In today’s interconnected digital landscape, the phrase "it’s not if, but when" has become a stark reality for organizations navigating cybersecurity threats. Every piece of software, every operating system, and every network device represents a potential entry point for malicious actors. Staying ahead of these threats isn’t just a best practice; it’s a critical imperative for survival, and at its core lies effective patch and vulnerability management. This is precisely where a robust Patch And Vulnerability Management Policy Template becomes an indispensable asset.
Crafting a comprehensive Patch And Vulnerability Management Policy Template provides a structured blueprint for safeguarding your digital assets. It offers clarity, consistency, and accountability, transforming what could be a chaotic, reactive process into a streamlined, proactive defense strategy. Whether you’re an IT manager grappling with an ever-expanding inventory of devices, a Chief Information Security Officer (CISO) striving for a hardened security posture, or a small business owner simply trying to protect customer data, this template serves as your foundational guide to mitigating risks and ensuring operational resilience.
Why a Patch And Vulnerability Management Policy Template is Essential Today
The pace of technological change is relentless, and with it comes a continuous stream of newly discovered vulnerabilities. From ransomware campaigns that cripple entire organizations to sophisticated nation-state attacks targeting critical infrastructure, the threat landscape is more diverse and aggressive than ever before. A well-defined Patch And Vulnerability Management Policy Template is no longer a luxury but a fundamental necessity for several compelling reasons.
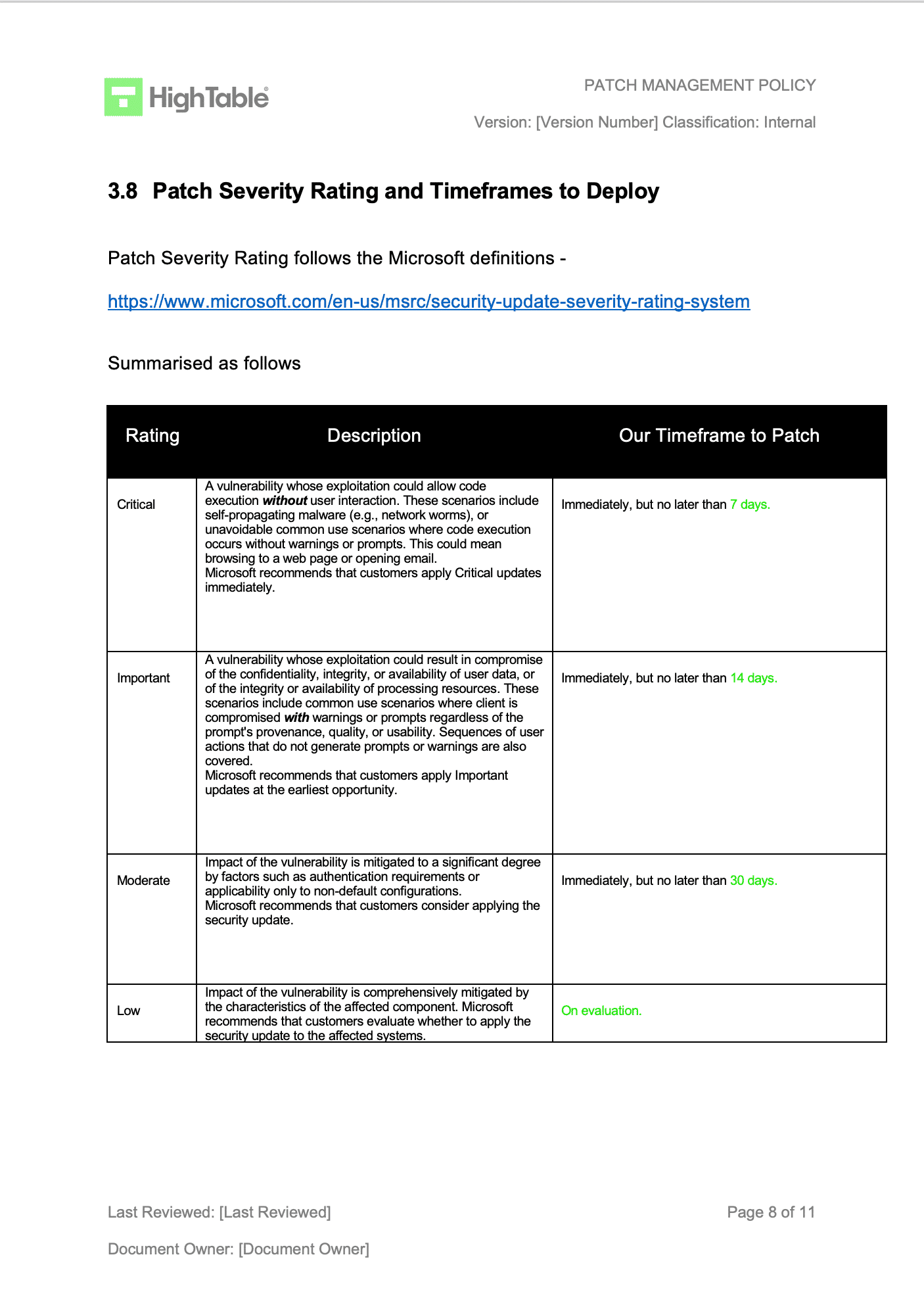
Firstly, it addresses the pervasive issue of known vulnerabilities. Many successful cyberattacks exploit weaknesses that have long been identified and for which patches are readily available. Implementing a Patch And Vulnerability Management Policy Template ensures that these critical updates are applied promptly and systematically, closing doors before attackers can walk through them. This proactive stance significantly reduces an organization’s attack surface.
