In today’s interconnected digital landscape, the question isn’t if an organization will face a cybersecurity threat, but when. Proactive defense mechanisms are no longer optional; they are paramount to survival and trust. Among these, a robust vulnerability management program stands as a critical pillar, continuously identifying, assessing, and remediating weaknesses before they can be exploited by malicious actors.
However, crafting a comprehensive and effective vulnerability management policy from scratch can be a daunting task, often mired in legalistic jargon and overwhelming complexity. This is where the concept of a Vulnerability Management Policy Template Sans comes into play – a streamlined, practical framework designed to cut through the noise and provide clear, actionable guidance. It’s for CISOs, IT directors, security managers, and compliance officers who seek an efficient, no-nonsense approach to establishing a foundational policy that truly works for their organization, rather than creating an unmanageable bureaucratic burden.
Why Vulnerability Management Policy Template Sans is Essential in Today’s Threat Landscape
The pace of digital transformation and the sophistication of cyber threats are escalating at an unprecedented rate. From pervasive ransomware campaigns to targeted zero-day exploits, organizations face a constant barrage of attacks that can cripple operations, compromise sensitive data, and erode customer confidence. In this volatile environment, merely reacting to incidents is insufficient; a strategic, proactive stance is imperative.
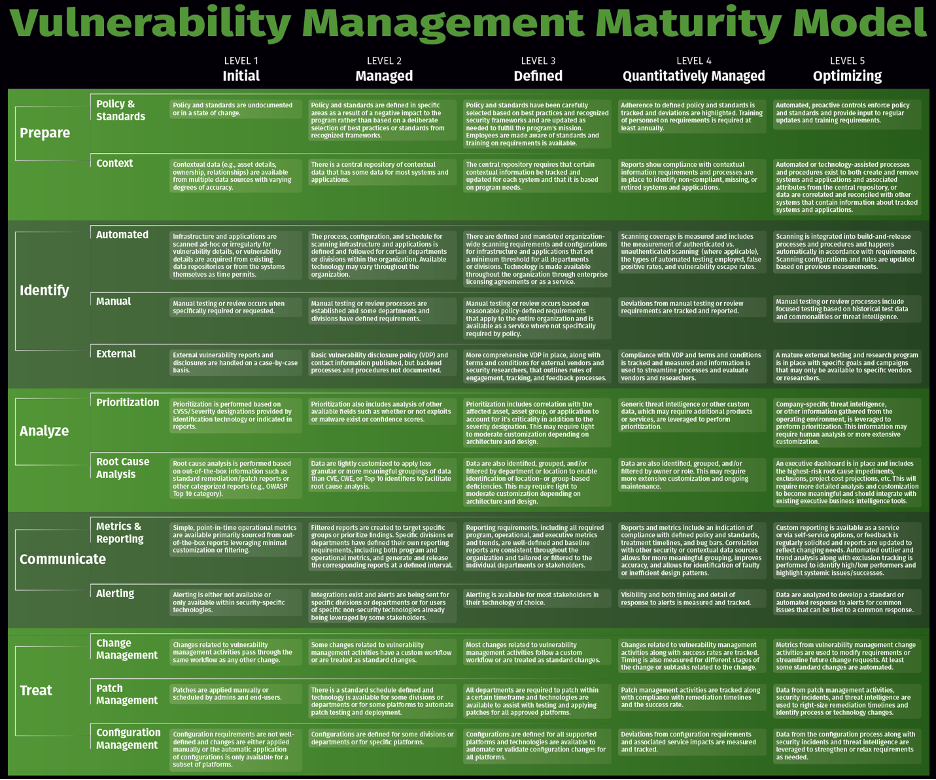
A well-defined vulnerability management policy acts as your organization’s roadmap for navigating these challenges. It codifies the processes, responsibilities, and standards required to systematically identify and address security weaknesses. Without such a policy, security efforts can become fragmented, inconsistent, and ultimately ineffective, leaving critical assets exposed. The Vulnerability Management Policy Template Sans simplifies the initial creation process, helping organizations quickly establish a baseline for robust data security and risk management that aligns with current threat intelligence.
