In today’s interconnected digital world, information is arguably an organization’s most valuable asset. From proprietary customer data and intellectual property to operational secrets, the sheer volume and sensitivity of information demand rigorous protection. Yet, the landscape of cyber threats is constantly evolving, presenting unprecedented challenges for businesses of all sizes. This escalating risk profile underscores a critical need for a structured, comprehensive approach to information security management.
This is where ISO 27001 enters the picture. As the internationally recognized standard for Information Security Management Systems (ISMS), it provides a robust framework to help organizations protect their information assets. A cornerstone of achieving and maintaining ISO 27001 certification is a well-defined and rigorously implemented information security policy. For many, crafting such a comprehensive document from scratch can be a daunting task. That’s precisely why an Iso 27001 Information Security Policy Template becomes an invaluable resource, offering a structured starting point for any organization serious about bolstering its defenses and demonstrating commitment to data security best practices.
Why an Iso 27001 Information Security Policy Template is Essential Today
The importance of a robust information security policy, informed by an Iso 27001 Information Security Policy Template, cannot be overstated in our current environment. Organizations face a daily barrage of cyber threats, ranging from sophisticated ransomware attacks and phishing scams to insider threats and accidental data leaks. Beyond the immediate operational disruption, these incidents can lead to severe financial penalties, significant reputational damage, and a profound loss of customer trust.
Furthermore, the regulatory landscape is becoming increasingly complex and stringent. Laws like the General Data Protection Regulation (GDPR) in Europe, the California Consumer Privacy Act (CCPA), and countless industry-specific regulations (such as HIPAA in healthcare or PCI DSS for payment card data) impose strict requirements on how organizations handle and protect personal and sensitive information. A well-crafted information security policy derived from an Iso 27001 Information Security Policy Template helps ensure compliance with these myriad legal obligations, mitigating the risk of costly fines and legal challenges.
Beyond compliance, having a clear and comprehensive information security policy signals to stakeholders—customers, investors, and partners—that your organization takes data protection seriously. It demonstrates a proactive approach to risk management and corporate governance, which can be a significant competitive differentiator. This level of transparency and commitment builds confidence and fosters a more secure operational environment for everyone involved.
Key Benefits of Using an Iso 27001 Information Security Policy Template
Leveraging an Iso 27001 Information Security Policy Template offers a multitude of benefits, streamlining the complex process of establishing a world-class information security management system (ISMS). Perhaps the most significant advantage is the rapid acceleration of your ISO 27001 certification journey. Instead of spending countless hours researching and drafting policies from the ground up, the template provides a pre-structured framework that aligns with the standard’s requirements, saving valuable time and resources.
Moreover, these templates are typically designed by experts with deep knowledge of ISO 27001, ensuring that critical areas are covered and best practices are incorporated. This significantly reduces the risk of overlooking essential controls or misinterpreting the standard’s clauses. By starting with a proven foundation, organizations can be more confident in the completeness and effectiveness of their security posture, ultimately leading to a more successful audit outcome.
An Iso 27001 Information Security Policy Template also promotes consistency across the organization. It ensures that all information security policies, procedures, and guidelines speak the same language and adhere to a unified strategy. This consistency is crucial for effective risk management, as it minimizes ambiguities and ensures that employees at all levels understand their roles and responsibilities in maintaining data security. It fosters a culture of security awareness, making information protection a shared organizational goal rather than an isolated IT function.
Customizing Your Iso 27001 Information Security Policy Template
While an Iso 27001 Information Security Policy Template provides an excellent foundation, it’s crucial to understand that it’s not a one-size-fits-all solution. Every organization is unique, with its own operational context, industry-specific risks, technological infrastructure, and regulatory landscape. Therefore, effective implementation demands significant customization to ensure the template truly reflects your specific needs and challenges.
