In an increasingly interconnected digital world, where data is king and cyber threats lurk around every corner, safeguarding sensitive information has become a paramount concern for organizations of all sizes. One of the most critical, yet often overlooked, aspects of a robust cybersecurity posture is effective access management. It’s not just about who gets in, but ensuring that those who have access still need it, and that their permissions are appropriate for their current role.
This is where a User Access Review Policy Template becomes an indispensable tool. Far from being just another piece of corporate bureaucracy, it’s a foundational document that empowers businesses to systematically verify and validate who has access to what systems and data. Whether you’re a small startup navigating initial growth or a large enterprise grappling with complex regulatory requirements, understanding and implementing such a policy is crucial for maintaining security, achieving compliance, and preventing costly data breaches.
Why a User Access Review Policy Template is Essential Today
The modern business landscape is riddled with escalating cyber risks and an ever-tightening web of regulatory requirements. Without a clear and comprehensive User Access Review Policy Template, organizations are essentially operating blind, leaving themselves vulnerable to a myriad of threats. This essential policy acts as a continuous audit mechanism, ensuring that access privileges remain aligned with business needs and security best practices.
Consider the implications of regulatory frameworks like HIPAA for healthcare, GDPR for data privacy in Europe (with significant implications for US companies dealing with European data), Sarbanes-Oxley (SOX) for financial reporting, and CCPA for California consumer data. Each of these mandates stringent controls over who can access sensitive information. A well-crafted User Access Review Policy Template provides the structured approach necessary to demonstrate due diligence and satisfy these complex compliance demands, helping to avoid hefty fines and reputational damage.
Furthermore, the threat of insider threats, whether malicious or accidental, cannot be understated. Employees change roles, leave the company, or acquire new responsibilities, and their access privileges often lag behind these changes. Stale access, or "privilege creep," is a significant vulnerability. By systematically reviewing and revoking unnecessary access, a robust policy significantly reduces the attack surface and mitigates the risk of unauthorized data exposure or manipulation. It’s about more than just data security; it’s about robust risk management and maintaining a strong internal control environment.
Key Benefits of Utilizing a User Access Review Policy Template
Implementing a standardized User Access Review Policy Template offers a wealth of advantages that extend far beyond mere compliance. It fundamentally strengthens an organization’s overall security posture and operational efficiency. The proactive nature of regular access reviews helps identify and rectify potential weaknesses before they can be exploited.
Firstly, enhanced security is a direct outcome. By ensuring that user access rights are always current and appropriate, the risk of unauthorized access, data breaches, and insider threats is dramatically reduced. This policy template provides a clear framework for systematically removing access for former employees or those who have changed roles, closing off potential backdoors.
Secondly, audit readiness becomes significantly easier. When auditors come knocking, they will invariably ask for evidence of access controls. Having a well-documented and consistently followed User Access Review Policy Template, complete with audit trails of reviews conducted, streamlines the audit process, saving time, resources, and stress. It demonstrates a commitment to governance and accountability.
Thirdly, operational efficiency can see unexpected improvements. While seemingly a compliance overhead, a structured approach helps streamline IT and HR processes related to onboarding, offboarding, and role changes. It forces clarity around who needs access to what, reducing the ad-hoc granting of excessive permissions and fostering a more organized identity management system. This clear set of workplace rules contributes to a more secure and efficient working environment.
Customizing Your User Access Review Policy Template
No two organizations are exactly alike, and therefore, a "one-size-fits-all" approach to an access review policy simply won’t suffice. The beauty of a User Access Review Policy Template lies in its adaptability. It provides a solid foundation that can be meticulously tailored to suit the specific needs, scale, industry, and risk appetite of your business.
For smaller businesses, customization might mean simplifying the review process, focusing on critical systems first, and assigning roles to a more limited pool of personnel. The emphasis might be on clarity and ease of implementation without excessive complexity. Conversely, a large enterprise with thousands of employees, intricate departmental structures, and diverse technological systems will require a more granular and sophisticated policy. This might involve defining different review frequencies for various data classifications or systems, establishing multi-tiered approval workflows, and integrating with advanced identity and access management (IAM) solutions.
Industry-specific regulations also play a significant role in customization. A financial institution, for instance, will need to incorporate specific requirements related to financial transactions and customer data privacy (e.g., Gramm-Leach-Bliley Act), while a healthcare provider will prioritize HIPAA compliance. Organizations operating in cloud environments will need to address cloud access controls, distinguishing them from on-premise system access. When adapting your User Access Review Policy Template, consider your organizational culture, the sensitivity of your data, and the specific regulatory obligations that govern your operations.
Essential Elements of a Comprehensive User Access Review Policy Template
A truly effective User Access Review Policy Template is more than just a vague declaration; it is a meticulously structured document that leaves no room for ambiguity. It must clearly define the scope, responsibilities, and procedures involved in managing and reviewing user access rights. Here are the critical components that should be included:
- Policy Statement and Purpose: Clearly articulate the policy’s objective, emphasizing the organization’s commitment to data security, compliance, and responsible access management.
- Scope: Define what systems, applications, data repositories, and types of user accounts (e.g., regular employees, contractors, service accounts, administrative accounts) are covered by the policy.
- Definitions: Provide clear definitions for key terms such as "user access," "privileged access," "access review," "role-based access control (RBAC)," and "data owner" to ensure consistent understanding.
- Roles and Responsibilities: Explicitly assign responsibilities for conducting reviews, approving changes, escalating issues, and maintaining documentation. This typically involves system owners, data owners, department heads, IT security, and HR.
- Review Frequency: Specify how often different types of access will be reviewed (e.g., quarterly for privileged access, semi-annually for standard user access, immediately upon role change or termination).
