In today’s hyper-connected world, where digital threats evolve at a dizzying pace, the foundational strength of an organization’s cybersecurity posture is paramount. Gone are the days when a simple firewall and antivirus software sufficed; modern enterprises face a relentless barrage of sophisticated attacks designed to exploit even the most minor weaknesses. Proactive vulnerability management is no longer a luxury but an absolute necessity, serving as the bedrock upon which robust data security and operational resilience are built.
Navigating this complex landscape requires a clear, comprehensive, and actionable strategy. This is precisely where a Vulnerability Management Policy Template Nist becomes an invaluable resource. It offers a structured framework, drawing upon the widely respected guidelines from the National Institute of Standards and Technology (NIST), to help organizations systematically identify, assess, prioritize, and mitigate security vulnerabilities. Whether you’re a Chief Information Security Officer (CISO), an IT director, a compliance officer, or simply responsible for safeguarding your company’s digital assets, this template provides a vital starting point for establishing an effective vulnerability management program.
Why a Vulnerability Management Policy Template NIST is Essential in Today’s Context
The digital attack surface for most organizations is expanding exponentially, driven by cloud adoption, remote workforces, IoT devices, and complex supply chains. Each new connection point introduces potential vulnerabilities, making the task of securing an enterprise more challenging than ever. Without a defined strategy, organizations risk operating in a reactive mode, constantly scrambling to address breaches rather than preventing them.
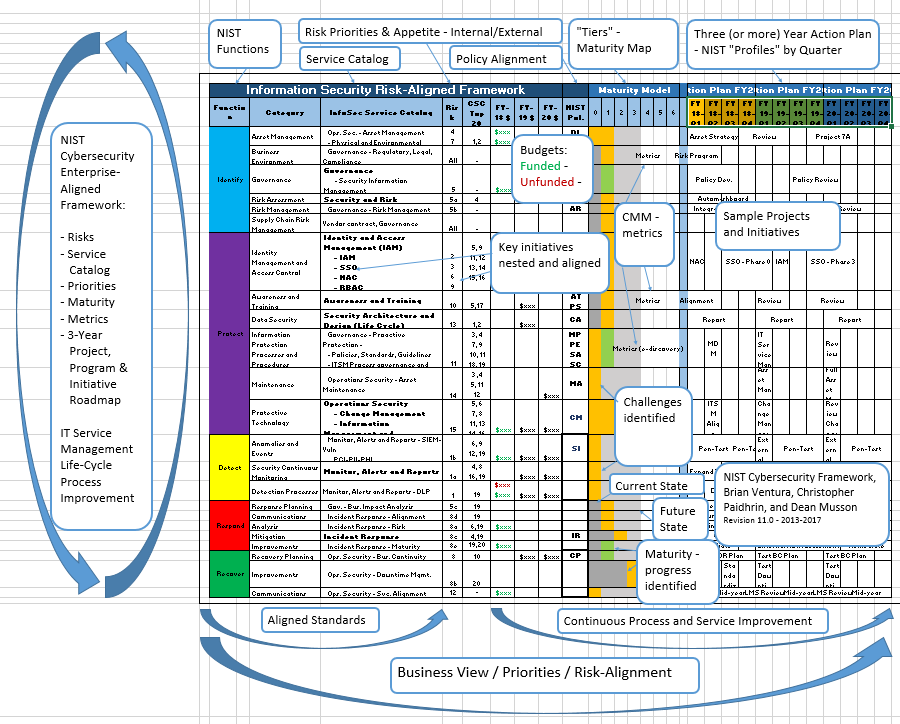
A robust Vulnerability Management Policy Template Nist provides the necessary structure to move from reactive firefighting to proactive risk management. It establishes a disciplined approach, ensuring that security teams aren’t just scanning for vulnerabilities, but systematically addressing them in alignment with business objectives. This not only minimizes the window of opportunity for attackers but also builds a more resilient and trustworthy infrastructure.
