In today’s hyper-connected digital landscape, IT systems are the beating heart of nearly every organization. From daily operations to strategic initiatives, their seamless functioning is non-negotiable. Yet, despite our best efforts, incidents—those unexpected disruptions ranging from minor glitches to full-blown cyberattacks—are an unavoidable reality. When these events strike, the difference between a minor inconvenience and a catastrophic business disruption often hinges on one critical factor: a well-defined and rigorously followed incident management strategy.
This is precisely where an It Incident Management Policy Template becomes an invaluable asset. Far more than just a document, it’s a strategic blueprint designed to empower your organization to respond swiftly, effectively, and consistently when the unexpected happens. For IT managers, security teams, compliance officers, and even executive leadership, having a robust framework in place isn’t just good practice—it’s a fundamental requirement for maintaining operational resilience, safeguarding data security, and protecting your brand’s reputation.
Why an It Incident Management Policy Template is Essential
The digital realm is a dynamic and often hostile environment. Organizations face a relentless barrage of threats, from sophisticated ransomware attacks and phishing campaigns to accidental data breaches and infrastructure failures. Without a clear, documented approach, responding to these incidents can devolve into chaos, leading to extended downtime, significant financial losses, reputational damage, and potential regulatory penalties. An It Incident Management Policy Template acts as your organization’s first line of defense, transforming a potentially reactive scramble into a structured, proactive response.
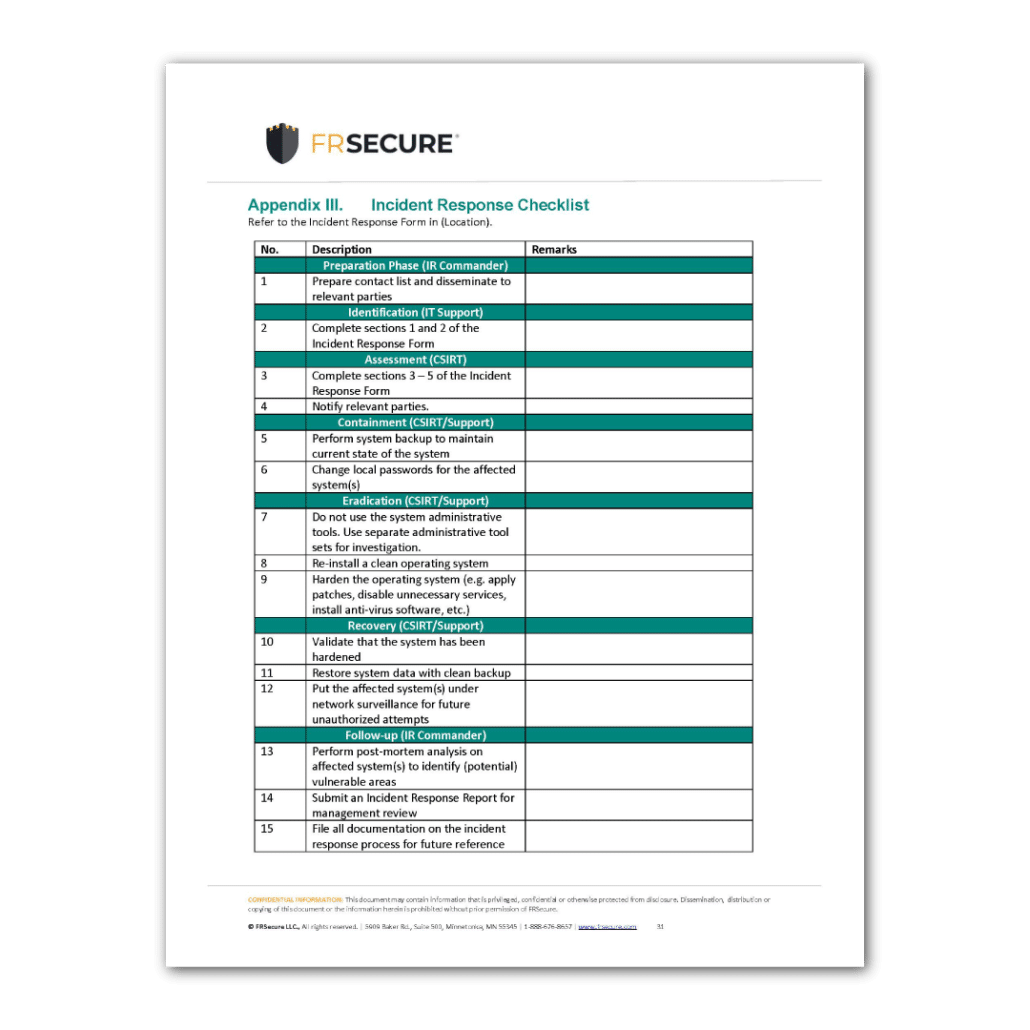
Beyond merely reacting, a robust policy ensures that your organization can meet its obligations for business continuity and data security. It lays the groundwork for compliance with an ever-expanding array of regulations such as HIPAA, GDPR, CCPA, and various industry-specific standards. By clearly outlining roles, responsibilities, and procedures, an effective It Incident Management Policy Template minimizes the impact of incidents, accelerates recovery, and helps your team learn valuable lessons to prevent future occurrences. It’s not just about fixing what’s broken; it’s about building a more resilient and secure operational environment.
