In today’s hyper-connected and rapidly evolving digital landscape, organizations face an unprecedented array of challenges, from sophisticated cyber threats to increasingly stringent regulatory demands. Maintaining the integrity, security, and operational efficiency of IT systems is no longer just a technical task; it’s a strategic imperative. Without a structured approach to managing IT assets and their configurations, businesses risk everything from costly downtime and data breaches to severe compliance penalties. This is where the methodical discipline of configuration management steps in, providing the necessary framework to bring order to complex IT environments.
For many, the sheer scale of modern IT infrastructure can make the task of establishing robust controls seem daunting. This is precisely why a well-articulated and comprehensively designed Nist Configuration Management Policy Template becomes an invaluable asset. It serves as a foundational blueprint, guiding organizations—from burgeoning startups to established enterprises—in developing, implementing, and maintaining a consistent and secure configuration posture across their entire technology stack. Whether you’re an IT manager striving for operational excellence, a security professional aiming to bolster defenses, or a compliance officer navigating a maze of regulations, understanding and utilizing such a template is a critical step towards achieving digital resilience and peace of mind.
Why Nist Configuration Management Policy Template is Essential
The digital world is in a constant state of flux, with systems being updated, patched, and reconfigured daily. Without a formalized approach, these changes can introduce vulnerabilities, cause system instability, and make it nearly impossible to maintain a clear security posture. A Nist Configuration Management Policy Template addresses these challenges head-on by providing a structured methodology rooted in the globally recognized National Institute of Standards and Technology (NIST) framework. This framework is a gold standard for cybersecurity best practices, making any policy derived from it inherently robust and credible.
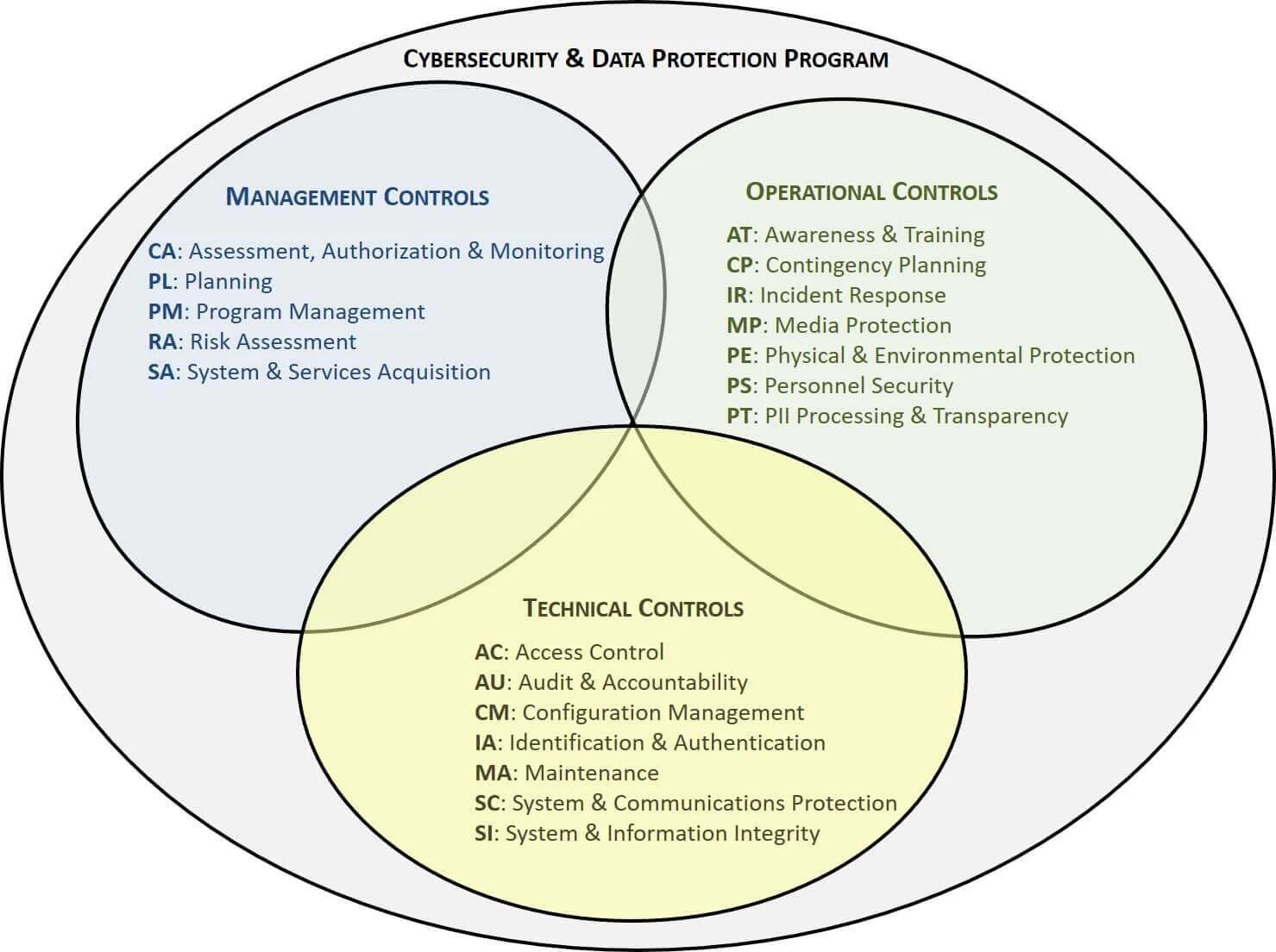
Implementing a policy based on the Nist Configuration Management Policy Template ensures that all changes to systems, software, and hardware are controlled, documented, and reviewed, significantly reducing the risk of unauthorized modifications or configuration drift. This proactive approach is vital for data security, minimizing exposure to common attack vectors that exploit misconfigurations. Furthermore, in an era of heightened regulatory scrutiny—ranging from HIPAA and GDPR to CMMC and PCI DSS—a robust configuration management policy becomes a cornerstone of compliance. It provides auditors with clear evidence of due diligence and control over critical IT assets, simplifying audits and demonstrating a commitment to governance and risk management. Without such a template guiding your efforts, organizations often find themselves reacting to incidents rather than preventing them, leading to higher operational costs and significant reputational damage.
Key Benefits of Using Nist Configuration Management Policy Template
Leveraging a Nist Configuration Management Policy Template offers a multitude of tangible benefits that extend across an organization’s operational, security, and compliance landscapes. Firstly, it dramatically enhances an organization’s security posture. By standardizing configurations and establishing baselines, the policy helps to eliminate common vulnerabilities arising from unmanaged or insecure settings, providing a consistent defense against cyber threats. This foundational security approach reduces the attack surface and fortifies critical systems against intrusion.