Moreover, the regulatory landscape is increasingly demanding. From HIPAA and PCI DSS to GDPR, CCPA, and the growing prominence of CMMC for government contractors, compliance with various data security standards is mandatory. A well-implemented Vulnerability Management Policy Template Nist directly contributes to meeting these stringent requirements, helping organizations demonstrate due diligence and avoid potentially crippling fines and reputational damage. It translates NIST’s authoritative guidance into practical, enforceable organizational policy, bridging the gap between abstract security frameworks and actionable internal procedures.
Key Benefits of Using a Vulnerability Management Policy Template NIST
Adopting a Vulnerability Management Policy Template Nist offers a multitude of strategic and operational advantages that extend far beyond simply finding bugs. It fundamentally transforms how an organization approaches cybersecurity, fostering a culture of continuous improvement and risk awareness.
Firstly, it provides a structured and systematic approach to vulnerability management. Instead of ad-hoc efforts, organizations gain a clear roadmap for identifying, assessing, prioritizing, and remediating security flaws, ensuring consistency and thoroughness across all assets. This standardized methodology enhances efficiency and reduces the chances of critical vulnerabilities being overlooked.
Secondly, a NIST-aligned policy significantly enhances compliance posture. By adhering to a globally recognized standard, organizations can confidently demonstrate their commitment to data security and risk mitigation to auditors, regulators, and stakeholders. This can be crucial for sectors subject to strict regulatory oversight, providing a clear path to satisfy audit requirements and avoid penalties.
Thirdly, it directly leads to reduced cyber risk and improved security posture. By systematically addressing weaknesses, the overall attack surface is significantly shrunk, making it harder for malicious actors to exploit systems. This proactive stance prevents costly breaches, protects sensitive information, and safeguards intellectual property, ultimately preserving business continuity.
Finally, the template fosters greater accountability and clear communication within an organization. It defines roles, responsibilities, and reporting lines, ensuring that everyone understands their part in maintaining security. This clarity minimizes confusion, streamlines incident response, and promotes a unified approach to organizational security, strengthening the overall defense against cyber threats.
How a Vulnerability Management Policy Template NIST Can Be Customized or Adapted to Different Needs
While a Vulnerability Management Policy Template Nist provides an excellent foundation, it’s crucial to understand that it is not a one-size-fits-all solution. Every organization has unique characteristics, including its industry, size, regulatory obligations, technological footprint, and risk appetite. Therefore, effective implementation demands thoughtful customization.
Small businesses, for instance, might need to scale down the complexity, focusing on core assets and leveraging readily available, cost-effective tools. Their policy might emphasize a streamlined patch management process and regular vulnerability scanning with external providers. Conversely, large enterprises with diverse IT environments, multiple cloud providers, and complex legacy systems will require a more comprehensive and granular policy, detailing advanced penetration testing schedules, threat intelligence integration, and sophisticated incident response protocols.
The specific industry also dictates necessary adaptations. A healthcare provider will need to place a heavy emphasis on HIPAA compliance and protecting Protected Health Information (PHI), which might involve specific requirements for medical device vulnerability management. A financial institution will prioritize PCI DSS compliance and the security of financial transactions, leading to rigorous controls around cardholder data environments. The Vulnerability Management Policy Template Nist acts as a robust framework, which can then be tailored with specific annexes or sections addressing these sector-specific nuances and compliance frameworks.
Moreover, organizations should consider their current security maturity level and available resources. If a company is just beginning its cybersecurity journey, the policy might initially focus on fundamental practices like asset inventory and basic scanning. As the organization matures, the policy can evolve to incorporate advanced techniques, automated tools, and a more sophisticated risk assessment methodology. The flexibility inherent in the NIST framework allows for this progressive approach, ensuring the policy remains relevant and achievable as the organization’s security capabilities grow.
Important Elements or Fields That Should Be Included in a Vulnerability Management Policy Template NIST
A truly effective Vulnerability Management Policy Template Nist must be comprehensive, leaving no critical aspect of the vulnerability management lifecycle unaddressed. It should serve as a clear, authoritative guide for all personnel involved in maintaining the organization’s security posture. Here are the essential elements:
- Policy Statement and Scope: A high-level declaration of the organization’s commitment to vulnerability management, clearly defining what systems, networks, applications, and data are covered by the policy.