Begin by assessing your organization’s specific risk profile. What kind of data do you handle? What are your most critical information assets? What threats are most pertinent to your industry? For instance, a healthcare provider will have different regulatory concerns (like HIPAA) and data types than a financial institution or a software development firm. The template should be adapted to clearly articulate policies relevant to these unique circumstances, going beyond generic statements to address your actual vulnerabilities.
Consider your organizational structure, size, and culture. A small startup will have different resources and operational complexities than a large multinational corporation. The roles and responsibilities section of your Iso 27001 Information Security Policy Template, for example, needs to be tailored to accurately assign duties within your existing hierarchy. Moreover, the language and tone of the policy should resonate with your employees, making it accessible and understandable, rather than an overly technical or legalistic document that gathers dust.
Important Elements of an Iso 27001 Information Security Policy Template
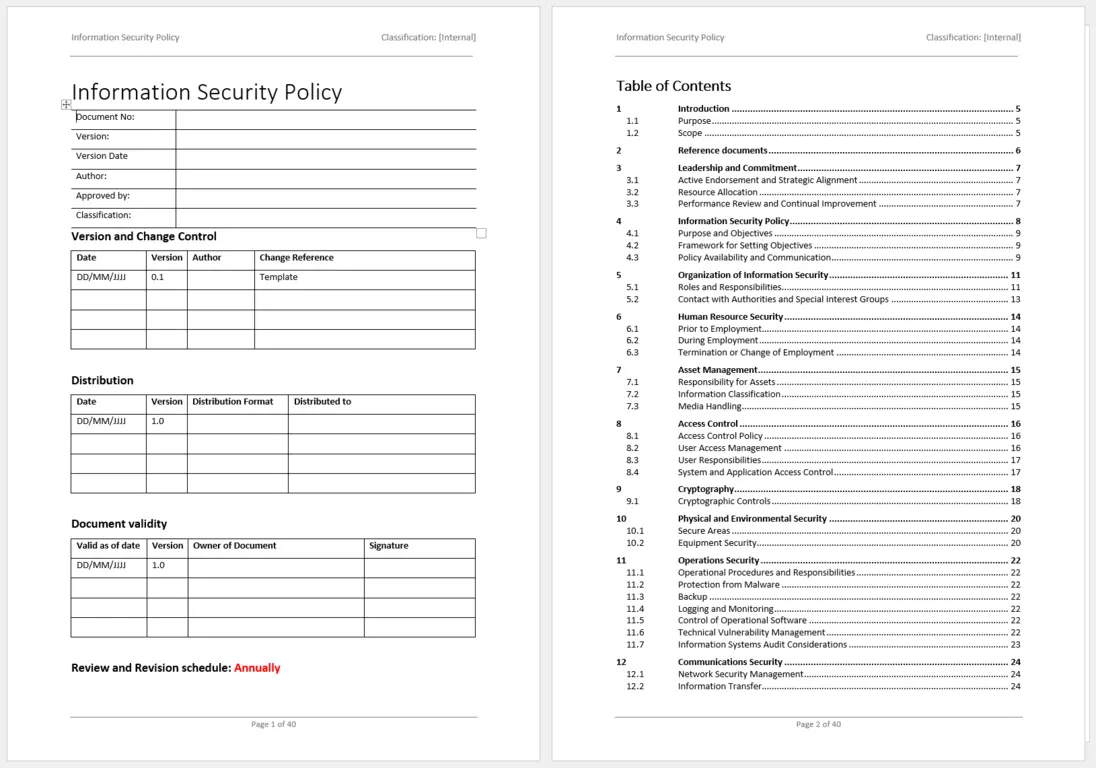
A comprehensive Iso 27001 Information Security Policy Template should meticulously cover all the critical domains of information security as outlined by the ISO 27001 standard. While the exact phrasing and depth will vary based on customization, certain core elements are indispensable for creating a robust and effective policy document.
Here are the key elements that should be included:
- Policy Scope and Objectives: Clearly define what the policy covers (e.g., all information assets, all employees, third parties) and its primary goals, such as protecting confidentiality, integrity, and availability of information.
