise are diverse and ever-evolving. Moreover, the regulatory environment has tightened considerably, with legislation like GDPR, CCPA, and HIPAA imposing significant penalties for data breaches and non-compliance. In this intricate scenario, having a clear, actionable, and ISO 27001 compliant information security policy is not just beneficial, it’s critical.
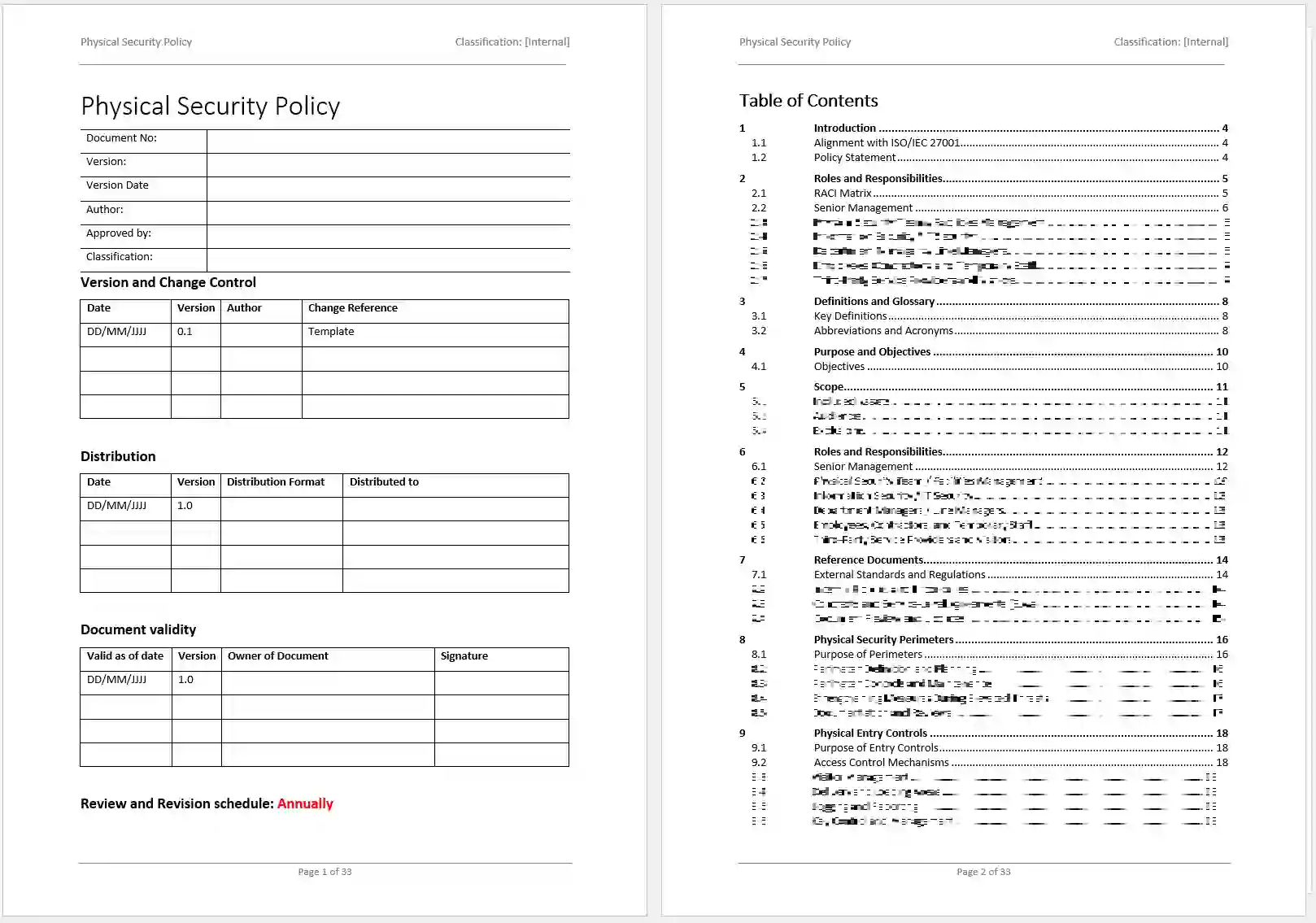
An Iso 27001 Information Security Policy Template Pdf provides the bedrock for managing these complex challenges. It translates the abstract principles of ISO 27001 into concrete, organizational policies that guide employee behavior, define security controls, and establish clear responsibilities. Without such a foundational document, an organization risks inconsistent security practices, confusion among staff, and a significantly higher probability of security incidents. It demonstrates a proactive commitment to protecting information assets, which in turn builds trust with customers, partners, and stakeholders, distinguishing your organization as a responsible data steward in a competitive market.
