In today’s hyper-connected world, where digital transformation drives business forward, the specter of cyber threats looms larger than ever. From sophisticated ransomware attacks crippling essential services to data breaches compromising sensitive customer information, the headlines are a constant reminder of the vulnerabilities lurking in our digital infrastructure. For any organization operating in this landscape, a robust defense is not merely an IT concern; it’s a fundamental business imperative. This is where the Nist Network Security Policy Template emerges as a critical resource, providing a structured, authoritative framework for building resilience.
Navigating the complexities of cybersecurity can feel overwhelming, especially for businesses without dedicated security teams. The Nist Network Security Policy Template offers a beacon of clarity, distilling decades of expert knowledge from the National Institute of Standards and Technology (NIST) into actionable guidelines. It’s a foundational tool designed to help organizations of all sizes establish, implement, and maintain comprehensive information security policies. Whether you’re a burgeoning startup, a mid-sized enterprise, or a large government agency, this template provides a vital starting point for protecting your digital assets, ensuring operational continuity, and meeting critical compliance obligations.
Why the Nist Network Security Policy Template is Essential Today
The modern digital ecosystem is characterized by an ever-evolving threat landscape. Cybercriminals are increasingly sophisticated, leveraging advanced techniques to exploit vulnerabilities in networks, applications, and human behavior. This constant barrage of threats, coupled with the rising volume and sensitivity of data organizations handle, makes a proactive and well-defined security strategy non-negotiable. The Nist Network Security Policy Template addresses this urgent need by offering a comprehensive roadmap for securing your digital perimeter.
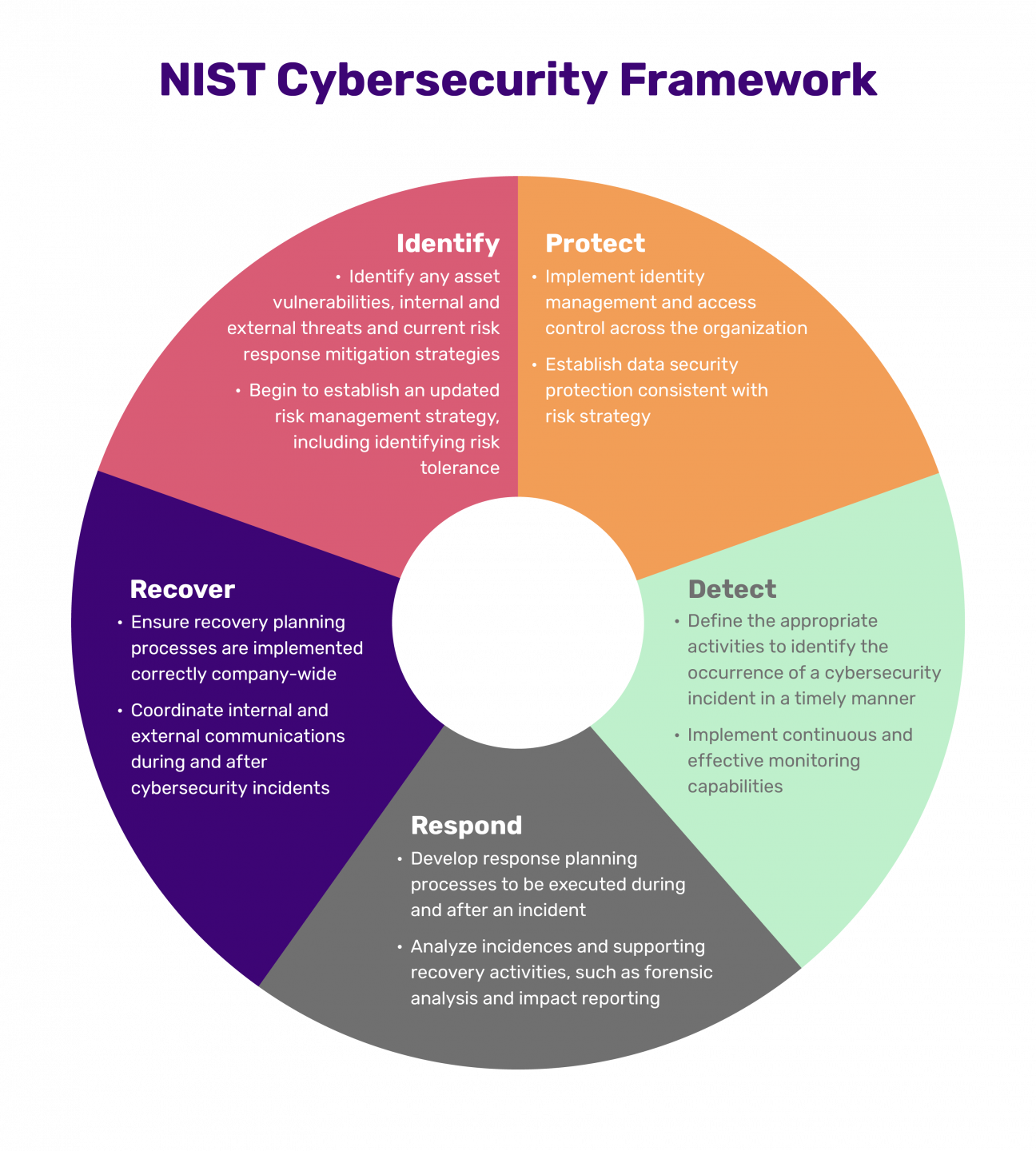
Beyond the immediate threat of cyberattacks, regulatory pressures are intensifying. Laws like HIPAA, GDPR, CCPA, and various industry-specific mandates (e.g., PCI DSS for credit card data) impose strict requirements on how organizations protect data and manage their networks. Non-compliance can lead to hefty fines, reputational damage, and a loss of customer trust. By aligning with the principles outlined in the Nist Network Security Policy Template, organizations can systematically address these regulatory requirements, demonstrating due diligence and a commitment to data security. It transforms what could be a chaotic, reactive response into a structured, defensible cybersecurity posture.
