In today’s interconnected digital world, the question isn’t if an organization will face a cyber threat, but when. From sophisticated ransomware attacks to subtle phishing attempts, the landscape of cyber risks is constantly evolving, posing significant challenges to businesses of all sizes. Navigating this complexity requires more than just advanced technology; it demands a robust, well-defined strategy, and that’s precisely where a comprehensive Nist Cyber Security Policy Template becomes an invaluable asset. It’s not merely a document; it’s the blueprint for an organization’s digital resilience, a strategic framework designed to protect vital information and ensure business continuity.
A Nist Cyber Security Policy Template serves as a foundational guide for establishing, implementing, and maintaining an effective cybersecurity program. It’s particularly beneficial for US organizations looking to align with widely recognized security standards, enhance their compliance posture, and systematically mitigate risks. Whether you’re a small business striving to protect customer data, a mid-sized enterprise grappling with supply chain security, or a large corporation navigating stringent regulatory frameworks, leveraging a Nist Cyber Security Policy Template offers a structured approach to building a formidable defense against an ever-present array of cyber threats.
Why a Nist Cyber Security Policy Template is Essential Today
The digital age has brought unprecedented opportunities, but it has also ushered in an era of heightened cyber threats. Data breaches are no longer isolated incidents; they are daily occurrences that can cripple businesses, erode customer trust, and incur devastating financial penalties. In this environment, relying on ad-hoc security measures is akin to building a house without a foundation. A Nist Cyber Security Policy Template provides that essential foundation, grounding an organization’s security efforts in proven principles.
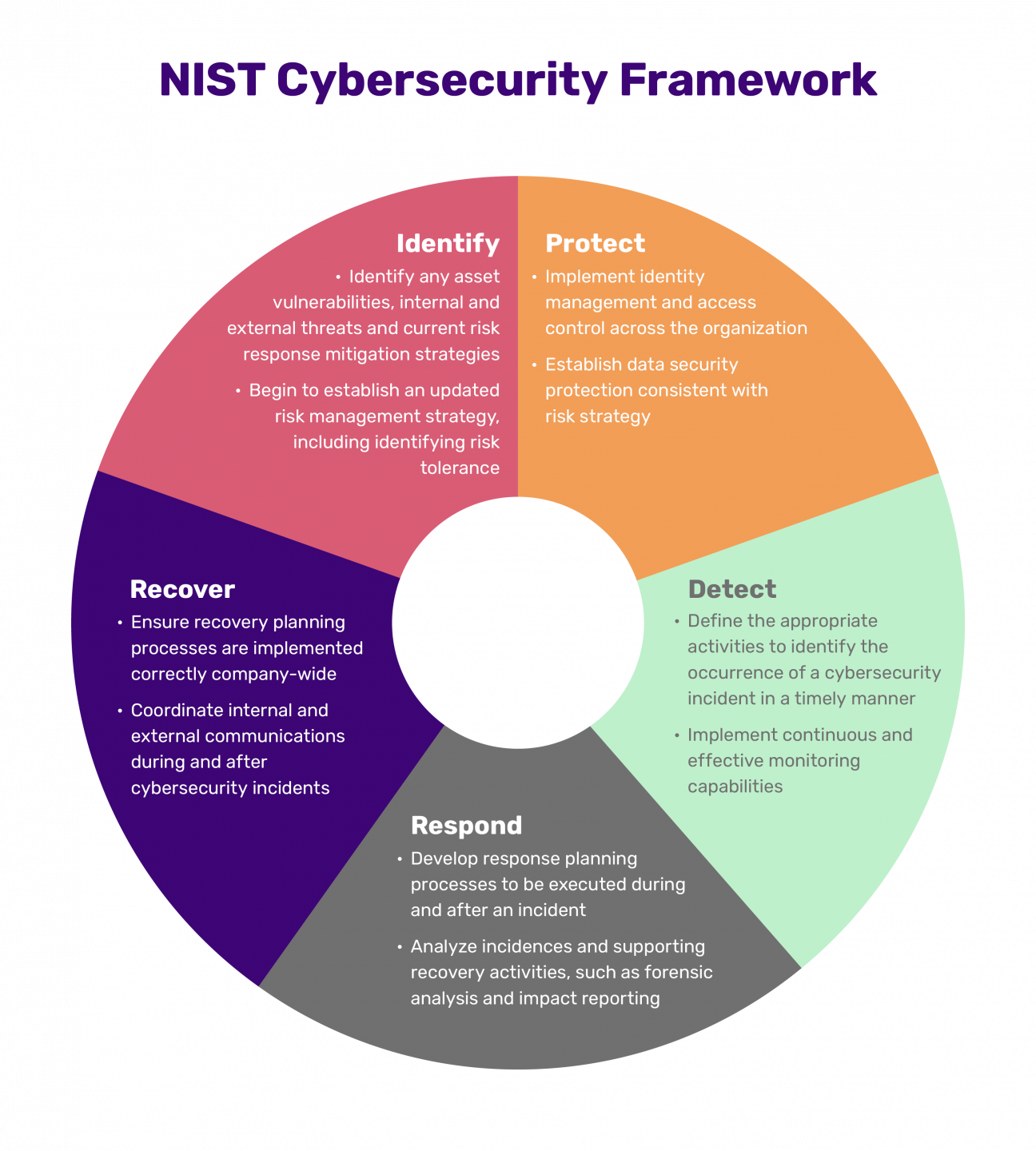
The National Institute of Standards and Technology (NIST) is renowned for its comprehensive guidelines and frameworks, such as the NIST Cybersecurity Framework (CSF) and various Special Publications (SP 800 series). These resources are widely adopted because they offer a flexible, risk-based approach to managing cybersecurity. A Nist Cyber Security Policy Template, built upon these authoritative guidelines, helps organizations translate complex security standards into actionable, clear workplace rules and operational procedures. It ensures that security isn’t just an IT concern but a fundamental part of the organizational culture, addressing everything from data security and incident response to employee conduct and third-party vendor management.
