In today’s hyper-connected world, where data breaches make headlines daily and regulatory compliance is no longer optional, securing information assets has become a paramount concern for organizations of all sizes. The digital landscape is rife with sophisticated threats, making a robust information security posture not just a best practice, but a fundamental business imperative. This is precisely where a well-structured and comprehensive information security policy comes into play, serving as the bedrock upon which an organization’s entire security framework is built.
For many, crafting such a policy from scratch can feel like an overwhelming task, akin to navigating a complex maze without a map. This is where an Iso 27002 Information Security Policy Template offers a strategic advantage. It provides a meticulously designed blueprint, leveraging globally recognized standards to help organizations establish, implement, maintain, and continually improve their information security management system (ISMS). Whether you’re a startup grappling with your first data protection regulations, an established enterprise seeking to enhance your compliance efforts, or a team aiming for ISO 27001 certification, understanding and utilizing an Iso 27002 Information Security Policy Template can be a game-changer.
Why an Iso 27002 Information Security Policy Template is Essential
The importance of a robust information security policy cannot be overstated in our current technological climate. Cyber threats are constantly evolving, ranging from phishing and ransomware to sophisticated state-sponsored attacks. Beyond the direct financial impact of a breach, organizations face significant reputational damage, loss of customer trust, and potential legal repercussions. Regulatory requirements, such as GDPR, CCPA, HIPAA, and various industry-specific mandates, place strict obligations on how organizations handle sensitive data, making effective data security a matter of legal compliance.
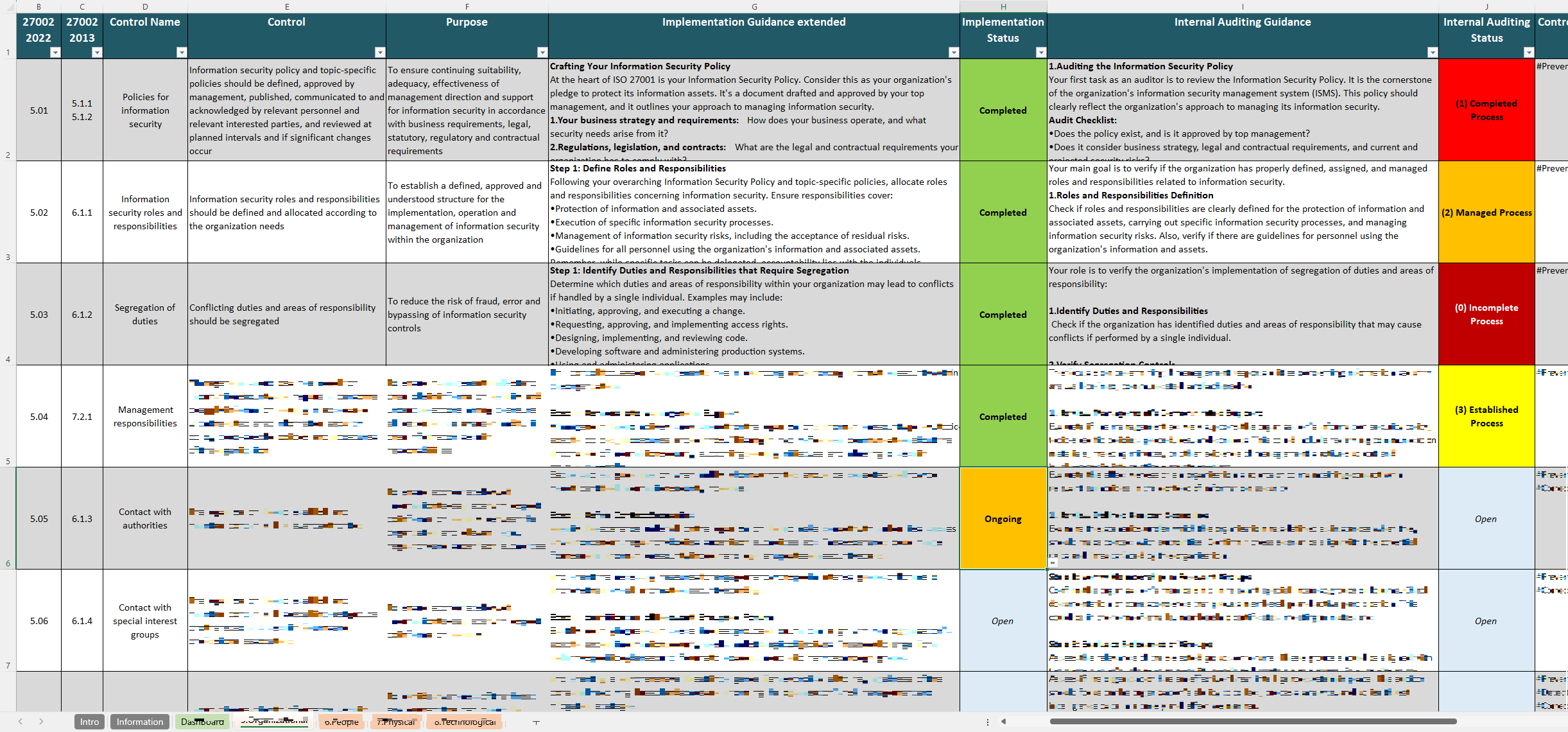
An Iso 27002 Information Security Policy Template addresses these challenges head-on by providing a structured, internationally recognized framework. ISO 27002 offers a comprehensive set of guidelines and best practices for information security controls, covering everything from access management and cryptography to incident response and physical security. By adopting an Iso 27002 Information Security Policy Template, organizations gain access to a proven methodology for identifying, assessing, and mitigating information security risks. It’s not just about protecting data; it’s about safeguarding business continuity, intellectual property, and stakeholder confidence, establishing clear workplace rules and employee obligations concerning information handling.