Secondly, compliance requirements are becoming increasingly stringent. Regulations like GDPR, HIPAA, PCI DSS, and frameworks such as NIST demand demonstrable diligence in protecting sensitive data and maintaining secure systems. A meticulously documented Patch And Vulnerability Management Policy Template provides clear evidence of an organization’s commitment to these standards, simplifying audit processes and helping to avoid hefty fines and reputational damage associated with non-compliance.
Finally, the financial and reputational costs of a breach can be catastrophic. Beyond immediate monetary losses from incident response, recovery, and potential lawsuits, the long-term damage to customer trust and brand image can be irreversible. By systematically managing patches and vulnerabilities through a robust Patch And Vulnerability Management Policy Template, organizations invest in long-term resilience, protecting their bottom line and their public perception. It transforms security from an afterthought into an integrated, strategic component of business operations.
Key Benefits of Using a Patch And Vulnerability Management Policy Template
Adopting a formalized Patch And Vulnerability Management Policy Template brings a multitude of strategic and operational benefits to any organization, regardless of size or industry. These advantages extend far beyond simply "fixing bugs" and contribute to a stronger, more resilient enterprise.
One of the primary benefits is the standardization of procedures. Without a clear policy, patching efforts can be ad-hoc, inconsistent, and prone to human error. A Patch And Vulnerability Management Policy Template establishes clear, repeatable processes for identifying, prioritizing, testing, and deploying updates, ensuring every team member follows the same best practices. This consistency reduces operational chaos and improves efficiency.
Moreover, it significantly enhances the organization’s overall security posture. By regularly addressing vulnerabilities, the likelihood of successful exploits decreases dramatically. This leads to reduced downtime, minimized data loss, and greater confidence in the integrity and availability of IT systems. It helps in building a mature cybersecurity framework that can withstand evolving threats.
A well-crafted Patch And Vulnerability Management Policy Template also streamlines compliance efforts. When audit trails and operational guidelines are clearly defined within the policy, demonstrating adherence to regulatory requirements becomes far simpler. This can save countless hours during compliance audits and provide peace of mind that legal obligations are being met.
Finally, it fosters a culture of security awareness and accountability. When roles and responsibilities are clearly delineated within the Patch And Vulnerability Management Policy Template, every individual understands their part in maintaining security. This clarity reduces ambiguity, encourages proactive engagement, and makes incident response efforts more efficient should a breach occur, ultimately strengthening the organization’s defense capabilities.
Customizing Your Patch And Vulnerability Management Policy Template
While a Patch And Vulnerability Management Policy Template provides an excellent starting point, it’s crucial to understand that no single template will perfectly fit every organization straight out of the box. Customization is not just recommended; it’s essential to ensure the policy is relevant, actionable, and effective for your specific operational context.
The process of adapting your Patch And Vulnerability Management Policy Template should begin by considering the unique characteristics of your organization. This includes your industry (e.g., healthcare, finance, retail, government), the size of your IT infrastructure, the types of systems and applications you use, and the regulatory environment you operate within. A small startup with cloud-native applications will have different needs than a large enterprise managing legacy on-premises systems.
Key stakeholders should be involved in the customization process. This typically includes IT operations, cybersecurity teams, legal counsel, compliance officers, and relevant business unit leaders. Their input ensures that the policy not only meets technical security requirements but also aligns with business objectives, legal obligations, and operational realities. For instance, HR might have input on employee training aspects, while legal teams would review language pertaining to compliance and workplace rules.
Consider also your existing IT governance and risk management frameworks. Your Patch And Vulnerability Management Policy Template should integrate seamlessly with these broader strategies, rather than existing as an isolated document. This ensures a cohesive approach to data security and risk mitigation, enhancing the overall resilience of your digital environment. Tailoring the policy to your specific tech stack, including specific vendors or open-source solutions, will make it far more practical and implementable.