Key Benefits of Using an Iso 27001 Information Security Policy Template Pdf
Adopting a pre-designed Iso 27001 Information Security Policy Template Pdf offers a multitude of advantages that can significantly accelerate and streamline your information security initiatives. These benefits extend beyond mere compliance, touching upon efficiency, cost-effectiveness, and overall organizational resilience.
Firstly, efficiency and time savings are paramount. Developing a comprehensive set of information security policies from the ground up requires extensive research, expert knowledge of ISO 27001 requirements, and considerable time investment. A robust Iso 27001 Information Security Policy Template Pdf bypasses much of this initial heavy lifting, providing a ready-made structure that aligns with the standard, allowing your team to focus on customization rather than creation. This dramatically shortens the development cycle.
Secondly, it leads to cost-effectiveness. Engaging external consultants to draft policies can be expensive. By utilizing an Iso 27001 Information Security Policy Template Pdf, organizations can significantly reduce these costs, leveraging internal resources to adapt a proven framework. This makes robust information security more accessible, especially for small to medium-sized businesses with tighter budgets.
Thirdly, it ensures consistency and clarity. A well-structured template promotes a standardized approach to information security across all departments. This consistency is vital for avoiding gaps in coverage, ensuring that all aspects of data handling, access control, and incident response are uniformly understood and applied. Clear, concise policies reduce ambiguity and empower employees to make secure decisions.
Fourthly, an Iso 27001 Information Security Policy Template Pdf acts as a powerful enabler for enhanced compliance and certification readiness. It directly addresses the documentation requirements of ISO 27001, making the certification audit process smoother and less stressful. Auditors will appreciate a logical, comprehensive set of organizational policies that clearly demonstrate adherence to the standard’s controls.
Finally, it contributes to proactive risk reduction. By outlining specific procedures and controls for various aspects of information security, the template helps identify and mitigate potential vulnerabilities before they can be exploited. This proactive stance is crucial for protecting sensitive data, maintaining business continuity, and safeguarding your organization’s reputation against the potentially devastating impact of a security breach.
How an Iso 27001 Information Security Policy Template Pdf Can Be Customized or Adapted
While an Iso 27001 Information Security Policy Template Pdf provides an excellent starting point, it’s crucial to understand that it’s a foundation, not a one-size-fits-all solution. Effective information security policies must be tailored to the unique context of your organization. Customization is not just recommended; it’s a requirement of ISO 27001, which emphasizes the need for an ISMS that fits the organization’s specific needs and risks.
The adaptation process begins with a thorough understanding of your organization’s operational environment. Consider your industry sector, as specific regulatory compliance requirements (e.g., healthcare, finance) will influence policy content. Your organizational size, structure, and geographical locations will also play a role, impacting aspects like roles and responsibilities, physical security, and communication protocols. The types of information assets you handle – intellectual property, customer data, financial records – and their criticality will dictate the level of protection required.
Furthermore, your existing technological infrastructure, including cloud services, on-premise systems, and mobile device usage, must be reflected in policies related to data security and access control. It’s also vital to integrate the template with any existing corporate governance, HR, or workplace rules that are already in place, ensuring a cohesive set of organizational policies rather than a disjointed collection. Engage key stakeholders from different departments – IT, HR, legal, operations, and senior management – in the customization process. Their input ensures that the policies are practical, enforceable, and reflect the true operational landscape of the business. A well-customized Iso 27001 Information Security Policy Template Pdf becomes a living document that genuinely supports your organization’s security objectives.
Important Elements to Include in an Iso 27001 Information Security Policy Template Pdf
A comprehensive Iso 27001 Information Security Policy Template Pdf needs to address various facets of information security to be truly effective and compliant. While the exact scope might vary, certain core elements are indispensable for any organization seeking to implement robust data security measures. These elements form the backbone of your Information Security Management System (ISMS).
- Scope and Objectives: Clearly define what the ISMS covers (e.g., specific departments, systems, data types) and state the overarching goals of information security within the organization. This sets the stage for all subsequent policies.
- Information Security Roles and Responsibilities: Outline who is responsible for what, from top management to individual employees. This includes roles like the CISO, data owners, system administrators, and general staff obligations regarding data protection.