Furthermore, the regulatory landscape is becoming increasingly demanding. Compliance mandates like HIPAA, GDPR, CCPA, and CMMC require organizations to demonstrate a commitment to protecting sensitive information. While a Nist Cyber Security Policy Template is not a magic bullet for instant compliance, it provides a structured pathway to meet these obligations. By systematically addressing control families and security domains outlined in NIST guidelines, organizations can build defensible policies that satisfy auditor requirements and prove due diligence, significantly reducing legal and financial exposure in the event of a security incident.
Key Benefits of Using a Nist Cyber Security Policy Template
Adopting a Nist Cyber Security Policy Template offers a myriad of benefits that extend far beyond simply checking a box for compliance. It represents a proactive investment in an organization’s future, enhancing resilience and fostering a culture of security. One of the primary advantages is the establishment of a standardized, consistent approach to information security across the entire enterprise. This consistency eliminates ambiguity, ensuring that all employees, from the executive suite to the front lines, understand their roles and responsibilities in maintaining a secure environment.
Beyond standardization, a well-crafted Nist Cyber Security Policy Template significantly improves an organization’s overall risk posture. By systematically identifying potential vulnerabilities and prescribing controls, it acts as a robust mechanism for risk management. This proactive stance helps prevent security breaches before they occur, protecting critical assets, intellectual property, and sensitive customer data. It also streamlines the audit process; when policies are clearly documented and aligned with recognized frameworks, demonstrating adherence to security standards becomes much more efficient and less burdensome.
Moreover, the implementation of a Nist Cyber Security Policy Template fosters greater operational efficiency. Clear policies reduce guesswork, simplify decision-making during security incidents, and ensure a coordinated response. This translates into less downtime, quicker recovery times, and ultimately, a more reliable service delivery for customers. For human resources departments, these policies provide essential guidelines for employee behavior, acceptable use of IT resources, and consequences for non-compliance, creating a more secure and accountable workplace. In essence, it transforms cybersecurity from a reactive chore into a strategic advantage, building trust with stakeholders and safeguarding the organization’s reputation.
Customizing and Adapting Your Nist Cyber Security Policy Template
While a Nist Cyber Security Policy Template provides an excellent starting point, it’s crucial to understand that it’s not a one-size-fits-all solution. Every organization possesses unique characteristics, including its size, industry sector, specific operational processes, regulatory obligations, and risk tolerance. Therefore, effective implementation necessitates thoughtful customization and adaptation to ensure the policies genuinely reflect the organization’s specific context and needs.
The process of tailoring a Nist Cyber Security Policy Template involves a thorough assessment of your current environment. This includes identifying your most critical assets, understanding your specific threat landscape, and evaluating your existing security controls. For instance, a healthcare provider will have different data security and privacy requirements (driven by HIPAA) than a manufacturing company, and their Nist Cyber Security Policy Template must reflect those distinct legal terms and operational realities. Small businesses might opt for a more streamlined set of policies initially, focusing on fundamental controls, while larger enterprises will require more granular and extensive documentation to cover a broader range of systems and departments.
Adaptation also means making the language accessible and relevant to your workforce. While the underlying technical principles are important, the policies themselves should be clear, concise, and understandable to non-technical staff. Consider how your organization operates day-to-day. Do you have a large remote workforce? Then your Nist Cyber Security Policy Template needs robust sections on remote access, secure endpoint configuration, and teleworking guidelines. Do you rely heavily on cloud services? Then cloud security and vendor risk management policies will be paramount. By treating the Nist Cyber Security Policy Template as a living document, subject to regular review and adjustment, organizations can ensure it remains effective and aligned with their evolving operational realities and compliance requirements.
Important Elements to Include in Your Nist Cyber Security Policy Template
A robust Nist Cyber Security Policy Template should encompass a wide array of critical areas to provide comprehensive guidance and establish clear expectations. These elements form the backbone of your cybersecurity program, addressing various facets of information security. While the exact components may vary based on an organization’s specific needs, here are some key elements or fields that should generally be included:
- Information Security Program Policy: An overarching statement outlining the organization’s commitment to information security, its objectives, scope, and the roles and responsibilities for its implementation.
