In today’s interconnected digital landscape, the question is no longer if a security incident will occur, but when. From sophisticated cyberattacks to accidental data exposures, organizations face a constant barrage of threats that can disrupt operations, erode customer trust, and incur significant financial penalties. Without a clear, pre-defined plan, the immediate aftermath of a breach can quickly devolve into chaos, exacerbating the damage and delaying recovery.
This is where a robust Security Incident Management Policy Template becomes indispensable. It serves as your organization’s blueprint for navigating the turbulent waters of a security event, transforming potential panic into a structured, efficient response. Businesses of all sizes, from agile startups to sprawling enterprises, as well as those responsible for compliance, data security, and operational resilience, will find immense value in adopting and adapting such a framework to safeguard their digital assets and maintain business continuity.
Why a Security Incident Management Policy Template is Essential
The modern threat landscape is characterized by its volatility and increasing complexity. Phishing attempts, ransomware attacks, insider threats, and zero-day exploits are just a few of the challenges organizations grapple with daily. In this environment, relying on ad-hoc responses or improvised decisions during a crisis is a recipe for disaster. A Security Incident Management Policy Template provides the necessary structure to react decisively and effectively.
Furthermore, regulatory pressures are more intense than ever. Compliance mandates like HIPAA, GDPR, CCPA, and various industry-specific regulations require organizations to not only protect data but also demonstrate a clear plan for responding to breaches. A well-articulated Security Incident Management Policy Template is a cornerstone of this compliance effort, helping organizations meet their legal obligations and avoid hefty fines and reputational damage. It frames an organization’s commitment to data security and its ability to handle unforeseen challenges, proving to stakeholders, customers, and regulators that due diligence is a priority.
Key Benefits of Utilizing a Security Incident Management Policy Template
Adopting and implementing a comprehensive Security Incident Management Policy Template offers a myriad of advantages that extend far beyond simply having a document on file. One of the most significant benefits is the dramatic reduction in incident response time. With predefined steps, clear roles, and established communication channels, teams can react swiftly, minimizing the window of vulnerability and the potential impact of a breach. This proactive stance significantly improves an organization’s overall cybersecurity posture.
Moreover, a standardized Security Incident Management Policy Template fosters consistency in how incidents are handled across different departments and teams. This ensures that every security event, regardless of its nature or scope, is addressed with the same level of rigor and adherence to best practices. This consistency is vital for effective incident tracking, analysis, and post-incident learning. It also bolsters an organization’s legal and regulatory standing, providing documented proof of a systematic approach to data protection and incident handling, which is crucial for demonstrating compliance and mitigating potential liabilities. The detailed incident response plan provided by the template helps to maintain business continuity and protect critical assets.
Customizing Your Security Incident Management Policy Template
While a Security Incident Management Policy Template provides a robust foundation, its true power lies in its adaptability. No two organizations are exactly alike, and their security needs, operational structures, and regulatory landscapes can vary significantly. Therefore, tailoring the template to fit your specific context is not just recommended, it’s crucial for its effectiveness.
For instance, a small business with limited IT staff might opt for a more streamlined Security Incident Management Policy Template, focusing on essential steps and leveraging external support agreements for specialized tasks. Conversely, a large financial institution would require a far more intricate policy, detailing specific protocols for different types of financial fraud, compliance with stringent federal regulations, and extensive stakeholder communication plans. Considerations for customization also include industry-specific data security requirements, the organization’s technological infrastructure (e.g., cloud-first vs. on-premise), and the maturity of its existing cybersecurity framework. Regularly reviewing and updating your customized Security Incident Management Policy Template ensures it remains relevant and effective against evolving threats and changes in your operational environment.
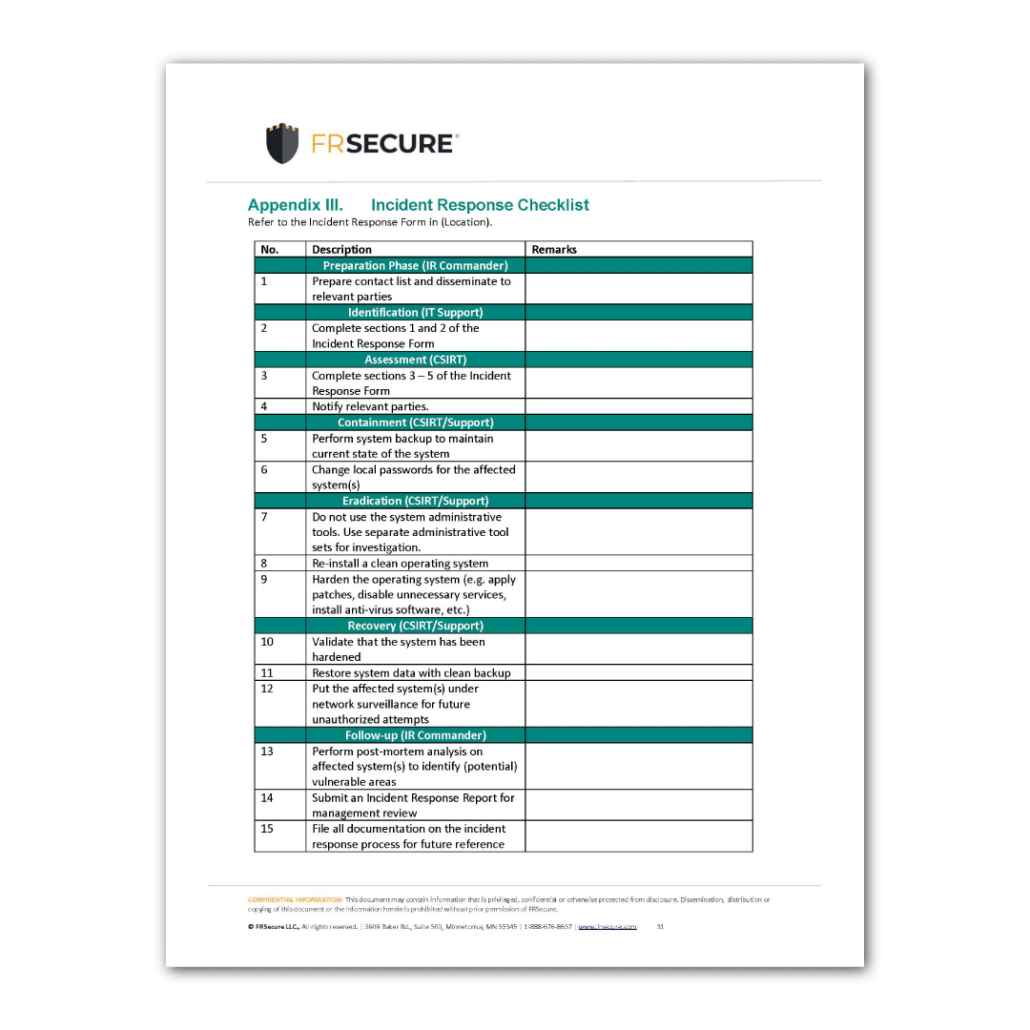
Essential Elements of a Security Incident Management Policy Template
A truly effective Security Incident Management Policy Template must encompass a variety of critical components to ensure a comprehensive and actionable framework for incident response. These elements provide clarity, structure, and guidance throughout the entire incident lifecycle, from initial detection to post-incident review. Without these core components, an incident response plan can quickly falter under pressure.