Important Elements for Your Patch And Vulnerability Management Policy Template
A truly effective Patch And Vulnerability Management Policy Template must be comprehensive, covering all critical aspects of managing software updates and security flaws. Here are the essential elements that should be included to ensure a robust and actionable policy:
- Policy Statement and Purpose: Clearly articulate the policy’s objective – typically to minimize security risks from unpatched vulnerabilities and ensure the integrity, confidentiality, and availability of information systems.
- Scope: Define what systems, software, networks, and data are covered by the policy. This might include servers, workstations, network devices, applications, cloud services, and mobile devices.
- Roles and Responsibilities: Clearly assign who is responsible for each aspect of vulnerability management, from identification to patching and reporting. This includes IT staff, security teams, asset owners, and management.
- Vulnerability Identification and Assessment: Detail the methods for discovering vulnerabilities, such as regular vulnerability scanning, penetration testing, security audits, and monitoring threat intelligence feeds (e.g., CVEs). Include procedures for prioritizing identified risks.
- Patch Management Procedures: Outline the process for acquiring, testing, approving, and deploying patches. This should cover different types of patches (security, functional, critical), testing environments, deployment schedules, and rollback procedures.
- Emergency Patching Procedures: Define a separate, expedited process for applying critical security patches or responding to zero-day exploits outside of the regular schedule.
- Exception Management: Establish a formal process for requesting, approving, and documenting exceptions to the policy, along with compensating controls to mitigate the associated risks.
- Configuration Management Integration: Describe how patch management aligns with configuration management to ensure updates don’t inadvertently introduce new vulnerabilities or break existing systems.
- Reporting and Documentation: Specify requirements for documenting patch deployment, vulnerability remediation, and policy adherence. This includes audit trails, success/failure rates, and regular status reports to management.
- Training and Awareness: Outline the need for ongoing training for staff on patch management procedures and general security awareness related to vulnerabilities.
- Policy Review and Update: Define a schedule and process for regularly reviewing and updating the Patch And Vulnerability Management Policy Template to reflect changes in technology, threats, and organizational structure.
- Compliance and Enforcement: Detail the consequences of non-compliance and how adherence to the policy will be monitored and enforced, aligning with broader workplace rules and IT governance.
- Incident Response Integration: Explain how this policy integrates with the overall incident response plan, especially in cases where a vulnerability leads to a security incident.
Tips for Design, Usability, and Implementation
A well-written Patch And Vulnerability Management Policy Template is only as effective as its usability and how well it’s implemented. Design and practical considerations play a significant role in ensuring the policy is understood, followed, and becomes an integral part of your organization’s security culture.
Firstly, focus on clarity and conciseness in your language. Avoid overly technical jargon where possible, or ensure it’s clearly defined. Use active voice and short sentences to make the policy easy to read and understand for all relevant personnel. Remember, a policy is a practical guide, not a theoretical treatise.
For usability, leverage formatting effectively. Employ clear headings (like those used in this article), bullet points, and numbered lists to break up dense text and highlight key information. A well-organized table of contents is also crucial for quick navigation, especially in digital formats. Consider flowcharts for complex processes like patch deployment or exception handling to provide a visual aid.
When it comes to implementation, communication is paramount. Simply publishing the Patch And Vulnerability Management Policy Template on an internal drive isn’t enough. Conduct training sessions to walk staff through the policy, explain its importance, and clarify roles and responsibilities. Ensure everyone understands the "why" behind the policy, not just the "what." This fosters better buy-in and compliance.
For digital implementation, ensure the document is easily accessible and searchable on your internal network or knowledge base. Implement version control to track changes and ensure everyone is always referencing the latest approved version. If your organization uses an IT service management (ITSM) platform, integrate the policy’s workflows and procedures into your existing tools to automate where possible and ensure consistency. Remember that the policy should be a living document, regularly reviewed and updated, reflecting the dynamic nature of both technology and threats. This continuous improvement approach ensures its long-term relevance and effectiveness.
In an era where cyber threats evolve by the minute, having a strong defense is non-negotiable. A meticulously crafted and actively managed Patch And Vulnerability Management Policy Template is more than just a bureaucratic document; it’s a living shield, protecting your organization from the relentless tide of digital dangers. It empowers your teams with clear directives, streamlines critical security operations, and significantly bolsters your overall security posture.
By investing the time and effort into developing, customizing, and implementing a comprehensive Patch And Vulnerability Management Policy Template, you are not just ticking a compliance box. You are proactively safeguarding your intellectual property, preserving customer trust, and ensuring business continuity. It provides the structured approach necessary to transform reactive firefighting into a strategic, continuous security program that builds resilience into the very fabric of your operations.
Embrace the power of a well-defined Patch And Vulnerability Management Policy Template. Let it be the cornerstone of your cybersecurity strategy, guiding your team towards a more secure and resilient future. Its value, in terms of risk reduction and peace of mind, is immeasurable in today’s digital world.