In today’s interconnected digital landscape, the stability and security of an organization’s IT infrastructure are paramount. Windows operating systems, powering the vast majority of business environments, are constantly under scrutiny from threat actors looking for vulnerabilities. Patching these systems isn’t merely a technical task; it’s a critical strategic imperative that underpins an organization’s entire cybersecurity posture. A well-defined Windows Patch Management Policy Template provides the essential framework for a proactive, consistent, and resilient defense strategy.
This comprehensive guide is designed for IT managers, cybersecurity professionals, system administrators, and business leaders who recognize the urgent need to formalize their patch management processes. It’s more than just a checklist; it’s a foundational document that helps you safeguard your digital assets, maintain operational continuity, and navigate the complex web of compliance requirements. By understanding and implementing a robust Windows Patch Management Policy Template, organizations can transform a reactive chore into a strategic advantage, ensuring their systems remain secure, stable, and ready for whatever challenges the digital world presents.
Why a Windows Patch Management Policy Template is Essential
The threat landscape is continuously evolving, with new vulnerabilities discovered daily. Cybercriminals are swift to exploit unpatched systems, turning known weaknesses into gateways for ransomware attacks, data breaches, and other malicious activities. Without a clear and enforceable Windows Patch Management Policy Template, organizations leave themselves exposed to significant risks, both financial and reputational. This template provides the backbone for a systematic approach to mitigating these threats.
Beyond immediate security concerns, regulatory compliance is a major driver for adopting a formal policy. Frameworks like HIPAA, GDPR, PCI DSS, and NIST CSF mandate stringent requirements for data security and vulnerability management. A robust Windows Patch Management Policy Template serves as documented proof of an organization’s commitment to these standards, helping to avoid costly fines and legal repercussions. It also establishes clear workplace rules and guidelines for IT staff, ensuring everyone understands their obligations in maintaining system integrity.
Furthermore, unpatched systems are prone to instability, leading to crashes, performance degradation, and service outages. Such disruptions can cripple business operations, resulting in lost productivity and damaged customer trust. A well-structured patch management policy helps ensure system stability and reliability, minimizing downtime and maintaining a seamless operational flow. It’s about being proactive rather than reactive, preventing problems before they impact your bottom line.
Key Benefits of Adopting a Windows Patch Management Policy Template
Implementing a standardized Windows Patch Management Policy Template offers a multitude of benefits that extend far beyond simply keeping systems updated. It acts as a force multiplier for an organization’s security and operational efficiency. One of the primary advantages is the significant enhancement of your overall security posture, as known vulnerabilities are systematically addressed and remediated before they can be exploited.
Another critical benefit is improved compliance adherence. With a formal policy, organizations can clearly demonstrate their commitment to regulatory requirements, making audit readiness significantly easier. This policy provides a documented blueprint for how the organization meets its obligations regarding data security and system integrity, reducing the stress and complexity associated with compliance audits. It ensures that internal agreements regarding security protocols are consistently met.
A formalized Windows Patch Management Policy Template also leads to greater operational efficiency. It standardizes processes, defines roles and responsibilities, and sets clear timelines for patch deployment. This consistency reduces human error, streamlines workflows, and ensures that IT resources are allocated effectively, preventing ad-hoc patching efforts that can consume valuable time and resources. Ultimately, this leads to reduced downtime and a more predictable IT environment, contributing directly to business continuity.
Customizing Your Windows Patch Management Policy Template
While a Windows Patch Management Policy Template provides an excellent starting point, it’s crucial to recognize that a one-size-fits-all approach rarely succeeds in the diverse world of IT. Every organization has unique needs, infrastructures, and risk profiles that necessitate tailoring the template to fit specific contexts. The beauty of a template lies in its adaptability, allowing you to create a policy framework that truly reflects your operational realities.
Consider your organization’s size and complexity. A small business with a handful of servers will have different needs than a large enterprise with thousands of endpoints across multiple geographical locations. The template should be adapted to reflect the scale of your operations, the size of your IT team, and the specific Windows versions and applications in use. This might involve adjusting the granularity of patch classifications or the frequency of deployment cycles.
