In today’s interconnected world, where cyber threats evolve with alarming speed and regulatory demands intensify, robust security isn’t just a feature—it’s foundational. Organizations are under immense pressure to not only build secure systems but also to demonstrate unequivocally that their security measures are comprehensive, effectively implemented, and continuously maintained. This often feels like navigating a complex maze of diverse requirements, technical controls, and compliance mandates. Without a structured approach, critical security aspects can easily slip through the cracks, leading to vulnerabilities, compliance failures, and significant reputational or financial costs.
This is where a methodical approach becomes invaluable. Imagine a tool that connects every security-related decision, from initial concept to deployment and beyond, back to its original requirement. A mechanism that provides a crystal-clear lineage, ensuring that every security control, test case, and mitigation strategy directly addresses a defined need. Such a tool transforms abstract security goals into tangible, verifiable actions, offering peace of mind to stakeholders and a clear roadmap for development teams. Let’s delve into how such a framework empowers teams to build and maintain truly secure systems, turning potential chaos into coherent, auditable order.
Why a Security Requirements Traceability Matrix is Indispensable
The journey of any software or system development is fraught with potential for misinterpretation and oversight, especially when it comes to security. Without a clear mechanism to link security requirements to design, implementation, and testing, projects risk deploying systems with gaping vulnerabilities or failing to meet critical compliance obligations. A security requirements traceability matrix (SRTM) acts as this essential bridge, providing a holistic view of how security needs are being addressed throughout the entire lifecycle. It’s not merely a document; it’s a living artifact that underpins an organization’s commitment to robust security.
This robust framework ensures that no security requirement is ever "forgotten" or left unaddressed. From the very first discussion of a new feature or system, security considerations are logged and tracked. As the project progresses, these initial requirements are meticulously linked to architectural decisions, specific security controls, test plans, and even deployment configurations. This unbroken chain of accountability is vital for preventing scope creep in security testing, ensuring that resources are allocated efficiently, and ultimately, building a more resilient product or service. Its utility extends far beyond initial development, serving as a critical resource for ongoing maintenance, audits, and continuous improvement.
Unpacking the Core Components of a Robust Traceability Matrix
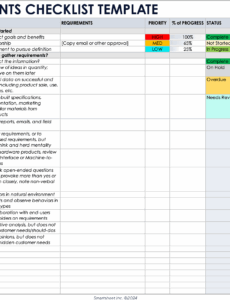
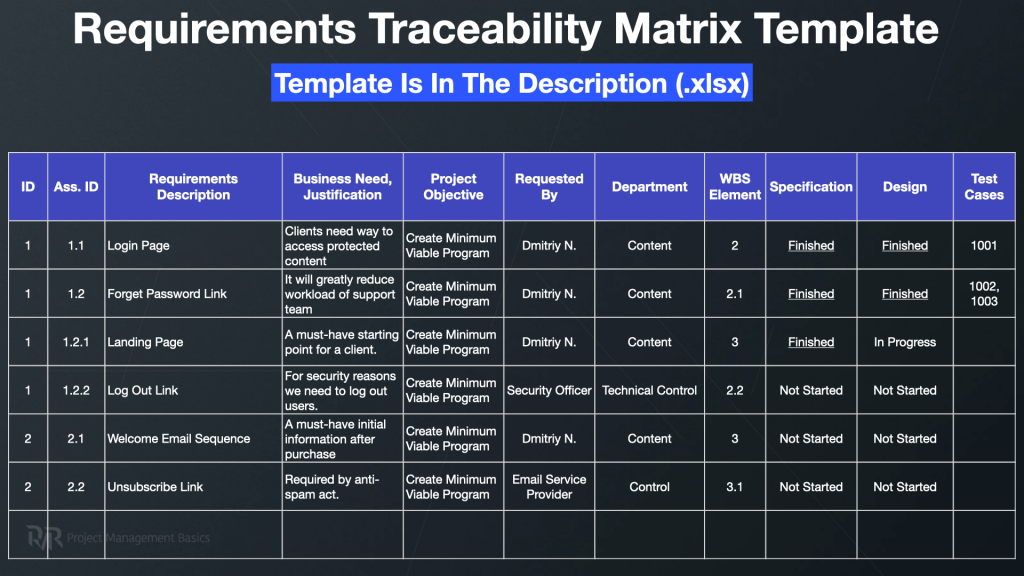
A well-constructed security traceability matrix is a detailed mapping document that provides a transparent link between different stages of the development and security lifecycle. While the exact columns may vary based on project specifics, industry, and regulatory environment, certain core elements are universally beneficial. These components ensure a comprehensive view and allow for effective tracking and verification of security posture. Understanding these building blocks is the first step towards leveraging a security requirements traceability matrix template effectively.