- Information Security Organization: Detail the governance structure for information security, including roles, responsibilities, and authorities (e.g., Chief Information Security Officer, Information Security Committee).
- Asset Management: Outline policies for identifying, classifying, and managing information assets throughout their lifecycle, including ownership, acceptable use, and retention.
- Human Resources Security: Address security considerations related to employees, from pre-employment screening and awareness training to disciplinary processes and termination procedures.
- Physical and Environmental Security: Establish policies for protecting physical facilities and equipment where information assets are stored or processed, including access control, power supply, and environmental controls.
- Access Control: Define rules for granting, reviewing, and revoking access to information systems, applications, and data based on the principle of least privilege.
- Cryptography: Provide guidance on the use of encryption and cryptographic controls to protect the confidentiality and integrity of information, both in transit and at rest.
- Operational Security: Cover policies related to the secure operation of information processing facilities, including malware protection, backup and restoration, logging, and monitoring.
- Communications Security: Address policies for securing network services, information transfer, and electronic messaging against unauthorized access or modification.
- Supplier Relationships: Outline requirements for managing information security risks associated with third-party suppliers, vendors, and partners.
- Information Security Incident Management: Define procedures for reporting, assessing, responding to, and recovering from information security incidents. This includes establishing a clear incident response team and communication plan.
- Information Security Aspects of Business Continuity Management: Detail policies to ensure the continuity of information security during disruptive events, linking to the organization’s broader business continuity plans.
- Compliance: State the organization’s commitment to complying with all relevant legal, statutory, regulatory, and contractual obligations related to information security. This section should also outline the policy review and update schedule.
Tips for Design, Usability, and Implementation
A well-written Iso 27001 Information Security Policy Template is only effective if it’s usable and actively implemented within the organization. The design and presentation of your final policy document play a crucial role in its adoption and understanding. Start by ensuring clarity and conciseness in the language used. Avoid overly technical jargon where plain language will suffice, making the policy accessible to all employees, regardless of their technical background.
For both print and digital versions, consider the layout and formatting. Use clear headings, subheadings, bullet points, and short paragraphs to break up large blocks of text, enhancing readability. A professional, consistent branding (e.g., company logo, colors) can also make the document feel more official and integrated with other workplace rules and HR policies. If distributing digitally, ensure the document is easily searchable and accessible on your internal network or knowledge base, perhaps with a clear table of contents for quick navigation.
Implementation is where the policy truly comes to life. It’s not enough to simply publish the document; active communication and training are paramount. Conduct regular training sessions to educate employees on the policy’s requirements, their individual responsibilities, and the consequences of non-compliance. Reinforce key messages through internal communications, posters, and regular security awareness campaigns. Establish a clear feedback mechanism where employees can ask questions or report concerns, fostering an open environment for security discussions.
Finally, remember that an information security policy is a living document. It requires continuous review and updates to remain relevant and effective. Establish a formal review process, ideally annually or whenever there are significant changes to your organization’s risk profile, technology, or legal obligations. Implement robust version control to track changes and ensure everyone is always working with the most current iteration of your Iso 27001 Information Security Policy Template-derived document.
In an era defined by persistent cyber threats and evolving regulatory demands, a robust information security framework is no longer optional—it’s imperative. Leveraging an Iso 27001 Information Security Policy Template offers a strategic advantage, providing a solid, expert-vetted foundation upon which to build your organization’s entire information security management system. It’s more than just a document; it’s a statement of your commitment to protecting valuable data, maintaining trust, and ensuring business resilience.
By carefully customizing and diligently implementing the principles outlined in an Iso 27001 Information Security Policy Template, organizations can confidently navigate the complexities of data security. It empowers them to not only achieve compliance with international standards but also to cultivate a proactive security culture that safeguards information assets against a diverse array of modern threats. Consider it an investment in your organization’s future, providing clarity, structure, and peace of mind in an increasingly digital world.