Secondly, it streamlines the complex processes of auditing and compliance. With a clear, documented policy outlining how configurations are managed, monitored, and approved, organizations can easily demonstrate adherence to various industry standards and regulatory requirements. This not only reduces the burden of compliance, but also minimizes the risk of costly fines and legal repercussions associated with non-compliance. A Nist Configuration Management Policy Template provides the systematic record-keeping and procedural clarity that auditors demand, showcasing a mature approach to IT governance.
Moreover, the template contributes to improved operational efficiency and system reliability. By controlling changes and ensuring consistency, it minimizes configuration-related incidents, reducing system downtime and the need for costly troubleshooting. This leads to higher availability of critical services, better performance, and a more predictable IT environment. Clear accountability, a direct result of a well-defined policy, also ensures that roles and responsibilities for configuration management are understood, fostering a culture of ownership and meticulousness within the IT team. Ultimately, by adopting a Nist Configuration Management Policy Template, organizations are investing in a more secure, stable, and cost-effective IT infrastructure.
Customizing Nist Configuration Management Policy Template
While the Nist Configuration Management Policy Template provides a powerful and comprehensive framework, it’s crucial to recognize that it’s not a one-size-fits-all solution. Every organization has unique needs, varying in size, industry, technological footprint, and risk appetite. Therefore, effectively customizing the template is essential to ensure it accurately reflects your specific operational environment and strategic objectives. The beauty of a template lies in its adaptability; it offers a solid starting point that can be tailored rather than forcing you to build from scratch.
Customization might involve adjusting the scope to encompass only specific departments or critical systems, or expanding it to include unique industry-specific software and hardware configurations. For example, a healthcare provider might need to heavily emphasize controls around patient data systems (PHI), while a manufacturing company might focus more on industrial control systems (ICS). Organizations should review their existing IT policies, governance structures, and current change management processes to identify areas where the Nist Configuration Management Policy Template needs to be harmonized or extended. This includes defining specific tools and technologies used for configuration management, such as CMDBs (Configuration Management Databases) or automated configuration tools, and integrating them into the policy’s procedural guidelines. By thoughtfully adapting the Nist Configuration Management Policy Template, organizations can create a policy that is not only compliant with NIST standards but also practically implementable and highly effective within their unique context.
Important Elements of Nist Configuration Management Policy Template
A comprehensive Nist Configuration Management Policy Template should detail various critical components to ensure thorough control and management of an organization’s IT assets. These elements form the backbone of a robust policy, ensuring that all aspects of configuration are addressed, from initial setup to ongoing maintenance and auditing.