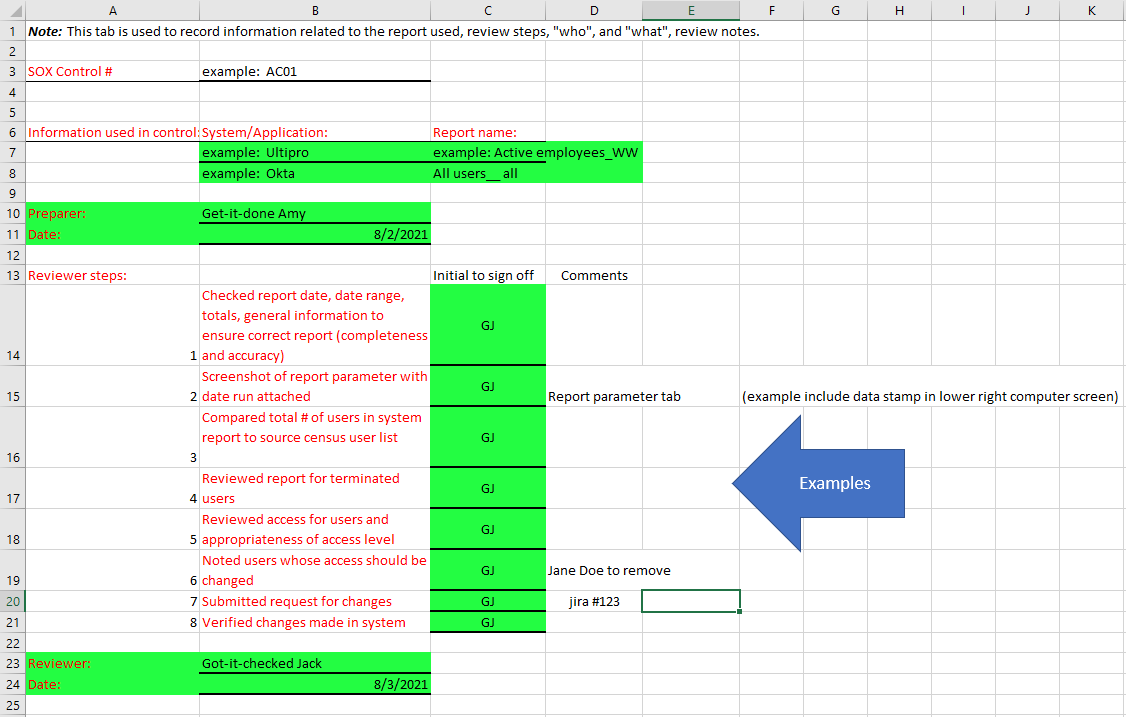
- Review Procedures: Detail the step-by-step process for conducting an access review, including how access lists are generated, who performs the initial verification, the approval workflow, and how discrepancies are handled.
- Documentation and Audit Trails: Outline requirements for documenting review results, approvals, and any changes made. This is crucial for demonstrating compliance and providing an audit trail.
- Exception Process: Establish a formal process for requesting and approving exceptions to the policy, ensuring that all exceptions are justified, time-limited, and properly documented.
- Training and Awareness: Describe how users and reviewers will be trained on the policy’s requirements and their responsibilities in maintaining proper access controls.
- Policy Enforcement and Consequences: Clearly state the consequences for non-compliance with the policy, reinforcing its importance and encouraging adherence.
- Policy Review and Updates: Specify a schedule for periodically reviewing and updating the User Access Review Policy Template itself to ensure it remains relevant and effective in a changing threat landscape.
Tips for Designing, Implementing, and Maintaining Your Policy
Developing a robust User Access Review Policy Template is only half the battle; its successful implementation and ongoing maintenance are equally crucial. A well-designed policy should be not only comprehensive but also practical, usable, and easily understood by all stakeholders. Think of it as a living document that guides continuous improvement in your organization’s security posture.
When designing your policy, prioritize clarity and conciseness. Avoid overly technical jargon where plain language will suffice, ensuring that even non-technical staff can understand their roles and obligations. Use clear headings, bullet points, and flowcharts to enhance readability. For digital distribution, ensure the User Access Review Policy Template is easily accessible on your intranet or through a dedicated policy management system. Consider creating an executive summary to highlight key takeaways for senior leadership, making the case for its importance.
Implementation requires a strategic approach. Start with a pilot program in a less critical department or system to iron out any kinks before a full rollout. Provide comprehensive training to all individuals involved in the access review process, from data owners to IT security personnel. Emphasize the "why" behind the policy – its role in protecting the organization and individuals – to foster buy-in rather than simply mandating compliance. Ongoing communication is key; regular reminders and updates can reinforce the policy’s importance.
Finally, maintenance is vital for the long-term effectiveness of your policy. Schedule regular reviews of the User Access Review Policy Template itself, typically annually or whenever significant organizational or technological changes occur. Establish a feedback mechanism to gather input from those executing the policy, allowing for continuous refinement. Regularly audit the access review process itself to ensure it’s being followed consistently and effectively. This proactive approach ensures your policy remains a strong defense against evolving threats and regulatory obligations.
In the complex tapestry of modern cybersecurity and compliance, a User Access Review Policy Template stands out as a critical thread. It’s more than just a bureaucratic checkbox; it’s a strategic asset that underpins your data security efforts, demonstrates accountability, and protects your organization from both internal and external threats. By systematically managing who has access to what, you are not just meeting regulatory requirements but actively building a more resilient and secure operational environment.
Investing the time and resources into developing, customizing, and rigorously implementing a comprehensive User Access Review Policy Template is an investment in your organization’s future. It provides the clarity, structure, and peace of mind necessary to navigate the digital age with confidence. Consider this not just a template, but a blueprint for a more secure and compliant tomorrow, empowering your team to protect what matters most.