- Acceptable Use Policy (AUP): Defines appropriate and inappropriate use of organizational IT resources, including networks, systems, software, and data, by employees, contractors, and other users.
- Access Control Policy: Details how access to systems, applications, and data is granted, managed, reviewed, and revoked. This includes principles like least privilege and segregation of duties.
- Data Classification and Handling Policy: Establishes guidelines for classifying information based on its sensitivity (e.g., public, internal, confidential) and specifies appropriate handling, storage, and transmission procedures for each classification.
- Incident Response Policy: Outlines the procedures for detecting, reporting, analyzing, containing, eradicating, and recovering from cybersecurity incidents, including roles, responsibilities, and communication protocols.
- Business Continuity and Disaster Recovery Policy: Addresses how the organization will maintain critical business functions and recover IT systems and data in the event of disruptive events.
- Security Awareness Training Policy: Mandates regular security awareness training for all personnel, covering topics like phishing, malware, password hygiene, and social engineering, emphasizing the importance of human firewalls.
- Vendor Risk Management Policy: Defines the process for assessing, managing, and monitoring the cybersecurity risks posed by third-party vendors, suppliers, and business partners.
- Physical Security Policy: Covers the protection of physical assets, data centers, and IT infrastructure from unauthorized access, theft, or damage.
- Patch Management Policy: Establishes procedures for identifying, evaluating, testing, and applying security patches and updates to all systems and applications in a timely manner.
- Remote Work/Telework Policy: Provides guidelines for secure remote access, endpoint security, data protection, and communication for employees working outside the traditional office environment.
- Cryptographic Controls Policy: Specifies when and how encryption should be used to protect sensitive data at rest and in transit.
- Audit and Accountability Policy: Mandates the logging and monitoring of system events, user activities, and security-related actions for auditing, investigation, and compliance purposes.
- System Configuration and Hardening Policy: Provides standards for securely configuring operating systems, applications, and network devices to minimize vulnerabilities.
- Privacy Policy: Outlines how the organization collects, uses, stores, and protects personal identifiable information (PII) in accordance with relevant privacy regulations.
These elements, when thoughtfully developed and integrated into a comprehensive Nist Cyber Security Policy Template, provide a clear roadmap for effective cybersecurity governance and operations.
Tips for Design, Usability, and Implementation
Creating a robust Nist Cyber Security Policy Template is only half the battle; ensuring its usability, clear communication, and effective implementation is equally vital. A policy, no matter how comprehensive, is useless if it’s not understood, accessible, or followed. Therefore, focus on design and usability aspects for both digital and, if necessary, print formats.
First and foremost, aim for clarity and conciseness in your language. Avoid overly technical jargon where plain language will suffice, making the policies accessible to everyone, not just IT professionals. Use short paragraphs and bullet points, as seen in the important elements section, to break up text and improve readability. For digital versions, ensure the Nist Cyber Security Policy Template is easily searchable and hyperlinked for quick navigation between related sections. Consider a dedicated section on your internal intranet where all current policies are hosted, ensuring employees always have access to the most up-to-date versions.
Effective implementation hinges on communication and training. Once your Nist Cyber Security Policy Template is finalized and approved, conduct mandatory security awareness training for all employees to educate them on the policies and their individual responsibilities. This training should be ongoing and refreshed regularly, especially as policies are updated. Integrate these cybersecurity policies with broader HR policies and onboarding processes, so new hires understand their obligations from day one. Establish a clear process for reporting policy violations and for employees to ask questions or seek clarification.
Finally, remember that a Nist Cyber Security Policy Template is a living document. Establish a regular review cycle (e.g., annually or bi-annually) to update policies in response to new threats, technological changes, evolving regulatory requirements, or organizational shifts. Version control is crucial here, ensuring that old policies are archived and new ones are clearly dated and communicated. By prioritizing usability, fostering a culture of understanding, and committing to continuous improvement, your organization can truly leverage the power of its Nist Cyber Security Policy Template to build a resilient and secure environment.
In a world where cyber threats are a constant, an organization’s ability to protect its digital assets is paramount to its success and longevity. Leveraging a comprehensive Nist Cyber Security Policy Template isn’t merely about ticking compliance boxes; it’s about embedding a proactive, strategic approach to security into the very fabric of your operations. It provides the clarity, structure, and foundational principles necessary to navigate the complex digital landscape with confidence.
By adopting, customizing, and diligently implementing a Nist Cyber Security Policy Template, organizations are not just reacting to threats but building an enduring framework for resilience. It equips employees with the knowledge they need, clarifies obligations for all stakeholders, and serves as a testament to an organization’s commitment to safeguarding data and maintaining trust. Consider it an indispensable investment—a practical solution that fortifies your defenses and ensures your digital journey is as secure as possible.