Here are the key elements that should be included:
- Policy Statement and Scope: Clearly define the purpose of the policy, its objectives, and the systems, assets, and personnel it covers. This sets the stage for the entire document and clarifies its applicability.
- Roles and Responsibilities: Outline specific roles (e.g., Configuration Manager, System Owners, Change Approvers) and their associated responsibilities in the configuration management process, ensuring clear accountability.
- Configuration Identification and Baselines: Establish how configuration items (CIs) are identified, categorized, and documented. Define the process for creating and maintaining secure baseline configurations for all systems and applications.
- Configuration Change Control Process: Detail the entire lifecycle of a configuration change, including request, review, approval, testing, deployment, verification, and rollback procedures. This is critical for preventing unauthorized or harmful changes.
- Configuration Monitoring and Auditing: Describe how configurations are regularly monitored for deviations from baselines and how audits are conducted to ensure ongoing compliance with the policy.
- Configuration Documentation: Specify requirements for documenting all aspects of configuration management, including baseline configurations, change records, and system specifications.
- Software and Hardware Configuration Management: Provide specific guidelines for managing both software (e.g., operating systems, applications, patches) and hardware (e.g., servers, network devices) configurations.
- Security Baselines and Hardening: Emphasize the creation and enforcement of security-specific configuration baselines, aligned with industry best practices and organizational security requirements.
- Tools and Technologies: Identify the specific tools, automated solutions, and systems (e.g., CMDBs, version control systems) used to support configuration management activities.
- Training and Awareness: Outline the need for regular training to ensure that all relevant personnel understand the policy, their roles, and the configuration management processes.
- Compliance and Reporting: Detail how compliance with the policy is measured and reported, including metrics and reporting frequencies for management and auditors.
- Policy Review and Update Cycle: Establish a schedule and process for regularly reviewing and updating the Nist Configuration Management Policy Template to ensure it remains relevant and effective in a changing technological and threat landscape.
Tips for Design, Usability, and Implementation
Crafting a robust Nist Configuration Management Policy Template is only half the battle; ensuring it’s usable, accessible, and effectively implemented is equally vital. When designing the policy document, prioritize clarity and conciseness. Use plain language, avoiding overly technical jargon where possible, or provide glossaries for specialized terms. Structure the document with logical headings and subheadings, utilizing bullet points and tables to break up dense text and improve readability. For digital versions, ensure it’s searchable and navigable with a clear table of contents and internal links.
For usability, consider your audience. The policy should be easy for IT professionals to reference during their daily tasks, and for managers to understand their oversight responsibilities. Provide practical examples or scenarios to illustrate key procedures, making the abstract principles more concrete. Furthermore, ensure the policy is readily accessible; whether it’s stored on a company intranet, a shared drive, or an internal documentation portal, it should be easy for authorized personnel to find and retrieve the latest version. Implement strong version control practices to prevent confusion over outdated policies.
Implementation is where the policy truly comes to life. Begin with a clear communication plan to inform all stakeholders about the new or updated Nist Configuration Management Policy Template. Provide mandatory training sessions to ensure that everyone understands their roles and the established processes, especially the change control procedures. Integrate the policy with existing IT service management (ITSM) tools, such as change management systems, incident management platforms, and your CMDB, to automate and streamline compliance. Consider a phased rollout, starting with a pilot program on non-critical systems before extending it enterprise-wide. Regular reviews and feedback mechanisms are essential for continuous improvement, allowing the policy to evolve alongside your organization’s technology and threat landscape.
The policy should also be designed with both print and digital considerations in mind. While digital access is paramount for ease of use and updates, a well-formatted print version might be useful for training materials or as a physical reference for specific teams. Ensure consistent branding and formatting across all mediums.
Embracing a Proactive Approach to IT Governance
Implementing a well-defined Nist Configuration Management Policy Template is more than just an administrative task; it’s a strategic investment in your organization’s security, stability, and future resilience. It shifts the paradigm from reactive problem-solving to proactive prevention, establishing a bedrock of control and consistency across your entire IT ecosystem. By aligning with NIST’s acclaimed cybersecurity framework, you are not merely ticking compliance boxes but actively building a more defensible and reliable operational environment capable of withstanding the complexities of the modern digital age.
As organizations continue to expand their digital footprints and grapple with an increasingly sophisticated threat landscape, the value of a robust configuration management policy cannot be overstated. It empowers IT teams, reassures stakeholders, and provides a clear pathway to achieving and maintaining optimal system integrity and data security. Therefore, consider adopting and tailoring a Nist Configuration Management Policy Template as a foundational element of your IT governance strategy—it’s a practical, actionable solution that will pay dividends in enhanced security, streamlined operations, and enduring peace of mind.