Key Benefits of Using the Nist Network Security Policy Template
Leveraging a Nist Network Security Policy Template offers a multitude of strategic and operational advantages for any organization committed to safeguarding its digital assets. It moves security from an ad-hoc activity to a structured, governable process, delivering tangible benefits across the board.
Firstly, it provides an authoritative and comprehensive framework. NIST is a globally recognized authority in cybersecurity. By utilizing their template, organizations gain access to best practices developed through extensive research and industry collaboration. This significantly reduces the time and resources required to develop policies from scratch, allowing teams to focus on implementation rather than initial policy creation.
Secondly, the Nist Network Security Policy Template enhances compliance and reduces risk. Its guidelines are often foundational to numerous regulatory frameworks. By adopting these policies, organizations can systematically address common requirements for data security, incident response, access control, and audit logging. This proactive approach not only helps avoid costly penalties but also significantly mitigates the financial and reputational damage associated with data breaches or operational disruptions.
Moreover, it fosters consistency and clarity within an organization. A well-defined policy ensures that all employees understand their roles and responsibilities regarding network security. It sets clear workplace rules, defining acceptable use policies for systems and data, thereby reducing the likelihood of insider threats or accidental misconfigurations. This uniformity in security practices strengthens the overall security posture and simplifies security awareness training programs.
Finally, implementing a Nist Network Security Policy Template improves incident response capabilities. By having predefined protocols for identifying, containing, eradicating, and recovering from security incidents, organizations can respond more swiftly and effectively. This structured approach minimizes downtime, limits data loss, and ensures a more resilient operation, ultimately protecting the organization’s bottom line and its valuable reputation.
How the Nist Network Security Policy Template Can Be Customized or Adapted
While the Nist Network Security Policy Template provides an exceptionally robust foundation, it’s crucial to understand that it is not a one-size-fits-all solution. Its true power lies in its adaptability and the ability for organizations to customize it to their specific operational context, industry vertical, and risk profile. Think of it as a comprehensive blueprint that needs tailoring to construct the perfect building for your unique needs.
For smaller businesses, the sheer volume of a full Nist Network Security Policy Template might seem overwhelming. In such cases, the template can be adapted by focusing on the most critical controls relevant to their operations and scaling back on less pertinent sections. Conversely, large enterprises or those in highly regulated sectors (like finance or defense) might need to expand certain areas, adding more granular detail, specific technological requirements, or integrating complex contractual obligations with third-party vendors. The flexibility of the Nist framework allows for this necessary scaling, ensuring the policies are proportionate to the level of risk and resources.
Customization also involves integrating the Nist Network Security Policy Template with an organization’s existing security tools and infrastructure. This might include specifying configurations for firewalls, intrusion detection systems, endpoint protection, and cloud security controls. Industry-specific requirements, such as HIPAA for healthcare or GDPR for international data handling, will necessitate adding specific clauses or clarifying how the Nist guidelines meet these particular regulatory requirements. Regular reviews and updates are also a form of adaptation, ensuring the policy remains relevant as technology evolves and business needs change, solidifying it as a living document within your organization’s broader information security policies.
Important Elements or Fields That Should Be Included in the Nist Network Security Policy Template
A truly effective Nist Network Security Policy Template is comprehensive, covering a broad spectrum of security domains. While the exact sections may vary slightly based on the specific NIST publication referenced (e.g., NIST SP 800-53 or NIST CSF), a robust template should generally include the following critical elements:
- Policy Statement and Scope: Clearly defines the purpose, applicability, and overarching goals of the network security policy. It should outline what the policy covers (e.g., all network assets, data, and users) and the organization’s commitment to security.
- Roles and Responsibilities: Delineates who is accountable for what aspects of network security, including IT staff, management, and general employees. This clarifies the chain of command for security operations and incident response.