Key Benefits of Using an Iso 27002 Information Security Policy Template
Leveraging an Iso 27002 Information Security Policy Template offers a multitude of benefits that extend far beyond simply meeting a compliance checklist. Firstly, it provides a powerful foundation for a systematic approach to information security. Instead of ad-hoc measures, organizations can develop a cohesive and integrated security program that covers all critical aspects of their operations. This structured approach helps in identifying gaps and ensuring that all bases are covered, from HR policies related to new hires to technical controls for network access.
Secondly, an Iso 27002 Information Security Policy Template significantly streamlines the policy development process. Rather than starting from scratch, security teams can customize an existing, expert-vetted framework, saving valuable time and resources. This efficiency allows organizations to deploy essential security policies more quickly, thereby reducing their exposure to risks sooner. Moreover, it ensures consistency across different policies and departments, fostering a unified security culture. Such templates are designed to incorporate best practices, guiding organizations toward a higher standard of data security and management.
Finally, an Iso 27002 Information Security Policy Template enhances an organization’s ability to achieve and maintain compliance with various regulatory frameworks and industry standards. It offers a clear path towards ISO 27001 certification, which is often a requirement for doing business with certain partners or in specific sectors. Beyond certification, it demonstrates a commitment to robust security practices to customers, partners, and regulators, building trust and strengthening business relationships. These benefits contribute directly to improved risk management and overall organizational resilience against evolving cyber threats.
How an Iso 27002 Information Security Policy Template Can Be Customized or Adapted
While an Iso 27002 Information Security Policy Template provides an excellent starting point, it’s crucial to understand that it is a framework, not a one-size-fits-all solution. Every organization has unique operational requirements, risk appetites, industry-specific challenges, and cultural nuances. Therefore, effective implementation hinges on the ability to tailor the template to fit these distinct needs. The beauty of a well-designed template lies in its flexibility, allowing it to be adapted to various contexts, whether for a small startup or a large multinational corporation.
Customization typically involves several steps. Initially, organizations must conduct a thorough risk assessment to identify their specific information assets, potential threats, and vulnerabilities. This assessment will directly inform which controls from ISO 27002 are most relevant and how they need to be implemented. For instance, a healthcare provider will have different privacy considerations than a manufacturing company, necessitating specific clauses for protected health information (PHI) that might not be as prominent in other sectors. Similarly, a cloud-native company will focus more heavily on virtual infrastructure security compared to an organization with significant on-premise hardware.
Furthermore, the language and tone of the policy should resonate with the organization’s culture and employee base. Policies should be clear, concise, and easy for all employees to understand, not just technical staff. This might involve simplifying complex legal terms or technical jargon, or providing additional guidance and training materials. By adapting the Iso 27002 Information Security Policy Template to reflect the organization’s unique operational realities and strategic objectives, it transforms from a generic document into a living, actionable set of guidelines that genuinely supports the organization’s information security goals and employee obligations.
Important Elements to Include in an Iso 27002 Information Security Policy Template
A comprehensive Iso 27002 Information Security Policy Template should be structured to cover the various domains of information security as outlined by ISO 27002. While the exact wording and level of detail will vary based on customization, certain key elements are universally critical for a complete and effective policy. These elements ensure that all aspects of an organization’s information security management system are addressed, from strategic oversight to day-to-day operational controls.
Here are the important elements or fields that should typically be included:
- Policy Statement and Scope: Clearly articulate the organization’s commitment to information security, define the purpose of the policy, and precisely delineate the information assets, systems, and personnel that fall under its purview. This also sets the context for compliance requirements.