- Roles and Responsibilities: Detailed assignment of duties for individuals and teams, including asset owners, security operations, IT administration, compliance officers, and executive management. This ensures clear accountability.
- Vulnerability Identification: Procedures for discovering vulnerabilities, encompassing regular vulnerability scanning (internal and external), penetration testing, code reviews, security audits, and leveraging threat intelligence feeds.
- Vulnerability Assessment and Prioritization: Methods for evaluating the severity and potential impact of identified vulnerabilities, often using standardized scoring systems like CVSS (Common Vulnerability Scoring System) and considering business context and data sensitivity.
- Remediation and Patch Management: Clearly defined processes for addressing vulnerabilities, including patch management procedures, configuration changes, workarounds, and secure coding practices. This section should also outline remediation timelines based on severity.
- Exception Handling: A formal process for requesting and approving exceptions to the policy when immediate remediation is not feasible, detailing the justification, compensatory controls, and re-evaluation schedule.
- Reporting and Communication: Guidelines for internal reporting of vulnerability status, remediation progress, and overall program effectiveness to relevant stakeholders, including management and incident response teams.
- Policy Review and Maintenance: A schedule and process for regularly reviewing, updating, and approving the vulnerability management policy to ensure its continued relevance and alignment with evolving threats and organizational changes.
- Training and Awareness: Requirements for educating employees, particularly those with security responsibilities, on the importance of vulnerability management and their role in upholding the policy.
- Compliance and Audit: How the organization will measure, monitor, and audit compliance with the policy, including metrics, reporting mechanisms, and processes for demonstrating adherence to regulatory requirements.
- Integration with Other Security Policies: Explanation of how this policy integrates with other organizational security policies, such as Incident Response, Acceptable Use, and Data Classification policies.
Tips on Design, Usability, or Implementation
Creating a robust Vulnerability Management Policy Template Nist is only half the battle; ensuring its usability and effective implementation is equally critical. A policy gathering dust on a server is as good as no policy at all.
Firstly, design for clarity and conciseness. Avoid overly technical jargon where plain language will suffice, and use clear, actionable statements. Employees from various departments, not just IT security, should be able to understand their responsibilities. Use a logical structure with clear headings and subheadings, making it easy to navigate and find specific information quickly.
For usability, consider both print and digital formats. While a digital version, perhaps on an internal wiki or a document management system, offers searchability and version control, a concise print-friendly summary might be useful for key personnel. Ensure the digital version is accessible from various devices and that there’s a clear process for version control, preventing confusion over outdated policies. Incorporate tables, flowcharts, or diagrams to visually represent complex processes, such as vulnerability prioritization or remediation workflows, enhancing comprehension.
When it comes to implementation, it’s crucial to treat the policy as a living document. It should be regularly reviewed, at least annually, or whenever significant changes occur in the organization’s IT environment, risk profile, or regulatory landscape. Actively involve key stakeholders—from executive management to front-line IT staff and even legal counsel—in the development and review process. This fosters buy-in and ensures the policy is practical and enforceable.
Finally, effective communication and training are paramount. Simply publishing the policy is insufficient. Conduct regular training sessions to educate employees about the policy’s requirements, their roles, and the importance of vulnerability management. Emphasize that security is a shared responsibility. Reinforce the policy’s principles through ongoing awareness campaigns, reminding everyone that vigilance is a continuous effort and a critical component of strong organizational security.
In a world where cyber threats are a constant and evolving challenge, a well-crafted Vulnerability Management Policy Template Nist is an indispensable asset for any organization. It provides the strategic clarity and operational guidance needed to navigate the complexities of cybersecurity, transforming potential weaknesses into fortified defenses.
By adopting and meticulously customizing this framework, businesses can move beyond reactive security measures to embrace a proactive, systematic approach to risk mitigation. It’s more than just a document; it’s a commitment to resilience, a blueprint for protecting critical assets, and a testament to an organization’s dedication to maintaining trust and operational integrity. Consider how a robust Vulnerability Management Policy Template Nist can fortify your defenses and ensure your organization is prepared for the cyber challenges of tomorrow.