Industry-specific regulations also play a significant role in customization. A healthcare provider, for instance, might need to incorporate stricter guidelines for patching systems that handle protected health information (PHI) to comply with HIPAA. Similarly, financial institutions will have unique requirements tied to their specific regulatory frameworks. Your customized Windows Patch Management Policy Template should clearly articulate how these external mandates are addressed, ensuring robust data security practices are embedded. Risk tolerance is another key factor; some organizations may prioritize rapid deployment, while others, due to the criticality of their systems, might opt for more extensive testing phases.
Important Elements of a Windows Patch Management Policy Template
A comprehensive Windows Patch Management Policy Template should clearly define the “who, what, when, where, and how” of patching. Each element serves a specific purpose in ensuring the policy is robust, actionable, and auditable.
- Policy Statement and Purpose: Clearly articulate the policy’s objective – to maintain the security, integrity, and availability of Windows systems by managing software updates and patches.
- Scope: Define which systems, applications, and operating system versions are covered (e.g., all Windows servers, workstations, specific critical applications, third-party software running on Windows).
- Roles and Responsibilities: Delineate who is responsible for each phase of patch management, from identification and testing to deployment, verification, and incident response. This includes IT staff, security teams, and management.
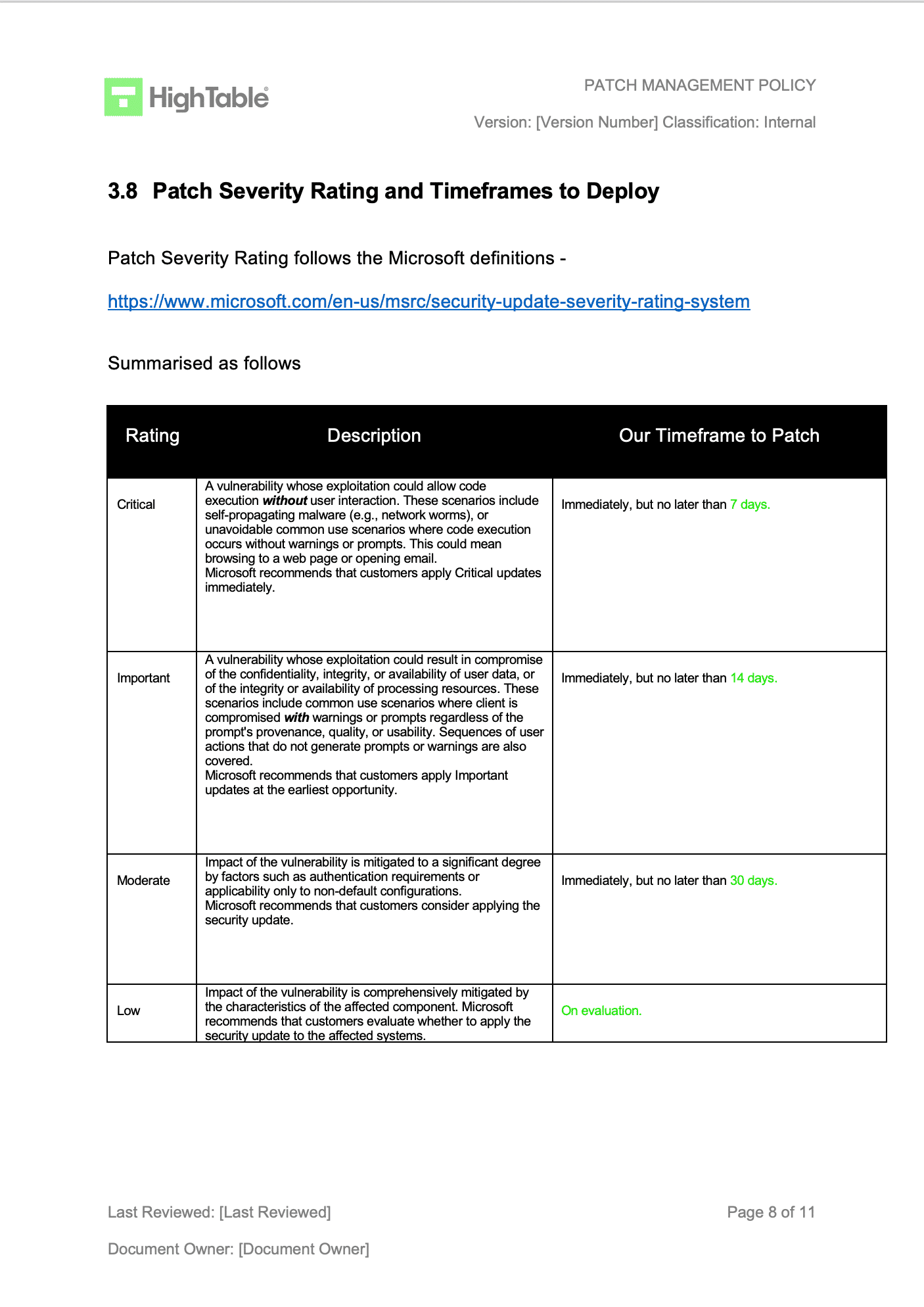
- Patch Classification and Prioritization: Establish a system for categorizing patches (e.g., critical security, non-critical security, functional updates, driver updates) and how their deployment priority is determined based on risk and impact.