- Roles and Responsibilities: Define who is accountable for information security at various levels, from the board of directors and senior management to individual employees, specifying their duties and obligations. This ensures clear lines of authority and accountability.
- Risk Management Framework: Outline the organization’s approach to identifying, assessing, treating, monitoring, and reviewing information security risks, ensuring a systematic and continuous improvement process.
- Asset Management: Policies for inventorying information assets, classifying them based on sensitivity and criticality, and assigning ownership for their protection.
- Human Resources Security: Address security considerations throughout the employee lifecycle, including pre-employment screening, security awareness training, disciplinary processes for policy violations, and termination procedures.
- Access Control: Define rules for granting, reviewing, and revoking access to information systems and data based on the principle of least privilege and segregation of duties.
- Cryptography: Policies regarding the use of encryption and cryptographic controls to protect the confidentiality, integrity, and authenticity of information, both in transit and at rest.
- Physical and Environmental Security: Controls for protecting physical facilities and equipment from unauthorized access, damage, and interference, including aspects like secure areas, entry controls, and equipment maintenance.
- Operations Security: Guidelines for secure operating procedures, malware protection, backup and recovery, logging and monitoring, and management of technical vulnerabilities.
- Communications Security: Policies related to network security management, information transfer, electronic messaging, and other forms of communication to protect information integrity and confidentiality.
- Supplier Relationships: Controls for managing information security risks associated with third-party suppliers, vendors, and partners, including contractual agreements and service level requirements.
- Information Security Incident Management: Procedures for detecting, reporting, assessing, responding to, and learning from information security incidents and breaches, ensuring a swift and effective response.
- Information Security Aspects of Business Continuity Management: Policies to ensure the resilience of information security during disruptive events, including recovery objectives and plans.
- Compliance: Detail the organization’s commitment to complying with relevant statutory, regulatory, and contractual obligations, as well as internal security policies. This section often references specific acts or standards.
- Policy Review and Update Schedule: Specify how often the policy will be reviewed and updated to remain relevant and effective in response to changing threats and organizational needs.
Tips on Design, Usability, and Implementation
Creating a comprehensive Iso 27002 Information Security Policy Template is only half the battle; ensuring it’s usable, understood, and effectively implemented is equally vital. A poorly designed or communicated policy, no matter how technically sound, will fail to achieve its objectives. Therefore, focusing on design, usability, and a robust implementation strategy is crucial for success.
When it comes to design, clarity and conciseness are paramount. Avoid overly technical jargon where possible, or provide clear explanations for complex terms. Use headings, subheadings, bullet points, and short paragraphs to break up text and improve readability. A visually appealing layout, whether for a printed copy or a digital document, can significantly enhance engagement. Consider creating an executive summary for quick reference by senior management, highlighting the key objectives and organizational commitment. For digital formats, ensure the policy is easily searchable and accessible through an intranet or document management system, allowing employees to quickly find relevant sections, much like navigating an online knowledge base.
Usability also extends to how the policy integrates into daily workflows. Instead of presenting it as a standalone, intimidating tome, break it down into digestible modules. For instance, specific policies related to "clean desk" or "password management" can be communicated separately, perhaps through short training videos or easily printable guides. Regular employee awareness training is essential, not just once a year, but through ongoing campaigns that reinforce key principles. This helps to embed security practices into the organizational culture, fostering a collective sense of responsibility for data security.
Implementation requires a strategic approach. Start with a clear communication plan, explaining the "why" behind the policies – not just the "what." Secure buy-in from leadership, as their visible support is critical. Designate clear policy owners and provide them with the resources needed to enforce the policies effectively. Integrate policy requirements into existing processes, such as HR onboarding for new employees or IT change management procedures. Finally, establish mechanisms for monitoring policy adherence and gather feedback from employees. This iterative process allows for continuous improvement, ensuring that the Iso 27002 Information Security Policy Template remains a living document that truly protects the organization’s valuable information assets.
Ultimately, an Iso 27002 Information Security Policy Template is more than just a document; it’s a strategic investment in your organization’s future. It provides the necessary structure to navigate the complexities of information security, transforming a daunting task into a manageable and systematic process. By leveraging its inherent best practices, organizations can not only fortify their defenses against an ever-growing array of cyber threats but also instill a culture of security awareness and responsibility across all levels.
Embracing an Iso 27002 Information Security Policy Template empowers your business to achieve robust compliance, enhance trust with stakeholders, and protect its most critical assets. It’s a proactive step towards building organizational resilience and ensuring business continuity in an increasingly digital world. Don’t let the challenge of information security paralyze your efforts; instead, harness the power of a proven framework to build a secure and sustainable future for your enterprise.