In an era defined by pervasive digital connectivity, the stakes for protecting sensitive information have never been higher. Every day, businesses across the globe face an onslaught of sophisticated cyber threats, from ransomware attacks to data breaches, each carrying the potential for devastating financial, reputational, and operational damage. It’s no longer a question of if an organization will face a security incident, but when and, more importantly, how well prepared it will be to respond and recover. This stark reality underscores the critical need for a robust and meticulously planned approach to cybersecurity.
This is where a well-defined Information Security Management Program (ISMP) becomes not just a best practice, but an absolute necessity. An Information Security Management Program Template isn’t just a document; it’s a strategic blueprint designed to guide organizations in establishing, implementing, maintaining, and continually improving their information security posture. It provides the foundational structure for managing security risks effectively, ensuring compliance with an ever-growing landscape of regulations, and safeguarding the invaluable digital assets that drive modern business.
Understanding the Imperative: Why an ISMP is Non-Negotiable
The digital landscape evolves at a breathtaking pace, and with it, the complexity and frequency of cyber threats. Organizations can no longer afford to view information security as an afterthought or a mere IT function. It must be an integral part of business strategy, championed from the top down. A comprehensive security management framework provides the necessary structure to navigate this challenging environment.
Beyond the immediate threat of cyberattacks, a robust information security management program addresses several critical business drivers. Regulatory compliance is a prime example; frameworks like HIPAA, GDPR, CCPA, and PCI DSS mandate specific security controls and processes. Non-compliance can lead to hefty fines, legal repercussions, and severe damage to customer trust. Furthermore, an effective ISMP is crucial for maintaining business continuity, ensuring that operations can quickly resume after an incident, minimizing downtime, and protecting revenue streams. It’s about building resilience and trust in an increasingly interconnected world.
The Core Components of a Robust Information Security Management Program
At its heart, an information security management program is a systematic approach to managing an organization’s sensitive information. It encompasses a wide array of policies, procedures, and technical controls designed to protect the confidentiality, integrity, and availability (CIA triad) of data. This program isn’t a one-time project but an ongoing cycle of planning, implementation, evaluation, and improvement, often aligned with internationally recognized standards like ISO 27001.
A successful ISMP integrates security into the fabric of the organization, touching every department and employee. It goes beyond technical safeguards to include human elements, processes, and governance. From identifying information assets and assessing risks to developing incident response plans and conducting regular security awareness training, each component plays a vital role in building a resilient defense against threats. Such a program establishes clear responsibilities, defines acceptable use, and outlines procedures for handling security incidents, ensuring that everyone understands their role in protecting critical data.
Leveraging an Information Security Management Program Template: Your Strategic Advantage
For many organizations, especially those without dedicated security teams or extensive resources, building an information security program from scratch can seem like a daunting, even overwhelming, task. This is precisely where an Information Security Management Program Template offers immense value. It acts as a pre-designed blueprint, providing a structured starting point that saves countless hours of research, planning, and drafting. Instead of beginning with a blank page, you start with a comprehensive framework that incorporates industry best practices and addresses common security requirements.
Using a well-crafted security management framework allows organizations to quickly establish a baseline for their security posture. It helps ensure that no critical areas are overlooked, from risk assessment methodologies to vendor management policies. While customization is always necessary to align with specific organizational needs and industry regulations, a program template significantly streamlines the initial development phase, accelerating the path to a mature and effective security program. It transforms a complex undertaking into a manageable, step-by-step process.
Key Elements to Expect in Your Program Framework
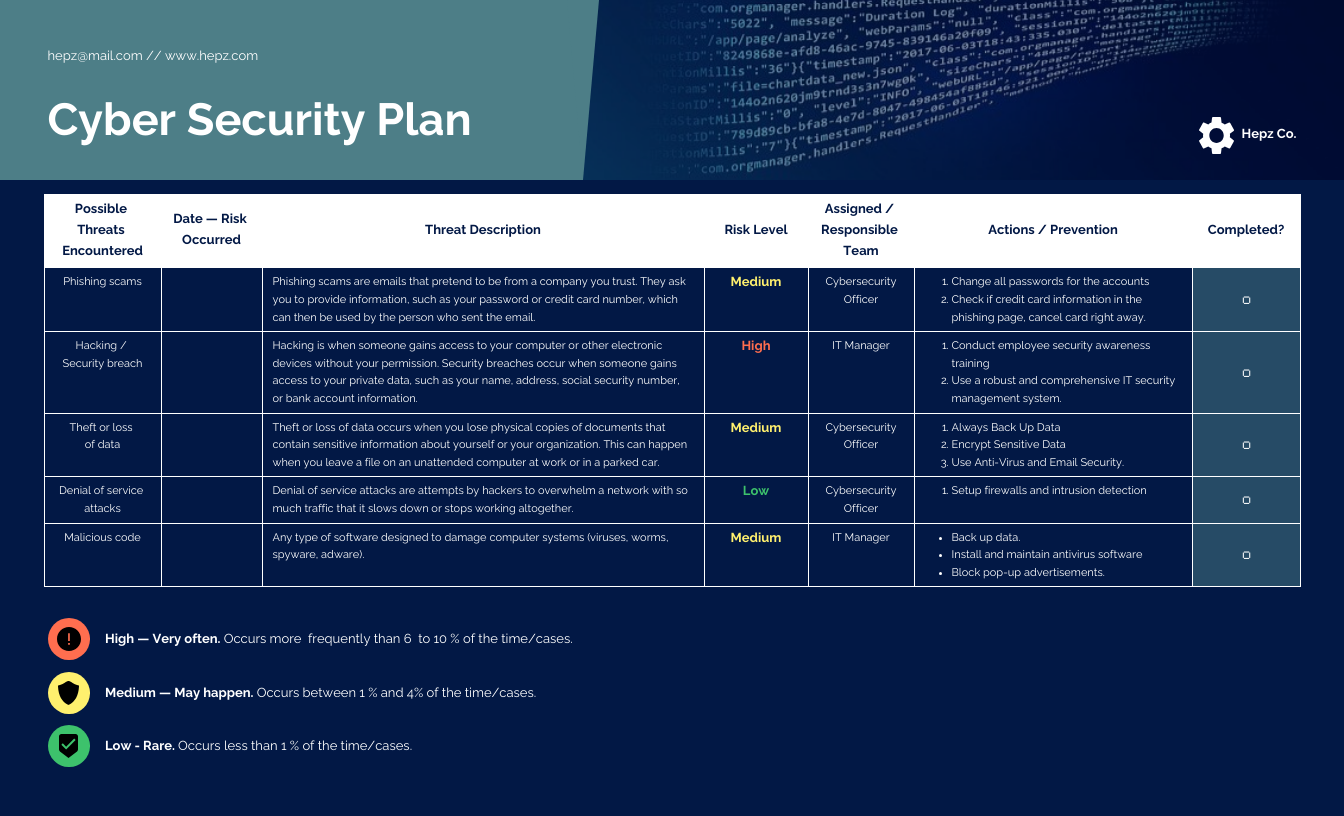