Here are the important elements that should be included in your Security Incident Management Policy Template:
- Policy Statement and Scope: A clear declaration of the policy’s purpose, objectives, and the assets or systems it covers. It should define what constitutes a security incident within the organization.
- Roles and Responsibilities: Clearly defined roles for the incident response team (IRT), management, legal, PR, and other key stakeholders, outlining who does what at each stage of an incident. This includes primary contacts and backup personnel.
- Incident Classification and Prioritization: A system for categorizing incidents based on their severity, impact, and potential for disruption. This helps in allocating resources effectively and ensuring critical incidents receive immediate attention.
- Incident Detection and Reporting Procedures: Detailed steps for identifying potential security incidents and the protocols for employees to report them. This includes contact information, reporting channels, and initial data collection requirements.
- Incident Response Stages: A structured outline of the incident response lifecycle, typically including:
- Preparation: Activities taken before an incident occurs (training, tools, policies).
- Identification: Confirming an incident, gathering initial data.
- Containment: Limiting the scope and impact of the incident.
- Eradication: Removing the root cause of the incident.
- Recovery: Restoring affected systems and data to normal operation.
- Post-Incident Activity: Reviewing the incident, documenting lessons learned, and implementing improvements.
- Communication Plan: Protocols for internal and external communication during and after an incident. This covers stakeholders, employees, customers, law enforcement, and regulatory bodies.
- Legal and Regulatory Considerations: A section detailing the organization’s obligations regarding data breach notification laws, privacy regulations (e.g., GDPR, CCPA), and other relevant legal frameworks. This is crucial for compliance.
- Evidence Handling and Forensics: Guidelines for collecting, preserving, and analyzing digital evidence in a legally sound manner, which is critical for investigations and potential legal action.
- Tools and Technologies: A list of approved tools, software, and services used for incident response, including SIEM systems, endpoint detection, and other security solutions.
- Training and Awareness: Requirements for regular training of employees on security awareness and incident reporting procedures to ensure preparedness.
- Policy Review and Update Schedule: A commitment to periodically review and update the Security Incident Management Policy Template to reflect changes in the threat landscape, technology, and organizational structure.
- Glossary of Terms: Definitions of key terms to ensure consistent understanding across the organization.
Design, Usability, and Implementation Tips for Your Policy Template
Developing a comprehensive Security Incident Management Policy Template is only half the battle; ensuring it’s usable, accessible, and effectively implemented is equally vital. A beautifully crafted policy that sits unread in a digital folder is practically useless during a crisis. Therefore, design and usability considerations are paramount for both print and digital versions.
First, keep the language clear, concise, and unambiguous. Avoid overly technical jargon where possible, or provide a clear glossary of terms. The policy should be easily understood by all relevant stakeholders, not just cybersecurity experts. Use headings, subheadings, bullet points, and numbered lists to break up dense text, making it scannable and digestible. For digital versions, ensure the Security Incident Management Policy Template is easily navigable, perhaps with a table of contents that links to specific sections. Version control is also critical for digital policies, ensuring that everyone is always referring to the most current iteration. Implement a system for tracking changes and communicating updates effectively. When it comes to implementation, don’t just distribute the policy; actively train your teams on its contents, conduct regular drills and tabletop exercises, and integrate it into your broader cybersecurity framework. Make it part of your workplace rules and employee training, so it becomes second nature during an actual event.
Ultimately, a Security Incident Management Policy Template isn’t just a document; it’s a living guide that empowers your organization to face security challenges head-on. By investing the time to develop, customize, and effectively implement this critical framework, you’re not just preparing for the inevitable; you’re building resilience, ensuring continuity, and safeguarding your most valuable assets. Think of it as your organization’s emergency playbook, ready to guide your team through any storm.
Embracing a well-crafted Security Incident Management Policy Template demonstrates a proactive commitment to data security and operational excellence. It transforms potential chaos into a controlled, strategic response, protecting your reputation, your finances, and your invaluable customer trust. Don’t wait for an incident to strike; put this essential tool to work for your organization today and build a stronger, more secure tomorrow.


