In today’s interconnected digital landscape, cloud computing has become the backbone of modern enterprise operations, powering everything from email and data storage to complex applications and artificial intelligence. This widespread adoption, while offering unparalleled flexibility and efficiency, simultaneously introduces a myriad of security challenges that organizations must meticulously address. Navigating this intricate environment demands a robust and well-defined strategy, and that’s precisely where the Nist Cloud Security Policy Template steps in as an indispensable resource.
This template isn’t just a document; it’s a strategic framework designed to help organizations build a strong foundation for their cloud security posture. It provides a structured approach to identifying, assessing, and mitigating risks associated with cloud services, ensuring compliance with various regulatory frameworks and best practices. Whether you’re a small startup leveraging SaaS solutions or a large enterprise managing a complex multi-cloud infrastructure, the Nist Cloud Security Policy Template offers the guidance needed to establish clear security guidelines, define responsibilities, and protect sensitive information in the cloud.
Why Nist Cloud Security Policy Template is Essential Today
The rapid evolution of cloud services and the increasing sophistication of cyber threats make a clear, comprehensive security policy more critical than ever. Organizations are facing an ever-growing array of compliance obligations, including HIPAA, GDPR, CCPA, and industry-specific mandates like CMMC. Without a structured approach, meeting these requirements and effectively managing cloud risks can feel overwhelming. The Nist Cloud Security Policy Template offers a universally recognized standard, providing a systematic methodology to address cloud-specific vulnerabilities and establish a proactive security stance.
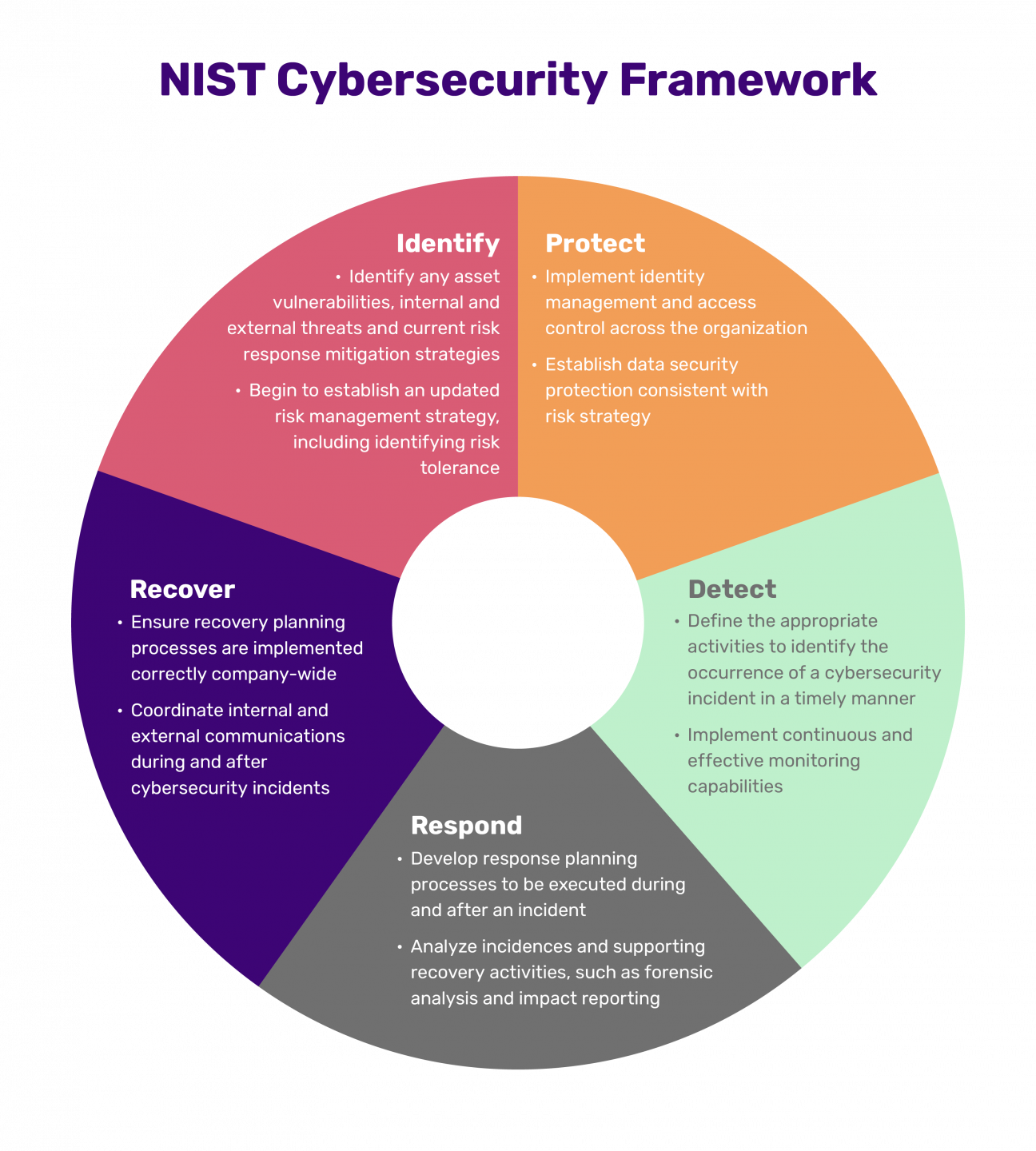
Moreover, the shared responsibility model inherent in cloud computing often creates ambiguity regarding who is responsible for what. A well-articulated Nist Cloud Security Policy Template clarifies these boundaries, both internally and with cloud service providers (CSPs), ensuring that no critical security area is overlooked. It helps organizations transition from reactive incident response to proactive risk management, embedding security into every layer of their cloud operations. This foundational template is not merely about preventing breaches; it’s about building resilience and ensuring business continuity in an era where data is paramount.
Key Benefits of Using Nist Cloud Security Policy Template
Leveraging a structured framework like the Nist Cloud Security Policy Template offers numerous strategic and operational advantages for any organization embracing cloud technology. Firstly, it provides a standardized and comprehensive approach to cloud security, significantly reducing the guesswork involved in developing effective policies from scratch. This consistency ensures all critical aspects of cloud security are considered, from data governance to access control.