Key Benefits of Using an It Incident Management Policy Template
Implementing and regularly updating an It Incident Management Policy Template offers a multitude of tangible benefits that extend across the entire organization. These advantages contribute significantly to operational efficiency, risk mitigation, and overall business stability.
Firstly, it provides standardization and consistency in how all incidents are handled. This ensures that every member of the incident response team understands their role and the steps to take, regardless of the incident’s nature or the time it occurs. Such consistency reduces errors, improves efficiency, and fosters a unified approach.
Secondly, a well-structured policy leads to faster response and resolution times. With predefined processes for detection, classification, escalation, and resolution, teams can bypass guesswork and move directly to problem-solving. This rapid response directly translates to reduced downtime, minimizing financial losses and limiting the exposure of sensitive data.
Thirdly, it significantly improves communication, both internally and externally. The template outlines who needs to be informed, when, and how, preventing miscommunication and ensuring stakeholders, customers, and regulatory bodies receive timely and accurate updates. Clear communication during a crisis is paramount for maintaining trust and managing expectations.
Fourthly, a strong It Incident Management Policy Template enhances compliance and regulatory adherence. By documenting your procedures, you provide clear evidence of your commitment to data security and privacy regulations, which can be crucial during audits or in the aftermath of a breach. It demonstrates due diligence and helps avoid costly fines and legal repercussions.
Finally, it facilitates better post-incident analysis and prevention. Every incident, regardless of its severity, offers a learning opportunity. The policy encourages thorough post-mortems, identifying root causes, evaluating the effectiveness of the response, and implementing preventative measures. This continuous improvement cycle strengthens your security posture and overall IT governance, making your organization more resilient against future threats and operational challenges.
Customizing Your It Incident Management Policy Template
While an It Incident Management Policy Template provides an excellent foundational structure, it’s crucial to understand that one size rarely fits all. Every organization possesses unique characteristics—from its size and industry to its technological stack, risk appetite, and the specific regulatory landscape it navigates. Therefore, adapting the template to fit your specific needs is not just recommended, it’s essential for its effectiveness.
Consider the nature of your IT infrastructure. An organization heavily reliant on cloud services, for example, will require different incident types, response procedures, and communication protocols than one primarily operating on-premise systems. Your customization should reflect these realities, detailing specific procedures for incidents affecting cloud platforms, SaaS applications, or hybrid environments. The escalation paths must also be tailored to your organizational hierarchy and team structure, ensuring that the right people are notified at the right time.
Furthermore, your industry dictates specific compliance requirements. A healthcare provider will need to embed HIPAA-specific data breach notification procedures directly into their policy, while a financial institution will adhere to different sets of regulations. The It Incident Management Policy Template should be a living document that aligns with your unique data security obligations, your existing workplace rules, and your broader IT governance framework, making it a practical and enforceable guide for your teams. Don’t be afraid to add sections, modify language, or integrate specific tools and technologies that are integral to your operations.
Important Elements for Your It Incident Management Policy Template
A comprehensive and actionable It Incident Management Policy Template should incorporate several key elements to ensure all facets of incident response are adequately addressed. These components provide a clear roadmap for your team, from the moment an incident is detected until its full resolution and subsequent analysis.
