In the complex landscape of project development, where ideas transform into tangible solutions, the initial spark of an concept can quickly get lost in translation. Misunderstandings between stakeholders, development teams, […]
BC Heathers Society
Christmas Party Event Program Template
The holiday season brings a unique blend of excitement and, let’s be honest, a touch of organizational challenge. From bustling office celebrations to intimate family gatherings, Christmas parties are a […]
Quality Policy Template Iso 9001
In today’s dynamic business landscape, where customer expectations are higher than ever and global competition is fierce, the commitment to quality isn’t just a buzzword – it’s a fundamental pillar […]
Return To Work Policy Template Nsw
Navigating an employee’s return to work after an injury or illness can be a complex and sensitive process for any organization. It’s a journey that requires careful planning, empathy, and […]
Catholic Wedding Without Mass Program Template
For many couples, a Catholic wedding holds deep spiritual significance, a sacred covenant witnessed by God and their loved ones. However, not every Catholic wedding ceremony includes a full Nuptial […]
Workflow Requirements Document Template
In the complex landscape of modern business, where projects often span multiple departments, involve numerous stakeholders, and rely on intricate sequences of tasks, clarity is not just a preference—it’s a […]
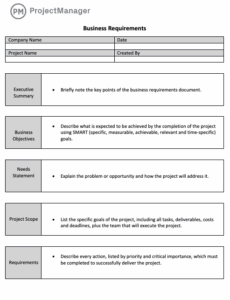
Best Business Requirements Document Template
In the fast-paced world of project management and software development, clarity is not just a virtue—it’s a necessity. Ambiguous goals, misunderstood features, and shifting requirements are the silent killers of […]
Agile High Level Requirements Template
In the fast-paced world of Agile development, maintaining a clear vision while adapting to change can feel like walking a tightrope. Teams strive for iterative progress, but without a foundational […]
Quality Assurance Policy Template Free
In today’s hyper-competitive business landscape, where customer expectations are higher than ever and regulatory scrutiny is constant, establishing a robust framework for consistent quality isn’t just a good idea—it’s absolutely […]
Recruitment And Selection Policy Template
In today’s dynamic labor market, attracting and retaining top talent is more critical than ever for business success. Companies are constantly competing for skilled professionals, and the process of bringing […]