Secondly, the template is instrumental in achieving and demonstrating regulatory compliance. By aligning with NIST’s robust guidelines, organizations can systematically address requirements from various compliance frameworks, streamlining audit processes and minimizing the risk of penalties. Thirdly, it fosters better risk management by providing a clear methodology for identifying, assessing, and mitigating cloud-specific threats and vulnerabilities. This proactive stance helps protect sensitive data and critical business functions.
Furthermore, a clearly defined Nist Cloud Security Policy Template promotes clarity and accountability within an organization. It delineates roles, responsibilities, and procedures for employees and stakeholders, ensuring everyone understands their part in maintaining cloud security. This consistency enhances operational efficiency and reduces internal friction. Lastly, by bolstering your security posture, the Nist Cloud Security Policy Template helps protect your brand reputation and build trust with customers, partners, and stakeholders, assuring them that their data is handled with the utmost care and professionalism.
How Nist Cloud Security Policy Template Can Be Customized or Adapted to Different Needs
While the Nist Cloud Security Policy Template provides a robust foundation, its true power lies in its adaptability. It is explicitly designed not as a rigid mandate, but as a flexible framework that organizations must tailor to their unique operational context, risk appetite, and regulatory landscape. The first step in customization involves understanding your specific cloud architecture—whether you’re utilizing public, private, hybrid, or multi-cloud environments, and the specific services (IaaS, PaaS, SaaS) involved. Each configuration presents distinct security considerations.
Organizations must then integrate their specific industry regulations and compliance mandates into the Nist Cloud Security Policy Template. For instance, a healthcare provider will need to embed HIPAA requirements, while a financial institution will focus on PCI DSS or GLBA. This customization ensures that the policy template addresses all relevant legal and ethical obligations. Additionally, the size and complexity of your organization, along with its existing IT governance frameworks and security controls, will dictate how the template is adapted. Smaller businesses might streamline certain sections, while larger enterprises with sophisticated security teams will expand upon them.
Finally, the template should reflect your organization’s unique risk profile and tolerance. A high-risk environment might require more stringent controls and frequent audits, whereas a lower-risk profile might allow for some flexibility. The Nist Cloud Security Policy Template serves as an excellent starting point, enabling teams to build upon a recognized standard while ensuring the final policy is a perfect fit for their operational realities and strategic objectives.
Important Elements or Fields That Should Be Included in Nist Cloud Security Policy Template
A comprehensive Nist Cloud Security Policy Template must encompass a wide array of critical elements to ensure all facets of cloud security are addressed effectively. These elements form the backbone of a resilient cloud security program.