A comprehensive security management program outline will typically cover a broad spectrum of areas essential for effective risk mitigation and compliance. These elements form the backbone of your organizational security program and provide a structured approach to protecting information assets. When examining a template or developing your own, ensure these core components are addressed:
- **Governance and Leadership:** Defining roles, responsibilities, and accountability for information security across the organization. This includes establishing a **security steering committee** and assigning a **Chief Information Security Officer (CISO)** or equivalent.
- **Risk Management Framework:** A systematic process for **identifying, assessing, treating, and monitoring** information security risks. This should include methodologies for risk ranking, acceptance, and mitigation strategies.
- **Policies and Procedures:** A set of formal documents outlining the organization’s stance on various security aspects. Key policies often include:
- **Acceptable Use Policy** for IT resources.
- **Access Control Policy** governing user access to systems and data.
- **Data Classification Policy** defining how data should be categorized and handled based on sensitivity.
- **Incident Response Plan** detailing steps to take before, during, and after a security breach.
- **Vulnerability Management Policy** for identifying and patching security flaws.
- **Encryption Policy** for protecting data at rest and in transit.
- **Backup and Recovery Policy** to ensure data availability and business continuity.
- **Security Awareness Training:** Mandatory and regular education for all employees on security best practices, **phishing recognition**, and their individual responsibilities.
- **Technical Controls:** Implementation of safeguards such as **firewalls, intrusion detection/prevention systems, anti-malware software**, and **multi-factor authentication**.
- **Physical Security:** Measures to protect physical access to data centers, offices, and critical infrastructure, including **access cards, surveillance**, and **environmental controls**.
- **Vendor and Third-Party Risk Management:** Processes for assessing and managing security risks introduced by **suppliers, partners**, and other external entities.
- **Compliance and Audit Management:** Strategies for meeting regulatory requirements and conducting internal and external **security audits** to verify effectiveness.
- **Business Continuity and Disaster Recovery:** Plans to ensure the **resilience of operations** and the rapid recovery of systems and data following a major disruption.
- **Continuous Improvement:** Mechanisms for **regular review, updates**, and enhancements to the security program based on new threats, technologies, and organizational changes.
Implementing and Customizing Your Security Management Blueprint
While an information security management program offers a fantastic starting point, its true value is unlocked through careful implementation and customization. No two organizations are identical; their risk profiles, operational environments, industry regulations, and technological stacks will always vary. Therefore, treating any security program template as a copy-and-paste solution is a recipe for disaster.
The implementation journey typically begins with a thorough gap analysis of your current security posture against the framework provided. This helps identify areas where your organization falls short. Engage key stakeholders from IT, legal, HR, and executive leadership early in the process to ensure organizational buy-in and alignment. Adapt the policies, procedures, and controls within the cybersecurity framework template to reflect your specific business operations, risk tolerance, and compliance obligations. Regular reviews and updates are also paramount; the threat landscape is dynamic, and your security program must evolve alongside it. This iterative process ensures that your organizational security program remains relevant, effective, and resilient against emerging threats.
Establishing a robust information security framework is no longer an optional endeavor but a fundamental requirement for any organization operating in today’s digital world. It’s an investment in resilience, reputation, and continued success. By systematically addressing risks, enforcing clear policies, and fostering a culture of security awareness, businesses can protect their most valuable assets from an ever-present array of threats.
Embracing the disciplined approach offered by a solid Information Security Management Program Template empowers organizations to proactively manage their cybersecurity posture, rather than reactively responding to incidents. It provides clarity, reduces complexity, and builds the confidence needed to navigate the challenges of digital transformation safely. Invest in a structured security approach, customize it to your unique needs, and build a foundation that protects your future.