Here are the key elements typically found in such a matrix:
- **Requirement ID:** A unique identifier for each individual security requirement. This allows for clear referencing and tracking.
- **Requirement Description:** A clear, concise statement of the security requirement itself. This should be specific, measurable, achievable, relevant, and time-bound (SMART).
- **Requirement Source:** Identifies where the requirement originated (e.g., regulatory mandate like **GDPR** or **HIPAA**, internal security policy, risk assessment, client contract, industry standard like **NIST SP 800-53**).
- **Priority/Severity:** Indicates the importance or criticality of the requirement. This helps in resource allocation and risk management (e.g., Critical, High, Medium, Low).
- **Associated Use Cases/Stories:** Links the security requirement to specific functional use cases or user stories that it protects or enables.
- **Design/Architectural Elements:** References specific design decisions, architectural patterns, or components intended to satisfy the requirement.
- **Implementation Modules/Code Components:** Points to the actual code modules, configurations, or system components that implement the security control.
- **Security Controls/Mitigations:** Specifies the particular security control(s) or mitigation strategies deployed to address the requirement (e.g., encryption, access control, input validation).
- **Test Cases/Verification Methods:** Outlines the test cases, vulnerability scans, penetration tests, or audit procedures used to verify that the requirement has been met successfully.
- **Status:** Tracks the current state of the requirement (e.g., Proposed, Approved, In Progress, Implemented, Tested, Verified, Deferred, Retired).
- **Responsible Party:** Identifies the individual or team responsible for implementing or verifying the requirement.
- **Compliance Mapping:** Maps the security requirement to specific clauses of regulatory standards or compliance frameworks it helps satisfy.
- **Risk Association:** Links the requirement to the specific risks it is designed to mitigate, often referencing a risk register ID.
Key Benefits: Beyond Just Checking a Box
Implementing a robust system for tracking security specifications offers a myriad of advantages that extend far beyond simple compliance. It fundamentally transforms how an organization approaches security, integrating it as a core component of quality and risk management rather than an afterthought. This comprehensive visibility into the security posture of a system or application provides strategic benefits that impact multiple facets of the business, fostering a culture of security by design.
Firstly, enhanced compliance and audit readiness are significant boons. When regulators or auditors demand proof of adherence to standards like PCI DSS, ISO 27001, or SOC 2, a well-maintained security requirement mapping provides an instant, verifiable trail. It dramatically reduces the time and effort required for audits, showcasing a proactive and mature security program. Secondly, it leads to improved communication and collaboration across teams. Developers, security architects, QA testers, and project managers can all refer to a single source of truth, minimizing misunderstandings and ensuring everyone is aligned on security objectives and their implementation.
Furthermore, a detailed mapping of security controls directly aids in risk management and mitigation. By clearly linking requirements to the risks they address, organizations can prioritize security efforts based on potential impact and likelihood, ensuring that critical vulnerabilities are addressed first. It also supports efficient defect management, as traceability helps pinpoint the root cause of security flaws by tracing them back to their originating requirement or missing control. Finally, it drives better decision-making and resource allocation. With clear visibility into the status of all security specifications, management can make informed decisions about project timelines, budgets, and the deployment of security talent, ensuring that resources are applied where they will have the greatest impact.
Implementing Your Security Traceability Solution: Practical Tips
Adopting a formal system for tracking security needs doesn’t have to be an overwhelming task. While the concept might seem complex, practical steps can make its implementation smooth and effective. The goal is to integrate this crucial practice into your existing workflows, making it a natural part of your secure development lifecycle (SDLC) rather than an isolated, burdensome activity. Successfully leveraging a security requirements traceability matrix requires thoughtful planning and consistent execution.
Start small: Begin by piloting the security specification tracking on a new, moderately sized project. This allows your team to learn, adapt, and refine the process before scaling it across the organization. Next, ensure tool selection aligns with your existing ecosystem. While a basic spreadsheet can serve as an initial security documentation template, specialized requirements management tools (like Jira, Azure DevOps, DOORS, or dedicated RTM software) offer automation, version control, and integration capabilities that become invaluable as your projects grow. Choose a solution that balances functionality with ease of use for your teams.