- Policy Scope and Purpose: Clearly defines what the policy covers, which cloud services it applies to, and its overarching objectives, such as protecting data and maintaining compliance.
- Roles and Responsibilities: Outlines who is accountable for various security tasks, from executive leadership and C-level officers to IT security teams, cloud administrators, and end-users.
- Cloud Service Provider (CSP) Due Diligence: Specifies processes for evaluating and selecting CSPs, including security assessments, contract reviews, and ongoing vendor management.
- Data Classification and Handling: Establishes guidelines for classifying data based on sensitivity and outlines specific controls for storage, processing, and transmission of data in the cloud (confidentiality, integrity, availability).
- Access Control and Identity Management: Details policies for user authentication, authorization, multi-factor authentication (MFA), least privilege principles, and identity governance across cloud environments.
- Network Security: Covers requirements for network segmentation, firewalls, intrusion detection/prevention systems (IDS/IPS), virtual private networks (VPNs), and secure connectivity to cloud resources.
- Vulnerability Management and Patching: Defines procedures for identifying, assessing, and remediating vulnerabilities in cloud infrastructure, applications, and virtual machines, including regular scanning and patch management.
- Incident Response and Disaster Recovery: Outlines the steps for detecting, responding to, and recovering from security incidents or service outages in the cloud, including communication plans and backup/restoration strategies.
- Logging and Monitoring: Specifies requirements for collecting, retaining, and analyzing security logs and events from cloud services to detect suspicious activity and ensure accountability.
- Compliance and Audit Requirements: Details the specific regulatory, legal, and industry standards the organization must adhere to, and how the cloud environment will be audited for compliance.
- Security Awareness Training: Mandates regular security training for all employees on cloud security best practices, recognizing threats, and adherence to policy.
- Data Encryption: Establishes requirements for encrypting data at rest (storage) and in transit (network communication) within cloud environments using approved cryptographic standards.
- Secure Configuration Management: Defines baselines and processes for securely configuring cloud services, operating systems, and applications, preventing misconfigurations.
- Supply Chain Risk Management: Addresses risks introduced by third-party cloud applications, services, and associated vendors, ensuring their security practices align with organizational standards.
Tips on Design, Usability, or Implementation
Effectively implementing the Nist Cloud Security Policy Template goes beyond merely filling in the blanks; it involves designing a policy that is not only robust but also practical and usable across the organization. For usability, strive for clarity and conciseness in language. Avoid overly technical jargon where plain language will suffice, ensuring that all employees, regardless of their technical background, can understand and adhere to the guidelines. Breaking down complex sections into digestible paragraphs and using bullet points, as demonstrated, can significantly improve readability.
When it comes to design, consider both digital and potential print formats. Digitally, host the Nist Cloud Security Policy Template on an easily accessible internal platform, such as an intranet portal or a dedicated Governance, Risk, and Compliance (GRC) tool. Utilize clear headings, a consistent layout, and searchable text to make navigation intuitive. If a print version is necessary for specific scenarios or compliance needs, ensure it’s well-formatted with clear page numbering and an index for quick reference.
For implementation, establishing a regular review cycle is paramount. Cloud technologies evolve rapidly, and your Nist Cloud Security Policy Template must adapt accordingly. Schedule annual or bi-annual reviews, or trigger reviews based on significant changes in cloud usage, regulatory landscape, or security incidents. Crucially, active communication and training are vital. Simply publishing the policy is not enough; integrate it into new employee onboarding and ongoing security awareness training programs. Ensure employees understand not just what the policy states, but why it matters to them and the organization, fostering a culture of security from the ground up.
In an era where digital transformation is synonymous with business growth, securing cloud environments is no longer optional—it’s foundational. The Nist Cloud Security Policy Template stands as an invaluable resource, offering a structured, recognized, and adaptable framework to navigate the complexities of cloud security. By leveraging this template, organizations can move beyond ad-hoc security measures to establish a comprehensive, resilient, and compliant cloud security posture.
Embracing the Nist Cloud Security Policy Template means investing in your organization’s future, safeguarding critical assets, and building stakeholder trust. It provides the clarity, consistency, and strategic direction needed to confidently leverage cloud innovation while effectively mitigating pervasive cyber risks. Don’t just migrate to the cloud; secure it proactively with a robust policy developed using this essential framework, ensuring your digital journey is both efficient and secure.