In the dynamic and highly sensitive realm of healthcare, safeguarding patient information isn’t just a best practice—it’s a legal imperative and a cornerstone of trust. Every day, countless individuals within a healthcare organization, from frontline nurses and physicians to administrative staff and IT professionals, require access to confidential patient data, electronic health records (EHRs), and operational systems. Managing this intricate web of access permissions without a robust, clearly defined framework can quickly lead to vulnerabilities, compliance breaches, and significant operational hurdles.
This is precisely where a well-crafted User Access Policy Template Healthcare becomes not just useful, but indispensable. It provides a foundational blueprint, a standardized approach to defining who can access what information, under what conditions, and with what level of authority. For practice managers, compliance officers, IT directors, and even clinic owners, understanding and implementing such a policy is crucial for maintaining data integrity, ensuring patient privacy, and navigating the complex landscape of healthcare regulations, particularly HIPAA in the United States.
Why a User Access Policy Template Healthcare is Essential
The modern healthcare environment is characterized by an ever-increasing reliance on digital systems and the constant threat of cyberattacks. Patient data, encompassing everything from medical histories to billing information, is highly valuable to malicious actors. Without a clear and enforceable User Access Policy Template Healthcare, organizations are left vulnerable to data breaches, unauthorized access, and potential misuse of sensitive information. This document serves as a critical defense line.
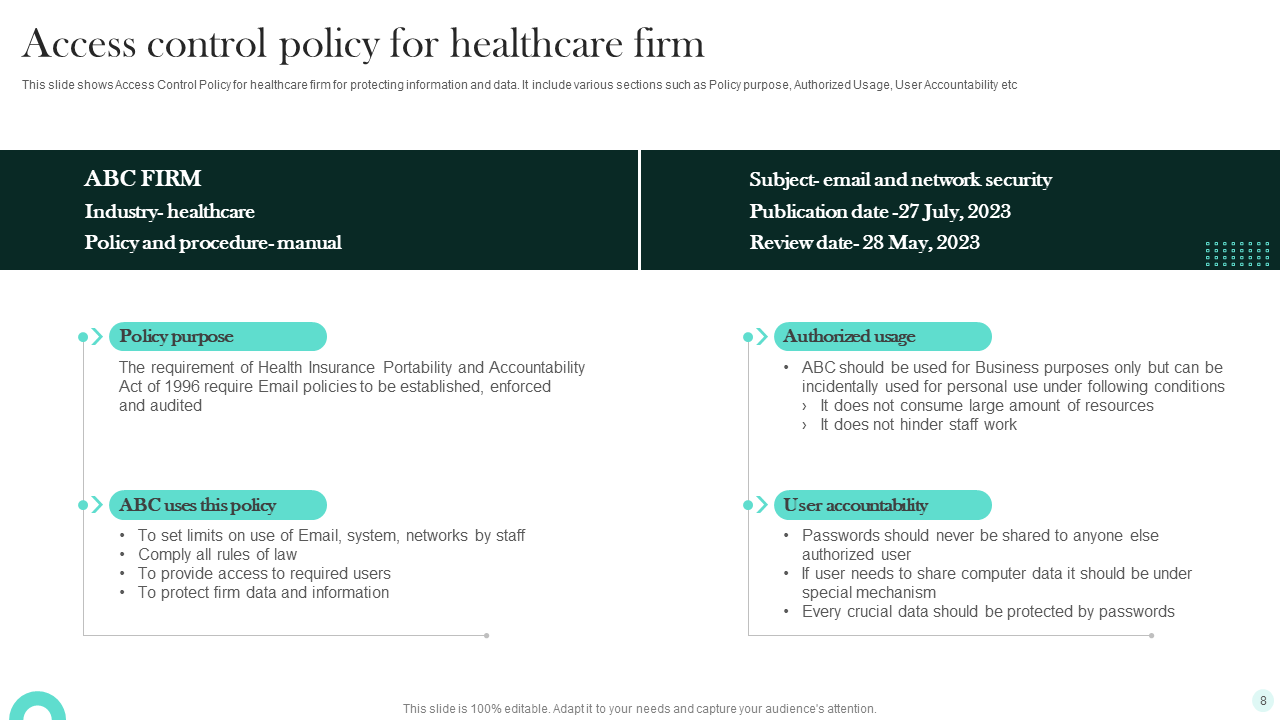
Beyond security, a robust policy is fundamental for regulatory compliance. HIPAA (Health Insurance Portability and Accountability Act) mandates strict controls over protected health information (PHI). A well-defined access policy is a tangible demonstration of an organization’s commitment to these regulations, helping to avoid hefty fines and reputational damage. It ensures that access to EMR/EHR systems and other data repositories is consistently managed, audited, and aligned with legal requirements, forming a vital part of comprehensive information governance and data protection strategies.