Crucially, define clear roles and respons responsibilities early on. Who is responsible for defining requirements, who updates their status, and who reviews the matrix? Establishing ownership prevents confusion and ensures accountability. Integrate the security traceability matrix into your existing SDLC gates. For example, ensure that design reviews include a check against security requirements, and that testing phases specifically validate the implementation of security controls referenced in the matrix. Regular reviews are also paramount; schedule periodic meetings to review and update the matrix, especially after significant changes in requirements, design, or detected vulnerabilities. This keeps the matrix current and relevant, maximizing its value as an audit readiness tool and a living record of your security assurance framework.
Common Pitfalls and How to Avoid Them
While the benefits of a robust security requirement mapping are clear, organizations can encounter several pitfalls during implementation that undermine its effectiveness. Being aware of these common challenges can help teams proactively avoid them and ensure the security traceability solution delivers its full value. Building a useful matrix is an ongoing commitment, not a one-time setup.
One major pitfall is treating the traceability matrix as a static document instead of a living artifact. Requirements, designs, and threats evolve; if the matrix isn’t updated regularly, it quickly becomes outdated and useless. To avoid this, embed its maintenance into routine project activities and assign clear ownership for updates. Another common issue is over-complication. Trying to capture every single minute detail from day one can lead to an unwieldy and unmanageable matrix that discourages use. Start with essential fields and gradually add complexity as your team gains experience and identifies specific needs.
Lack of team buy-in is also a significant hurdle. If team members perceive the security requirement tracking as unnecessary overhead, they won’t maintain it diligently. Address this by communicating the benefits clearly, providing adequate training, and making the process as streamlined as possible. Integrate it into existing tools to minimize context switching. Furthermore, watch out for inconsistent granularity in requirements. Some requirements might be too high-level, others too granular, making mapping difficult. Strive for a consistent level of detail that is actionable and verifiable. Finally, avoid insufficient tooling or automation. Manual upkeep of a large matrix can be incredibly time-consuming and prone to errors. Invest in tools that support automation, version control, and integration with other project management or security tools to reduce manual effort and improve data accuracy, making it a more effective secure development lifecycle tool.
The value of a well-implemented traceability matrix extends far beyond mere documentation; it’s a strategic asset that underpins an organization’s security posture. By systematically linking security requirements to their implementation, testing, and compliance, teams gain unparalleled visibility and control over their systems’ security. This meticulous approach not only fosters a culture of accountability but also significantly strengthens the ability to respond to audits, mitigate risks, and adapt to the ever-changing threat landscape.
In an era where data breaches and compliance failures carry severe consequences, investing in a structured method for managing security requirements is no longer optional—it’s imperative. A robust security traceability framework empowers organizations to build resilience, instill confidence, and ensure that security is not just an aspiration but a verifiable reality woven into the fabric of every product and service.
Frequently Asked Questions
What is the primary purpose of a security requirements traceability matrix?
The primary purpose is to provide a comprehensive, documented link between an organization’s security requirements and their implementation, testing, and verification throughout the entire system development lifecycle. It ensures that every security need is addressed and auditable.
How often should a security traceability matrix be updated?
A security traceability matrix should be updated whenever there are changes to requirements, design, implementation, test results, or compliance mandates. It’s a living document that requires continuous maintenance to remain accurate and valuable.
Can a spreadsheet be used as a security requirements traceability matrix template?
Yes, a spreadsheet can serve as a basic security requirements traceability matrix template, especially for smaller projects. However, for larger, more complex projects, specialized requirements management tools or integrated project management software offer superior features like version control, automation, and collaborative capabilities.
What’s the difference between a general Requirements Traceability Matrix and one focused on security?
While both track requirements, a general Requirements Traceability Matrix (RTM) focuses on linking functional and non-functional requirements to design, development, and testing. A security-focused RTM specifically emphasizes security requirements, linking them to security controls, threat models, security testing, compliance standards, and risk mitigation strategies.
Who typically uses or benefits from a security traceability matrix?
Security architects, project managers, development teams, quality assurance testers, compliance officers, and auditors all significantly benefit. It helps developers ensure secure coding, QA in validating security controls, compliance teams in demonstrating adherence to regulations, and auditors in verifying security posture.