In today’s interconnected digital landscape, organizations face an ever-growing barrage of cyber threats. Protecting sensitive data and critical systems is no longer just an IT concern; it’s a fundamental business imperative. This is where a robust Security Assessment And Authorization Policy Template becomes an invaluable asset, serving as the cornerstone for a proactive and resilient cybersecurity posture. It’s more than just a document; it’s a strategic framework that guides how an organization identifies, assesses, and formally accepts the risks associated with its information systems.
Navigating the complexities of information security, regulatory compliance, and risk management requires a structured approach. Without a clear policy, security efforts can become fragmented, inconsistent, and ultimately, ineffective. A well-crafted Security Assessment And Authorization Policy Template provides the necessary roadmap, ensuring that security controls are consistently evaluated, and that leadership formally acknowledges and authorizes the operational use of systems based on their assessed risk. This framework benefits not only security and IT professionals but also risk managers, compliance officers, and executive leadership seeking clarity and accountability in their cyber defense strategies.
Why a Security Assessment And Authorization Policy Template Is Essential
The modern threat landscape is characterized by its relentless evolution and increasing sophistication. From ransomware attacks that cripple operations to insidious data breaches that erode public trust, the stakes have never been higher. A Security Assessment And Authorization Policy Template is absolutely critical in this environment because it establishes a standardized, repeatable process for managing security risks across an organization’s entire IT infrastructure.
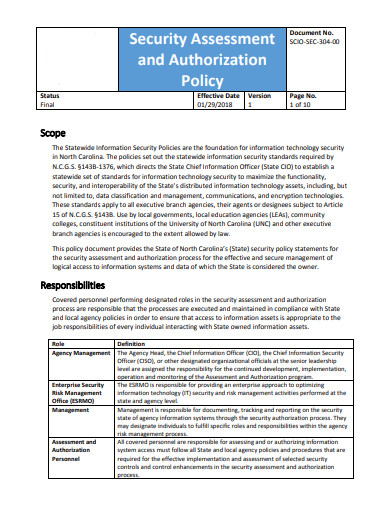
This template helps organizations move beyond reactive security measures to a proactive, risk-informed approach. It ensures that before any system, application, or service goes live or undergoes significant changes, its security posture is thoroughly evaluated against established standards and potential threats. By formalizing this process, the Security Assessment And Authorization Policy Template acts as a crucial governance tool, aligning security activities with broader business objectives and regulatory requirements, such as those imposed by HIPAA, PCI DSS, or NIST frameworks. It clarifies who is responsible for what, preventing oversight and promoting a culture of accountability in data protection and system integrity.
Key Benefits of Using a Security Assessment And Authorization Policy Template
Implementing a comprehensive Security Assessment And Authorization Policy Template offers a multitude of benefits that extend far beyond mere compliance. It fundamentally transforms an organization’s approach to security, turning potential weaknesses into managed risks.
One primary advantage is the establishment of a consistent and repeatable security process. This ensures that every new system or significant change undergoes the same rigorous assessment, reducing the likelihood of critical vulnerabilities slipping through the cracks. It brings clarity to the often-complex world of cybersecurity, defining clear roles and responsibilities for all stakeholders involved in the assessment and authorization lifecycle.
Furthermore, a robust Security Assessment And Authorization Policy Template significantly reduces organizational risk. By systematically identifying and evaluating potential threats and vulnerabilities before systems are deployed, organizations can implement appropriate security controls, thereby mitigating exposure to cyberattacks and data breaches. This proactive stance not only protects assets but also safeguards the organization’s reputation and financial stability.
The policy also greatly enhances audit readiness and regulatory compliance. With a documented process for security assessments and formal authorizations, organizations can easily demonstrate to auditors and regulators that they have a structured framework in place for managing information security risks. This can streamline audit processes and help avoid costly penalties associated with non-compliance. Ultimately, it fosters a more secure and resilient operational environment, enabling confident decision-making regarding the deployment and management of IT assets.
How the Security Assessment And Authorization Policy Template Can Be Customized
While the core principles of security assessment and authorization remain universal, the specific application of a Security Assessment And Authorization Policy Template must be flexible enough to adapt to diverse organizational needs, industry regulations, and technological landscapes. This is not a one-size-fits-all document; its strength lies in its adaptability.
Organizations of varying sizes will naturally require different levels of detail and formality. A small startup might adopt a streamlined version focusing on essential controls and a simpler approval process, whereas a large enterprise operating in a highly regulated industry will need a more expansive policy, incorporating specific industry standards, advanced assessment methodologies, and multi-layered authorization workflows. The Security Assessment And Authorization Policy Template can be tailored to address unique industry requirements, such as those found in healthcare (HIPAA), finance (GLBA), or government (FISMA), by integrating relevant compliance mandates directly into the assessment criteria and authorization prerequisites.