Furthermore, a User Access Policy Template Healthcare contributes significantly to operational efficiency. By clearly outlining roles, responsibilities, and access levels, it streamlines the onboarding process for new staff, reduces administrative overhead associated with granting and revoking access, and minimizes errors stemming from ambiguous permissions. It establishes clear workplace rules regarding data handling, fostering a culture of accountability and security across the entire workforce. This proactive approach minimizes confusion and ensures that all personnel understand their obligations regarding secure access to systems and patient data.
Key Benefits of Utilizing a User Access Policy Template Healthcare
The advantages of adopting and implementing a comprehensive User Access Policy Template Healthcare extend across multiple facets of a healthcare organization, offering both immediate and long-term gains. One of the primary benefits is enhanced data security. By stipulating granular access controls based on the "principle of least privilege," organizations can drastically reduce the risk of unauthorized access and internal data breaches, ensuring that individuals only have access to the information absolutely necessary for their job functions.
Another significant benefit is streamlined compliance management. With a pre-designed structure that addresses common regulatory requirements like HIPAA, a User Access Policy Template Healthcare simplifies the process of meeting legal obligations. It provides a clear, documented framework that can be presented during audits, demonstrating due diligence and a proactive approach to patient privacy and data protection. This structured approach helps in building a robust legal framework around data access.
Moreover, such a template promotes consistency and clarity across the organization. It ensures that access provisioning and de-provisioning processes are uniform, regardless of department or role, reducing inconsistencies that can lead to security gaps or operational inefficiencies. This clear articulation of expectations regarding secure access and information handling helps in maintaining strong internal controls and managing workforce access effectively.
Finally, a well-implemented User Access Policy Template Healthcare provides a crucial layer of legal protection. In the unfortunate event of a data breach or compliance violation, having a documented and enforced policy demonstrates that the organization took reasonable steps to protect sensitive information. This can mitigate potential penalties and legal liabilities, reinforcing the importance of robust operational policies and robust IT security measures. It’s an essential component of an overall risk management strategy.
Customizing Your User Access Policy Template Healthcare
While a User Access Policy Template Healthcare provides an excellent starting point, its true value comes from its adaptability to the unique needs and scale of each healthcare entity. A small, independent clinic will have different requirements than a multi-hospital system or a specialized research facility. The beauty of a template lies in its flexibility to be molded to fit these diverse operational landscapes and specific information governance needs.
For instance, a template can be customized to reflect the specific roles within an organization. A primary care physician might require broad access to patient records, while a billing specialist might only need access to financial and demographic data. Customization allows for the precise mapping of access levels to job functions, incorporating Role-Based Access Control (RBAC) principles that define what types of data and systems each role can interact with. This ensures that secure access is tailored to the actual duties performed by staff.
Furthermore, the template should be adapted to account for the specific technologies and systems in use. Whether it’s a particular EHR vendor, a bespoke patient portal, or specialized diagnostic equipment, the policy must clearly define access protocols for each. Considerations such as single sign-on (SSO) integration, multi-factor authentication (MFA) requirements, and remote access policies need to be explicitly detailed within the customized document to align with the organization’s unique technological infrastructure and IT security protocols.
Finally, state-specific regulations and specialized accreditation standards may necessitate further customization. While HIPAA provides a federal baseline, many states have additional privacy laws that impact data protection and information sharing. Organizations must review their User Access Policy Template Healthcare to ensure it not only meets federal requirements but also adheres to any more stringent local mandates, providing a truly comprehensive legal framework for their operations. This proactive approach to tailoring operational policies is key to effective compliance.
Essential Elements of a User Access Policy Template Healthcare
A robust User Access Policy Template Healthcare should be comprehensive, covering all critical aspects of managing who can access what within a healthcare setting. Here are the important elements and fields that should be included:
- Policy Scope and Purpose: Clearly define what the policy covers (e.g., all information systems, data, and personnel) and its overarching goals (e.g., protect PHI, ensure compliance, maintain data integrity).