- Risk Management Framework: Describe the organization’s approach to identifying, assessing, treating, and monitoring information security risks. This is a central component of ISO 27001.
- Acceptable Use of Assets: Detail guidelines for the appropriate use of organizational assets, including computers, networks, software, and mobile devices, preventing misuse and unauthorized activities.
- Access Control Policy: Establish rules for granting, reviewing, and revoking access to information systems and data based on the principle of least privilege, ensuring only authorized personnel can access sensitive information.
- Incident Management and Response: Define procedures for reporting, managing, and recovering from information security incidents and breaches, including communication plans and forensic analysis.
- Business Continuity and Disaster Recovery: Outline strategies and plans to ensure the continued availability of critical information and systems in the event of disruptive incidents.
- Data Classification and Handling: Establish a system for classifying information based on its sensitivity and criticality, and prescribe appropriate handling, storage, and disposal methods for each classification.
- Physical and Environmental Security: Address controls for protecting physical facilities and equipment where information assets are stored or processed, including access to server rooms and offices.
- Supplier Relationship Security: Define requirements and controls for managing information security risks associated with third-party vendors and external suppliers, ensuring their compliance with your standards.
- Legal and Regulatory Compliance: Document how the organization meets its legal, statutory, regulatory, and contractual obligations related to information security and privacy.
- Policy Review and Update Process: Specify how frequently policies will be reviewed, updated, and approved, ensuring they remain current and relevant to the evolving threat landscape and organizational changes.
Tips for Design, Usability, and Implementation of Your Iso 27001 Information Security Policy Template Pdf
Developing a comprehensive Iso 27001 Information Security Policy Template Pdf is only half the battle; ensuring it is usable, accessible, and effectively implemented is equally crucial. A policy document, no matter how technically sound, is ineffective if it’s not understood or followed by your employees.
Clarity and Simplicity should be your guiding principles for design. Avoid overly technical jargon where possible, or provide clear definitions. Use plain language that all employees, regardless of their technical background, can comprehend. Short, concise paragraphs and bullet points, as demonstrated throughout this article, enhance readability. This ensures that the essential workplace rules and compliance obligations are easily digestible.
Consider Accessibility for both print and digital formats. While the "Pdf" in Iso 27001 Information Security Policy Template Pdf suggests a digital document, some organizations may still require printed versions for specific contexts or for employees without regular computer access. Ensure the PDF is searchable and bookmarkable for easy navigation. For digital distribution, hosting it on an intranet or a dedicated document management system with proper access controls makes it readily available.
Version Control is paramount. Implement a clear system for tracking changes, version numbers, and approval dates. Each policy document should explicitly state its version number and effective date. This prevents confusion and ensures that everyone is working from the most current set of organizational policies. Regular review cycles, as mandated by ISO 27001, necessitate robust version management.
Training and Awareness are non-negotiable for successful implementation. Policies sitting in a folder are useless. Conduct mandatory training sessions for all employees, explaining the importance of the policies, their individual responsibilities, and the consequences of non-compliance. Reinforce key concepts through regular awareness campaigns, newsletters, and internal communications.
Finally, foster Stakeholder Buy-in from the top down. Senior management must visibly support and champion the information security policies. Their commitment cascades through the organization, encouraging employees to take their responsibilities seriously. Regularly review policy effectiveness and gather feedback to continuously improve, ensuring your Iso 27001 Information Security Policy Template Pdf evolves with your organization and the threat landscape.
In a world increasingly reliant on digital data, the integrity, confidentiality, and availability of information are non-negotiable. Embracing the ISO 27001 standard through a well-crafted and implemented information security policy is not merely about achieving a certification; it’s about building a resilient, trustworthy, and secure organization prepared for the challenges of the digital age.
The journey to robust information security can be complex, but with an Iso 27001 Information Security Policy Template Pdf, you gain a significant head start. It provides the structure, the content, and the confidence to establish clear guidelines, manage risks effectively, and protect your most valuable assets. Think of it as investing in an essential blueprint that underpins your entire data security strategy, ensuring all employees understand their roles in maintaining a secure environment.
Ultimately, leveraging an Iso 27001 Information Security Policy Template Pdf is a strategic move towards operational excellence and enhanced organizational trust. It streamlines compliance efforts, strengthens your defense against cyber threats, and demonstrates a steadfast commitment to protecting sensitive information. For any organization serious about safeguarding its future, considering this practical and comprehensive solution is not just smart business—it’s imperative.