- Patch Source and Verification: Specify approved sources for patches (e.g., Microsoft Update, WSUS, SCCM, vendor portals) and procedures for verifying their authenticity and integrity before deployment.
- Deployment Process: Outline the systematic steps for deploying patches, including:
- Testing: Procedures for testing patches in a non-production environment (staging, UAT) to identify potential conflicts or issues.
- Approval Process: Requirements for management or stakeholder approval before production deployment.
- Deployment Schedule: Defined maintenance windows, frequency (e.g., monthly, quarterly), and staggered rollout approaches.
- Verification: Steps to confirm successful patch installation and system stability post-deployment.
- Rollback Procedures: Detail the steps to revert systems to a pre-patch state in case of unexpected issues or critical failures after patch deployment.
- Reporting and Auditing: Define what patch status reports should be generated, their frequency, recipients, and how audit trails of patch activities are maintained for compliance and historical review.
- Vulnerability Management Integration: Explain how patch management integrates with the broader vulnerability management program, including scanning for unpatched vulnerabilities and remediation workflows.
- Compliance Mandates: Explicitly reference relevant regulatory requirements (e.g., HIPAA, PCI DSS, NIST CSF) and how the policy helps meet these obligations.
- Policy Review and Update Cycle: Specify how often the Windows Patch Management Policy Template itself will be reviewed, updated, and approved to adapt to evolving threats and organizational changes.
Tips for Design, Usability, and Implementation
A policy, however well-written, is only effective if it’s usable and properly implemented. When developing your Windows Patch Management Policy Template, consider its overall design and how it will be consumed by its intended audience. For instance, a clear, logical structure with headings, subheadings, and a table of contents (especially for longer, printable versions) will greatly enhance readability and make it easier for staff to quickly find the information they need.
Use clear, concise language, avoiding overly technical jargon where possible, or providing definitions for complex terms. The policy should be accessible not only to seasoned IT professionals but also to new hires or even non-technical stakeholders who might need to understand the basic premises of your data security protocols. Think about creating a concise executive summary if the full policy becomes extensive, providing a high-level overview for leadership.
For implementation, a comprehensive communication plan is crucial. Don’t just publish the policy; actively communicate its existence, its importance, and any changes to relevant teams. Consider incorporating the policy into new employee onboarding and regular training programs. This can involve dedicated training sessions on the policy and associated workplace rules, ensuring everyone understands their roles and responsibilities. Digital availability, perhaps on an internal wiki or SharePoint, alongside easily printable quick-reference guides, will ensure the policy is always at hand. Finally, integrate the policy with your existing IT tools and processes, such as WSUS, SCCM, Microsoft Intune, or third-party patching solutions, to ensure seamless execution. Regular review and updates are also key; a policy is a living document that must evolve with your organization and the threat landscape.
Crafting and implementing a robust Windows Patch Management Policy Template is more than just an administrative task; it’s a foundational pillar of modern cybersecurity and operational excellence. It transforms what could be a chaotic, reactive process into a structured, proactive defense mechanism, safeguarding your digital assets against an ever-increasing barrage of threats. By meticulously defining roles, processes, and responsibilities, organizations establish a clear path to maintaining system integrity and mitigating risks effectively.
Embracing this template allows you to move beyond merely reacting to vulnerabilities and instead build a resilient IT environment that can withstand sophisticated cyberattacks. It provides the peace of mind that comes from knowing your systems are secure, your data is protected, and your organization is well-positioned to meet compliance requirements. Take the proactive step today to customize and implement a Windows Patch Management Policy Template, reinforcing your commitment to a secure, stable, and compliant digital future.