- **Purpose and Scope:** Clearly state the policy’s objective (e.g., minimize impact, ensure business continuity) and the systems, data, and personnel it covers.
- **Definitions:** Provide clear, unambiguous definitions for key terms like “incident,” “major incident,” “security event,” “data breach,” “root cause,” and “service level agreement (SLA).”
- **Roles and Responsibilities:** Outline the specific duties of individuals and teams involved in incident management, including the incident commander, responders, communication lead, and executive stakeholders.
- **Incident Classification and Prioritization:** Establish criteria for categorizing incidents (e.g., low, medium, high, critical) based on their impact, severity, and urgency, along with guidelines for assigning priority.
- **Detection and Reporting Procedures:** Detail the mechanisms for identifying incidents (e.g., monitoring tools, user reports) and the precise steps for employees to report them, including contact information and required initial information.
- **Response and Containment Steps:** Provide step-by-step instructions for initial response actions, including isolation of affected systems, data preservation, and immediate mitigation strategies to prevent further damage.
- **Eradication and Recovery:** Outline procedures for eliminating the root cause of the incident, restoring affected systems and data from backups, and validating system functionality after recovery.
- **Post-Incident Review (Lessons Learned):** Mandate a formal process for reviewing significant incidents to identify what went well, what could be improved, and how to prevent similar incidents in the future. This includes documentation and action item assignments.
- **Communication Plan:** Specify who needs to be informed (internal teams, management, customers, legal, PR, regulatory bodies), the channels to use, and the content of communications at different stages of an incident.
- **Training and Awareness:** Require regular training for all relevant personnel on incident management procedures, security best practices, and their roles within the policy.
- **Policy Review and Update Schedule:** Establish a regular cadence for reviewing and updating the It Incident Management Policy Template to ensure it remains current with evolving threats, technologies, and organizational changes.
- **References to Other Policies:** Link to related documents such as the Data Security Policy, Business Continuity Plan, Disaster Recovery Plan, and Acceptable Use Policy to ensure a cohesive IT governance framework.
- **Emergency Contact Information:** Include a readily accessible list of key personnel, vendors, and external support contacts.
Tips for Design, Usability, and Implementation
An It Incident Management Policy Template is only as effective as its ability to be easily understood, accessed, and acted upon during a crisis. Therefore, careful consideration of its design, usability, and implementation is paramount.
When it comes to design, prioritize clarity and conciseness. Use simple, direct language, avoiding jargon where possible. Employ a logical structure with clear headings, subheadings, bullet points, and numbered lists to break up text and improve readability. White space is your friend—it makes the document less intimidating and easier to scan. Consider using flowcharts or diagrams for complex processes like escalation paths, as visual aids can be processed much faster than dense text, especially under pressure.
For usability, ensure the policy is easily accessible to everyone who needs it, both in print and digital formats. While a digital version (e.g., on an intranet or shared drive) offers searchability and easy updates, having printed copies in key locations is vital in scenarios where network access is compromised. Implement robust version control to prevent confusion, clearly indicating the last update date and version number. Make sure the document is integrated with your existing IT Service Management (ITSM) tools or ticketing systems, so team members can seamlessly reference policy guidelines as they work through incidents.
Implementation extends beyond just publishing the document. It requires active engagement. Conduct regular training sessions for all relevant staff to familiarize them with the policy and their roles. Even better, run tabletop exercises or full-scale incident simulations to test the policy’s effectiveness in a real-world context. These drills help identify weaknesses, refine procedures, and build muscle memory within your team. Remember to treat the It Incident Management Policy Template as a living document; actively solicit feedback from responders after incidents, regularly review its content against emerging threats and technologies, and update it as needed to maintain its relevance and efficacy.
Navigating the complexities of IT incidents demands more than just technical expertise; it requires a strategic, unified approach. A well-crafted It Incident Management Policy Template serves as the cornerstone of this approach, providing the structure, clarity, and consistency needed to transform potential chaos into controlled, effective response. It empowers your teams, protects your assets, and reinforces your commitment to operational excellence.
By investing the time and resources into developing and refining a robust It Incident Management Policy Template, organizations are not merely preparing for the inevitable; they are actively building a more resilient, secure, and trustworthy digital environment. This proactive measure ensures that when the unexpected strikes, your organization is not just ready to react, but poised to recover swiftly, learn effectively, and emerge stronger than before.