- Definitions: Provide clear definitions for key terms such as Protected Health Information (PHI), Electronic Health Record (EHR), User, Access Provisioning, etc., to ensure universal understanding of workplace rules.
- Roles and Responsibilities: Outline the responsibilities of various stakeholders, including Data Owners, System Administrators, End Users, and Compliance Officers, in maintaining and enforcing the policy.
- Access Levels and Types: Detail the different levels of access (e.g., read-only, read/write, administrative) and specify how these map to job roles and departments, ideally using Role-Based Access Control (RBAC).
- User Authentication: Mandate requirements for strong passwords, multi-factor authentication (MFA), password expiry, and secure login procedures to ensure secure access.
- Access Provisioning: Describe the standardized process for granting new users access, including authorization steps, required documentation, and necessary training.
- Access Review and Recertification: Establish a schedule and procedure for regularly reviewing and re-certifying user access permissions to ensure they remain appropriate and current.
- Access De-provisioning: Outline the process for revoking access when an employee leaves, changes roles, or is no longer authorized, ensuring immediate removal of access privileges to protect data.
- Acceptable Use Policy (AUP): Integrate guidelines on the acceptable use of organizational IT resources, including internet, email, and software, to prevent misuse and maintain IT security.
- Data Confidentiality and Privacy: Reiterate commitments to HIPAA and other privacy regulations, emphasizing the need for users to protect PHI and report any potential breaches.
- Reporting Security Incidents: Provide clear instructions on how users should report suspected security incidents, unauthorized access, or policy violations.
- Policy Enforcement and Sanctions: Define the consequences for non-compliance, ranging from disciplinary action to legal repercussions, reinforcing the serious nature of data protection.
- Policy Review and Revision History: Specify how often the policy will be reviewed and updated, and maintain a record of all revisions, including dates and changes made, for audit trails and information governance.
Design, Usability, and Implementation Tips for Your User Access Policy Template Healthcare
Even the most robust User Access Policy Template Healthcare can fall short if it’s not designed for clarity, usability, and effective implementation. The goal is not just to have a document, but to have a living, accessible set of guidelines that every employee understands and adheres to.
When it comes to design, prioritize clarity and conciseness. Use plain language, avoiding overly technical jargon where possible. Employ clear headings, subheadings, and bullet points to break up text and make it easy to digest. A well-organized table of contents can also significantly enhance navigability, especially for longer policies. For digital versions, ensure the document is searchable and mobile-friendly, allowing staff to quickly find relevant sections whether they’re at a desktop or on the go.
Usability extends to how the policy is presented and communicated. Don’t just publish it and expect everyone to read it. Incorporate the User Access Policy Template Healthcare into new employee onboarding and regular compliance training. Use real-world examples in training sessions to illustrate acceptable and unacceptable behavior. Consider creating a simplified "Key Takeaways" summary or an FAQ document to accompany the full policy, making core principles more accessible.
For implementation, leverage both print and digital strategies. While a digital version is essential for accessibility and updates, having a concise printed version (or key sections) readily available in common areas might be beneficial for quick reference, particularly in clinical settings. Integrate the policy with your organization’s broader information governance framework and IT security protocols. Utilize digital tools for managing user access, such as identity and access management (IAM) systems, which can automate provisioning, de-provisioning, and access reviews, ensuring consistent application of the defined workplace rules. Regular reminders and communications about the importance of secure access and data protection will keep the policy top-of-mind.
In the complex and ever-evolving landscape of healthcare, a meticulously crafted User Access Policy Template Healthcare is more than just a regulatory checkbox; it’s a strategic asset. It provides the essential framework for safeguarding sensitive patient data, ensuring operational continuity, and building a culture of security and compliance that permeates every level of the organization. By adopting and diligently customizing such a policy, healthcare entities can proactively mitigate risks, enhance trust, and focus on their primary mission: delivering exceptional patient care.
Embracing a well-defined User Access Policy Template Healthcare means investing in your organization’s future, securing its digital perimeter, and upholding the solemn responsibility of protecting patient privacy. It’s an indispensable tool for any healthcare provider committed to best practices in data protection and information governance, offering a clear path to managing secure access in an increasingly digital world. Don’t view it as a burden, but rather as an empowering solution that strengthens your entire operational and legal framework.