Moreover, the regulatory landscape is growing increasingly stringent. Frameworks like GDPR, HIPAA, PCI DSS, and various state-specific data protection laws demand demonstrable due diligence in protecting sensitive information. An effective vulnerability management program, guided by a clear policy, provides the necessary evidence of compliance and adherence to best practices. Leveraging a Vulnerability Management Policy Template Sans allows organizations to swiftly adapt and demonstrate their commitment to regulatory requirements, building a strong security posture from the ground up without getting bogged down in unnecessary complexities.
Key Benefits of Embracing Vulnerability Management Policy Template Sans
Adopting a tailored Vulnerability Management Policy Template Sans offers a multitude of advantages that extend beyond mere compliance, fundamentally strengthening an organization’s overall security and operational resilience.
Firstly, it provides unparalleled clarity and consistency. By establishing standardized procedures, explicit roles, and clear responsibilities for every stage of the vulnerability lifecycle, it eliminates ambiguity. This ensures that everyone, from the security analyst to the executive team, understands their part in maintaining the organization’s security posture, leading to more efficient and coordinated efforts.
Secondly, it significantly enhances compliance enablement. For organizations operating under strict regulatory requirements or adherence to security frameworks like NIST CSF or ISO 27001, a well-structured policy is indispensable. The Vulnerability Management Policy Template Sans serves as a robust framework to align internal processes with external mandates, simplifying audit readiness and demonstrating a proactive approach to governance. This structured approach helps in navigating the complex world of legal terms and obligations related to data protection.
Thirdly, its primary benefit is risk reduction. By mandating regular scanning, assessment, and remediation, the policy ensures that known vulnerabilities are identified and addressed before threat actors can exploit them. This proactive stance dramatically lowers the likelihood and potential impact of a successful cyberattack, protecting critical assets and sensitive data from compromise.
Furthermore, a clear policy fosters improved communication and collaboration across departments. It defines the channels and expectations for information sharing between security teams, IT operations, development, and business units. This collaborative environment ensures that vulnerability management is not siloed but integrated into the broader organizational security strategy, making the policy enforcement more effective.
Finally, it leads to resource optimization. With defined processes and priorities, organizations can allocate their security resources – both human and technological – more efficiently. This prevents wasted effort on low-priority issues and focuses attention on critical risks, ultimately making the vulnerability management program more cost-effective and sustainable. A good Vulnerability Management Policy Template Sans simplifies the task of resource allocation by clearly outlining what needs to be done and by whom.
Customizing Vulnerability Management Policy Template Sans for Unique Organizational Needs
While a "template sans" implies a lean, effective starting point, it’s crucial to recognize that no single policy fits every organization perfectly. The true power of a Vulnerability Management Policy Template Sans lies in its adaptability and the ease with which it can be customized to reflect your specific operational realities, risk appetite, and strategic objectives.
The customization process should consider several key factors. First, organizational size and complexity will dictate the level of detail and formality required. A small startup might need a more agile policy than a large multinational corporation with diverse IT infrastructure and numerous regulatory obligations. Second, your industry and regulatory environment are paramount. Healthcare organizations, for example, will have distinct requirements related to HIPAA, while financial institutions face PCI DSS and other specific financial regulations.
Consider your technology stack and operational environment. Whether your assets are predominantly on-premise, cloud-based, or a hybrid model will influence the scope and methods of vulnerability identification and remediation. Your organization’s risk appetite also plays a significant role; some organizations may tolerate certain low-level risks, while others demand immediate remediation for almost any identified weakness.
Engaging key stakeholders from IT, security, legal, HR, and business units is vital during customization. Their input ensures the policy is practical, enforceable, and aligned with overall business goals. The "Sans" philosophy in Vulnerability Management Policy Template Sans means that the core structure is stripped down to essentials, providing a clear foundation that is easy to build upon, rather than an overly prescriptive document that hinders adaptation. This allows you to integrate existing security frameworks and governance structures seamlessly, ensuring a coherent and effective overall security strategy.
Important Elements and Fields in Your Vulnerability Management Policy Template Sans
A robust vulnerability management policy, even one designed to be streamlined, must cover essential components to be truly effective. The following are critical elements and fields that should be included when adapting your Vulnerability Management Policy Template Sans:
- Policy Statement and Objectives: Clearly articulate the purpose, scope, and goals of the vulnerability management program. This includes its commitment to protecting information assets and maintaining a strong security posture.
- Scope: Define precisely what assets, systems, applications, and networks fall under the purview of this policy. Specify whether it covers internal, external, cloud, or on-premise environments.