- Access Control Policies: Details how access to network resources is granted, managed, and revoked. This includes user authentication (e.g., strong passwords, multi-factor authentication), authorization principles (least privilege), and control over remote access.
- Network Segmentation and Architecture: Specifies guidelines for dividing the network into segments (VLANs, subnets) to limit the lateral movement of threats and protect critical assets. It also covers secure network design principles.
- Wireless Network Security: Outlines standards for securing Wi-Fi networks, including encryption protocols (e.g., WPA3), authentication methods, and rogue access point detection.
- Data Encryption Standards: Defines requirements for encrypting data at rest and in transit, specifying approved cryptographic algorithms and key management practices to protect sensitive information.
- Incident Response Plan Integration: References or directly includes procedures for detecting, analyzing, containing, eradicating, and recovering from network security incidents. This is crucial for minimizing damage and downtime.
- Vulnerability Management and Patching: Mandates regular scanning for vulnerabilities, assessment of risks, and timely application of security patches to operating systems, applications, and network devices.
- Acceptable Use Policy (AUP): Informs users about permissible and prohibited activities on the organizational network and IT resources. This is key for establishing workplace rules around technology use.
- Remote Access and Virtual Private Network (VPN) Policies: Establishes secure guidelines for employees accessing the corporate network from outside the physical perimeter, including VPN configuration and user responsibilities.
- Vendor and Third-Party Security: Addresses security requirements for third-party access to the network, cloud service providers, and supply chain security to manage external risks.
- Security Awareness Training: Emphasizes the importance of ongoing training for all personnel to educate them about security best practices, phishing threats, and their role in upholding information security policies.
- Audit and Logging Requirements: Specifies what network events should be logged, how long logs should be retained, and how they should be reviewed to aid in monitoring, forensics, and compliance.
- Physical Security Considerations: While primarily a network policy, it should touch upon physical security measures for network infrastructure (e.g., server rooms, wiring closets) to prevent unauthorized access.
- Policy Review and Update Schedule: Defines the frequency and process for reviewing and updating the Nist Network Security Policy Template to ensure its continued relevance and effectiveness against evolving threats and technologies.
Tips on Design, Usability, or Implementation
Creating a robust Nist Network Security Policy Template is one thing; making it effective in practice is another. The design, usability, and implementation strategy are paramount to ensuring your policies are not just documents but living, actionable guidelines that truly protect your organization.
First and foremost, clarity and simplicity are key. While the underlying technical concepts can be complex, the policy language should be as clear and concise as possible. Avoid excessive jargon where plain language will suffice. Short, focused paragraphs and bullet points, as seen in this article, can significantly enhance readability and comprehension, ensuring that employees across all departments can understand and adhere to the guidelines.
For usability, consider how your Nist Network Security Policy Template will be accessed. Digital accessibility is crucial. Host the policy on an internal intranet, a dedicated security portal, or a shared document management system where it is easily searchable and always up-to-date. Ensure robust version control is in place, so everyone knows they are referencing the current approved document. If printed copies are necessary for certain scenarios, ensure they are clearly labeled with version numbers and revision dates.
Implementation requires a multi-faceted approach. Start with strong leadership buy-in; without executive support, policy adoption will struggle. Integrate the Nist Network Security Policy Template into your employee onboarding process, making it a mandatory read. Follow up with regular, engaging security awareness training sessions that explain the "why" behind the policies, not just the "what." Use real-world examples to illustrate the importance of compliance and the potential consequences of negligence.
Finally, remember that information security policies are not static. Schedule regular reviews and updates—at least annually, or whenever significant changes occur in technology, regulatory requirements, or organizational structure. Solicit feedback from employees and IT staff, as their practical insights can reveal areas where the policy is unclear or impractical. Integrating these policies with your HR department for enforcement of workplace rules and considering legal review for complex obligations or contractual agreements will also bolster their efficacy.
A well-designed and implemented policy is an accessible and understandable resource that empowers employees to be part of the solution, rather than an obscure document gathering digital dust.
The Nist Network Security Policy Template stands as an indispensable resource in the continuous battle for cybersecurity resilience. It transcends being merely a compliance checklist; it’s a strategic framework that empowers organizations to build robust defenses, manage risk proactively, and foster a security-conscious culture. By providing a structured, authoritative, and adaptable approach to information security policies, NIST offers a pathway for businesses to confidently navigate the treacherous digital landscape.
Embracing the Nist Network Security Policy Template isn’t just about protecting your networks; it’s about protecting your entire operation, your reputation, and your customers’ trust. In an era where a single breach can have catastrophic consequences, leveraging such a well-regarded template is a proactive and prudent investment. It transforms complex cybersecurity challenges into manageable, actionable steps, ensuring that your organization is not just reactive to threats, but fundamentally resilient against them, ready to face the future with enhanced digital security.