Moreover, the template should be adaptable to different types of systems and technologies. Whether it’s a cloud-based application, an on-premise server, or an IoT device, the policy can be customized to define appropriate assessment scopes, security control baselines, and authorization thresholds for each. This ensures that the policy remains a living document that can evolve with the organization’s technology stack and strategic goals, serving as a dynamic framework that continuously supports its unique cybersecurity journey.
Important Elements for a Security Assessment And Authorization Policy Template
A truly effective Security Assessment And Authorization Policy Template must be comprehensive, addressing all critical phases and components necessary for robust risk management. While customization is key, certain foundational elements should always be present to ensure clarity, accountability, and thoroughness.
Here are the important elements or fields that should be included:
- Policy Statement and Purpose: Clearly define the policy’s objective, scope, and the organization’s commitment to security assessment and authorization.
- Scope: Specify which information systems, applications, and services fall under this policy, including boundaries and exclusions.
- Roles and Responsibilities: Detail the specific duties and accountabilities of all personnel involved, including system owners, security officers, assessors, authorizing officials, and continuous monitoring teams.
- Definitions: Provide clear explanations of key terms (e.g., risk, vulnerability, control, ATO, Security Assessment Report) to ensure common understanding.
- Security Assessment Procedures: Outline the methodologies for conducting security assessments, including types of assessments (e.g., vulnerability scans, penetration tests, control reviews), frequency, and criteria for evaluation.
- Risk Management Framework: Describe the organization’s approach to identifying, analyzing, and treating risks, including acceptable risk thresholds and criteria for risk acceptance.
- Authorization Process: Detail the steps for requesting, reviewing, and granting authorization to operate (ATO), including documentation requirements, approval workflows, and timelines.
- Documentation Requirements: Specify all necessary artifacts for the assessment and authorization package, such as System Security Plans, Security Assessment Reports, Plans of Action and Milestones (POAMs), and Authorization Decisions.
- Continuous Monitoring Program: Explain how systems will be continuously monitored post-authorization to ensure ongoing security posture and compliance, including reassessment triggers and reporting requirements.
- Policy Review and Update Cycle: Define the schedule and process for regularly reviewing and updating the Security Assessment And Authorization Policy Template itself to ensure its continued relevance and effectiveness.
- Enforcement and Non-Compliance: Outline the consequences of non-adherence to the policy and the procedures for addressing such instances.
Tips on Design, Usability, and Implementation
A well-written Security Assessment And Authorization Policy Template is only effective if it is usable, accessible, and properly implemented throughout the organization. Design and usability considerations are paramount, whether the policy is primarily consumed in print or digital format.
For digital implementation, ensure the policy is available on an easily accessible internal platform, such as an intranet or a dedicated policy management system. Use clear, concise language and avoid overly technical jargon where possible, or provide a comprehensive glossary. Employ a logical structure with clear headings, subheadings, and a table of contents to facilitate navigation. Hyperlinks to relevant external resources, regulatory documents, or internal forms can significantly enhance its utility. Version control is also crucial; clearly indicate the current version, effective date, and any changes from previous iterations to prevent confusion and ensure everyone is referencing the most up-to-date information.
When considering print distribution (perhaps for compliance officers or for specific training sessions), ensure the layout is clean and professional. Use legible fonts, sufficient white space, and logical page breaks. While the digital version can be dynamic, a printed copy should still be comprehensive and easy to follow. Regardless of format, providing accompanying training sessions or awareness campaigns can significantly boost understanding and adoption across the organization. Make sure that new employees are onboarded with this policy as part of their initial training on workplace rules and data security protocols. Encourage feedback from users to continuously refine and improve the Security Assessment And Authorization Policy Template, making it a truly practical and living document that serves the organization effectively.
The journey to robust cybersecurity is continuous, and a well-defined Security Assessment And Authorization Policy Template is an indispensable compass for this journey. It transforms an often-abstract concept of "security" into a tangible, actionable process, allowing organizations to manage risk proactively and make informed decisions about their IT systems. By adopting and tailoring such a template, you’re not just creating a document; you’re building a foundation for resilience, compliance, and sustained operational integrity.
Ultimately, embracing a comprehensive Security Assessment And Authorization Policy Template empowers organizations to navigate the complexities of the digital age with confidence. It serves as a testament to an organization’s commitment to protecting its assets, its customers, and its reputation, making it not just a necessity but a strategic advantage in today’s interconnected world. Consider this framework not as a burden, but as an essential investment in your organization’s future security posture.