- Roles and Responsibilities: Clearly delineate the individuals, teams, or departments responsible for each phase of vulnerability management, from identification to remediation and reporting. This includes responsibilities for asset management.
- Vulnerability Identification: Detail the methods used to discover vulnerabilities, such as regular vulnerability scanning, penetration testing (both internal and external), web application security testing, and leveraging threat intelligence feeds.
- Vulnerability Assessment and Prioritization: Outline the criteria and methodology for assessing the risk level of identified vulnerabilities. This often involves a risk scoring system (e.g., CVSS) that considers factors like severity, exploitability, and asset criticality.
- Vulnerability Remediation and Patch Management: Establish clear procedures and Service Level Agreements (SLAs) for patching, configuration changes, or other remediation actions. Specify timelines based on vulnerability severity and asset importance.
- Exception Handling Process: Define a formal process for requesting and approving exceptions to the policy, including justification, compensating controls, and re-evaluation schedules.
- Reporting and Metrics: Specify the types of reports to be generated, their frequency, target audience, and key performance indicators (KPIs) to track the effectiveness of the vulnerability management program.
- Policy Review and Updates: Mandate a regular review cycle for the policy itself to ensure it remains relevant, effective, and aligned with evolving threats, technologies, and regulatory requirements.
- Compliance and Enforcement: Detail the consequences of non-compliance with the policy and how adherence will be enforced. This links directly to broader workplace rules and data security protocols.
- Integration with Incident Response: Describe how vulnerability management activities feed into and support the broader incident response plan, ensuring a cohesive security operation.
Tips for Design, Usability, and Implementation of Your Policy
Crafting an effective Vulnerability Management Policy Template Sans is only half the battle; its true value is realized through its design, usability, and successful implementation across the organization.
Clarity and Simplicity are paramount. Avoid overly technical jargon where plain language will suffice. The policy should be understandable by all relevant personnel, not just security experts. Keep sentences concise and paragraphs short (2-4 sentences) to improve readability. A good Vulnerability Management Policy Template Sans prioritizes ease of understanding.
For accessibility and usability, ensure the policy is easy to find and reference. Host it on an accessible digital platform, such as your company intranet, a dedicated security portal, or a document management system. While digital formats are often preferred, also consider if a print-ready version is necessary for specific scenarios, ensuring consistent formatting across both. Organize the document with clear headings and a logical flow, perhaps even including a table of contents.
Version control is absolutely critical. Implement a robust system to track changes, review dates, and approvals. This not only ensures everyone is working from the most current version but also provides an essential audit trail for compliance purposes. The history of policy updates shows a commitment to ongoing improvement.
Training and awareness are key to successful implementation. Simply publishing the policy is not enough. Conduct regular training sessions for all personnel involved, explaining their roles, responsibilities, and the importance of adherence. Security awareness campaigns can reinforce key messages and foster a culture of security.
Consider integration with existing tools. Your Vulnerability Management Policy Template Sans should complement, not conflict with, your security tools. This includes vulnerability scanners, ticketing systems, CMDBs (Configuration Management Databases), and asset management solutions. The policy can specify how these tools are used to fulfill its objectives, creating a seamless workflow for remediation and compliance.
Finally, remember that a policy is a living document. It’s not a set-and-forget artifact. Establish a schedule for regular review and updates (e.g., annually or whenever significant changes in technology, threats, or regulations occur). This iterative approach ensures your policy remains relevant and effective in addressing the ever-evolving threat landscape.
The journey to a resilient cybersecurity posture is ongoing, and a well-crafted vulnerability management policy is an indispensable guide. By embracing the principles of a Vulnerability Management Policy Template Sans, organizations can avoid the common pitfalls of overly complex or ambiguous documentation, opting instead for a clear, actionable, and adaptable framework. This streamlined approach empowers security teams to focus on what truly matters: identifying and mitigating risks effectively, safeguarding critical assets, and ensuring business continuity.
Ultimately, a pragmatic policy allows for better allocation of resources, clearer understanding of obligations, and a more robust defense against an increasingly sophisticated array of cyber threats. By leveraging the flexibility and essential structure provided by a Vulnerability Management Policy Template Sans, organizations can build a stronger, more compliant, and more secure future, turning potential vulnerabilities into manageable risks. It’s a practical solution for any enterprise looking to fortify its digital perimeter without getting lost in unnecessary complexity.


